debian12极简快速安装k8s
操作系统:debian121、Master主机:2核以上CPU、4G以上内存、20G硬盘 2、Node主机:2核以上CPU3、节点之中不可以有重复的主机名、MAC 地址或 product_uuid4、为了保证 kubelet 正常工作,必须禁用交换分区。
一.前期安装准备
操作系统:debian12
Kubernetes : v1.29.2
docker:25.0.3
containerd:1.6.20
runc : 1.1.5
准备工作
1、Master主机:2核以上CPU、4G以上内存、20G硬盘 2、Node主机:2核以上CPU
3、节点之中不可以有重复的主机名、MAC 地址或 product_uuid
4、为了保证 kubelet 正常工作,必须禁用交换分区
二、前期安装配置
前期配置
配置各主节点的主机名称
hostnamectl set-hostname k8smaster && hostname
hostnamectl set-hostname k8snode1 && hostname配置各节点的Host文件,为了初始化集群节点间的通信
nano /etc/hosts
ip k8smaster
ip k8snode1
永久禁用各节点的交换分区,为了提高各节点的性能
swapoff -a && sed -i 's/.*swap.*/#&/' /etc/fstab同步各节点的时区
timedatectl set-timezone Asia/Shanghai安装ipset及ipvsadm
apt update
apt install ipset ipvsadm
#配置ipvsadm模块加载
cat << EOF |tee /etc/modules-load.d/ipvs.conf
ip_vs
ip_vs_rr
ip_vs_wrr
ip_vs_sh
ip_conntrack
EOF
cat << EOF |tee ipvs.sh
#!/bin/sh
modprobe -- ip_vs
modprobe -- ip_vs_rr
modprobe -- ip_vs_wrr
modprobe -- ip_vs_sh
modprobe -- ip_conntrack
EOF
#执行sh
sh ipvs.sh各节点安装容器运行时以及配置
docker安装(docker官网地址)
#先卸载非官方的docker
for pkg in docker.io docker-doc docker-compose podman-docker containerd runc; do apt-get remove $pkg; done
apt-get update
apt-get install ca-certificates curl
install -m 0755 -d /etc/apt/keyrings
curl -fsSL https://download.docker.com/linux/debian/gpg -o /etc/apt/keyrings/docker.asc
chmod a+r /etc/apt/keyrings/docker.asc
echo \
"deb [arch=$(dpkg --print-architecture) signed-by=/etc/apt/keyrings/docker.asc] https://download.docker.com/linux/debian \
$(. /etc/os-release && echo "$VERSION_CODENAME") stable" | \
tee /etc/apt/sources.list.d/docker.list > /dev/null
apt-get update
#这是安装最新版本
apt-get install docker-ce docker-ce-cli containerd.io docker-buildx-plugin docker-compose-plugin
#查看是否启动
service docker status
service docker start #启动
#设置开机自启
systemctl enable docker && systemctl restart docker && systemctl status docker
docker info #基本信息编辑containerd 配置文件
nano /etc/containerd/conf.toml (把文件内容替换成如下内容) 然后保存
disabled_plugins = []
imports = []
oom_score = 0
plugin_dir = ""
required_plugins = []
root = "/var/lib/containerd"
state = "/run/containerd"
temp = ""
version = 2
[cgroup]
path = ""
[debug]
address = ""
format = ""
gid = 0
level = ""
uid = 0
[grpc]
address = "/run/containerd/containerd.sock"
gid = 0
max_recv_message_size = 16777216
max_send_message_size = 16777216
tcp_address = ""
tcp_tls_ca = ""
tcp_tls_cert = ""
tcp_tls_key = ""
uid = 0
[metrics]
address = ""
grpc_histogram = false
[plugins]
[plugins."io.containerd.gc.v1.scheduler"]
deletion_threshold = 0
mutation_threshold = 100
pause_threshold = 0.02
schedule_delay = "0s"
startup_delay = "100ms"
[plugins."io.containerd.grpc.v1.cri"]
device_ownership_from_security_context = false
disable_apparmor = false
disable_cgroup = false
disable_hugetlb_controller = true
disable_proc_mount = false
disable_tcp_service = true
enable_selinux = false
enable_tls_streaming = false
enable_unprivileged_icmp = false
enable_unprivileged_ports = false
ignore_image_defined_volumes = false
max_concurrent_downloads = 3
max_container_log_line_size = 16384
netns_mounts_under_state_dir = false
restrict_oom_score_adj = false
sandbox_image = "registry.aliyuncs.com/google_containers/pause:3.9"
selinux_category_range = 1024
stats_collect_period = 10
stream_idle_timeout = "4h0m0s"
stream_server_address = "127.0.0.1"
stream_server_port = "0"
systemd_cgroup = false
tolerate_missing_hugetlb_controller = true
unset_seccomp_profile = ""
[plugins."io.containerd.grpc.v1.cri".cni]
bin_dir = "/opt/cni/bin"
conf_dir = "/etc/cni/net.d"
conf_template = ""
ip_pref = ""
max_conf_num = 1
[plugins."io.containerd.grpc.v1.cri".containerd]
default_runtime_name = "runc"
disable_snapshot_annotations = true
discard_unpacked_layers = false
ignore_rdt_not_enabled_errors = false
no_pivot = false
snapshotter = "overlayfs"
[plugins."io.containerd.grpc.v1.cri".containerd.default_runtime]
base_runtime_spec = ""
cni_conf_dir = ""
cni_max_conf_num = 0
container_annotations = []
pod_annotations = []
privileged_without_host_devices = false
runtime_engine = ""
runtime_path = ""
runtime_root = ""
runtime_type = ""
[plugins."io.containerd.grpc.v1.cri".containerd.default_runtime.options]
[plugins."io.containerd.grpc.v1.cri".containerd.runtimes]
[plugins."io.containerd.grpc.v1.cri".containerd.runtimes.runc]
base_runtime_spec = ""
cni_conf_dir = ""
cni_max_conf_num = 0
container_annotations = []
pod_annotations = []
privileged_without_host_devices = false
runtime_engine = ""
runtime_path = ""
runtime_root = ""
runtime_type = "io.containerd.runc.v2"
[plugins."io.containerd.grpc.v1.cri".containerd.runtimes.runc.options]
BinaryName = ""
CriuImagePath = ""
CriuPath = ""
CriuWorkPath = ""
IoGid = 0
IoUid = 0
NoNewKeyring = false
NoPivotRoot = false
Root = ""
ShimCgroup = ""
SystemdCgroup = true
[plugins."io.containerd.grpc.v1.cri".containerd.untrusted_workload_runtime]
base_runtime_spec = ""
cni_conf_dir = ""
cni_max_conf_num = 0
container_annotations = []
pod_annotations = []
privileged_without_host_devices = false
runtime_engine = ""
runtime_path = ""
runtime_root = ""
runtime_type = ""
[plugins."io.containerd.grpc.v1.cri".containerd.untrusted_workload_runtime.options]
[plugins."io.containerd.grpc.v1.cri".image_decryption]
key_model = "node"
[plugins."io.containerd.grpc.v1.cri".registry]
config_path = ""
[plugins."io.containerd.grpc.v1.cri".registry.auths]
[plugins."io.containerd.grpc.v1.cri".registry.configs]
[plugins."io.containerd.grpc.v1.cri".registry.configs."k8smaster:5000".tls]
insecure_skip_verify = true
[plugins."io.containerd.grpc.v1.cri".registry.headers]
[plugins."io.containerd.grpc.v1.cri".registry.mirrors]
[plugins."io.containerd.grpc.v1.cri".registry.mirrors."k8smaster:5000"]
endpoint = ["http://k8smaster:5000"]
[plugins."io.containerd.grpc.v1.cri".x509_key_pair_streaming]
tls_cert_file = ""
tls_key_file = ""
[plugins."io.containerd.internal.v1.opt"]
path = "/opt/containerd"
[plugins."io.containerd.internal.v1.restart"]
interval = "10s"
[plugins."io.containerd.internal.v1.tracing"]
sampling_ratio = 1.0
service_name = "containerd"
[plugins."io.containerd.metadata.v1.bolt"]
content_sharing_policy = "shared"
[plugins."io.containerd.monitor.v1.cgroups"]
no_prometheus = false
[plugins."io.containerd.runtime.v1.linux"]
no_shim = false
runtime = "runc"
runtime_root = ""
shim = "containerd-shim"
shim_debug = false
[plugins."io.containerd.runtime.v2.task"]
platforms = ["linux/amd64"]
sched_core = false
[plugins."io.containerd.service.v1.diff-service"]
default = ["walking"]
[plugins."io.containerd.service.v1.tasks-service"]
rdt_config_file = ""
[plugins."io.containerd.snapshotter.v1.aufs"]
root_path = ""
[plugins."io.containerd.snapshotter.v1.btrfs"]
root_path = ""
[plugins."io.containerd.snapshotter.v1.devmapper"]
async_remove = false
base_image_size = ""
discard_blocks = false
fs_options = ""
fs_type = ""
pool_name = ""
root_path = ""
[plugins."io.containerd.snapshotter.v1.native"]
root_path = ""
[plugins."io.containerd.snapshotter.v1.overlayfs"]
root_path = ""
upperdir_label = false
[plugins."io.containerd.snapshotter.v1.zfs"]
root_path = ""
[plugins."io.containerd.tracing.processor.v1.otlp"]
endpoint = ""
insecure = false
protocol = ""
[proxy_plugins]
[stream_processors]
[stream_processors."io.containerd.ocicrypt.decoder.v1.tar"]
accepts = ["application/vnd.oci.image.layer.v1.tar+encrypted"]
args = ["--decryption-keys-path", "/etc/containerd/ocicrypt/keys"]
env = ["OCICRYPT_KEYPROVIDER_CONFIG=/etc/containerd/ocicrypt/ocicrypt_keyprovider.conf"]
path = "ctd-decoder"
returns = "application/vnd.oci.image.layer.v1.tar"
[stream_processors."io.containerd.ocicrypt.decoder.v1.tar.gzip"]
accepts = ["application/vnd.oci.image.layer.v1.tar+gzip+encrypted"]
args = ["--decryption-keys-path", "/etc/containerd/ocicrypt/keys"]
env = ["OCICRYPT_KEYPROVIDER_CONFIG=/etc/containerd/ocicrypt/ocicrypt_keyprovider.conf"]
path = "ctd-decoder"
returns = "application/vnd.oci.image.layer.v1.tar+gzip"
[timeouts]
"io.containerd.timeout.bolt.open" = "0s"
"io.containerd.timeout.shim.cleanup" = "5s"
"io.containerd.timeout.shim.load" = "5s"
"io.containerd.timeout.shim.shutdown" = "3s"
"io.containerd.timeout.task.state" = "2s"
[ttrpc]
address = ""
gid = 0
uid = 0
设置containerd的开机自启
#设置开机自启
systemctl enable containerd
#重启containerd
systemctl restart containerd
systemctl status containerd三、安装kubelet、kubeadm 和 kubectl
apt-get update
添加 Kubernetes 官方 GPG 密钥并添加稳定版仓库源
apt-get install -y apt-transport-https ca-certificates curl gpg
curl -fsSL https://pkgs.k8s.io/core:/stable:/v1.29/deb/Release.key | gpg --dearmor -o /etc/apt/keyrings/kubernetes-apt-keyring.gpg
添加 Kubernetes apt 仓库
echo 'deb [signed-by=/etc/apt/keyrings/kubernetes-apt-keyring.gpg] https://pkgs.k8s.io/core:/stable:/v1.29/deb/ /' | tee /etc/apt/sources.list.d/kubernetes.list
更新包
apt update
安装 kubelet、kubeadm 和 kubectl
apt-get install -y kubelet kubeadm kubectl
apt-mark hold kubelet kubeadm kubectl #锁定版本,标记软件包不被自动更新
systemctl enable kubelet #添加 kubelet 开机自启
systemctl restart kubelet && systemctl status kubelet # 重启并查看状态四、初始化 Master节点
版本必须和上边安装的kubelet,kubead,kubectl保持一致
查询k8s各组件的版本号
# 查询k8s各组件的版本号
kubeadm config images list
----------------------------
registry.k8s.io/kube-apiserver:v1.29.2
registry.k8s.io/kube-controller-manager:v1.29.2
registry.k8s.io/kube-scheduler:v1.29.2
registry.k8s.io/kube-proxy:v1.29.2
registry.k8s.io/coredns/coredns:v1.11.1
registry.k8s.io/pause:3.9
registry.k8s.io/etcd:3.5.10-0
#输出类似这种k8s中nodePort是用来暴露服务到集群外部的节点(即宿主机)上的特定端口,这个端口范围默认是30000至32767,如果需要指定范围外的端口 (这块看自己需求设置,一般使用默认的)
初始化时加入一个参数值
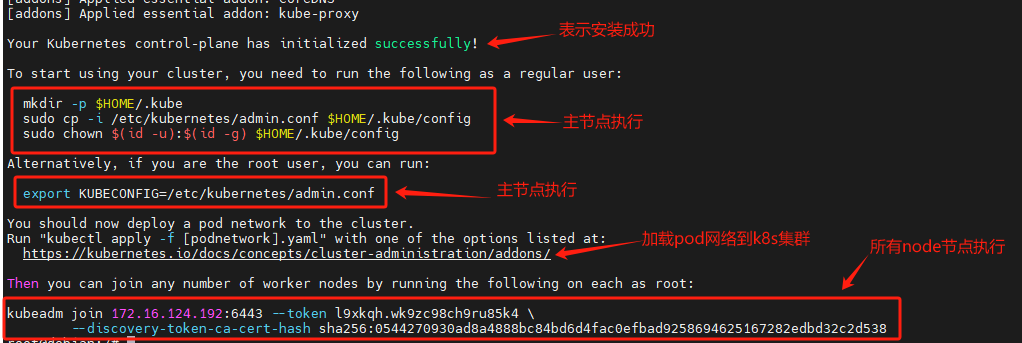
kubeadm init --service-node-port-range=<your-desired-range>初始化主节点
kubeadm init \
--kubernetes-version=1.29.2 \ 指定版本
--apiserver-advertise-address=0.0.0.0 \ #为通告给其它组件的IP,一般应为master节点的IP地址
--pod-network-cidr=10.244.0.0/16 \
--image-repository=registry.aliyuncs.com/google_containers #指定镜像源拉取完后

配置环境变量
执行初始化成功后输出的那三条命令,然后配置环境变量
mkdir -p $HOME/.kube
cp -i /etc/kubernetes/admin.conf $HOME/.kube/config
chown $(id -u):$(id -g) $HOME/.kube/config
export KUBECONFIG=/etc/kubernetes/admin.conf
#查看Token
kubeadm token list五、配置calico网络插件
kubectl create -f https://raw.gitmirror.com/projectcalico/calico/v3.27.2/manifests/tigera-operator.yaml
apt update
apt install wget
wget https://raw.gitmirror.com/projectcalico/calico/v3.27.2/manifests/custom-resources.yaml
#更改配置文件
nano custom-resources.yaml
#把里边cidr:ip 更换
cidr: 10.244.0.0/16
#再创建文件
kubectl create -f custom-resources.yaml
#查看pod容器
kubectl get pod -A
测试外部是否能请求地址(这里简单部署一个nginx)
kubectl create deployment nginx --image=nginx
kubectl expose deployment nginx --port=80 --type=NodePort
#查看端口
kubectl get svc -A
外部请求 http://ip:端口

表示网络插件部署完成
查看节点信息
kubectl get node![]()
六、配置node节点
编辑 /etc/sysctl.conf 文件
#在文件末尾添加或修改以下行
net.ipv4.ip_forward = 1
#应用新的内核参数配置
sysctl -p /etc/sysctl.confNode节点执行
(这个根据自己初始化时候输出token去加入)
kubeadm join 172.16.124.192:6443 --token iccha2.zkkh61v9qpbhyh3y
--discovery-token-ca-cert-hash sha256:bfb1ba73a182d289b12e81bbc1dd315f34f0b1f599c5e242872bffce4566d5b6配置kube.conf
mkdir ~/.kube
cp /etc/kubernetes/kubelet.conf ~/.kube/config主节点查看 node

至此配置完成
七、可能出现的污点
在部署nginx的时候可能拉不下来
查看是否有污点
kubectl describe nodes 自己节点名 |grep Taints
#删除污点
kubectl taint node 节点名 污点名-更多推荐
 已为社区贡献2条内容
已为社区贡献2条内容






所有评论(0)