k8s安装ArgoCD(统一身份认证对接LDAP)(配置用户的角色及权限)
K8S安装argocd,统一身份认证对接ldap,并且配置不同的角色及权限项。
一、安装 Argo CD
- k8s版本是v1.19.1
使用以下命令在 argocd 命名空间部署 Argo CD。
# 创建命名空间
kubectl create namespace argocd
# 部署 argo cd
wget https://raw.githubusercontent.com/argoproj/argo-cd/v2.4.9/manifests/ha/install.yaml
kubectl apply -n argocd -f install.yaml
# 或者 kubectl create -n argocd -f install.yaml
- 卸载argocd
kubectl delete -f install.yaml -n argocd
安装完成后,验证见下:
- 1、Pod
[admin@jenkins]$ kubectl -n argocd get pod
NAME READY STATUS RESTARTS AGE
argocd-application-controller-0 1/1 Running 0 26m
argocd-applicationset-controller-68b9bdbd8b-ld6cf 1/1 Running 0 26m
argocd-dex-server-6cff7fb675-l94r4 1/1 Running 0 26m
argocd-notifications-controller-6dbcbc6849-tr2jb 1/1 Running 0 26m
argocd-redis-599b855497-q5hft 1/1 Running 0 26m
argocd-repo-server-548b5f4c9b-hw2x4 1/1 Running 0 26m
argocd-server-754cbf9fd7-m2tkc 1/1 Running 0 26m
- 2、查看admin用户的密码
xjABvQ9kFSS3DerW
[admin@jenkins]$ kubectl -n argocd get secret \
argocd-initial-admin-secret \
-o jsonpath="{.data.password}" | base64 -d
xjABvQ9kFSS3DerW
二、发布 Argo CD 服务
默认情况下, Argo CD 服务不对外暴露服务,可以通过 LoadBalancer 或者 NodePort 类型的 Service、Ingress、Kubectl 端口转发等方式将 Argo CD 服务发布到 Kubernetes 集群外部。
这里使用以下命令通过 NodePort 服务的方式暴露 Argo CD 到集群外部。
kubectl patch svc argocd-server -n argocd -p '{"spec": {"type": "NodePort"}}'
因为我没有使用Ingress的方式暴露访问域名,是使用IP+PORT的方式暴露访问地址。
可以看到,argocd-server的类型已经是NodePort了,它生成了一个随机端口30984。所以argocd的访问地址是:https://192.168.80.180:30984/ (192.168.80.180是node节点的ip地址)
[admin@jenkins]$ kubectl get svc -n argocd
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
argocd-applicationset-controller ClusterIP 10.108.149.65 <none> 7000/TCP,8080/TCP 7d20h
argocd-dex-server ClusterIP 10.96.208.150 <none> 5556/TCP,5557/TCP,5558/TCP 7d20h
argocd-metrics ClusterIP 10.99.225.44 <none> 8082/TCP 7d20h
argocd-notifications-controller-metrics ClusterIP 10.97.136.140 <none> 9001/TCP 7d20h
argocd-redis ClusterIP 10.99.13.121 <none> 6379/TCP 7d20h
argocd-repo-server ClusterIP 10.97.72.137 <none> 8081/TCP,8084/TCP 7d20h
argocd-server NodePort 10.111.136.78 <none> 80:30984/TCP,443:30348/TCP 7d20h
argocd-server-metrics ClusterIP 10.106.102.243 <none> 8083/TCP 7d20h
三、对接LDAP
- 1、编写ldap-patch-dex.yaml
[admin@jenkins]$ vi ldap-patch-dex.yaml
# Please edit the object below. Lines beginning with a '#' will be ignored,
# and an empty file will abort the edit. If an error occurs while saving this file will be
# reopened with the relevant failures.
#
apiVersion: v1
data:
dex.config: |-
connectors:
- type: ldap
name: ..................
id: ldap
config:
# Ldap server address
host: 192.168.5.16:389
insecureNoSSL: true
insecureSkipVerify: true
# Variable name stores ldap bindDN in argocd-secret
bindDN: "$dex.ldap.bindDN"
# Variable name stores ldap bind password in argocd-secret
bindPW: "$dex.ldap.bindPW"
usernamePrompt: .........
# Ldap user serch attributes
userSearch:
baseDN: "ou=people,dc=xxx,dc=com"
filter: "(objectClass=person)"
username: uid
idAttr: uid
emailAttr: mail
nameAttr: cn
# Ldap group serch attributes
groupSearch:
baseDN: "ou=argocd,ou=group,dc=xxx,dc=com"
filter: "(objectClass=groupOfUniqueNames)"
userAttr: DN
groupAttr: uniqueMember
nameAttr: cn
# 注意:这个是argocd的访问地址,必须配置,否则会导致不会跳转.
url: https://192.168.80.180:30984
- 2、configMap
[admin@jenkins]$ kubectl -n argocd patch configmaps argocd-cm --patch "$(cat ldap-patch-dex.yaml)"
- 3、修改configMap
kubectl edit cm argocd-cm -n argocd
- 3、secret
# bindDN是cn=admin,dc=xxx,dc=com
kubectl -n argocd patch secrets argocd-secret --patch "{\"data\":{\"dex.ldap.bindDN\":\"$(echo cn=admin,dc=xxx,dc=com | base64 -w 0)\"}}"
# 密码bindPW是123456
kubectl -n argocd patch secrets argocd-secret --patch "{\"data\":{\"dex.ldap.bindPW\":\"$(echo 123456 | base64 -w 0)\"}}"
- 4、查看日志
kubectl logs -f -n argocd argocd-dex-server-7689686bd9-4srkc
time="2023-06-27T07:10:00Z" level=info msg="ArgoCD Dex Server is starting" built="2023-06-16T14:35:08Z" commit=a2430af1c356b283e5e3fc5bde1f5e2b5199f258 namespace=argocd version=v2.7.5+a2430af.dirty
time="2023-06-27T07:10:00Z" level=info msg="Generating self-signed TLS certificate for this session"
time="2023-06-27T07:10:00Z" level=info msg="Starting configmap/secret informers"
time="2023-06-27T07:10:00Z" level=info msg="Configmap/secret informer synced"
time="2023-06-27T07:10:00Z" level=info msg="0xc0006ac600 subscribed to settings updates"
time="2023-06-27T07:10:00Z" level=info msg="dex is not configured"
time="2023-06-27T07:18:35Z" level=info msg="Notifying 1 settings subscribers: [0xc0006ac600]"
time="2023-06-27T07:18:35Z" level=info msg="dex config modified. restarting dex"
time="2023-06-27T07:18:35Z" level=info msg="Dex Version: v2.36.0-dirty, Go Version: go1.20.2, Go OS/ARCH: linux amd64"
time="2023-06-27T07:18:35Z" level=info msg="config issuer: https://192.168.80.180:30984/api/dex"
time="2023-06-27T07:18:35Z" level=info msg="config storage: memory"
time="2023-06-27T07:18:35Z" level=info msg="config static client: Argo CD"
time="2023-06-27T07:18:35Z" level=info msg="config static client: Argo CD CLI"
time="2023-06-27T07:18:35Z" level=info msg="config connector: ldap"
time="2023-06-27T07:18:35Z" level=info msg="config skipping approval screen"
time="2023-06-27T07:18:35Z" level=info msg="config refresh tokens rotation enabled: true"
time="2023-06-27T07:18:35Z" level=warning msg="Deprecated: LDAP: use groupSearch.userMatchers option instead of \"userAttr/groupAttr\" fields."
time="2023-06-27T07:18:35Z" level=info msg="keys expired, rotating"
time="2023-06-27T07:18:36Z" level=info msg="keys rotated, next rotation: 2023-06-27 13:18:36.026673153 +0000 UTC"
time="2023-06-27T07:18:36Z" level=info msg="listening (telemetry) on 0.0.0.0:5558"
time="2023-06-27T07:18:36Z" level=info msg="listening (https) on 0.0.0.0:5556"
time="2023-06-27T07:18:36Z" level=info msg="listening (grpc) on 0.0.0.0:5557"
time="2023-06-27T08:49:52Z" level=info msg="performing ldap search ou=people,dc=xxx,dc=com sub (&(objectClass=person)(uid=150xxxx9916))"
time="2023-06-27T08:49:52Z" level=info msg="username \"150xxxx9916\" mapped to entry cn=150xxxx9916,ou=java-platform,ou=people,dc=xxx,dc=com"
time="2023-06-27T08:49:52Z" level=info msg="performing ldap search ou=argocd,ou=group,dc=xxx,dc=com sub (&(objectClass=groupOfUniqueNames)(uniqueMember=cn=150xxxx9916,ou=java-platform,ou=people,dc=xxx,dc=com))"
time="2023-06-27T08:49:52Z" level=info msg="login successful: connector \"ldap\", username=\"150xxxx9916\", preferred_username=\"\", email=\"xxx@xxx.com\", groups=[\"argocd-admin\"]"
- 5、删除POD,以重启,让上面的ldap配置生效。
kubectl delete pod -n argocd argocd-server-7bf49f8b5-ksq6l
kubectl delete pod -n argocd argocd-dex-server-7689686bd9-xwxf8
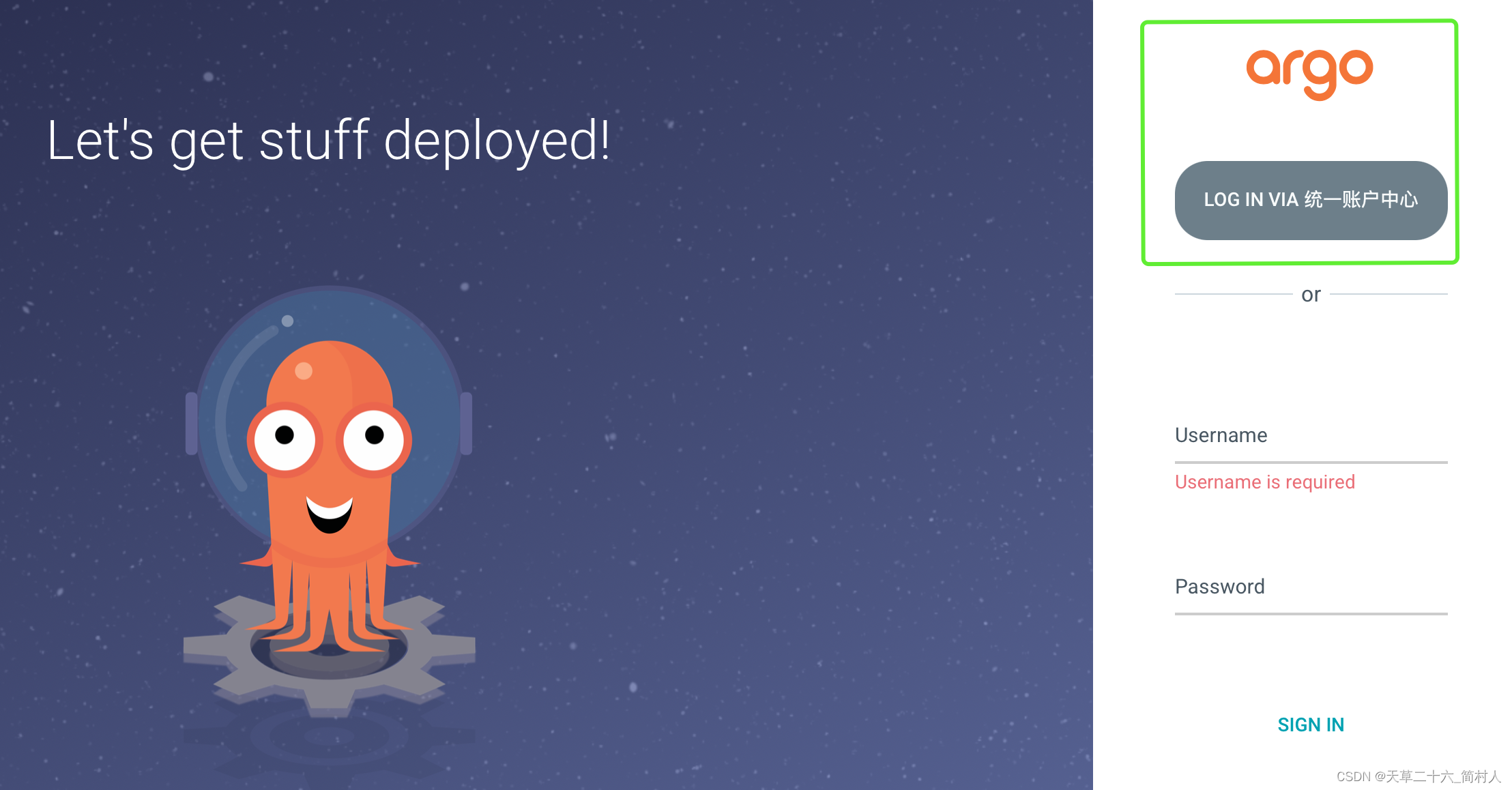
四、登录测试
重启后,这里会多一个登录入口,支持LDAP。

输入用户名和密码,登录系统~
但是,不同的浏览器对这个界面的样式展示会有差异,下面是Safari浏览器。

五、Ldap设置
新建两个组,argocd-admin(管理员),argocd-users(普通用户)

六、argocd的权限
参考其官方网址:https://argo-cd.readthedocs.io/en/stable/operator-manual/rbac/
1、自定义角色
kubectl edit configmaps -n argocd argocd-rbac-cm
- 创建一个devops角色,具备某一部分的权限。
apiVersion: v1
kind: ConfigMap
metadata:
name: argocd-rbac-cm
namespace: argocd
data:
policy.csv: |
# 先定义角色及对应的权限项列表
# 角色leader-admin,和默认的角色admin一样
p, role:leader-admin, *, *, *, allow
# 配置应用同步权限
p, role:devops, applications, sync, *, allow
# 配置应用回滚权限
p, role:devops, applications, update, *, allow
# 配置查看应用日志权限
p, role:devops, logs, get, *, allow
# 配置用户可以进入容器终端进行操作的权限
p, role:devops, exec, create, */*, allow
# 下面是对组进行赋予角色
# ldap组argocd-admin赋予角色leader-admin
g, argocd-admin, role:leader-admin
# ldap组argocd-users赋予角色devops
g, argocd-users, role:devops
# 默认的权限包含role:readonly
policy.default: role:readonly
重启Pod: argocd-server、argocd-dex-server。
2、默认角色对应的权限
默认,系统已创建好了两个角色,见下:
- role:admin
- role:readonly
详细的权限项见下,官网链接是https://github.com/argoproj/argo-cd/blob/master/assets/builtin-policy.csv
# Built-in policy which defines two roles: role:readonly and role:admin,
# and additionally assigns the admin user to the role:admin role.
# There are two policy formats:
# 1. Applications, logs, and exec (which belong to a project):
# p, <user/group>, <resource>, <action>, <project>/<object>
# 2. All other resources:
# p, <user/group>, <resource>, <action>, <object>
p, role:readonly, applications, get, */*, allow
p, role:readonly, certificates, get, *, allow
p, role:readonly, clusters, get, *, allow
p, role:readonly, repositories, get, *, allow
p, role:readonly, projects, get, *, allow
p, role:readonly, accounts, get, *, allow
p, role:readonly, gpgkeys, get, *, allow
p, role:readonly, logs, get, */*, allow
p, role:admin, applications, create, */*, allow
p, role:admin, applications, update, */*, allow
p, role:admin, applications, delete, */*, allow
p, role:admin, applications, sync, */*, allow
p, role:admin, applications, override, */*, allow
p, role:admin, applications, action/*, */*, allow
p, role:admin, applicationsets, get, */*, allow
p, role:admin, applicationsets, create, */*, allow
p, role:admin, applicationsets, update, */*, allow
p, role:admin, applicationsets, delete, */*, allow
p, role:admin, certificates, create, *, allow
p, role:admin, certificates, update, *, allow
p, role:admin, certificates, delete, *, allow
p, role:admin, clusters, create, *, allow
p, role:admin, clusters, update, *, allow
p, role:admin, clusters, delete, *, allow
p, role:admin, repositories, create, *, allow
p, role:admin, repositories, update, *, allow
p, role:admin, repositories, delete, *, allow
p, role:admin, projects, create, *, allow
p, role:admin, projects, update, *, allow
p, role:admin, projects, delete, *, allow
p, role:admin, accounts, update, *, allow
p, role:admin, gpgkeys, create, *, allow
p, role:admin, gpgkeys, delete, *, allow
p, role:admin, exec, create, */*, allow
# 角色role:admin追加角色role:readonly,相当于取权限的并集了。
g, role:admin, role:readonly
# 用户admin赋予角色role:admin
g, admin, role:admin
3、权限的补充说明
你可以使用正则表达式像下面这样~
# 权限仅限于项目dev-project
p, dev-group, applicationsets, *, dev-project/*, allow
关于resource和action到底有哪些:
Resources: clusters, projects, applications, applicationsets, repositories, certificates, accounts, gpgkeys, logs, exec, extensions
Actions: get, create, update, delete, sync, override,action/<group/kind/action-name>
注意:后面的Actions(sync, override, and action/<group/kind/action-name>) 只适用于 resource-applications。
4、argocd-users组下的用户登录argocd
测试验证project的create权限,提示用户不能创建,缺少权限。

七、出现过的问题
1、argocd-repo-server安装失败
time="2023-07-04T07:49:59Z" level=info msg="ArgoCD Repository Server is starting" built="2023-06-20T20:51:13Z" commit=00c914a948d9e8ad99be8bd82a368fbdeba12f88 port=8081 version=v2.7.6+00c914a.dirty
time="2023-07-04T07:49:59Z" level=info msg="Generating self-signed TLS certificate for this session"
time="2023-07-04T07:49:59Z" level=info msg="Initializing GnuPG keyring at /app/config/gpg/keys"
time="2023-07-04T07:49:59Z" level=info msg="gpg --no-permission-warning --logger-fd 1 --batch --gen-key /tmp/gpg-key-recipe2861856502" dir= execID=cb51c
time="2023-07-04T07:50:05Z" level=error msg="`gpg --no-permission-warning --logger-fd 1 --batch --gen-key /tmp/gpg-key-recipe2861856502` failed exit status 2" execID=cb51c
time="2023-07-04T07:50:05Z" level=info msg=Trace args="[gpg --no-permission-warning --logger-fd 1 --batch --gen-key /tmp/gpg-key-recipe2861856502]" dir= operation_name="exec gpg" time_ms=6049.890974
time="2023-07-04T07:50:05Z" level=fatal msg="`gpg --no-permission-warning --logger-fd 1 --batch --gen-key /tmp/gpg-key-recipe2861856502` failed exit status 2"
- 目前的解决办法:降低argocd的版本号
更多推荐
 已为社区贡献23条内容
已为社区贡献23条内容







所有评论(0)