【码上爬】图灵爬虫练习实战详解
【码上爬】图灵爬虫练习平台-全题型实战详解,附分析过程、js逆向过程以及源码
码上爬:aHR0cHM6Ly93d3cubWFzaGFuZ3BhLmNvbS8=
目录
码上爬练习题
第一题
import time
import requests
urls = ['https://www.mashangpa.com/api/problem-detail/1/data/?page={}'.format(i) for i in range(1,21)]
# 需要登录,请先登录,获取cookie并完善参数
cookies = {
'xxx':'xxxx',
......
}
final_sum = 0
start_time = time.time()
for url in urls:
response = requests.get(url,cookies=cookies)
data = response.json().get('current_array')
print(f"当前url: {url}, 数组: {data}")
final_sum += sum(data)
end_time = time.time()
print(f"最终的和为: {final_sum}, 耗时: {end_time - start_time:.5f}s")第二题
因为有反爬,需要设置headers,增加user-agent和referer防盗链即可。
import time
import requests
urls = ['https://www.mashangpa.com/api/problem-detail/2/data/?page={}'.format(i) for i in range(1,21)]
headers = {
'User-Agent':'Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/137.0.0.0 Safari/537.36 Edg/137.0.0.0',
'referer':'https://www.mashangpa.com/problem-detail/2/'
}
# 需要登录,请先登录,获取cookie并完善参数
cookies = {
'xxx':'xxxx',
......
}
final_sum = 0
start_time = time.time()
for url in urls:
response = requests.get(url,cookies=cookies, headers=headers)
data = response.json().get('current_array')
print(f"当前url: {url}, 数组: {data}")
final_sum += sum(data)
end_time = time.time()
print(f"最终的和为: {final_sum}, 耗时: {end_time - start_time:.5f}s")第三题
F12调试,被嘲讽了哈哈~~,手动打开调试器也会被检测......(最基础的浏览器反爬手段)

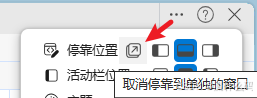
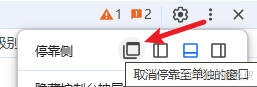
最简单的解决方法:在打开第三题的页面之前,F12把调试器打开,并在右上角三个小点,选择停靠位置为取消停靠到单独的窗口,此时再点击访问第三题,此时在网络中就能看到获取的数据包了。edge和chrome浏览器操作如下:
import time
import requests
urls = ['https://www.mashangpa.com/api/problem-detail/3/data/?page={}'.format(i) for i in range(1,21)]
headers = {
'User-Agent':'Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/137.0.0.0 Safari/537.36 Edg/137.0.0.0',
'referer':'https://www.mashangpa.com/problem-detail/3/'
}
# 需要登录,请先登录,获取cookie并完善参数
cookies = {
'xxx':'xxxx',
......
}
final_sum = 0
start_time = time.time()
for url in urls:
response = requests.get(url,cookies=cookies, headers=headers)
data = response.json().get('current_array')
print(f"当前url: {url}, 数组: {data}")
final_sum += sum(data)
end_time = time.time()
print(f"最终的和为: {final_sum}, 耗时: {end_time - start_time:.5f}s")第四题
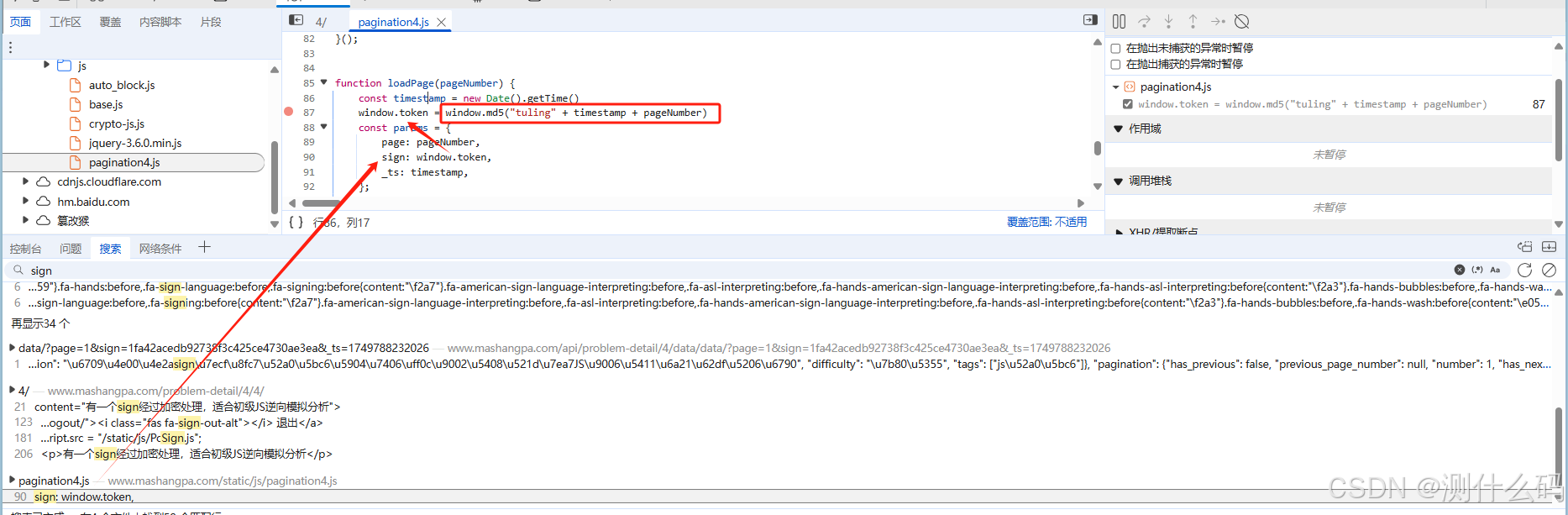
断点调试,发现请求中有个sign进行加密,sign是由window.token进行MD5加密得到,_ts为时间戳。
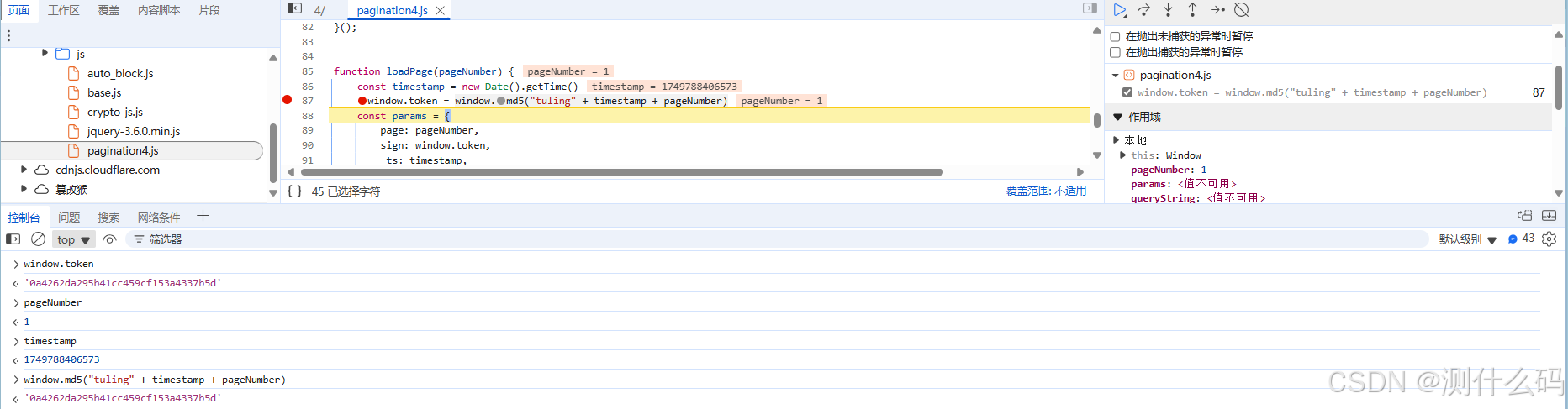
调试验证,与结果一致
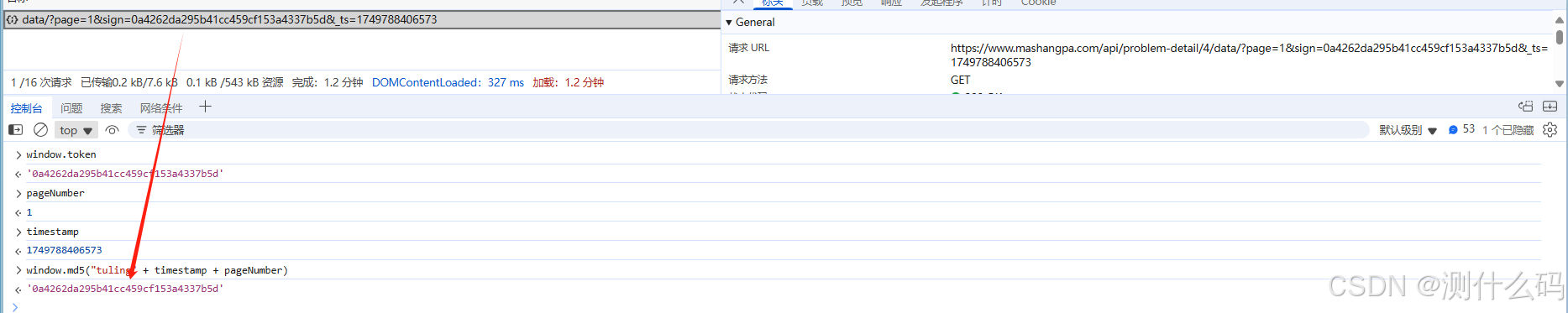
import time
import hashlib
import requests
headers = {
'User-Agent':'Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/137.0.0.0 Safari/537.36 Edg/137.0.0.0',
'referer':'https://www.mashangpa.com/problem-detail/4/'
}
# 需要登录,请先登录,获取cookie并完善参数
cookies = {
'xxx':'xxxx',
......
}
final_sum = 0
start_time = time.time()
for page in range(1,21):
time_stamp = int(time.time() * 1000)
text = "tuling" + str(time_stamp) + str(page)
sign = hashlib.md5(text.encode('utf-8'))
sign = sign.hexdigest()
url = f'https://www.mashangpa.com/api/problem-detail/4/data/?page={page}&sign={sign}&_ts={time_stamp}'
print(url)
response = requests.get(url, cookies=cookies, headers=headers)
data = response.json().get('current_array')
print(f"当前url: {url}, 数组: {data}")
final_sum += sum(data)
end_time = time.time()
print(f"最终的和为: {final_sum}, 耗时: {end_time - start_time:.5f}s")第五题
断点调试,请求数据中有个加密的载荷xl,定位调试
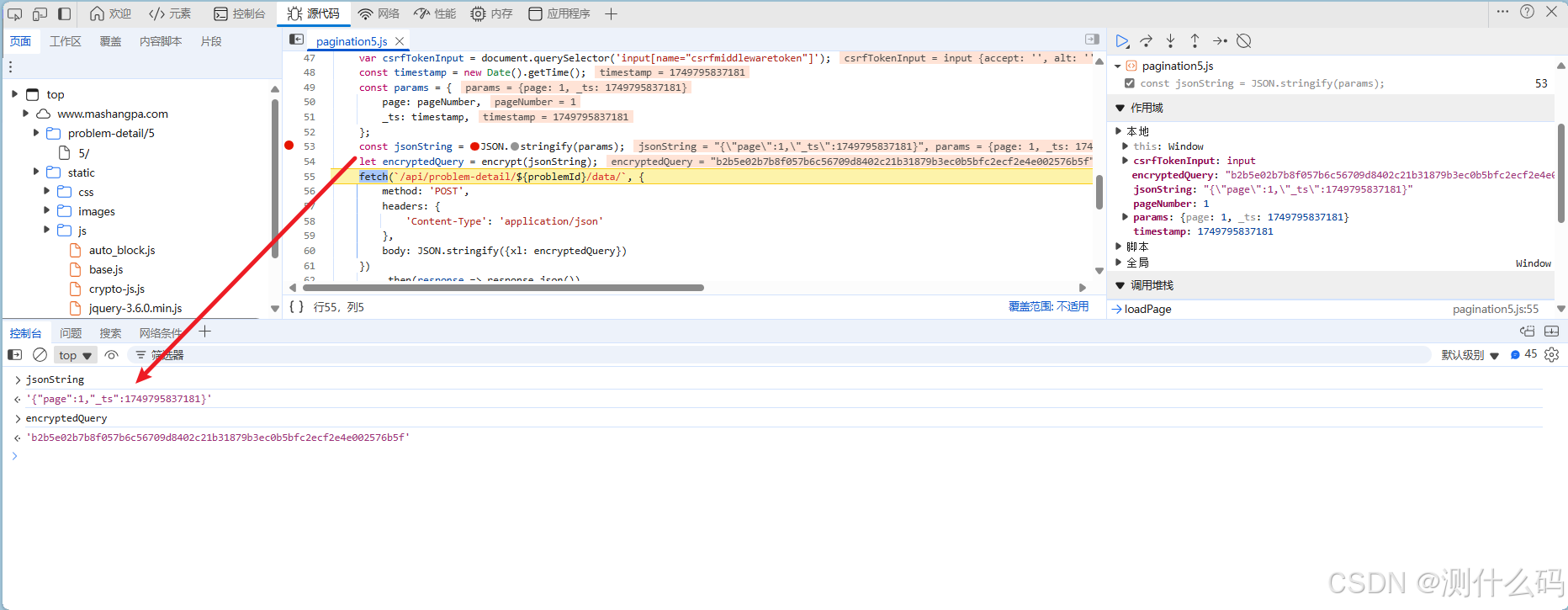
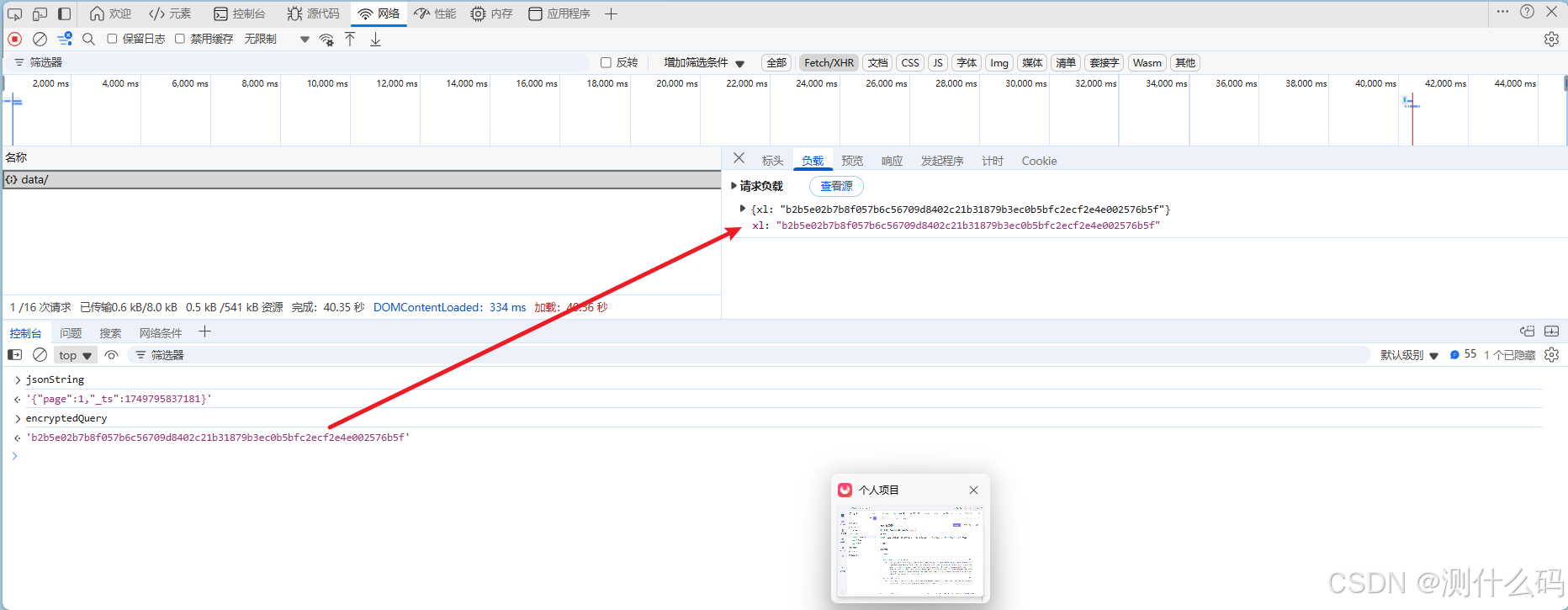
找到encrypt的加密函数的位置,经过ob混淆,AES算法+CBC模式+Pkcs7填充,可以通过解混淆更容易看出来。
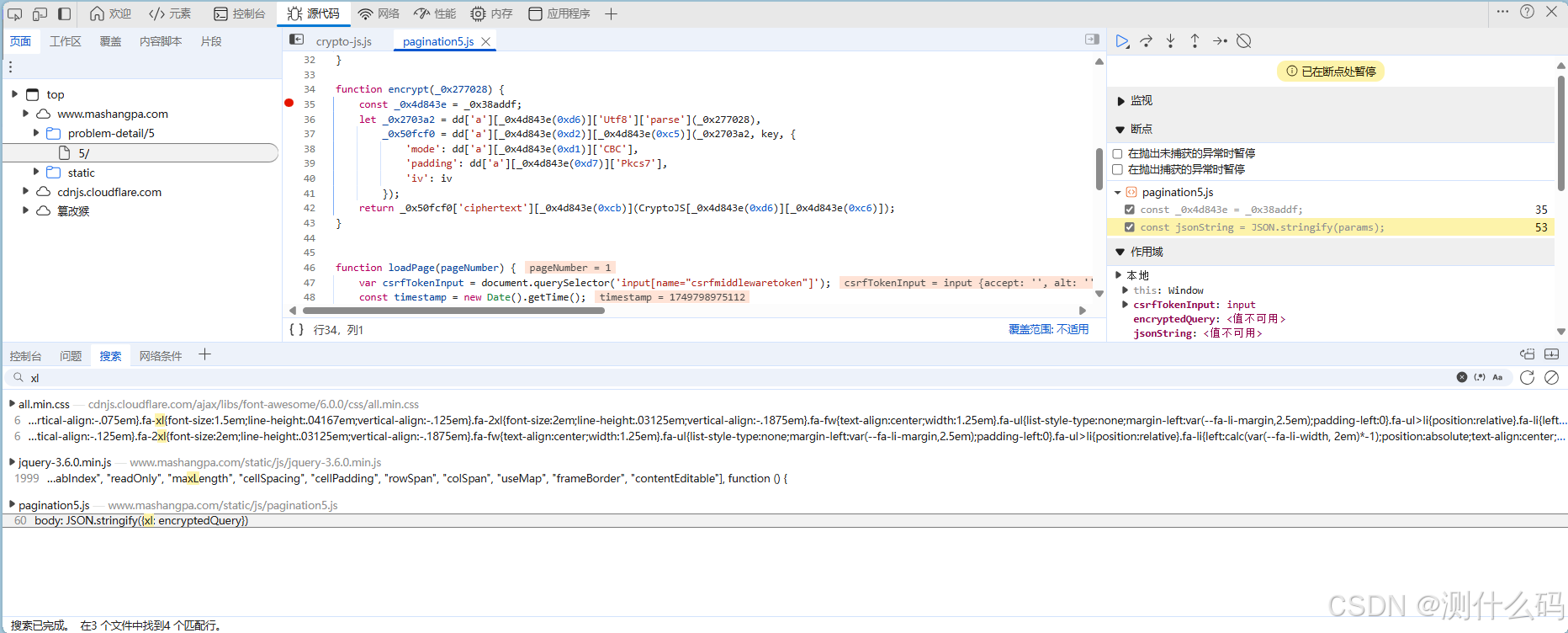
复制loadpage函数,以及加密的encrypt代码块到js文件中,使用execjs调用js文件,缺啥就找到对应的代码复制进来即可。
import execjs
import requests
headers = {
'User-Agent':'Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/137.0.0.0 Safari/537.36 Edg/137.0.0.0',
'referer':'https://www.mashangpa.com/problem-detail/5/'
}
# 需要登录,请先登录,获取cookie并完善参数
cookies = {
'xxx':'xxxx',
......
}
final_sum = 0
for page in range(1,21):
with open('./js/5.js', 'r', encoding='utf-8') as f:
js_code = f.read()
xl = execjs.compile(js_code).call('loadPage',page)
json_data = {
'xl':xl
}
response = requests.post('https://www.mashangpa.com/api/problem-detail/5/data/', headers=headers, cookies=cookies, json=json_data)
print(f"第{page}页数组:{response.json()['current_array']}")
final_sum += sum(response.json()['current_array'])
print(f"最终的和为: {final_sum}")
第六题
请求加密参数s和tt,找到对应js代码
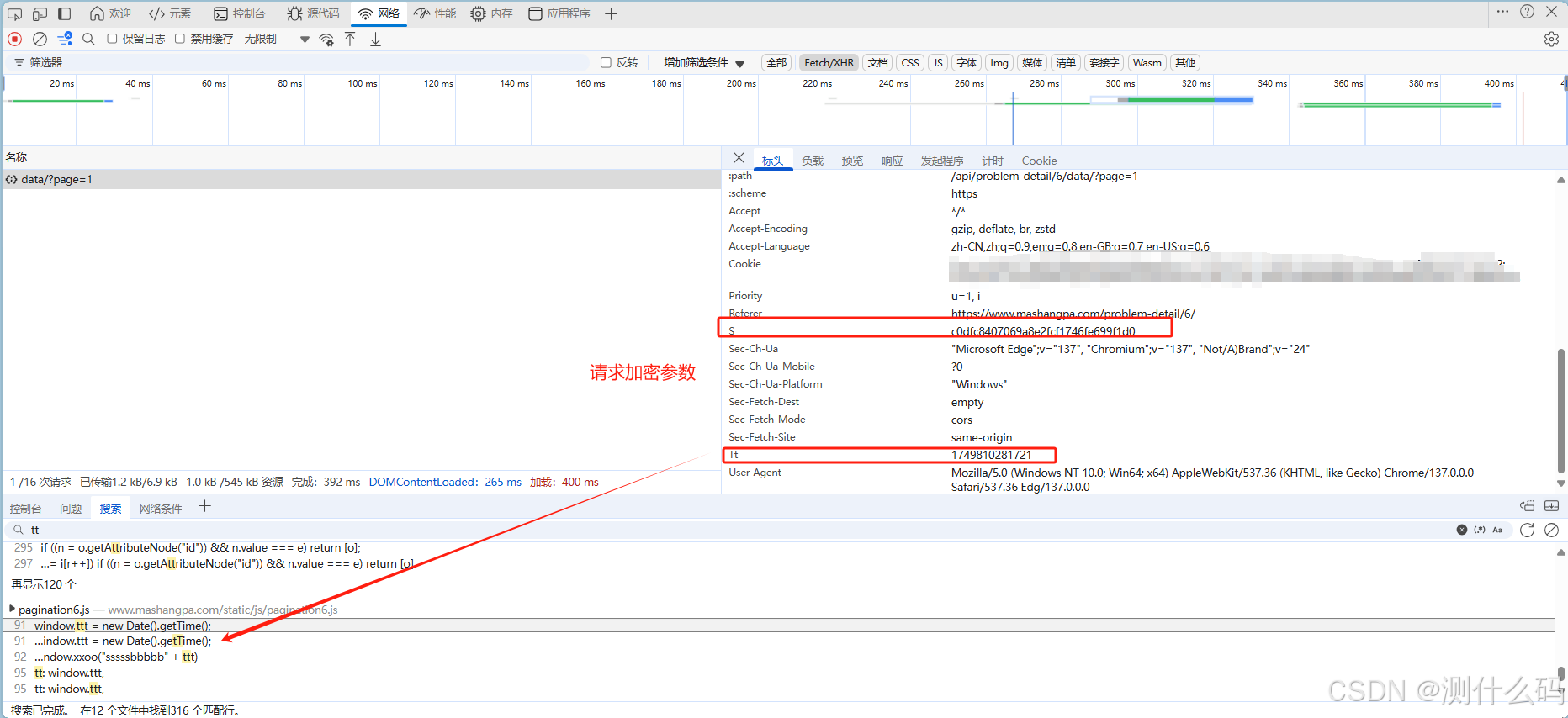
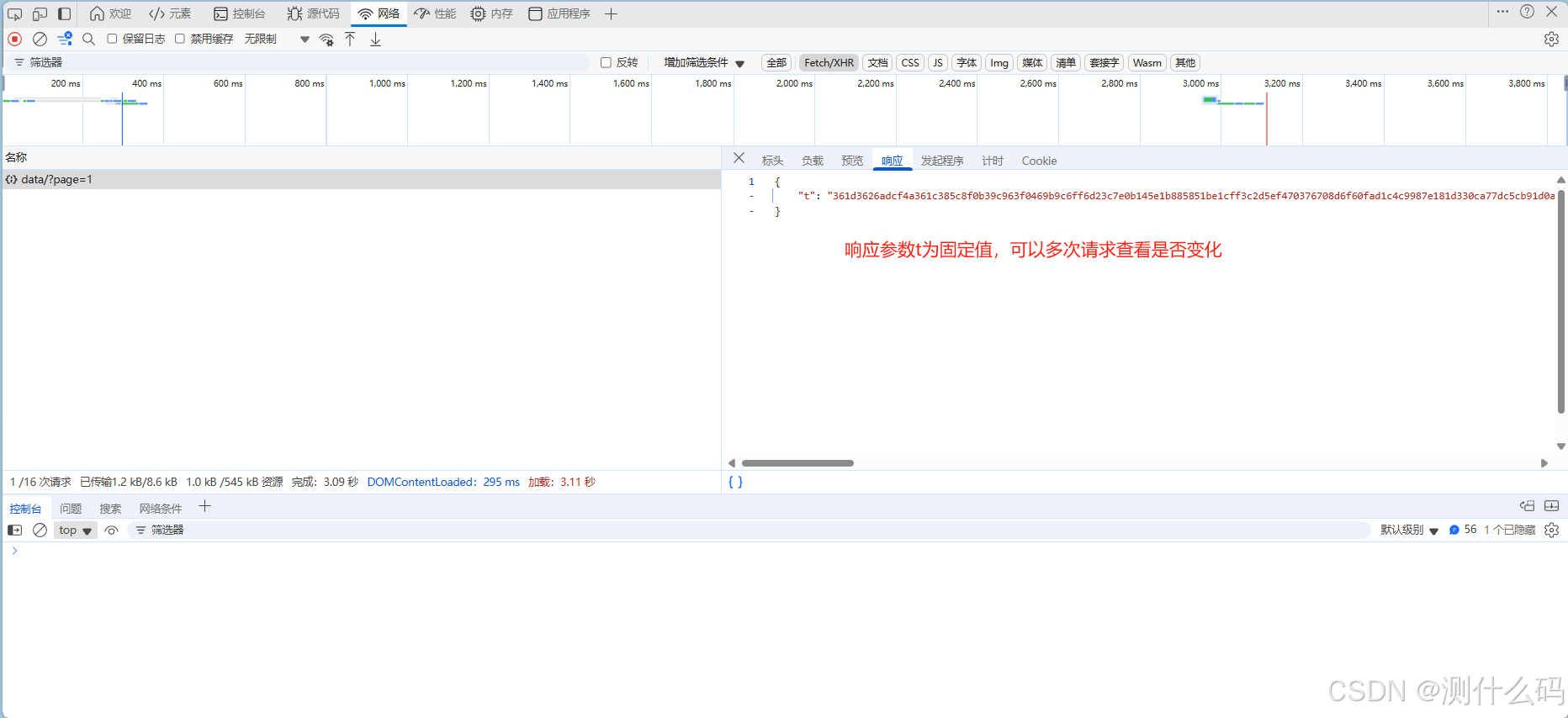
tt为13位时间戳,s为固定字符串+tt时间戳进行加密
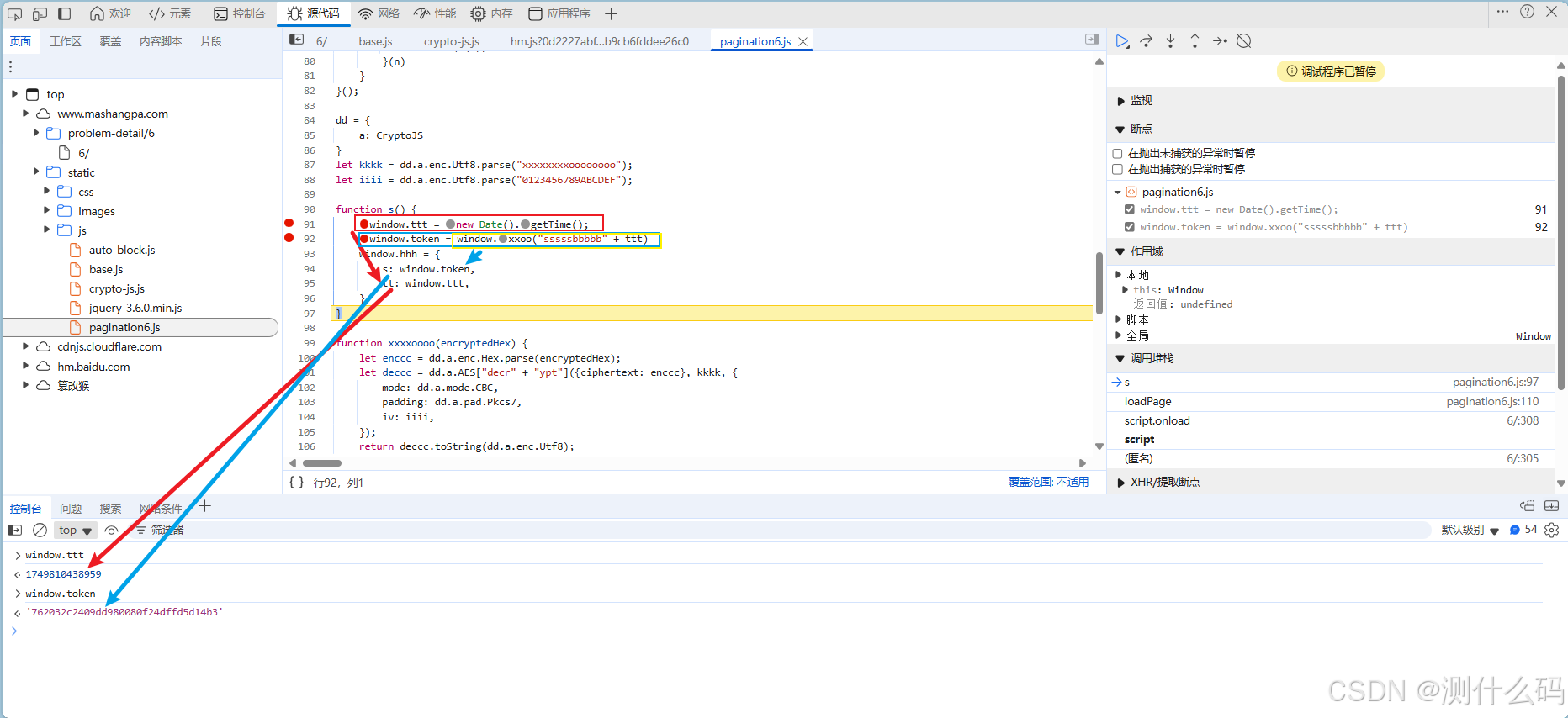
响应参数t固定值,调用的时候传入此参数即可
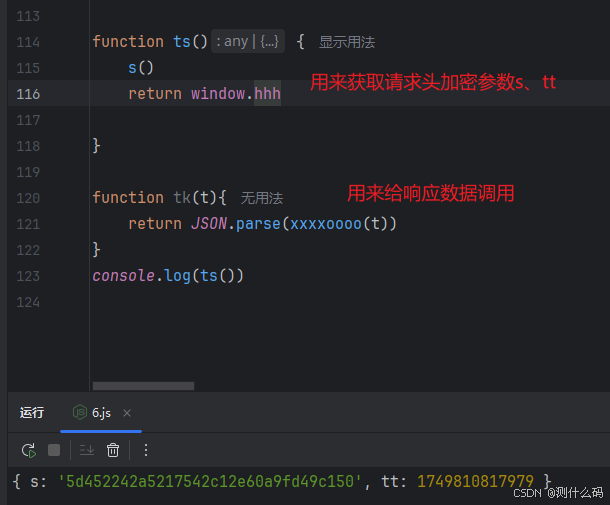
开始扣js文件,除了loadPage函数,其他都扣出来,使用console.log()调用函数输出测试一下
import json
import execjs
import requests
# 需要登录,请先登录,获取cookie并完善参数
cookies = {
'xxx':'xxxx',
......
}
var = 0
for i in range(1,21):
with open('./js/6.js', 'r', encoding='utf-8') as f:
js_code = f.read()
result = execjs.compile(js_code).call('loadPage')
print(result)
s = result['s']
tt = str(result['tt'])
headers = {
'User-Agent': 'Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/137.0.0.0 Safari/537.36 Edg/137.0.0.0',
'referer': 'https://www.mashangpa.com/problem-detail/6/',
'tt': tt,
's': s,
}
params = {
'page': i,
}
res =requests.get('https://www.mashangpa.com/api/problem-detail/6/data/',headers=headers, params=params, cookies=cookies)
data = res.json()['t']
val = execjs.compile(js_code).call('xxxxoooo', data)
#print(val)
val_json = json.loads(val)
print(val_json)
var += sum(val_json['current_array'])
print(f"和为:{var}")第七题
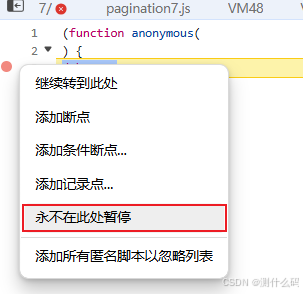
无限debugger,打开调试器后,等待跳转到debugger处,右击永远不在此处暂停即可跳过
查看请求头加密参数,发现有两个参数,一个加密参数M,一个时间戳Ts
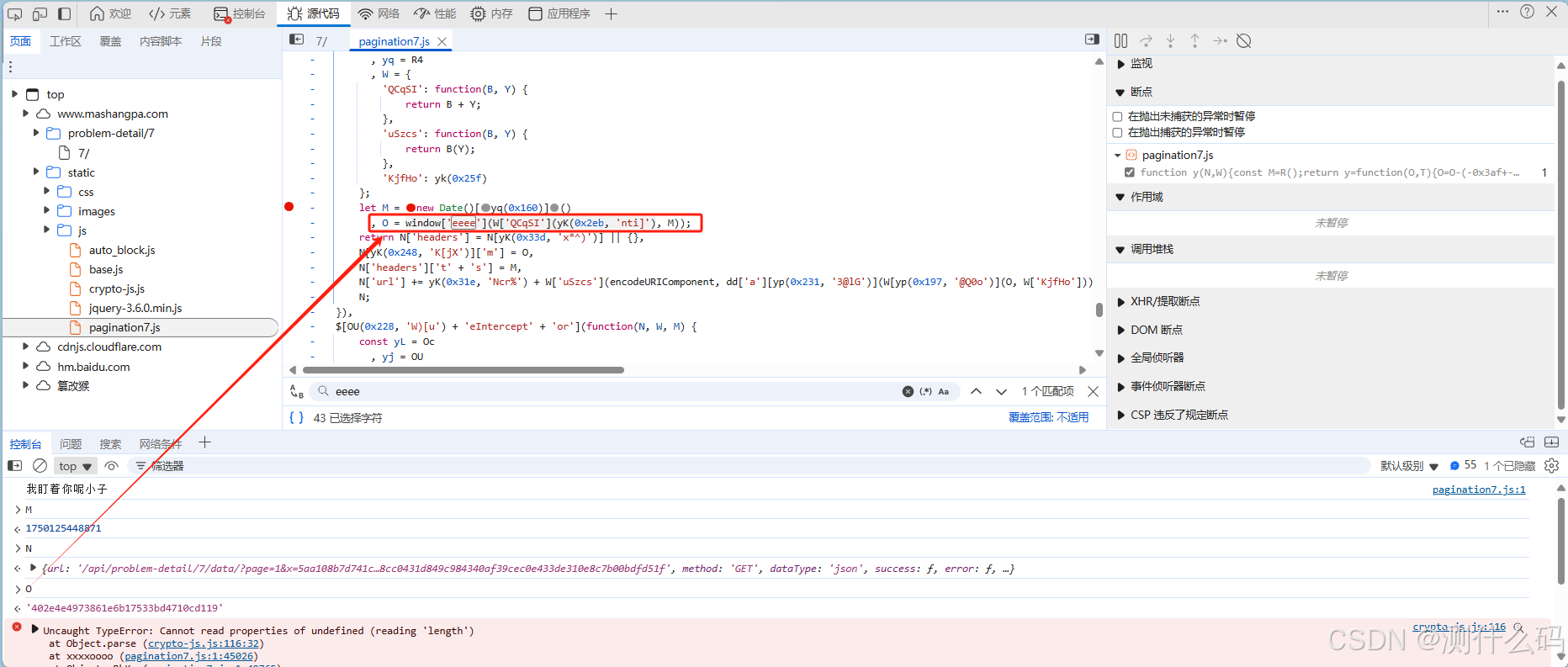
js代码中,实际M只是一个时间戳,O的值才是最终的请求头加密参数M的值
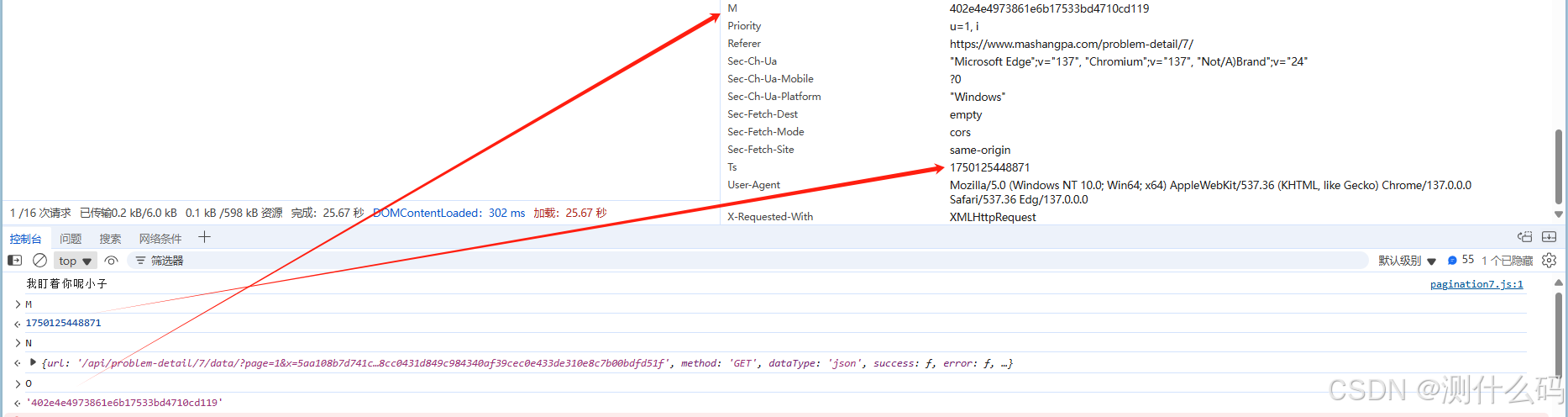
断点调试,发现把时间戳和字符进行拼接后进行MD5加密
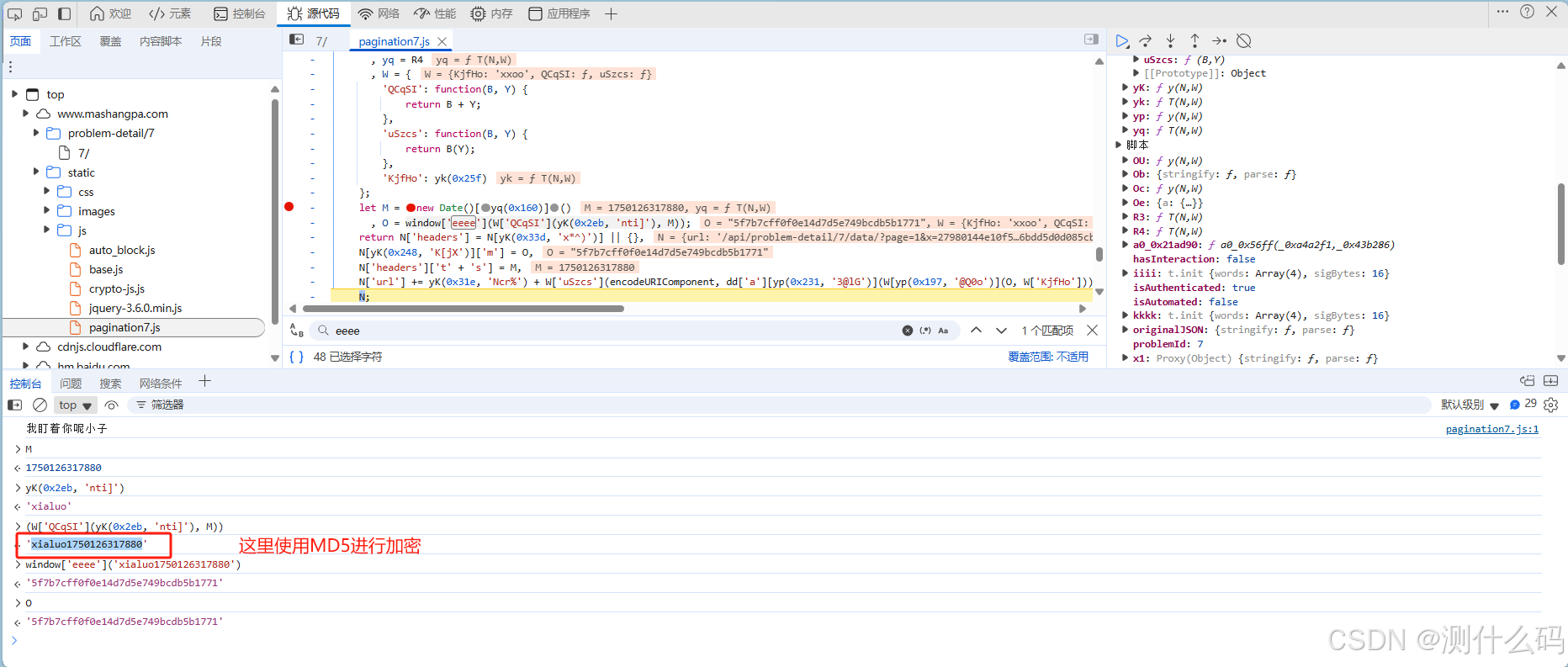
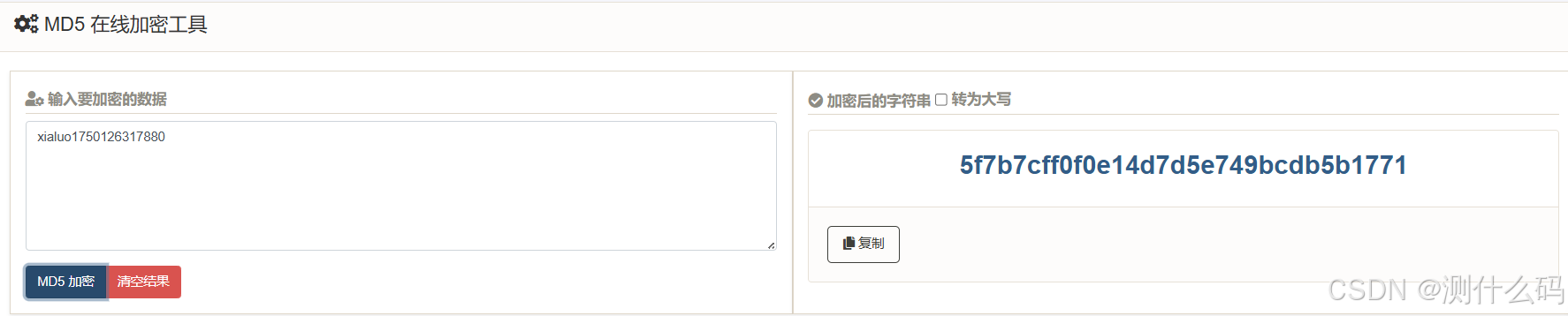
继续调试,请求负载中加密参数x,可知是由上方MD5加密值与固定字符拼接进行SHA256加密
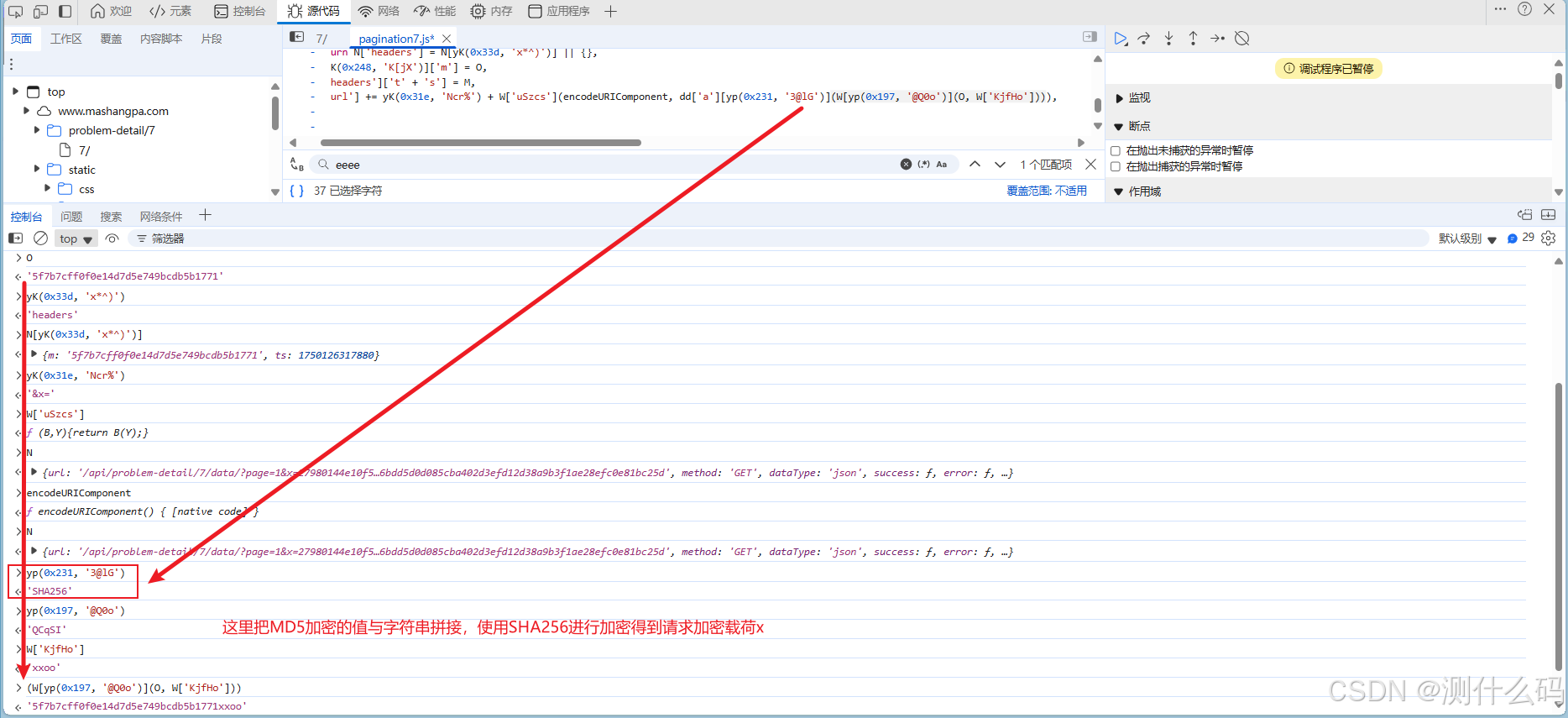
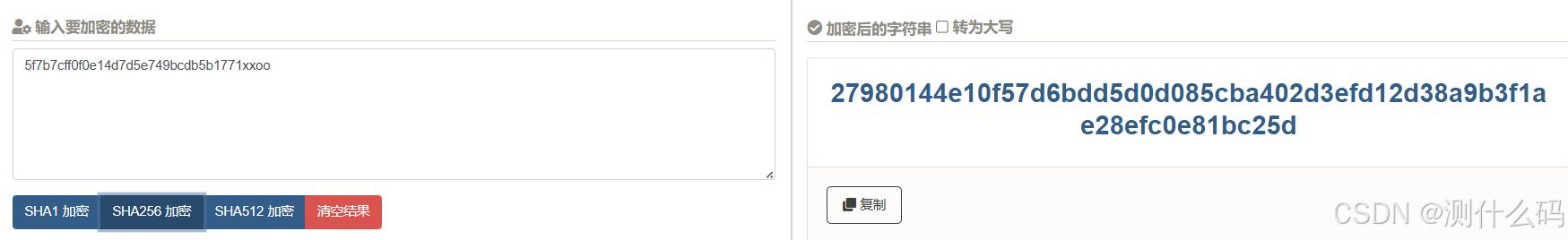
接下来找到响应加密参数r,根据上方得到的加密请求参数后可以得到
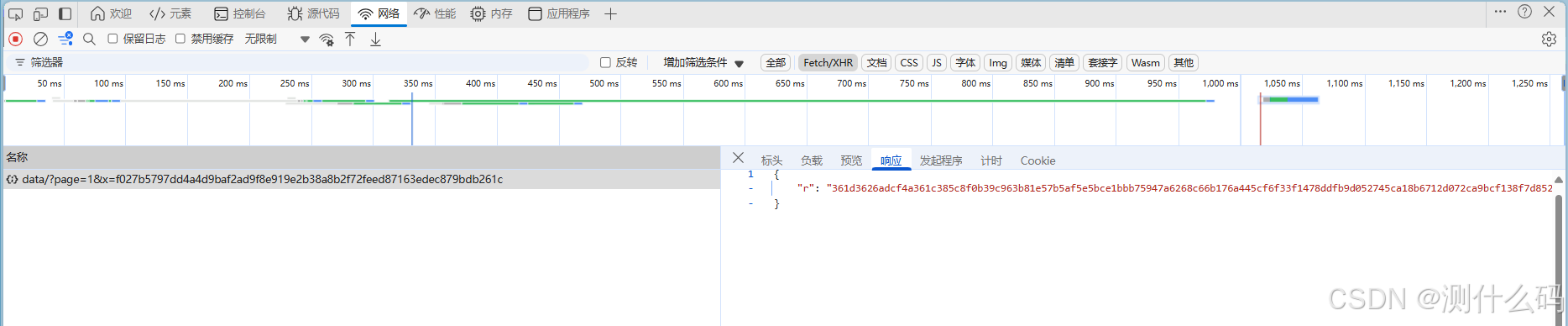
响应参数r通过oooxxx方法进行AES解密,ok,直接拿下
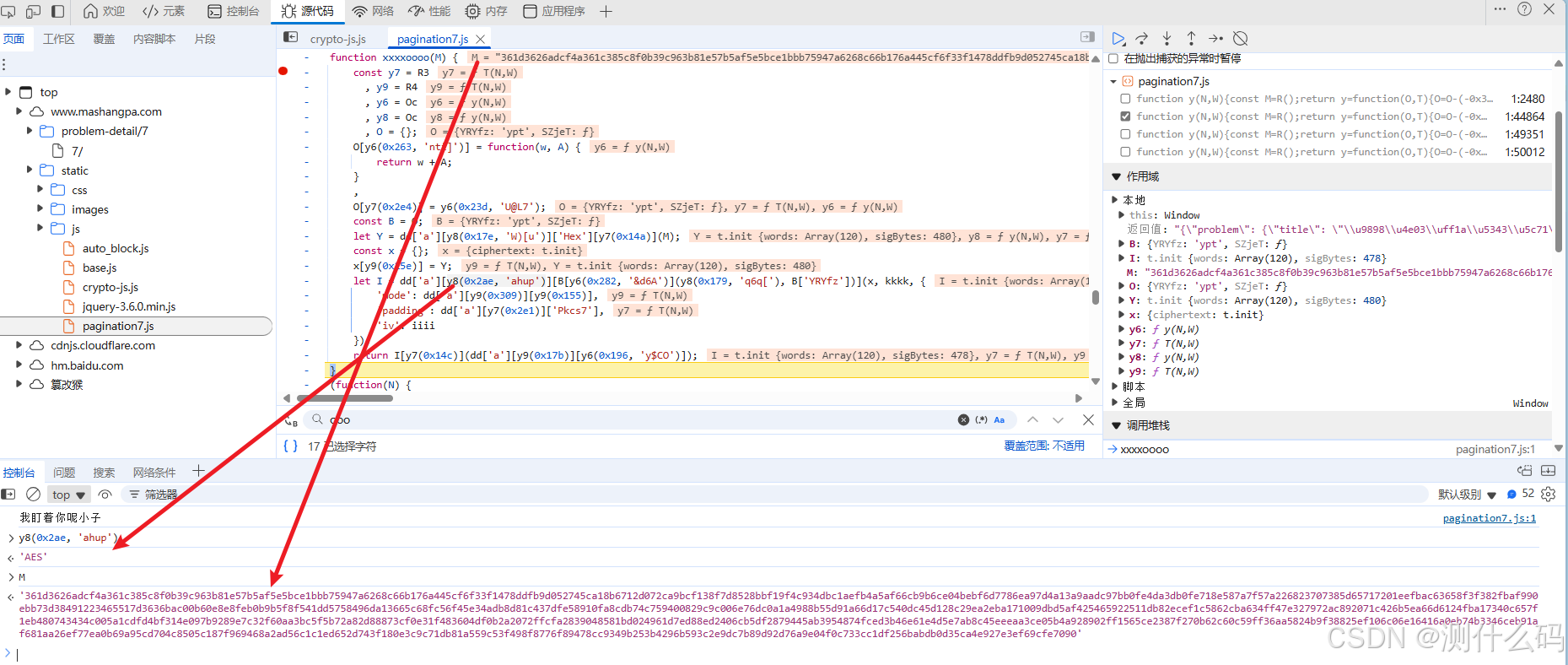 解密使用的key和iv也在上方定义,成功拿到。
解密使用的key和iv也在上方定义,成功拿到。
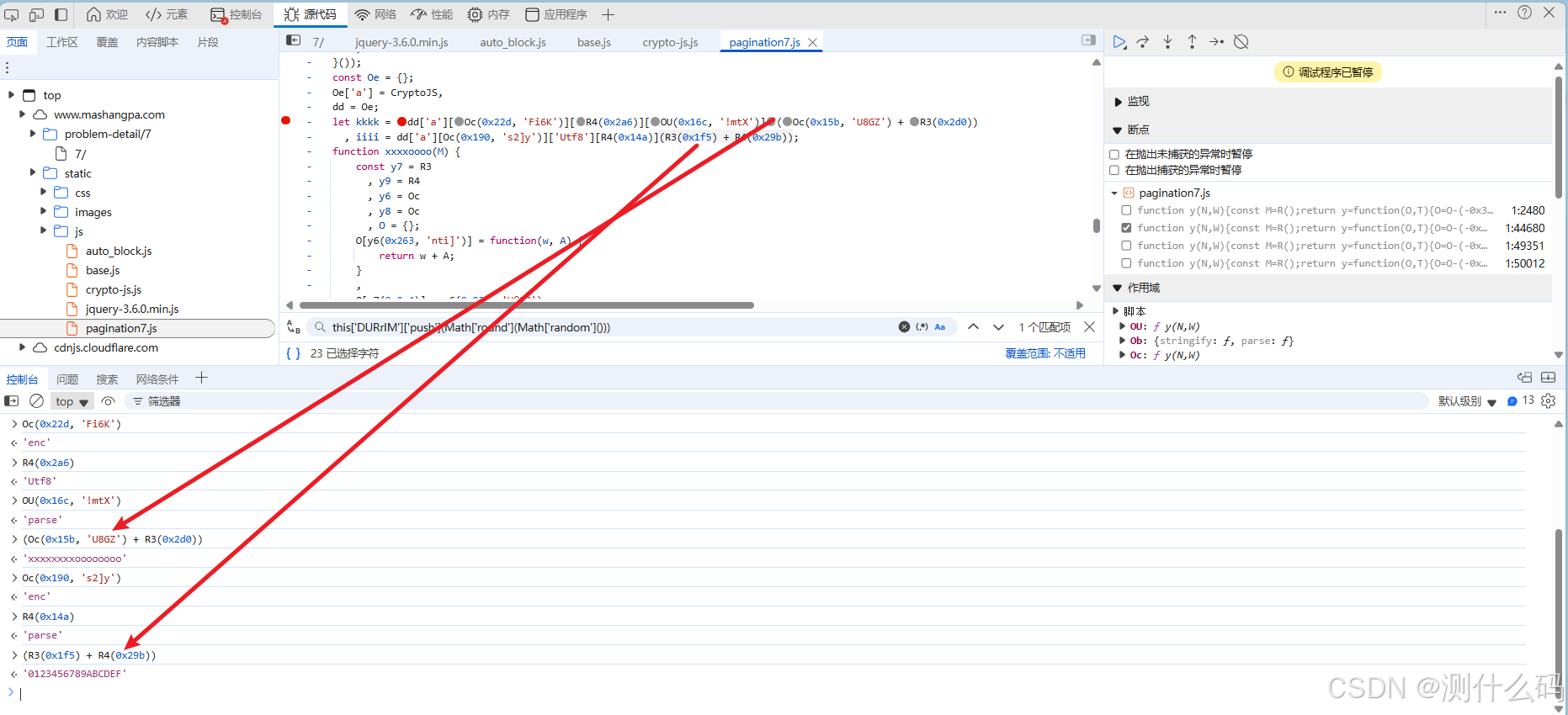
直接使用python代码模拟AES解密过程
import binascii
from hashlib import md5, sha256
import requests
import time
from Crypto.Cipher import AES
from Crypto.Util.Padding import unpad
import json
# 需要登录,请先登录,获取cookie并完善参数
cookies = {
'xxx':'xxxx',
......
}
def e(encry):
key = b'xxxxxxxxoooooooo'
iv = b'0123456789ABCDEF'
ciphertext = binascii.unhexlify(encry)
cipher = AES.new(key, AES.MODE_CBC, iv)
decrypted = cipher.decrypt(ciphertext)
plaintext = unpad(decrypted, AES.block_size)
return plaintext.decode()
final_sum = 0
for i in range(1, 21):
ts = str(int(time.time()) * 1000)
M_1 = 'xialuo' + ts
M = md5(M_1.encode()).hexdigest()
x_1 = str(M) + 'xxoo'
x = sha256(x_1.encode()).hexdigest()
url = f'https://www.mashangpa.com/api/problem-detail/7/data/?page={i}&x={x}'
headers = {
'User-Agent': 'Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/137.0.0.0 Safari/537.36 Edg/137.0.0.0',
'referer': 'https://www.mashangpa.com/problem-detail/7/',
'M': M,
'ts': ts
}
response = requests.get(url, headers=headers, cookies=cookies)
response.raise_for_status()
response.encoding = 'utf-8'
final_sum += sum(json.loads(e(response.json()['r']))['current_array'])
print(final_sum)第八题
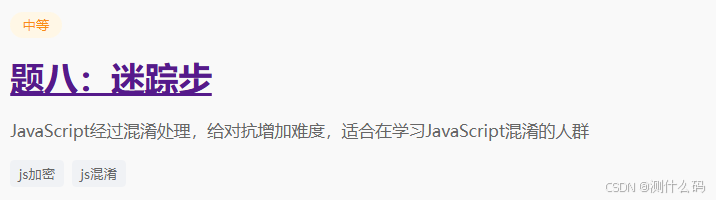
无限debugger,还是老方法,右击选择永不在此处暂停,查看请求参数中,有两个加密参数M和T,直接发现T是base64编码(最后有两个==,一般都是base64),这里使用 btoa 浏览器自带的方法进行base64编码。
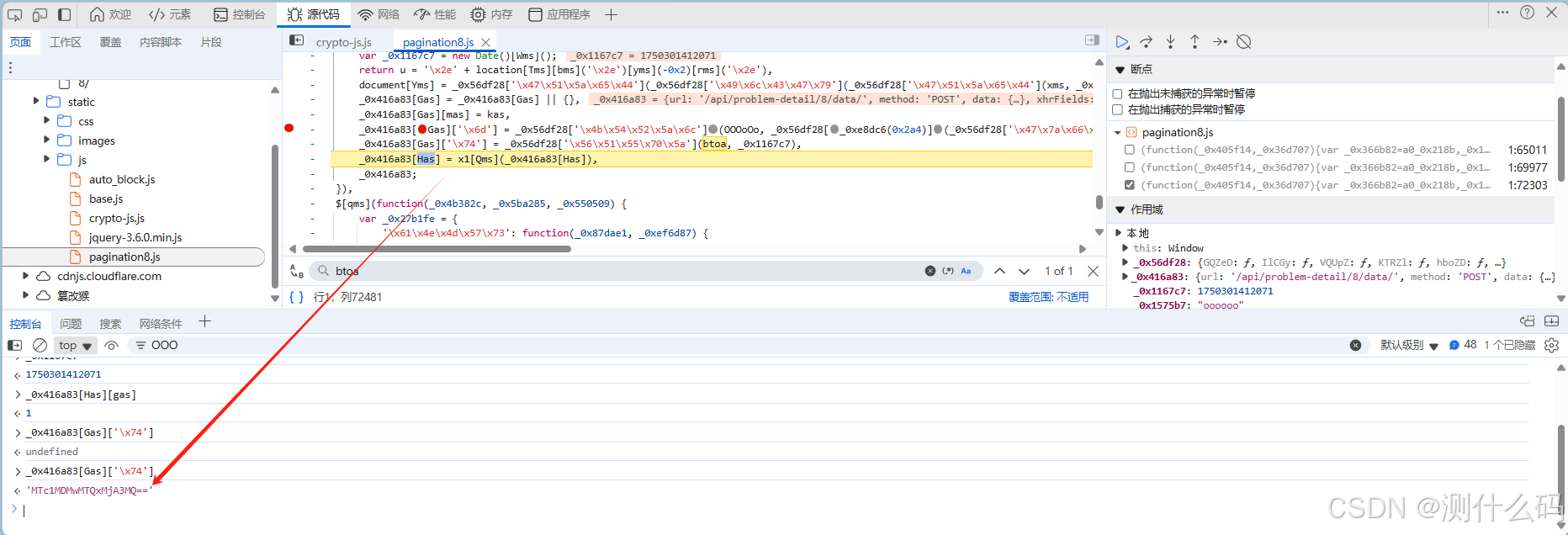
现在来解决加密参数M,M是由固定字符+time+page+固定字符,调用OOOoOo方法进行加密
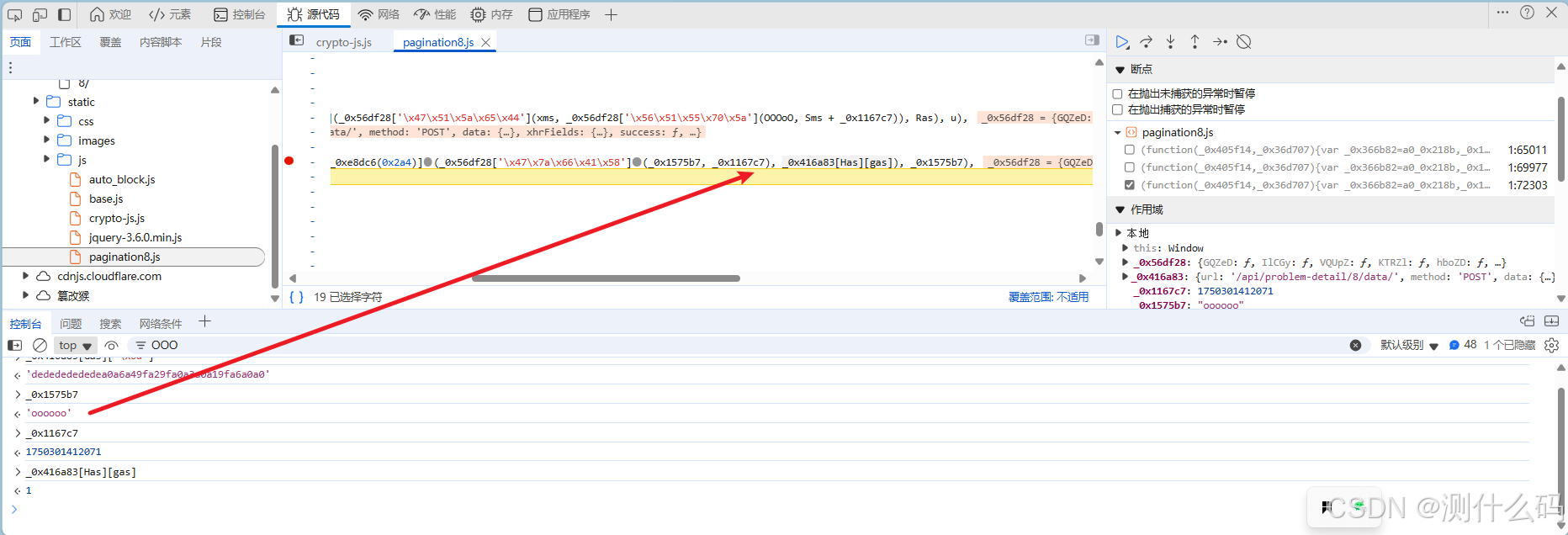
Cookie中还有一个参数s,s是由固定字符+time,调用OOOoO方法进行加密
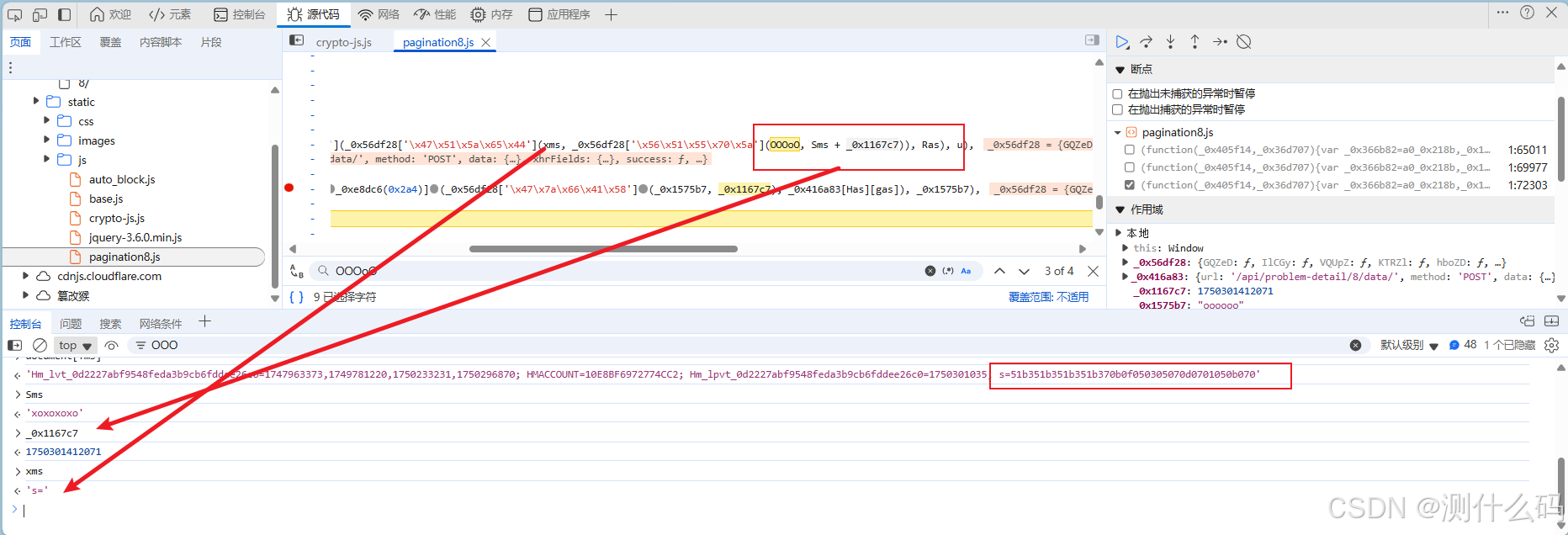
这里我们扣js代码,缺啥补啥,(用了半小时,终于扣完了^v^)
import execjs
import requests
import time
total_sum = 0
for i in range(1,21):
timestamp = str(int(time.time() * 1000))
with open('./js/8.js', 'r', encoding='utf-8') as f:
js_code = f.read()
data = execjs.compile(js_code).call('run',timestamp,i)
# 需要登录,请先登录,获取cookie并完善参数
cookies = {
'xxx':'xxxx',
......
's':xxx
}
headers = {
'M': data[0],
'referer': 'https://www.mashangpa.com/problem-detail/8/',
'T': data[1],
'user-agent': 'Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/137.0.0.0 Safari/537.36 Edg/137.0.0.0',
}
json_data = {
'page': i,
}
response = requests.post('https://www.mashangpa.com/api/problem-detail/8/data/', cookies=cookies, headers=headers,
json=json_data)
print(response.json())
total_sum += sum(response.json()['current_array'])
print(f"和为:{total_sum}")js部分核心代码
# js代码调用主方法,补全所有缺失的变量和方法(部分函数需要替换成对应的函数'\x57\x...')
function run(time,page) {
const T = btoa(time)
const m = OOOoOo(_0x1575b7 + time + page, _0x1575b7)
const s = xms + OOOoO(Sms + time)
return [m, T, s]
}
# 测试调用结果
console.log(run(time,6))第九题
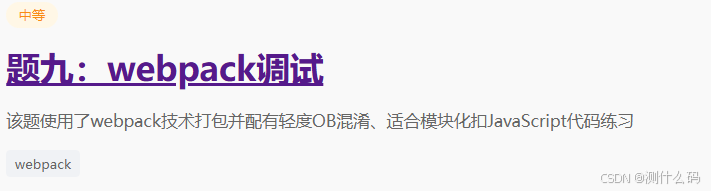
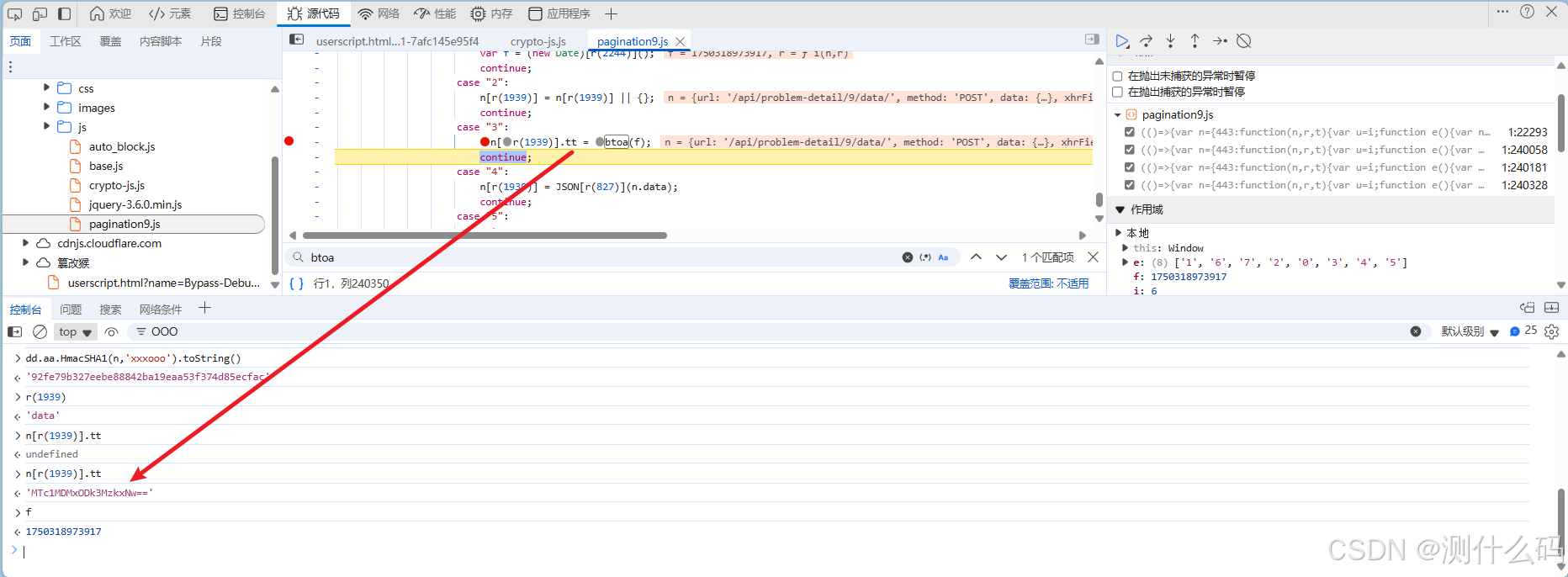
无限debugger,还是老方法,右击选择永不在此处暂停,查看请求参数中,有两个加密参数m和tt
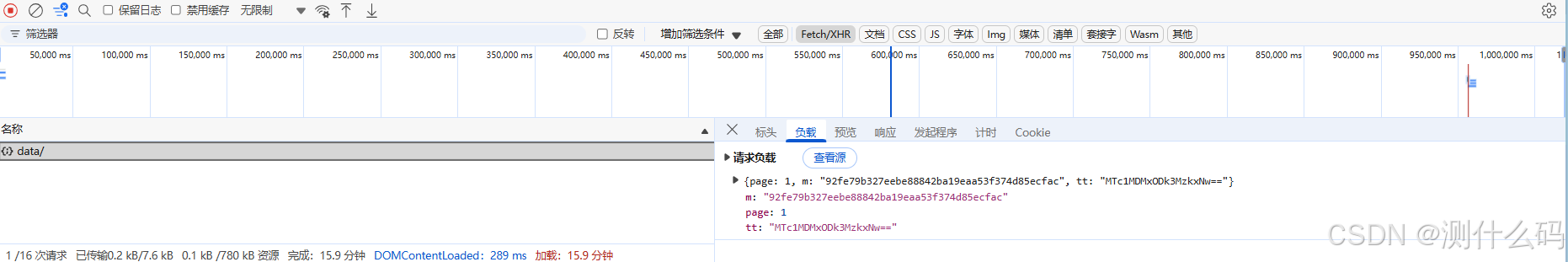
找到参数m的加密位置
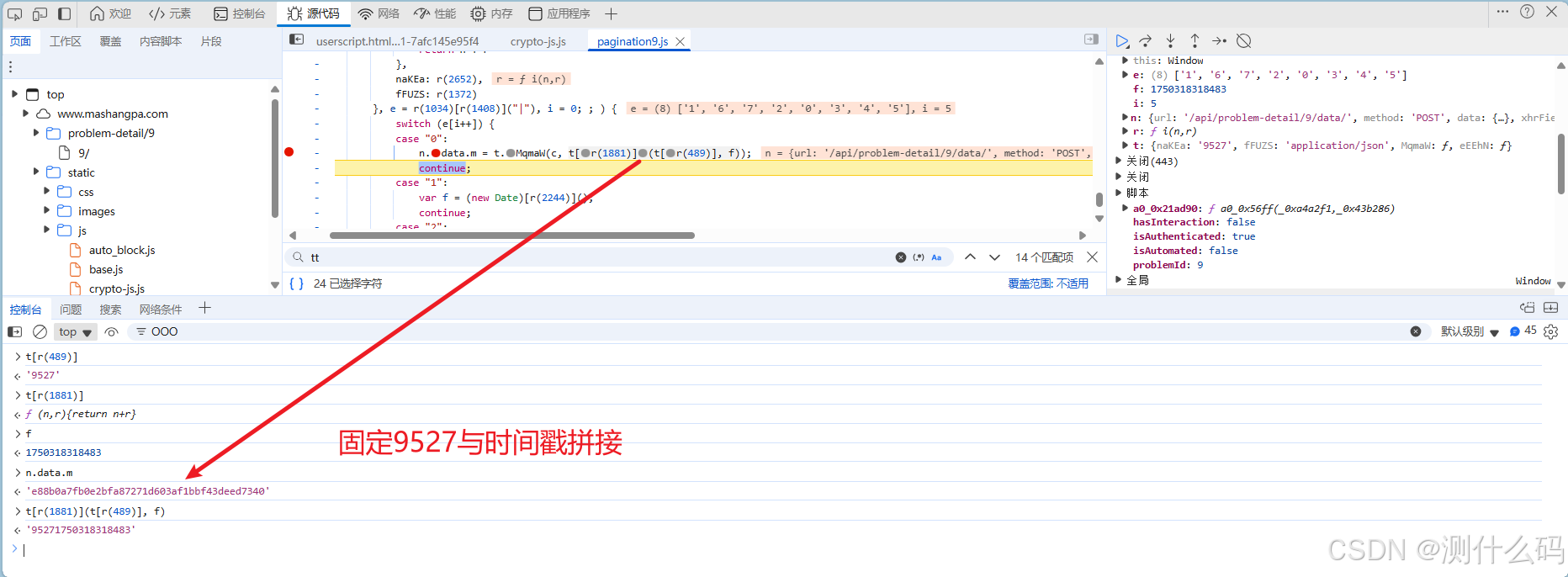
参数m,是由上方拼接后的值与‘xxxooo’进行HmacSHA1加密得到的
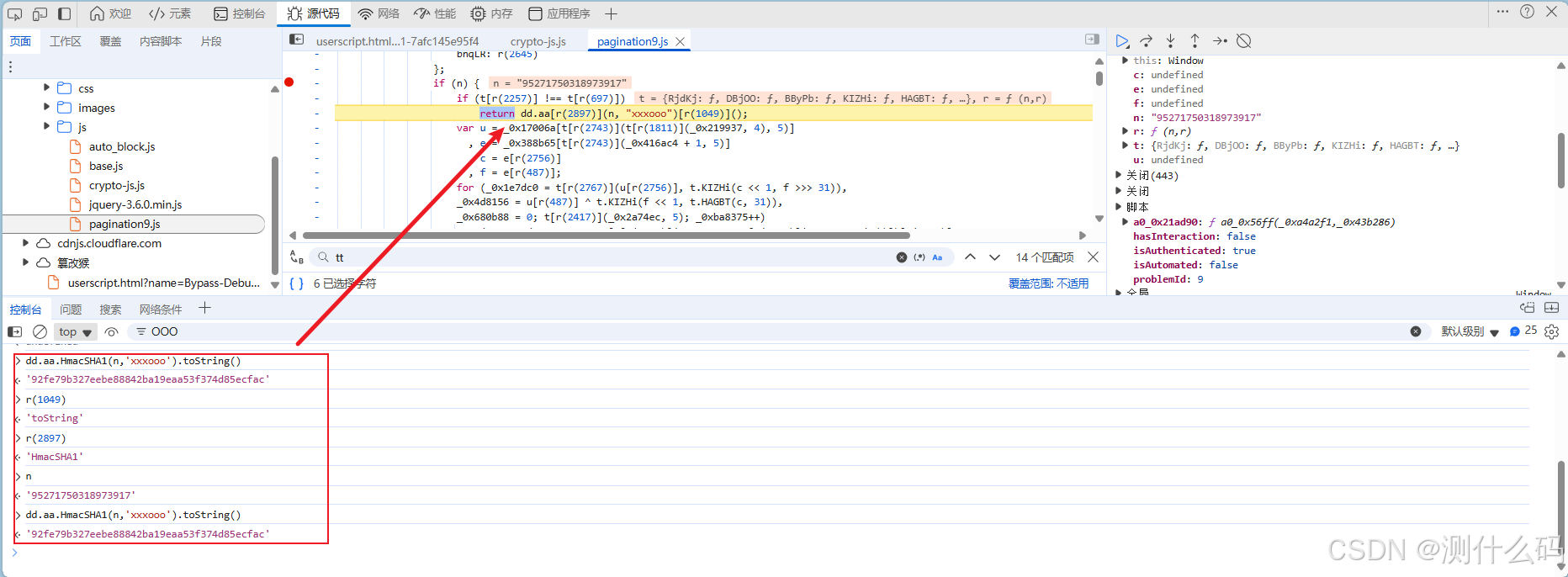 参数tt,对时间戳调用btoa方法进行的base64加密
参数tt,对时间戳调用btoa方法进行的base64加密
import execjs
import requests
total_sum = 0
for i in range(1,21):
with open('./js/9.js', 'r', encoding='utf-8') as f:
js_code = f.read()
data = execjs.compile(js_code).call('get')
m = data[0]
tt = data[1]
# 需要登录,请先登录,获取cookie并完善参数
cookies = {
'xxx':'xxxx',
......
}
headers = {
'referer': 'https://www.mashangpa.com/problem-detail/9/',
'user-agent': 'Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/137.0.0.0 Safari/537.36 Edg/137.0.0.0',
}
json_data = {
'page': i,
'm': m,
'tt': tt
}
response = requests.post('https://www.mashangpa.com/api/problem-detail/9/data/', cookies=cookies, headers=headers,
json=json_data)
print(response.json())
total_sum += sum(response.json()['current_array'])
print(f"和为:{total_sum}")第十题
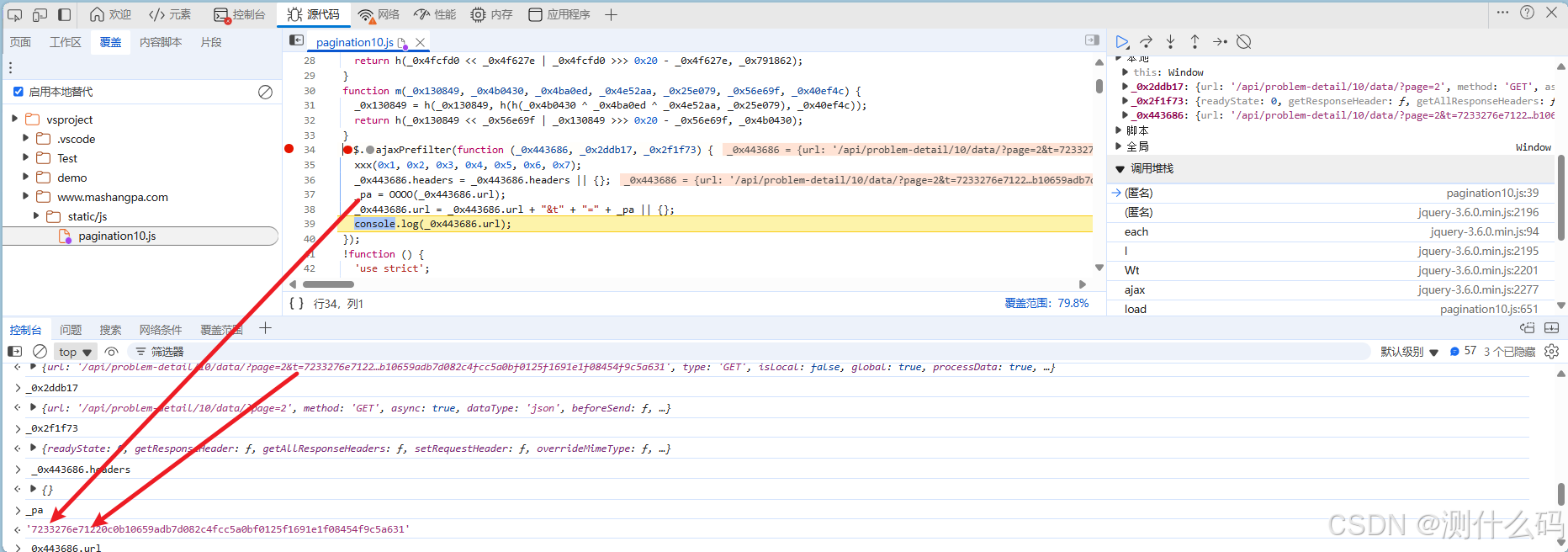
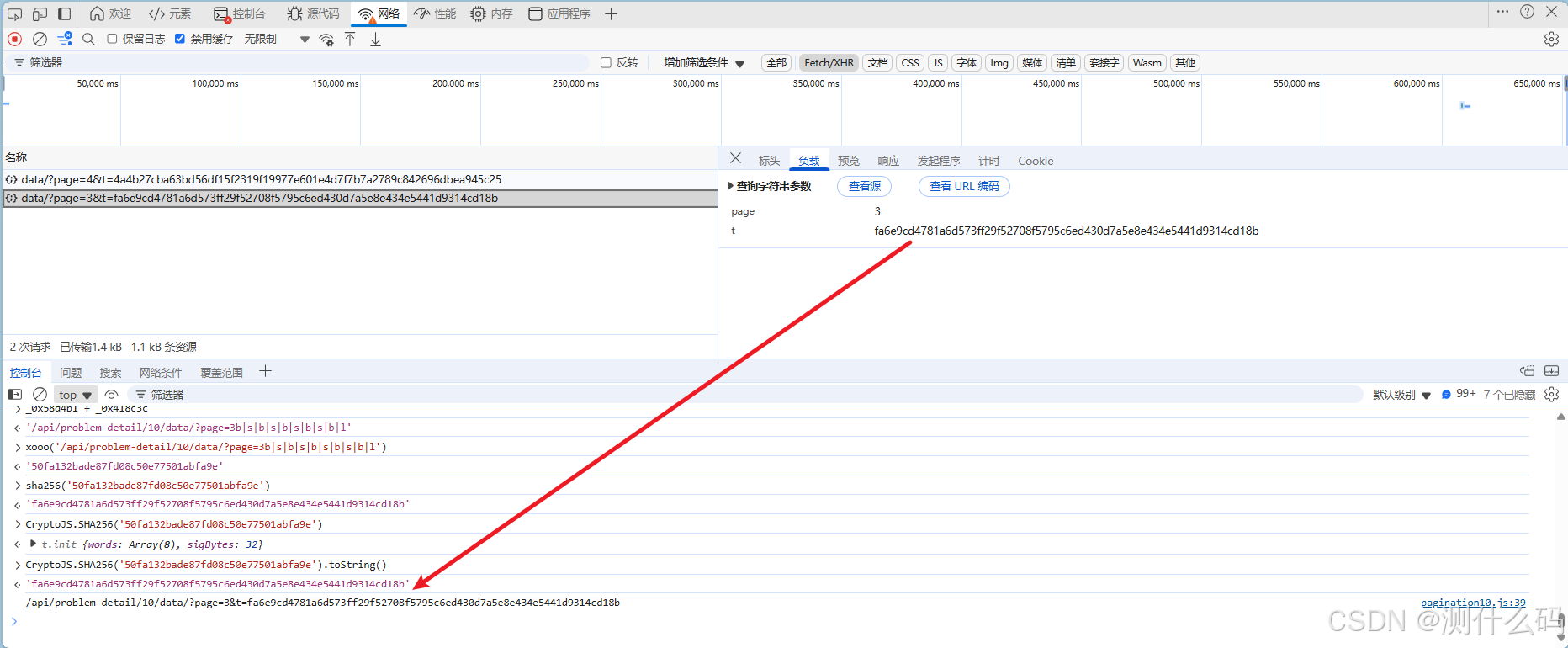
老样子,跳过无限debugger,然后查看请求参数,发现page和加密参数t,需要找到t的加密逻辑,这里我们对js文件进行解密,并替换,进行断点调试,发现_pa的值就是这个加密参数t
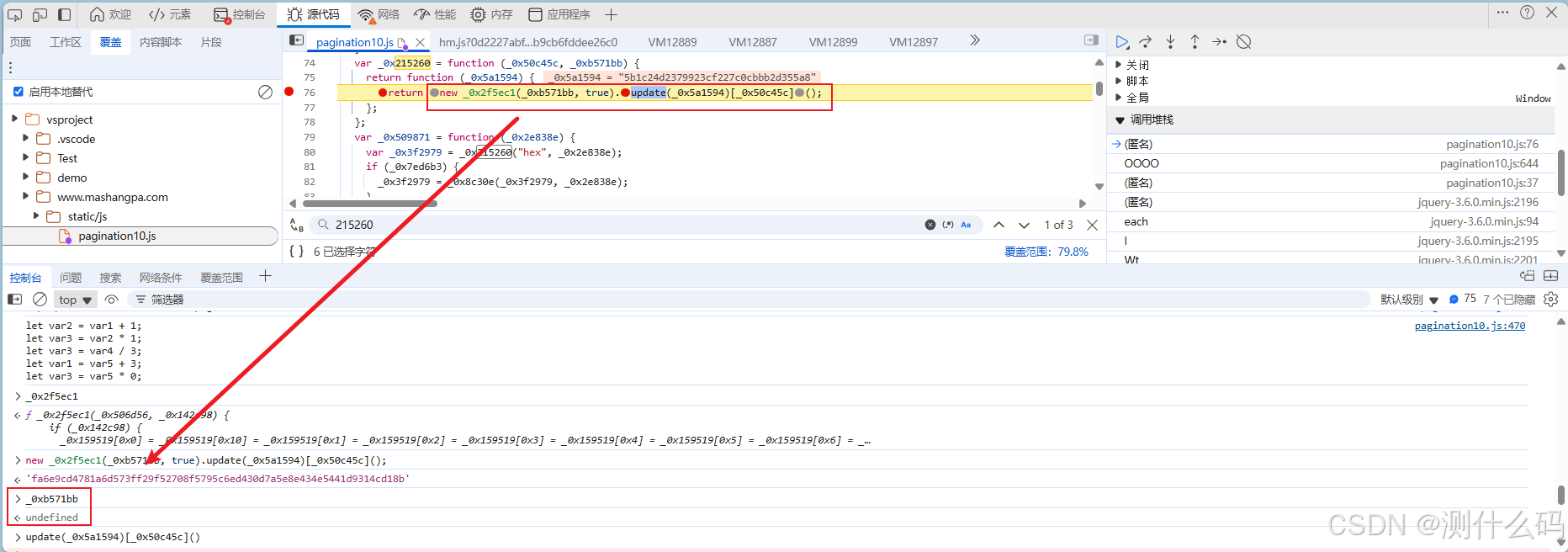
开始扣js代码,缺啥补啥扣到最后会发现确缺少一个sha256的方法,这里我们定位到此处,发现加密参数t最终是通过此处返回的
因为此题为魔改,所以这个sha256方法也无法正常找到,尝试找到sha256加密的函数位置
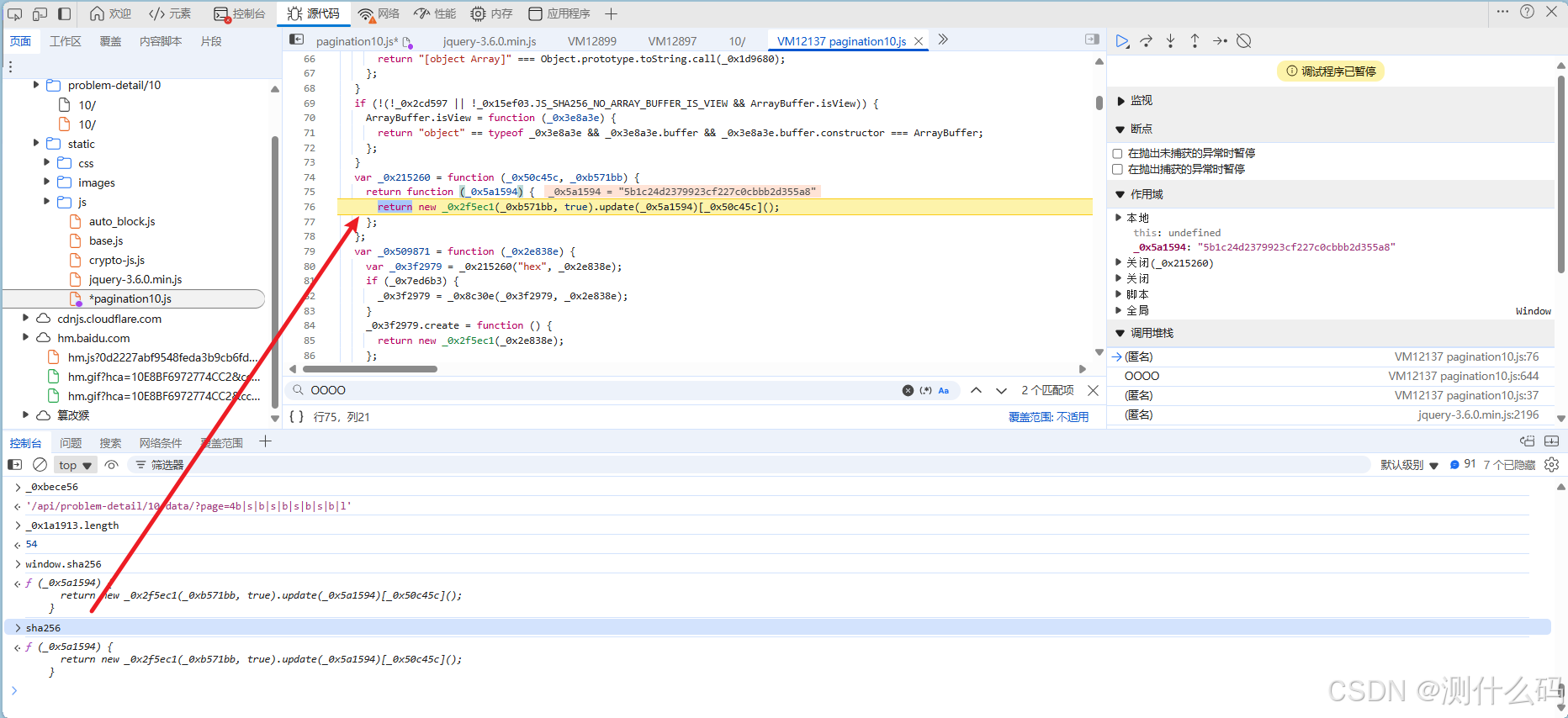
这里发现魔改的加密和CryptoJS加密结果是一致的,我们直接在解混淆后的hoo方法中返回加密后的参数t即可,每页的t都是固定的,可以多次断点调试来验证。
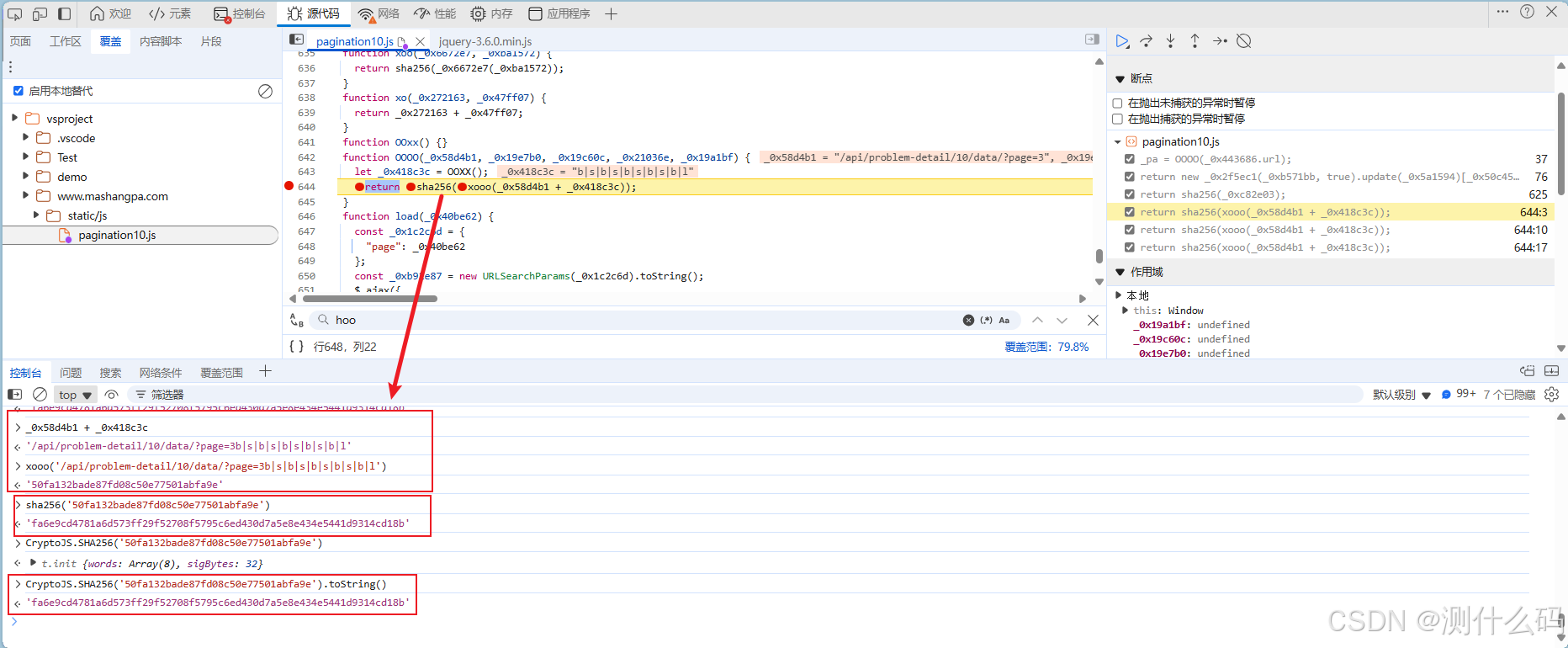
模拟加密过程与最终加密参数t是一致的,说明过程正确。
import execjs
import requests
# 需要登录,请先登录,获取cookie并完善参数
cookies = {
'xxx':'xxxx',
......
}
headers = {
'referer': 'https://www.mashangpa.com/problem-detail/10/',
'user-agent': 'Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/137.0.0.0 Safari/537.36 Edg/137.0.0.0',
}
total_sum = 0
with open('./js/10.js', 'r', encoding='utf-8') as f:
ctx = execjs.compile(f.read())
for i in range(1, 21):
t = ctx.call('get', i)
print(t)
url = f'https://www.mashangpa.com/api/problem-detail/10/data/?page={i}&t={t}'
response = requests.get(url, cookies=cookies, headers=headers)
print(response.json()['current_array'])
total_sum += sum(response.json()['current_array'])
print(f"和为:{total_sum}")
第十一题
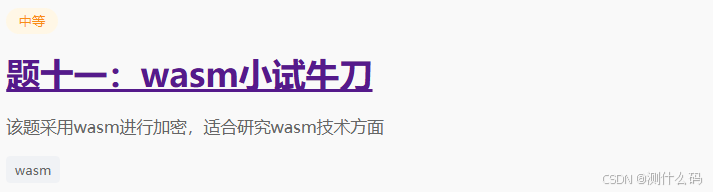
无限debugger,老方法进行跳过,发现请求负载中有两个加密参数m和_ts,其中_ts是时间戳,这里需要找到m的加密逻辑。
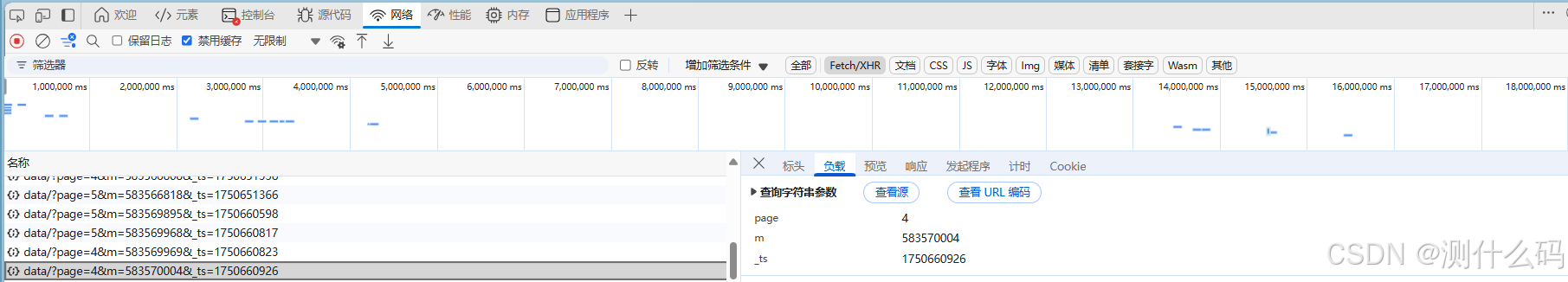
这里可以发现,最终的m参数是由f得来的,而f通过调用了一个方法进行加密,参数c和e分别是当前page和时间戳。
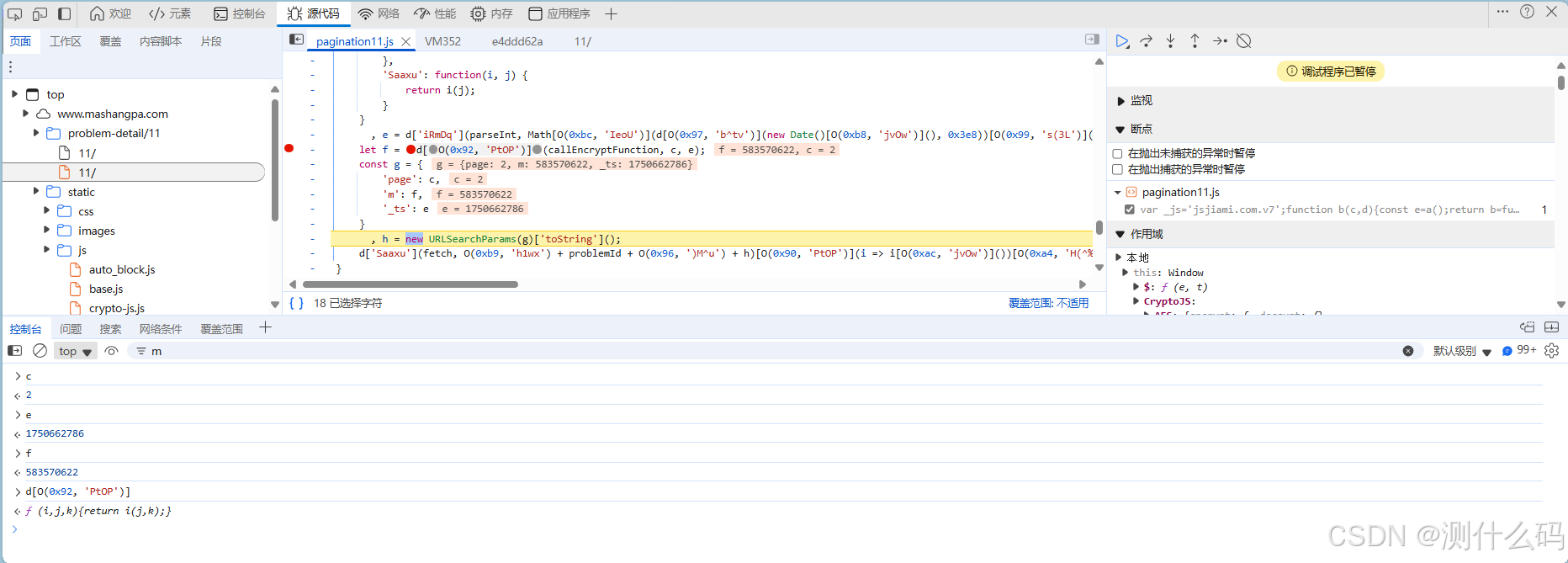
开始扣js代码,补齐相关函数方法,此处的加密是wasm
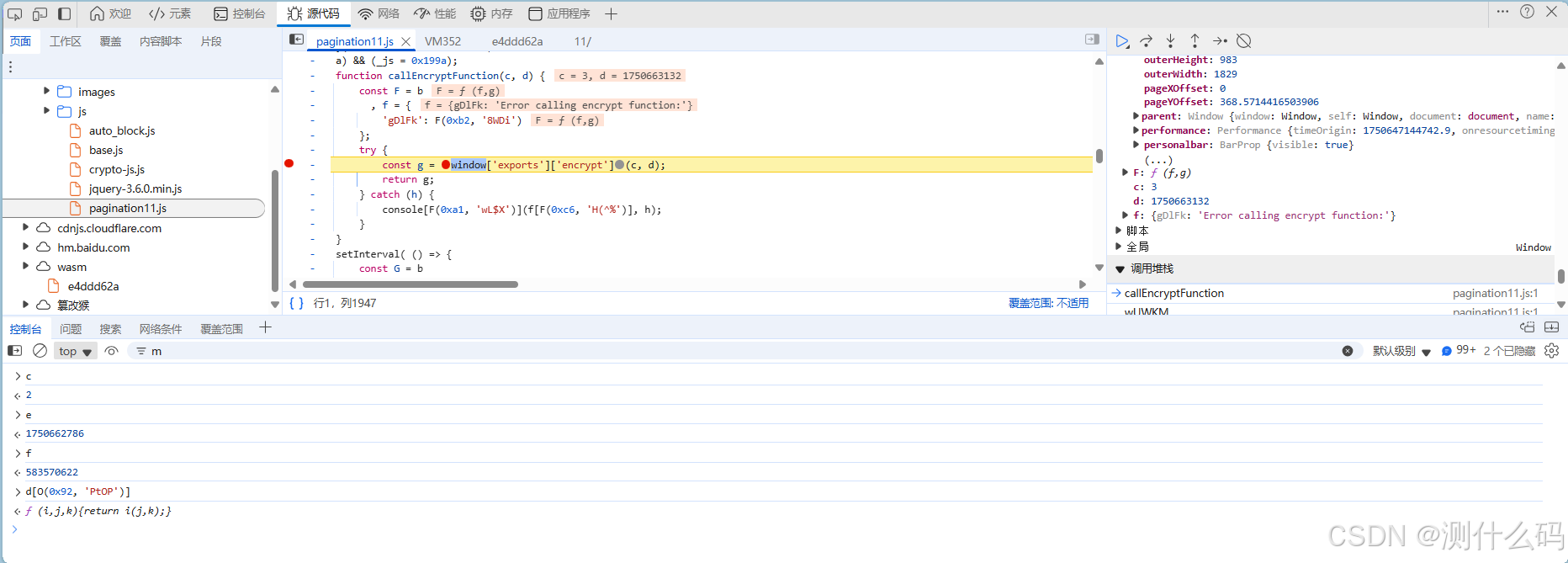
如下,转换成js代码就是:两个参数,此一个参数为page,第二个为时间戳,[page + 时间戳/3)+ 16358] ,直接定义一个加密方法,时间此计算逻辑即可。
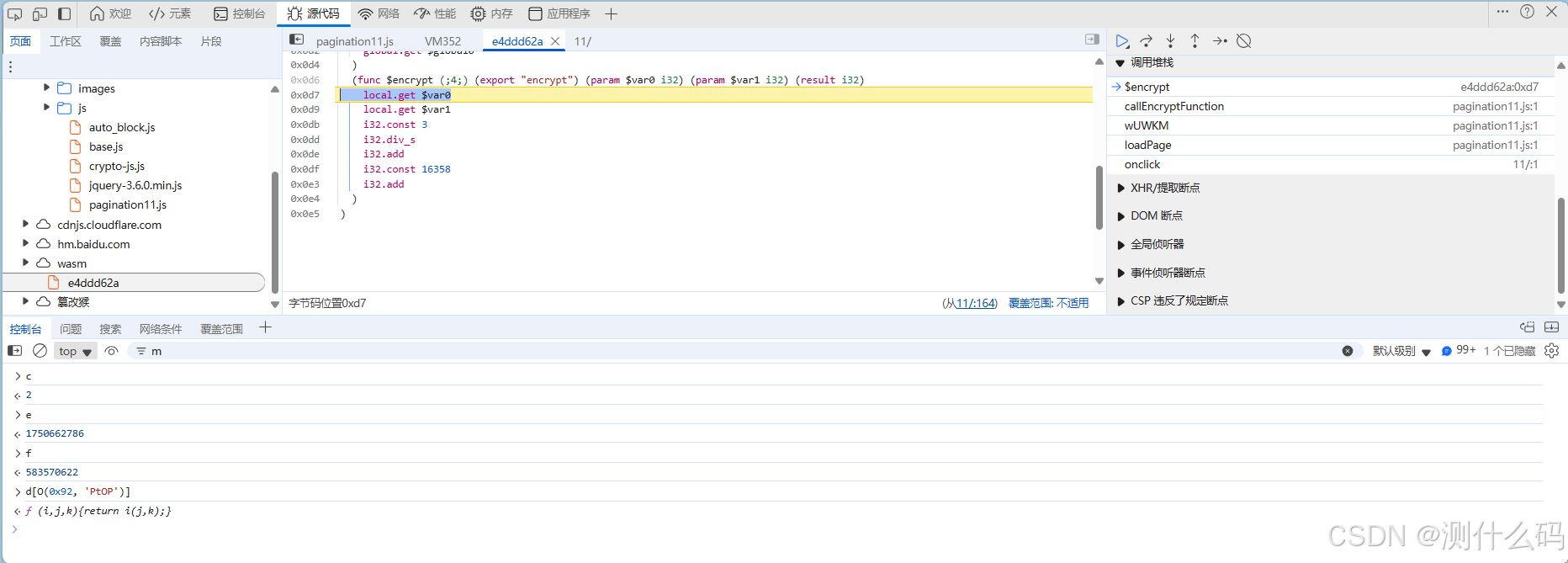
import time
import execjs
import requests
# 需要登录,请先登录,获取cookie并完善参数
cookies = {
'xxx':'xxxx',
......
}
headers = {
'referer': 'https://www.mashangpa.com/problem-detail/11/',
'user-agent': 'Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/137.0.0.0 Safari/537.36 Edg/137.0.0.0',
}
total_sum = 0
with open('./js/11.js', 'r', encoding='utf-8') as f:
ctx = execjs.compile(f.read())
for i in range(1, 21):
t = int(time.time())
print(t)
m = ctx.call('callEncryptFunction', i,t)
print(m)
url = f'https://www.mashangpa.com/api/problem-detail/11/data/?page={i}&m={m}&_ts={t}'
response = requests.get(url, cookies=cookies, headers=headers)
print(response.json()['current_array'])
total_sum += sum(response.json()['current_array'])
print(f"和为:{total_sum}")第十二题
全扣js代码,定义方法调用loadpage方法,定义js自吐环境以及代理器,运行js文件调试,增加原型链依赖。这里可能需要结合canvas,注意$未找到,需要定义。
import time
import execjs
import requests
cookies = {
xxxxx
}
headers = {
'referer': 'https://www.mashangpa.com/problem-detail/12/',
'user-agent': 'Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/137.0.0.0 Safari/537.36 Edg/137.0.0.0',
}
total_sum = 0
for i in range(20, 21):
t = int(time.time())
with open('./js/12.js', 'r', encoding='utf-8') as f:
ctx = execjs.compile(f.read())
uri = ctx.call('get', i)
url = 'https://www.mashangpa.com'+ uri
print(url)
response = requests.get(url, cookies=cookies, headers=headers)
print(response.json()['current_array'])
total_sum += sum(response.json()['current_array'])
print(total_sum)
print(f"和为:{total_sum}")
第十三题
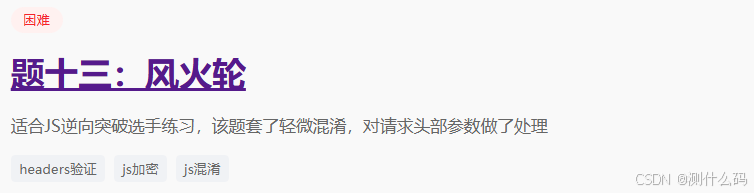
无限debugger,老方法跳过,查看请求参数中有三个参数,加密参数R和S,T为时间戳。
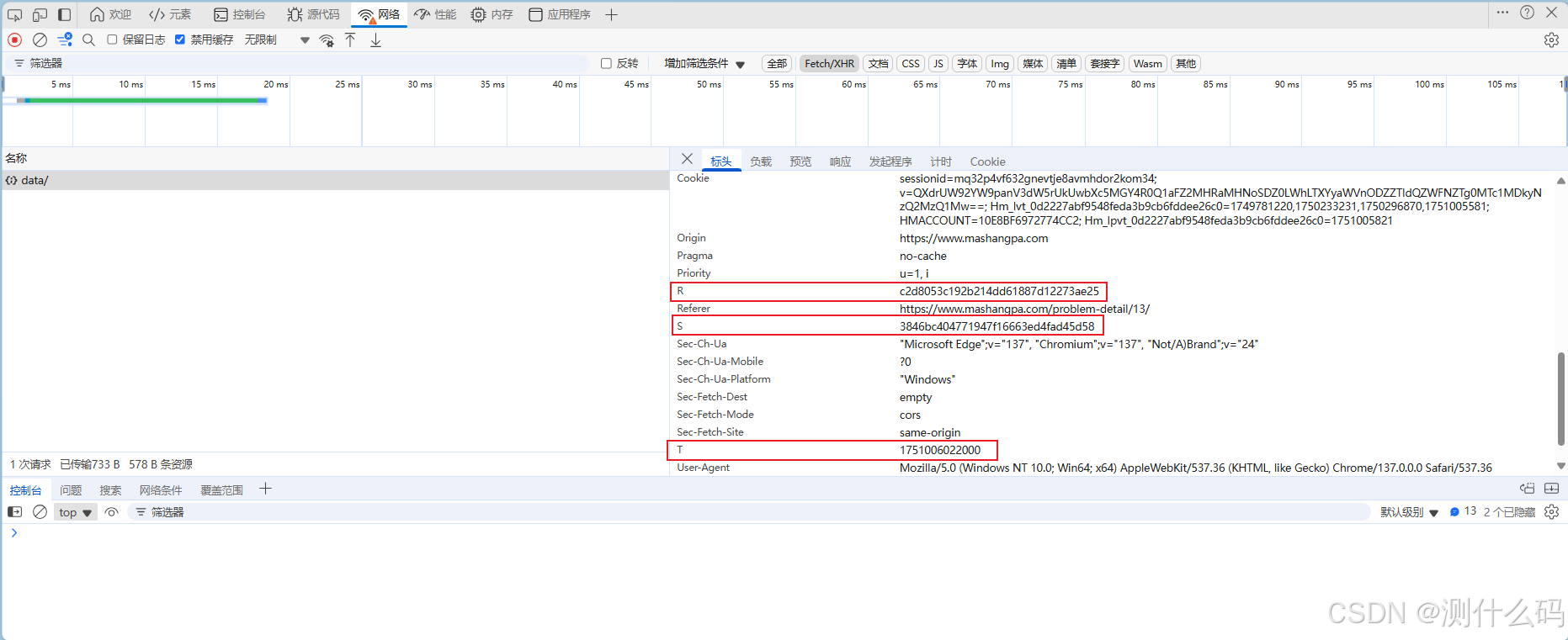
直接定位到jqueryxhr.js中,可以先进行解混,发现加密参数的加密位置。
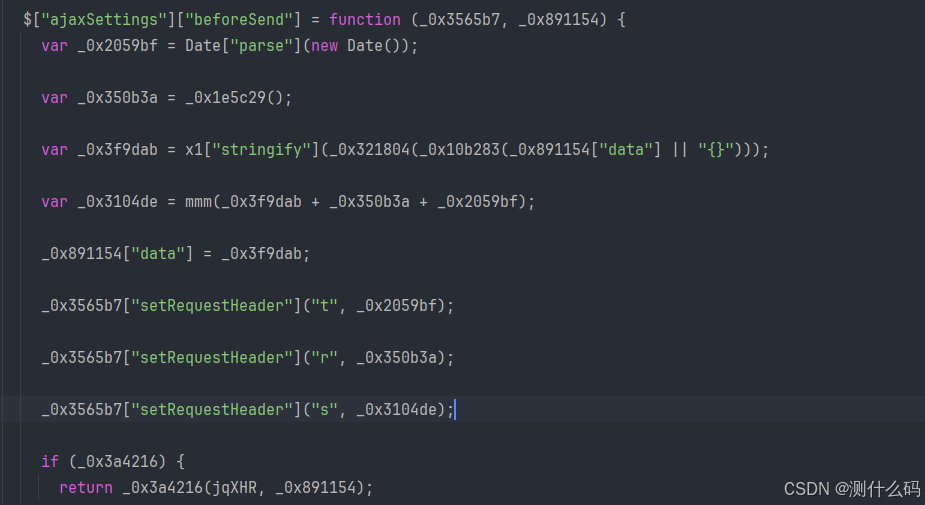
直接开始扣代码, 改造参数加密,需要注意_0x3f9dab实际的参数是一个page的字符串。
import time
import execjs
import requests
cookies = {
xxxx
}
total_sum = 0
for i in range(1, 21):
with open('./js/13.js', 'r', encoding='utf-8') as f:
ctx = execjs.compile(f.read())
dt = ctx.call('get', i)
print(dt)
json_data = '{"page":"'+str(i)+'"}'
print(json_data)
headers = {
'referer': 'https://www.mashangpa.com/problem-detail/13/',
'user-agent': 'Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/137.0.0.0 Safari/537.36 Edg/137.0.0.0',
'R': dt.get('R'),
'S': dt.get('S'),
'T': dt.get('T')
}
url = 'https://www.mashangpa.com/api/problem-detail/13/data/'
response = requests.post(url, cookies=cookies, headers=headers,data=json_data)
print(response.json())
total_sum += sum(response.json()['current_array'])
print(total_sum)
print(f"和为:{total_sum}")第十四题
观察请求参数,发现负载中有个加密参数m。
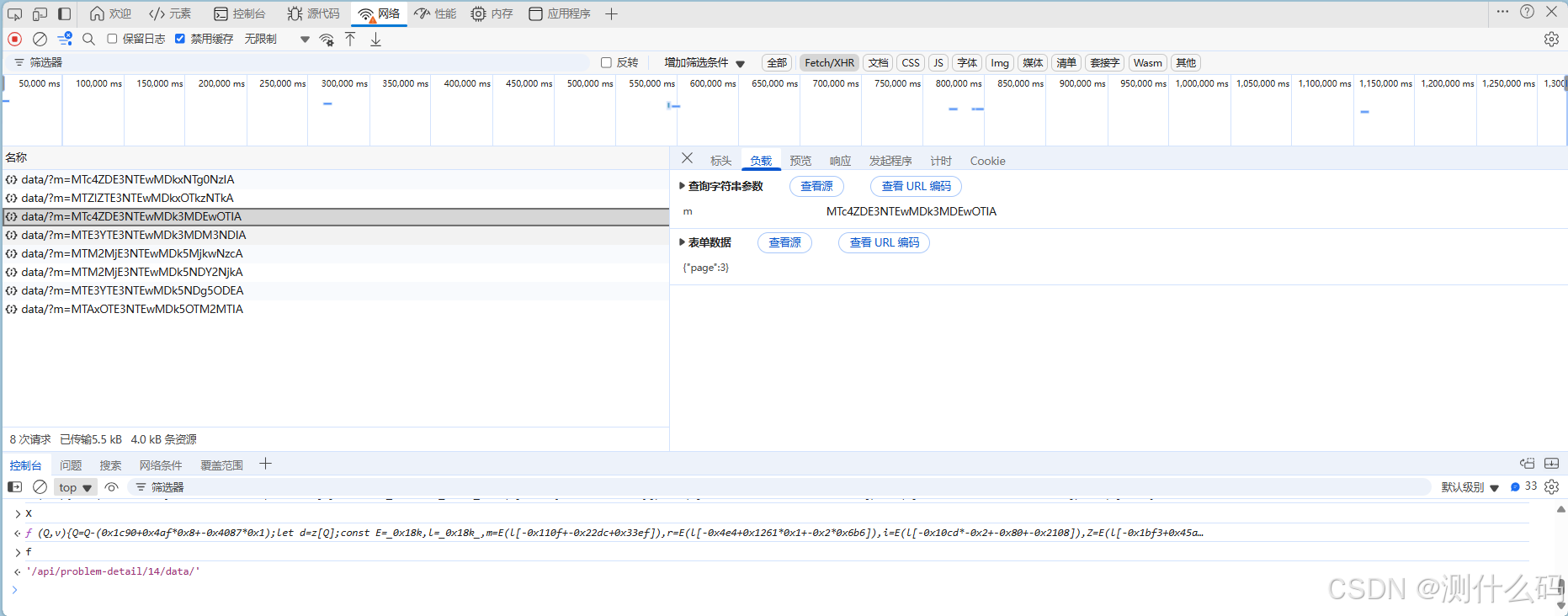
查看请求调用堆栈,进行断点调试,最终来自xhr.js中,发现加密函数x(),值为f。
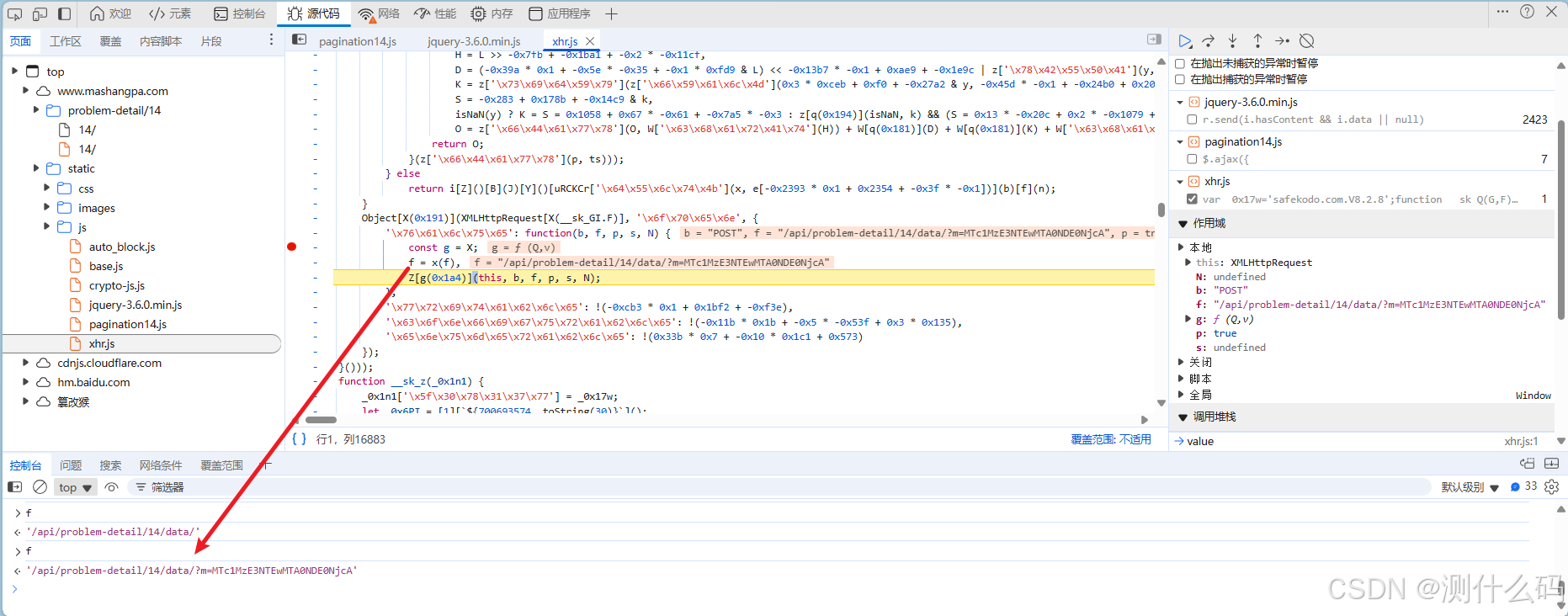
进入x方法进行调试,发现直接进入if判断中,直接扣下if中的代码,运行调试,补齐缺失代码。
import execjs
import requests
cookies = {
xxxx
}
total_sum = 0
for i in range(1, 21):
with open('./js/14.js', 'r', encoding='utf-8') as f:
ctx = execjs.compile(f.read())
uri = ctx.call('get')
#json_data = '{"page":' + str(i) + '}'
json_data = {
"page": i
}
print(json_data)
headers = {
'referer': 'https://www.mashangpa.com/problem-detail/14/',
'user-agent': 'Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/137.0.0.0 Safari/537.36 Edg/137.0.0.0',
}
url = 'https://www.mashangpa.com' + uri
print(url)
response = requests.post(url, cookies=cookies, headers=headers,json=json_data)
print(response.json())
total_sum += sum(response.json()['current_array'])
print(total_sum)
print(f"和为:{total_sum}")第十五题
与i问财的加密逻辑一致,直接把js代码全扣除来,定义window和document变量,可以结合hook来定位调试到cookie加密位置,并添加js自吐环境和代理器(运行js调试),需要补充一下原型链依赖==,没有基础的确实复杂一些。
import time
import execjs
import requests
total_sum = 0
for i in range(1, 21):
t = int(time.time())
with open('./js/15.js', 'r', encoding='utf-8') as f:
ctx = execjs.compile(f.read())
v = ctx.call('main123', i)
headers = {
'referer': 'https://www.mashangpa.com/problem-detail/15/',
'user-agent': 'Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/137.0.0.0 Safari/537.36 Edg/137.0.0.0',
'Hexin-V': v
}
cookies = {
xxxxx,
'v':v
}
url = f'https://www.mashangpa.com/api/problem-detail/15/data/?page={i}'
response = requests.get(url, cookies=cookies, headers=headers)
response.raise_for_status()
print(response.json())
total_sum += sum(response.json()['current_array'])
print(total_sum)
print(f"和为:{total_sum}")第十六题
F12无法使用,需要手动打开开发工具,发现请求负载加密参数h5
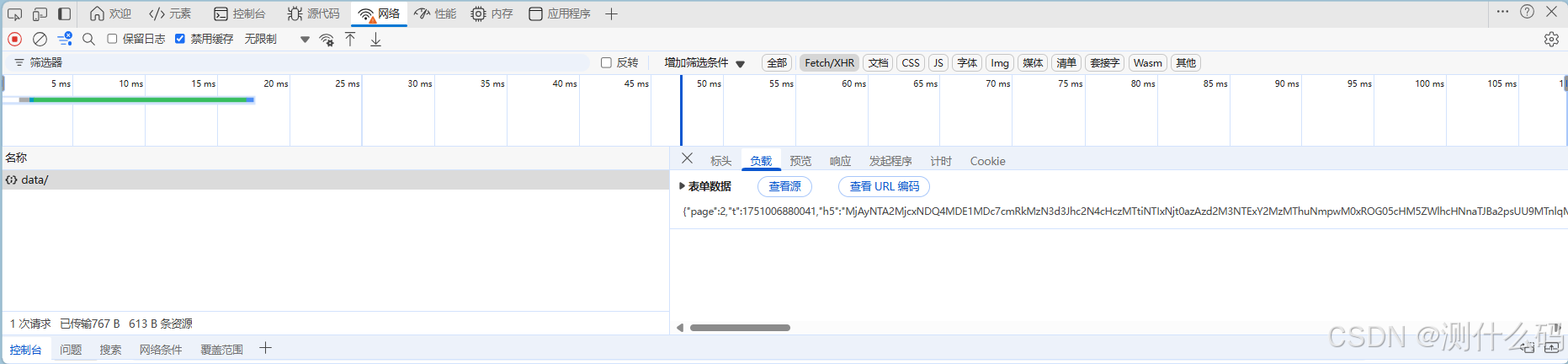
直接堆栈分析,查看请求堆栈响应,断点分析后,定位到PcSign.js中,直接扣下全部代码,补充js自吐环境,sign中_$lw就是h5的加密值,所以我们需要使用window全局变量存入此值,最后在自定义方法中返回此值即可。
import time
import execjs
import requests
headers = {
'referer': 'https://www.mashangpa.com/problem-detail/16/',
'user-agent': 'Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/137.0.0.0 Safari/537.36 Edg/137.0.0.0',
}
cookies = {
xxxxx
}
total_sum = 0
for i in range(1, 21):
t = int(time.time() * 1000)
with open('./js/16.js', 'r', encoding='utf-8') as f:
ctx = execjs.compile(f.read())
h5 = ctx.call('get', i,t)
json_data = {
"page":i,
"t":t,
"h5":h5,
}
url = 'https://www.mashangpa.com/api/problem-detail/16/data/'
response = requests.post(url, cookies=cookies, headers=headers,json=json_data)
print(response.json())
total_sum += sum(response.json()['current_array'])
print(total_sum)
print(f"和为:{total_sum}")第十七题
是对响应的数组进行了加密,找到加密的映射关系就很好解决
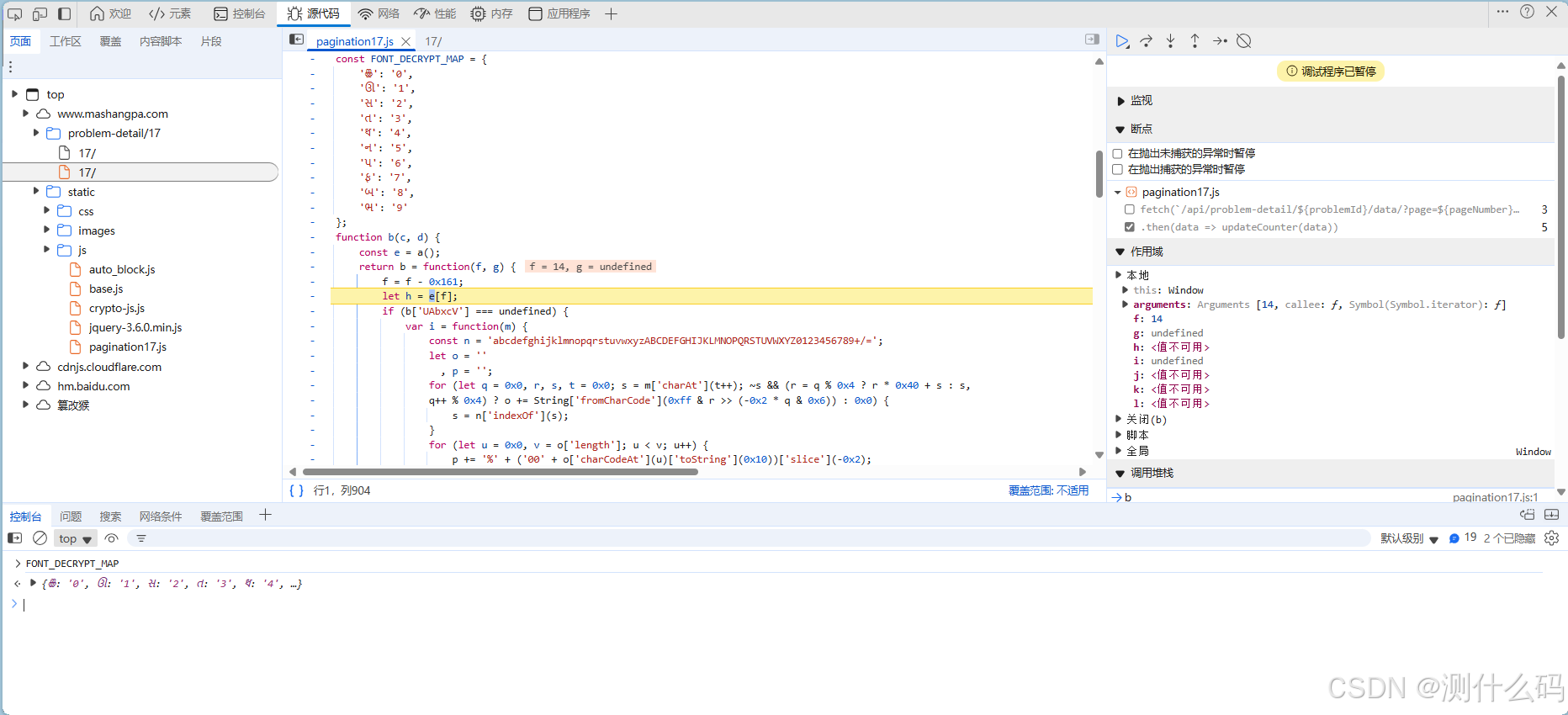
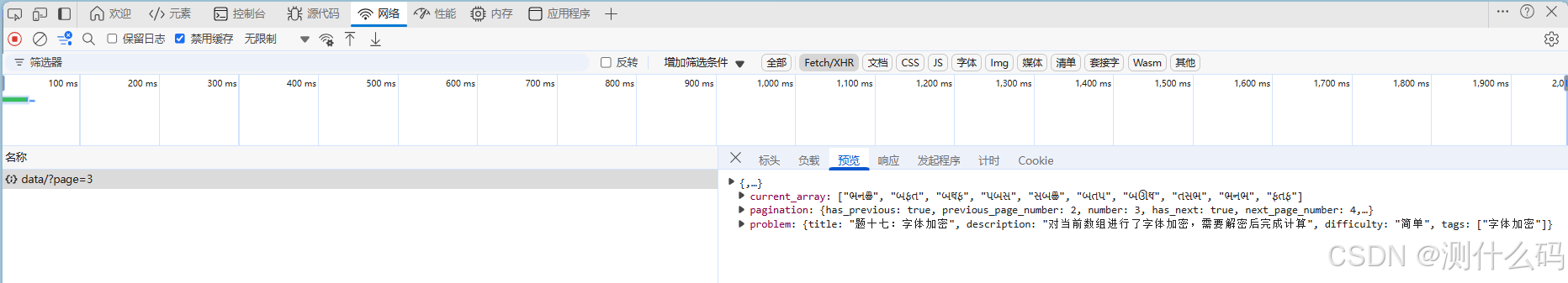 断点调试,这里找到了映射关系,直接使用python代码进行解析。
断点调试,这里找到了映射关系,直接使用python代码进行解析。
import requests
# 需要登录,请先登录,获取cookie并完善参数
cookies = {
'xxx':'xxxx',
......
}
headers = {
'referer': 'https://www.mashangpa.com/problem-detail/17/',
'user-agent': 'Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/137.0.0.0 Safari/537.36 Edg/137.0.0.0',
}
def decrypt_special_chars_py(input_array):
"""纯 Python 实现的解密函数"""
mapping = {
'\uA66E': '0', # ꙮ
'\u0A8A': '1', # ઊ
'\u0AB8': '2', # સ
'\u0AA4': '3', # ત
'\u09A7': '4', # ধ
'\u0AA8': '5', # ન
'\u0AAA': '6', # પ
'\u0AAB': '7', # ફ
'\u0AAC': '8', # બ
'\u0AAD': '9' # ભ
}
return [
''.join(mapping.get(char, char) for char in item)
for item in input_array
]
total_sum = 0
for i in range(1, 21):
url = f'https://www.mashangpa.com/api/problem-detail/17/data/?page={i}'
response = requests.get(url, cookies=cookies, headers=headers)
data_array = response.json()['current_array']
final_array1 = decrypt_special_chars_py(data_array)
final_array2 = [int(num) for num in final_array1]
print(final_array2)
total_sum += sum(final_array2)
print(f"和为:{total_sum}")第十八题
查看请求参数,发现加密参数M和时间戳Timestamp。
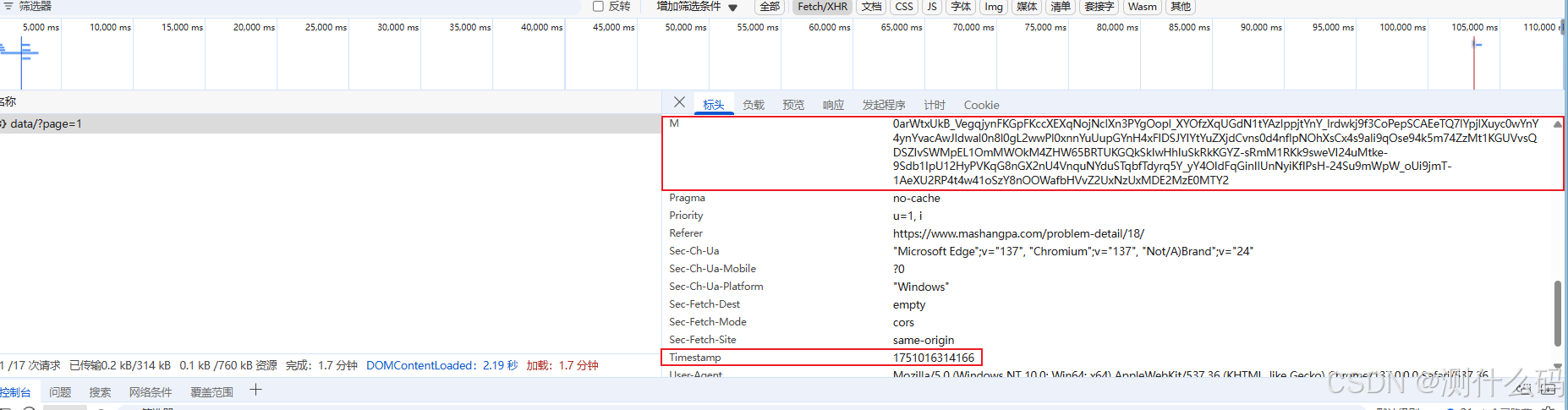
查看请求调用堆栈,找到m生成位置。
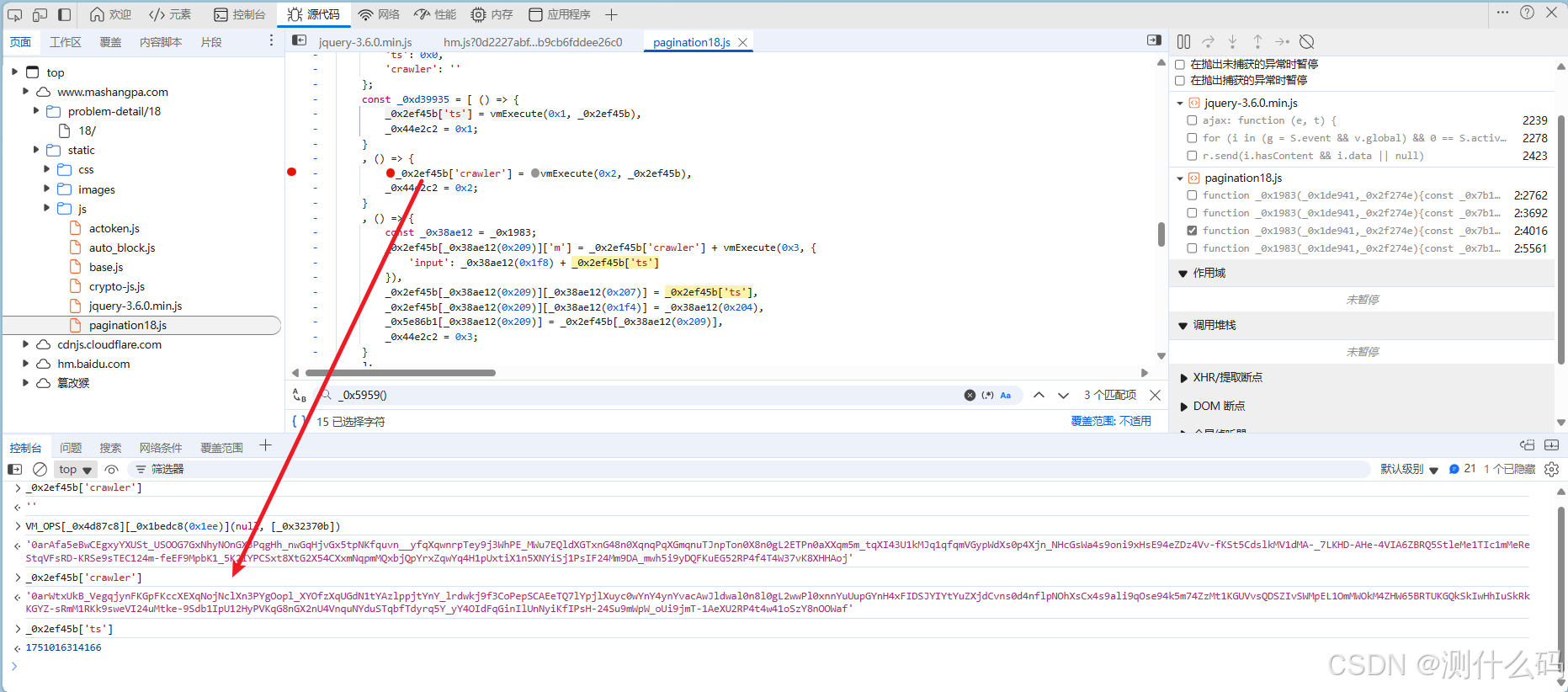
发现M是由固定加密拼接固定字符与时间戳的base64。只需要找到前半部分的加密逻辑即可,直接找到加密文件,这里直接扣下全部代码,最后发现进入anti(0x4)方法,找到anti = n出,这就是最终的m前半部分值,保存后在getCrawlerInfo中供给调用。
import execjs
import requests
import time
cookies = {
xxxxx
}
final_total = 0
for page in range(1, 21):
url = f"https://www.mashangpa.com/api/problem-detail/18/data/?page={page}"
with open('js/18.js', 'r', encoding='utf-8') as f:
ctx = execjs.compile(f.read())
info = ctx.call('get')
print(info)
headers = {
'referer': 'https://www.mashangpa.com/problem-detail/18/',
'user-agent': 'Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/137.0.0.0 Safari/537.36 Edg/137.0.0.0',
'm': info.get('m'),
'timestamp': info.get('ts')
}
response = requests.get(url,headers=headers, cookies=cookies)
print(response.json())
final_total += sum(response.json()['current_array'])
print(final_total)
time.sleep(0.5)
print(f"和为:{final_total}")第十九题
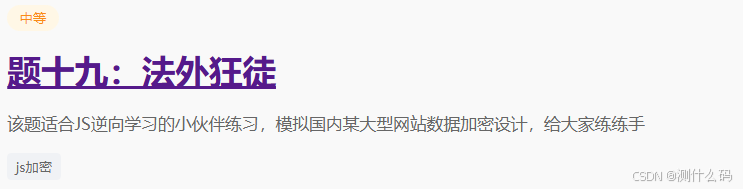
查看请求参数以及响应参数,发现响应加密参数r和k。
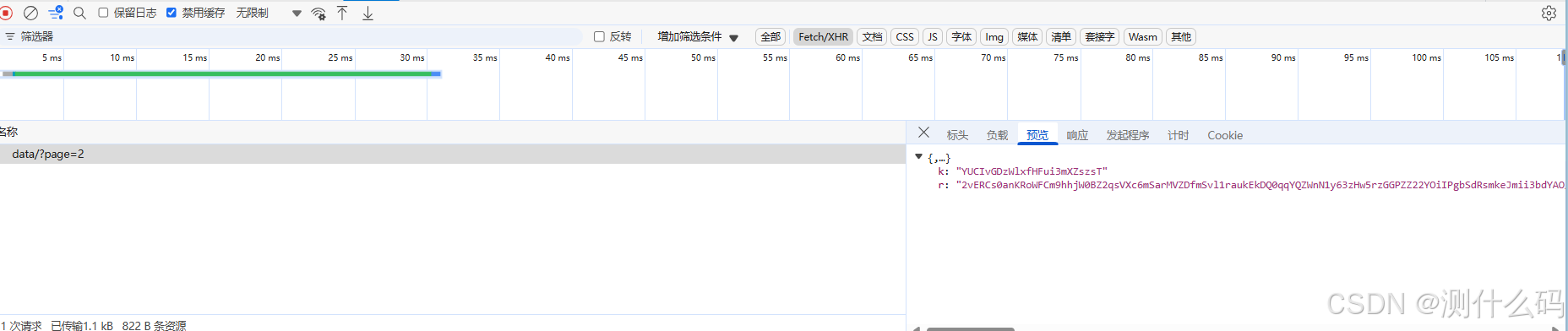
查看请求调用堆栈,进行断点调试,发现是通过自定义的DES3.decrypt进行解密。
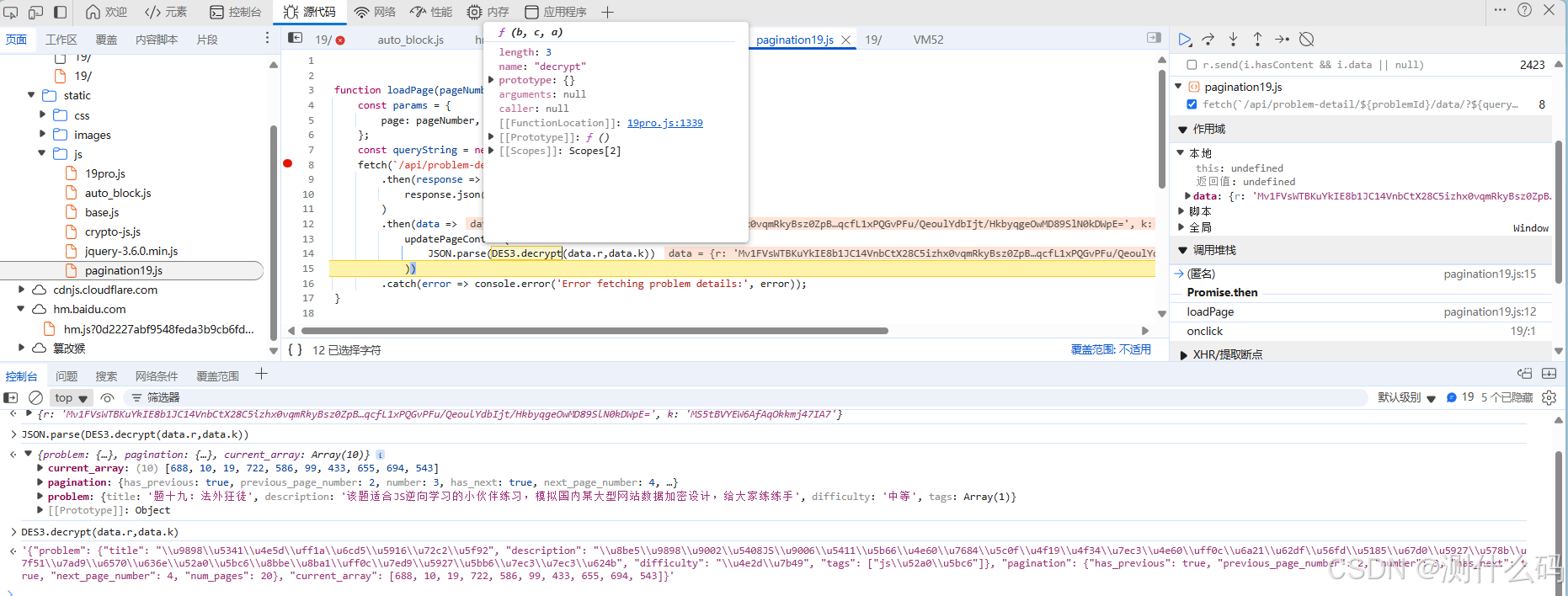
开始扣代码,扣取formatDate和DES3,并引入CryptoJS变量。把响应的参数传入并调用DES3.decrypt即可得到解密后的响应数据。
import json
import execjs
import requests
import time
cookies = {
xxxxx
}
headers = {
'accept': 'application/json, text/javascript, */*; q=0.01',
'accept-language': 'zh-CN,zh;q=0.9,en;q=0.8,en-GB;q=0.7,en-US;q=0.6',
'cache-control': 'no-cache',
'client-version': '1.0.0',
'pragma': 'no-cache',
'priority': 'u=1, i',
'referer': 'https://www.mashangpa.com/problem-detail/19/',
'sec-ch-ua': '"Not)A;Brand";v="8", "Chromium";v="138", "Microsoft Edge";v="138"',
'sec-ch-ua-mobile': '?0',
'sec-ch-ua-platform': '"Windows"',
'sec-fetch-dest': 'empty',
'sec-fetch-mode': 'cors',
'sec-fetch-site': 'same-origin',
'user-agent': 'Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/138.0.0.0 Safari/537.36 Edg/138.0.0.0',
'x-requested-with': 'XMLHttpRequest',
}
final_total = 0
for page in range(1, 21):
url = "https://www.mashangpa.com/api/problem-detail/19/data/?"
with open('js/19.js', 'r', encoding='utf-8') as f:
ctx = execjs.compile(f.read())
params = {
"page": page,
}
response = requests.get(url, headers=headers, cookies=cookies, params=params)
print(response.json())
data = response.json()
info = json.loads(ctx.call('get',data.get("r"),data.get("k")))
print(info['current_array'])
final_total += sum(info['current_array'])
time.sleep(1)
print(f"和为:{final_total}")
学习到这里就已经结束啦!有不懂的欢迎在评论区留言~
❤如果文章对您有帮助,您的点赞就是我最大的动力❤
更多推荐
 已为社区贡献1条内容
已为社区贡献1条内容









所有评论(0)