k8s学习-CKS真题-日志审计 log audit
-audit-log-path 指定用来写入审计事件的日志文件路径。不指定此标志会禁用日志后端。- -audit-log-maxsize 定义审计日志文件轮转之前的最大大小(兆字节)- -audit-log-maxbackup 定义要保留的审计日志文件的最大数量。- -audit-log-maxage 定义保留旧审计日志文件的最大天数。- -audit-policy-file 指定审计策略文件。修
·
题目
Task
在 cluster 中启用审计日志。为此,请启用日志后端,并确保:
日志存储在 /var/log/kubernetes/audit-logs.txt
日志文件能保留 10 天
最多保留 2 个旧审计日志文件
/etc/kubernetes/logpolicy/sample-policy.yaml 提供了基本策略。它仅指定不记录的内容。
注意:基本策略位于 cluster 的 master 节点上。
编辑和扩展基本策略以记录:
RequestResponse 级别的 persistentvolumes 更改
namespace front-apps 中 configmaps 更改的请求体
Metadata 级别的所有 namespace 中的 ConfigMap 和 Secret 的更改
此外,添加一个全方位的规则以在 Metadata 级别记录所有其他请求。
注意:不要忘记应用修改后的策略。
kube-apiserver.yaml选项解释:
- -audit-policy-file 指定审计策略文件
- -audit-log-path 指定用来写入审计事件的日志文件路径。不指定此标志会禁用日志后端。
- -audit-log-maxage 定义保留旧审计日志文件的最大天数
- -audit-log-maxbackup 定义要保留的审计日志文件的最大数量
- -audit-log-maxsize 定义审计日志文件轮转之前的最大大小(兆字节)
更多见参考
环境搭建
命令
mkdir -p /etc/kubernetes/logpolicy/
vim /etc/kubernetes/logpolicy/sample-policy.yaml
内容
apiVersion: audit.k8s.io/v1
kind: Policy
# Don't generate audit events for all requests in RequestReceived stage.
omitStages:
- "RequestReceived"
rules:
# Don't log watch requests by the "system:kube-proxy" on endpoints or services
- level: None
users: ["system:kube-proxy"]
verbs: ["watch"]
resources:
- group: "" # core API group
resources: ["endpoints", "services"]
# Don't log authenticated requests to certain non-resource URL paths.
- level: None
userGroups: ["system:authenticated"]
nonResourceURLs:
- "/api*" # Wildcard matching.
- "/version"
# Please do not delete the above rule content, you can continue add it below.
解题
命令
vim /etc/kubernetes/logpolicy/sample-policy.yaml
内容
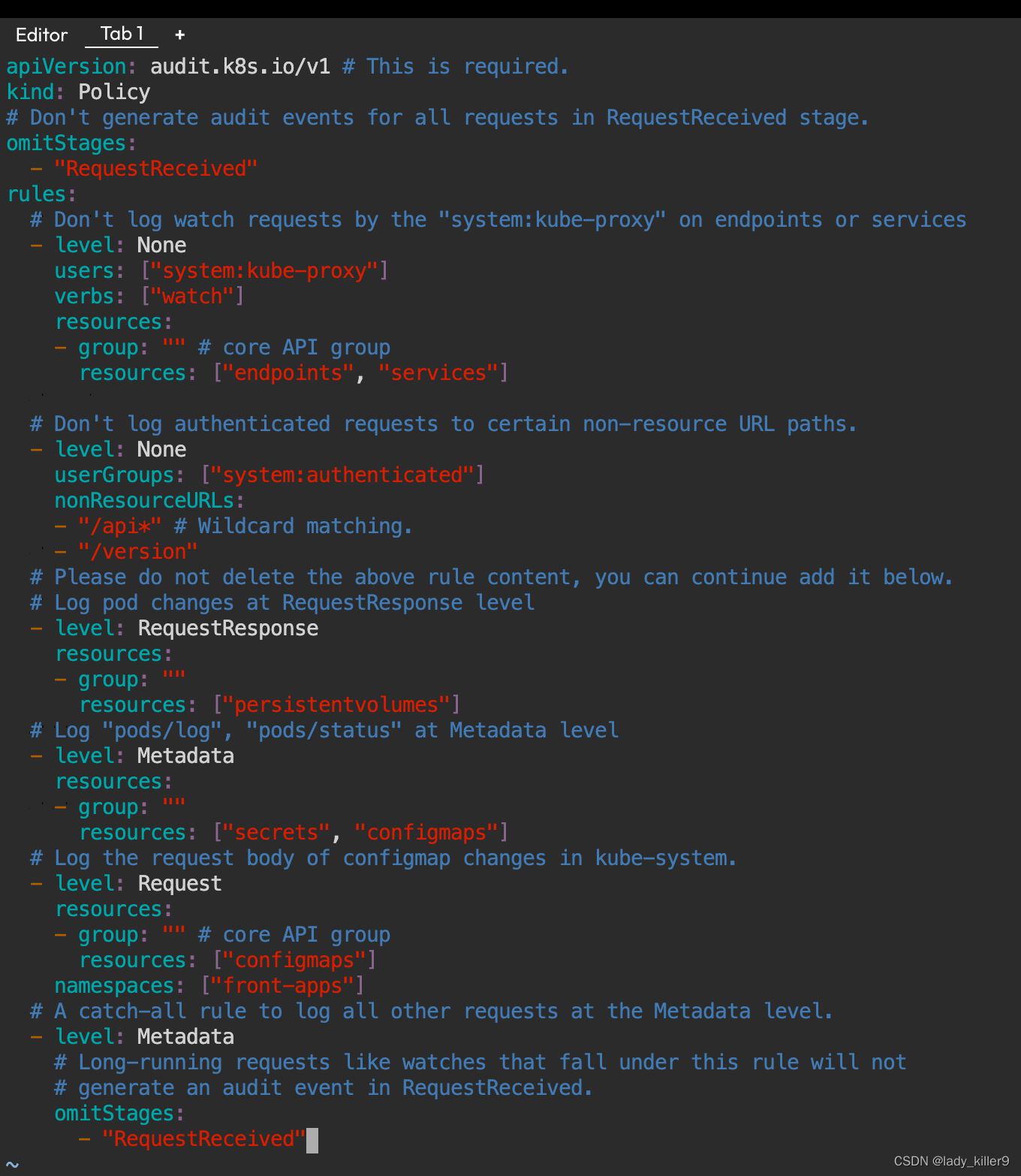
apiVersion: audit.k8s.io/v1 # This is required.
kind: Policy
# Don't generate audit events for all requests in RequestReceived stage.
omitStages:
- "RequestReceived"
rules:
# Don't log watch requests by the "system:kube-proxy" on endpoints or services
- level: None
users: ["system:kube-proxy"]
verbs: ["watch"]
resources:
- group: "" # core API group
resources: ["endpoints", "services"]
# Don't log authenticated requests to certain non-resource URL paths.
- level: None
userGroups: ["system:authenticated"]
nonResourceURLs:
- "/api*" # Wildcard matching.
- "/version"
# Please do not delete the above rule content, you can continue add it below.
# Log pod changes at RequestResponse level
- level: RequestResponse
resources:
- group: ""
resources: ["persistentvolumes"]
# Log "pods/log", "pods/status" at Metadata level
- level: Metadata
resources:
- group: ""
resources: ["secrets", "configmaps"]
# Log the request body of configmap changes in kube-system.
- level: Request
resources:
- group: "" # core API group
resources: ["configmaps"]
namespaces: ["front-apps"]
# A catch-all rule to log all other requests at the Metadata level.
- level: Metadata
# Long-running requests like watches that fall under this rule will not
# generate an audit event in RequestReceived.
omitStages:
- "RequestReceived"
截图

修改kube-apiserverl.yaml配置文件
命令
vim /etc/kubernetes/manifests/kube-apiserver.yaml
添加以下四个启动项
- --audit-log-path=/var/log/kubernetes/audit-logs.txt
- --audit-policy-file=/etc/kubernetes/logpolicy/sample-policy.yaml
- --audit-log-maxage=10
- --audit-log-maxbackup=2
截图

截图

重启kubelet
命令
systemctl daemon-reload
systemctl restart kubelet
截图

模拟题


参考
更多推荐
 已为社区贡献44条内容
已为社区贡献44条内容






所有评论(0)