Docker&;K8s---Docker的安装、部署、镜像管理、容器操作、Dockerfile_izusz
还有兄弟不知道网络安全面试可以提前刷题吗?费时一周整理的160+网络安全面试题,金九银十,做网络安全面试里的显眼包!王岚嵚工程师面试题(附答案),只能帮兄弟们到这儿了!如果你能答对70%,找一个安全工作,问题不大。对于有1-3年工作经验,想要跳槽的朋友来说,也是很好的温习资料!【完整版领取方式在文末!!内容实在太多,不一一截图了。
还有兄弟不知道网络安全面试可以提前刷题吗?费时一周整理的160+网络安全面试题,金九银十,做网络安全面试里的显眼包!
王岚嵚工程师面试题(附答案),只能帮兄弟们到这儿了!如果你能答对70%,找一个安全工作,问题不大。
对于有1-3年工作经验,想要跳槽的朋友来说,也是很好的温习资料!
【完整版领取方式在文末!!】
93道网络安全面试题



需要体系化学习资料的朋友,可以加我V获取:vip204888 (备注网络安全)
内容实在太多,不一一截图了
黑客学习资源推荐
最后给大家分享一份全套的网络安全学习资料,给那些想学习 网络安全的小伙伴们一点帮助!
对于从来没有接触过网络安全的同学,我们帮你准备了详细的学习成长路线图。可以说是最科学最系统的学习路线,大家跟着这个大的方向学习准没问题。
😝朋友们如果有需要的话,可以联系领取~
1️⃣零基础入门
① 学习路线
对于从来没有接触过网络安全的同学,我们帮你准备了详细的学习成长路线图。可以说是最科学最系统的学习路线,大家跟着这个大的方向学习准没问题。

② 路线对应学习视频
同时每个成长路线对应的板块都有配套的视频提供:

2️⃣视频配套工具&国内外网安书籍、文档
① 工具

② 视频

③ 书籍

资源较为敏感,未展示全面,需要的最下面获取


② 简历模板

因篇幅有限,资料较为敏感仅展示部分资料,添加上方即可获取👆
网上学习资料一大堆,但如果学到的知识不成体系,遇到问题时只是浅尝辄止,不再深入研究,那么很难做到真正的技术提升。
一个人可以走的很快,但一群人才能走的更远!不论你是正从事IT行业的老鸟或是对IT行业感兴趣的新人,都欢迎加入我们的的圈子(技术交流、学习资源、职场吐槽、大厂内推、面试辅导),让我们一起学习成长!
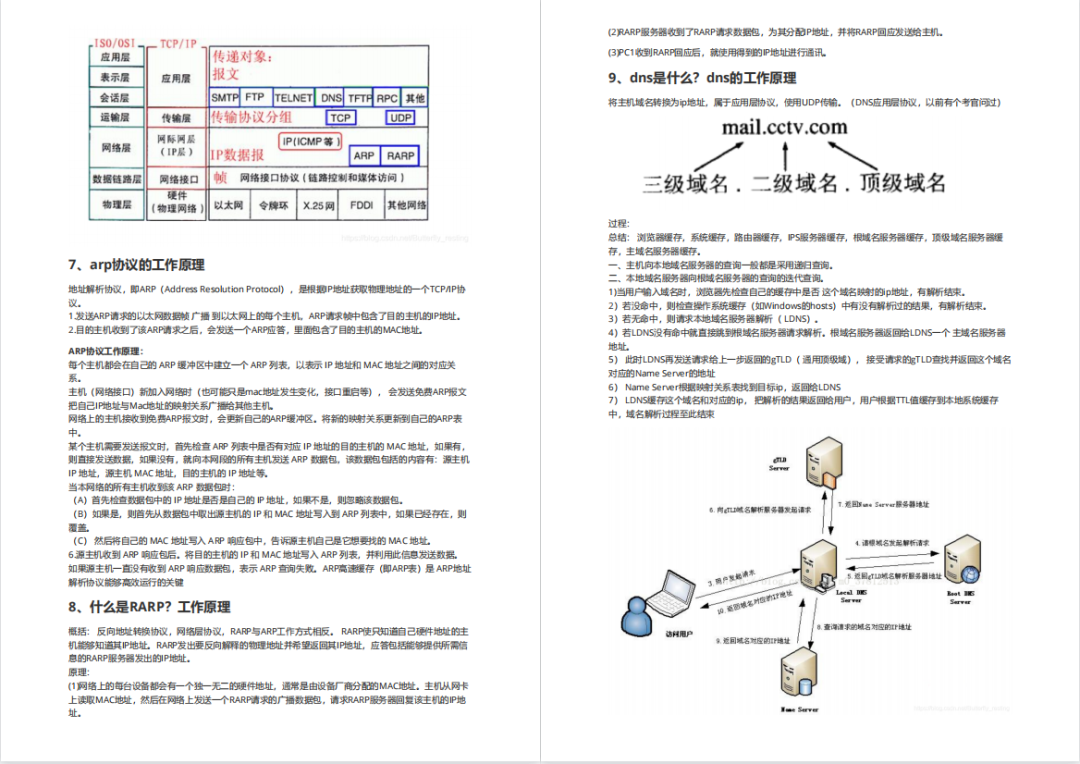
Docker安装和部署
安装
阿里云ECS
[root@iZuf6g4e6vhdv58sz2z1klZ ~]# uname -a
Linux iZuf6g4e6vhdv58sz2z1klZ 4.18.0-193.28.1.el8_2.x86_64 #1 SMP Thu Oct 22 00:20:22 UTC 2020 x86\_64 x86\_64 x
[root@iZuf6g4e6vhdv58sz2z1klZ ~]# cat /etc/redhat-release
CentOS Linux release 8.2.2004 (Core)
[root@iZuf6g4e6vhdv58sz2z1klZ ~]# getenforce
Disabled
[root@iZuf6g4e6vhdv58sz2z1klZ ~]# systemctl stop firewalld
[root@iZuf6g4e6vhdv58sz2z1klZ ~]# free -m
total used free shared buff/cache available
Mem: 1723 1115 139 3 468 440
Swap: 1024 301 723
# epel源
[root@iZuf6g4e6vhdv58sz2z1klZ ~]# yum install epel-release -y
Repository epel is listed more than once in the configuration
Last metadata expiration check: 2:47:33 ago on Wed 16 Jun 2021 03:07:22 PM CST.
Package epel-release-8-10.el8.noarch is already installed.
Dependencies resolved.
Nothing to do.
Complete!
# 安装docker
[root@iZuf6g4e6vhdv58sz2z1klZ ~]# yum install -y yum-utils
[root@iZuf6g4e6vhdv58sz2z1klZ ~]# yum-config-manager --add-repo http://mirrors.aliyun.com/docker-ce/linux/centos/docker-ce.repo
[root@iZuf6g4e6vhdv58sz2z1klZ ~]# yum list docker-ce --showduplicate
Repository epel is listed more than once in the configuration
Docker CE Stable - x86_64 78 kB/s | 14 kB 00:00
Available Packages
docker-ce.x86_64 3:19.03.13-3.el8 docker-ce-stable
docker-ce.x86_64 3:19.03.14-3.el8 docker-ce-stable
docker-ce.x86_64 3:19.03.15-3.el8 docker-ce-stable
docker-ce.x86_64 3:20.10.0-3.el8 docker-ce-stable
docker-ce.x86_64 3:20.10.1-3.el8 docker-ce-stable
docker-ce.x86_64 3:20.10.2-3.el8 docker-ce-stable
docker-ce.x86_64 3:20.10.3-3.el8 docker-ce-stable
docker-ce.x86_64 3:20.10.4-3.el8 docker-ce-stable
docker-ce.x86_64 3:20.10.5-3.el8 docker-ce-stable
docker-ce.x86_64 3:20.10.6-3.el8 docker-ce-stable
docker-ce.x86_64 3:20.10.7-3.el8 docker-ce-stable
[root@iZuf6g4e6vhdv58sz2z1klZ ~]# yum install docker-ce -y
部署
# 开机自启动
[root@iZuf6g4e6vhdv58sz2z1klZ ~]# systemctl enable docker
Created symlink /etc/systemd/system/multi-user.target.wants/docker.service → /usr/lib/systemd/system/docker.service.
# 启动docker
[root@iZuf6g4e6vhdv58sz2z1klZ ~]# systemctl start docker
# 配置
[root@iZuf6g4e6vhdv58sz2z1klZ ~]#vi /etc/docker/daemon.json
配置文件
{
"graph": "/mydata/docker",
"storage-driver": "overlay2",
"insecure-registries": ["registry.access.redhat.com", "quay.io"],
"registry-mirrors": ["https://q2gr04ke.mirror.aliyuncs.com/"],
"bip": "172.17.0.1/24",
"exec-opts": ["native.cgroupdriver=systemd"],
"live-restore":true
}
docker info
查看容器信息和启动是否正常
[root@iZuf6g4e6vhdv58sz2z1klZ ~]# systemctl restart docker
[root@iZuf6g4e6vhdv58sz2z1klZ ~]# docker info
Client:
Context: default
Debug Mode: false
Plugins:
app: Docker App (Docker Inc., v0.9.1-beta3)
buildx: Build with BuildKit (Docker Inc., v0.5.1-docker)
scan: Docker Scan (Docker Inc., v0.8.0)
Server:
Containers: 0
Running: 0
Paused: 0
Stopped: 0
Images: 0
Server Version: 20.10.7
Storage Driver: overlay2
Backing Filesystem: xfs
Supports d_type: true
Native Overlay Diff: true
userxattr: false
Logging Driver: json-file
Cgroup Driver: systemd
Cgroup Version: 1
Plugins:
Volume: local
Network: bridge host ipvlan macvlan null overlay
Log: awslogs fluentd gcplogs gelf journald json-file local logentries splunk syslog
Swarm: inactive
Runtimes: io.containerd.runc.v2 io.containerd.runtime.v1.linux runc
Default Runtime: runc
Init Binary: docker-init
containerd version: d71fcd7d8303cbf684402823e425e9dd2e99285d
runc version: b9ee9c6314599f1b4a7f497e1f1f856fe433d3b7
init version: de40ad0
Security Options:
seccomp
Profile: default
Kernel Version: 4.18.0-193.28.1.el8_2.x86_64
Operating System: CentOS Linux 8 (Core)
OSType: linux
Architecture: x86_64
CPUs: 2
Total Memory: 1.683GiB
Name: iZuf6g4e6vhdv58sz2z1klZ
ID: T3TJ:BJTA:U5PY:ZX74:K57G:7CDR:RMCT:CSBG:JLFG:FXPQ:KUB6:MVJT
Docker Root Dir: /mydata/docker
Debug Mode: false
Registry: https://index.docker.io/v1/
Labels:
Experimental: false
Insecure Registries:
quay.io
registry.access.redhat.com
127.0.0.0/8
Registry Mirrors:
https://q2gr04ke.mirror.aliyuncs.com/
Live Restore Enabled: true
第一个命令hello world
[root@iZuf6g4e6vhdv58sz2z1klZ ~]# docker run hello-world
Unable to find image 'hello-world:latest' locally
latest: Pulling from library/hello-world
b8dfde127a29: Pull complete
Digest: sha256:9f6ad537c5132bcce57f7a0a20e317228d382c3cd61edae14650eec68b2b345c
Status: Downloaded newer image for hello-world:latest
Hello from Docker!
This message shows that your installation appears to be working correctly.
To generate this message, Docker took the following steps:
1. The Docker client contacted the Docker daemon.
2. The Docker daemon pulled the "hello-world" image from the Docker Hub.
(amd64)
3. The Docker daemon created a new container from that image which runs the
executable that produces the output you are currently reading.
4. The Docker daemon streamed that output to the Docker client, which sent it
to your terminal.
To try something more ambitious, you can run an Ubuntu container with:
$ docker run -it ubuntu bash
Share images, automate workflows, and more with a free Docker ID:
https://hub.docker.com/
For more examples and ideas, visit:
https://docs.docker.com/get-started/
Docker典型的C/S架构引擎
To generate this message, Docker took the following steps:
- The Docker client contacted the Docker daemon.
- The Docker daemon pulled the “hello-world” image from the Docker Hub.
(amd64)- The Docker daemon created a new container from that image which runs the
executable that produces the output you are currently reading.- The Docker daemon streamed that output to the Docker client, which sent it
to your terminal.

Docker的镜像管理
远端仓库
注册dockerhub: https://hub.docker.com/repositories
登录: docker login docker.io
[root@iZuf6g4e6vhdv58sz2z1klZ ~]# docker login docker.io
Login with your Docker ID to push and pull images from Docker Hub. If you don't have a Docker ID, head over to https://hub.docker.com to create one.
Username: dachongming
Password:
WARNING! Your password will be stored unencrypted in /root/.docker/config.json.
Configure a credential helper to remove this warning. See
https://docs.docker.com/engine/reference/commandline/login/#credentials-store
Login Succeeded
[root@iZuf6g4e6vhdv58sz2z1klZ ~]#
# 信息存储在
[root@iZuf6g4e6vhdv58sz2z1klZ ~]# cat /root/.docker/config.json
搜索镜像
docker search alpine
[root@iZuf6g4e6vhdv58sz2z1klZ ~]# docker search alpine
NAME DESCRIPTION STARS OFFICIAL AUTOMATED
alpine A minimal Docker image based on Alpine Linux… 7551 [OK]
mhart/alpine-node Minimal Node.js built on Alpine Linux 484
anapsix/alpine-java Oracle Java 8 (and 7) with GLIBC 2.28 over A… 470 [OK]
frolvlad/alpine-glibc Alpine Docker image with glibc (~12MB) 261 [OK]
alpine/git A simple git container running in alpine li… 183 [OK]
yobasystems/alpine-mariadb MariaDB running on Alpine Linux [docker] [am… 89 [OK]
alpine/socat Run socat command in alpine container 68 [OK]
davidcaste/alpine-tomcat Apache Tomcat 7/8 using Oracle Java 7/8 with… 44 [OK]
kiasaki/alpine-postgres PostgreSQL docker image based on Alpine Linux 44 [OK]
jfloff/alpine-python A small, more complete, Python Docker image … 41 [OK]
byrnedo/alpine-curl Alpine linux with curl installed and set as … 34 [OK]
zenika/alpine-chrome Chrome running in headless mode in a tiny Al… 34 [OK]
hermsi/alpine-sshd Dockerize your OpenSSH-server with rsync and… 33 [OK]
hermsi/alpine-fpm-php FPM-PHP 7.0 to 8.0, shipped along with tons … 25 [OK]
etopian/alpine-php-wordpress Alpine WordPress Nginx PHP-FPM WP-CLI 25 [OK]
bashell/alpine-bash Alpine Linux with /bin/bash as a default she… 18 [OK]
davidcaste/alpine-java-unlimited-jce Oracle Java 8 (and 7) with GLIBC 2.21 over A… 13 [OK]
roribio16/alpine-sqs Dockerized ElasticMQ server + web UI over Al… 13 [OK]
spotify/alpine Alpine image with `bash` and `curl`. 11 [OK]
cfmanteiga/alpine-bash-curl-jq Docker Alpine image with Bash, curl and jq p… 6 [OK]
bushrangers/alpine-caddy Alpine Linux Docker Container running Caddys… 1 [OK]
ellerbrock/alpine-mysql-client MySQL Client based on Alpine Linux 1 [OK]
apteno/alpine-jq Weekly build of alpine image with curl, wget… 1
dwdraju/alpine-curl-jq Alpine Docker Image with curl, jq, bash 1 [OK]
goodguykoi/alpine-curl-internal simple alpine image with curl installed no C… 1 [OK]
也可在dockerhub上搜索,有可视化界面

下载一个镜像
docker pull alpine
docker pull alpine 默认下载最新版
docker pull alpine:3.10.1 下载指定tag
docker pull docker.io/library/alpine:3.10.1 完整路径,其他仓库不可省,只有dockerhub可省
镜像结构: registry_name/repository_name/image_name:tag_name
例如:docker.io/library/alpine:3.10.1
[root@iZuf6g4e6vhdv58sz2z1klZ ~]# docker pull alpine
Using default tag: latest
latest: Pulling from library/alpine
5843afab3874: Pull complete
Digest: sha256:234cb88d3020898631af0ccbbcca9a66ae7306ecd30c9720690858c1b007d2a0
Status: Downloaded newer image for alpine:latest
docker.io/library/alpine:latest
查看本地镜像
docker image ls
[root@iZuf6g4e6vhdv58sz2z1klZ ~]# docker image ls
REPOSITORY TAG IMAGE ID CREATED SIZE
alpine latest d4ff818577bc 14 hours ago 5.6MB
hello-world latest d1165f221234 3 months ago 13.3kB
给镜像打标签
docker tag IMAGE ID registry_name/repository_name/image_name:tag_name
[root@iZuf6g4e6vhdv58sz2z1klZ ~]# docker tag d4ff818577bc docker.io/dachongming/alpine:v3.14.0
[root@iZuf6g4e6vhdv58sz2z1klZ ~]# docker image ls
REPOSITORY TAG IMAGE ID CREATED SIZE
dachongming/alpine v3.14.0 d4ff818577bc 14 hours ago 5.6MB
alpine latest d4ff818577bc 14 hours ago 5.6MB
hello-world latest d1165f221234 3 months ago 13.3kB
推送镜像
docker push docker.io/dachongming/alpine:v3.14.0
[root@iZuf6g4e6vhdv58sz2z1klZ ~]# docker push docker.io/dachongming/alpine:v3.14.0
The push refers to repository [docker.io/dachongming/alpine]
72e830a4dff5: Mounted from library/alpine
v3.14.0: digest: sha256:1775bebec23e1f3ce486989bfc9ff3c4e951690df84aa9f926497d82f2ffca9d size: 528

删除镜像
docker rmi docker.io/dachongming/alpine:v3.14.0
只是删除标签
docker rmi -f IMAGE ID
强制删除所有
docker hub 上依然存在,想再有,直接pull即可

镜像只第一次拉取比较多,以后每次只拉取增量部分.
Docker容器的基本操作
查看本地的容器进程
docker ps -a
[root@iZuf6g4e6vhdv58sz2z1klZ ~]# docker ps -a
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
d3f98566b856 hello-world "/hello" 2 hours ago Exited (0) 2 hours ago gallant_kepler
[root@iZuf6g4e6vhdv58sz2z1klZ ~]#
启动容器(运行镜像)
docker run [OPTIONS] IMAGE [COMMAND] [ARG...]
[root@iZuf6g4e6vhdv58sz2z1klZ ~]# docker run --help
Usage: docker run [OPTIONS] IMAGE [COMMAND] [ARG...]
OPTIONS:选项
-i:表示启动一个可交互的容器,并持续打开标准输入
-t:表示使用终端关联到容器的标准输入输出上
-d:表示将容器放置在后台运行
-rm:退出后即删除容器
-name:表示定义容器唯一名称
IMAGE:表示要运行的镜像
COMMAND:表示启动容器时要运行的命令
- 交互式启动一个容器
[root@iZuf6g4e6vhdv58sz2z1klZ ~]# docker run -it docker.io/dachongming/alpine:v3.14.0 /bin/sh
/ # cat /etc/issue
Welcome to Alpine Linux 3.14
Kernel \r on an \m (\l)
/ # exit
[root@iZuf6g4e6vhdv58sz2z1klZ ~]#
- 非交互式启动一个容器
[root@iZuf6g4e6vhdv58sz2z1klZ ~]# docker run -rm docker.io/dachongming/alpine:v3.14.0 /bin/echo hello
- 后台运行
[root@iZuf6g4e6vhdv58sz2z1klZ ~]# docker run -d docker.io/dachongming/alpine:v3.14.0 /bin/sleep 300
[root@iZuf6g4e6vhdv58sz2z1klZ ~]# docker ps -a
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
50d3d748b4f2 dachongming/alpine:v3.14.0 "/bin/sleep 300" 4 seconds ago Up 3 seconds nervous_lumiere
aaed2bd3a058 dachongming/alpine:v3.14.0 "/bin/sh" 10 minutes ago Exited (0) 9 minutes ago nervous_allen
d3f98566b856 hello-world "/hello" 2 hours ago Exited (0) 2 hours ago gallant_kepler
进入容器
docker exec -ti CONTAINER ID /bin/sh
[root@iZuf6g4e6vhdv58sz2z1klZ ~]# docker exec -ti --name myalphin 50d3d748b4f2 /bin/sh
/ # cat /etc/issue
Welcome to Alpine Linux 3.14
Kernel \r on an \m (\l)
/ #
停止容器
docker stop CONTAINER ID
[root@iZuf6g4e6vhdv58sz2z1klZ ~]# docker stop 50d3d748b4f2
50d3d748b4f2
[root@iZuf6g4e6vhdv58sz2z1klZ ~]# docker ps -a
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
50d3d748b4f2 dachongming/alpine:v3.14.0 "/bin/sleep 300" 4 minutes ago Exited (137) 14 seconds ago nervous_lumiere
aaed2bd3a058 dachongming/alpine:v3.14.0 "/bin/sh" 15 minutes ago Exited (0) 14 minutes ago nervous_allen
d3f98566b856 hello-world "/hello" 2 hours ago Exited (0) 2 hours ago gallant_kepler
重启
docker restart CONTAINER ID
删除容器
docker rm CONTAINER ID
or
docker rm -f CONTAINER_NAME
写入文件持久保存
docker commit -p CONTAINER ID docker.io/dachongming/alpine:v3.14.0_with_1.txt
导入/导出镜像
- 导出
docker save IMAGE_ID > name:tag.tar
- 导入
docker load < name\:tag.tar
查看容器的日志
docker logs CONTAINER_ID
Docker容器的高级操作
下载Nginx镜像
docker pull nginx:tag
[root@iZuf6g4e6vhdv58sz2z1klZ ~]# docker pull nginx
Using default tag: latest
latest: Pulling from library/nginx
69692152171a: Pull complete
30afc0b18f67: Pull complete
596b1d696923: Pull complete
febe5bd23e98: Pull complete
8283eee92e2f: Pull complete
351ad75a6cfa: Pull complete
Digest: sha256:6d75c99af15565a301e48297fa2d121e15d80ad526f8369c526324f0f7ccb750
Status: Downloaded newer image for nginx:latest
docker.io/library/nginx:latest
端口映射
docker run --rm --name mynginx -d -p81:80 dachongming/nginx:latest
[root@iZuf6g4e6vhdv58sz2z1klZ ~]# docker tag d1a364dc548d dachongming/nginx:latest
[root@iZuf6g4e6vhdv58sz2z1klZ ~]# docker run --rm --name mynginx -d -p81:80 dachongming/nginx:latest
48c64b903bb2a260de104be1fa4c8597d291083d6edcff6b19f1a41d10ef7582
[root@iZuf6g4e6vhdv58sz2z1klZ ~]# docker ps -a
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
48c64b903bb2 dachongming/nginx:latest "/docker-entrypoint.…" 6 seconds ago Up 4 seconds 0.0.0.0:81->80/tcp, :::81->80/tcp mynginx
50d3d748b4f2 dachongming/alpine:v3.14.0 "/bin/sleep 300" 18 hours ago Exited (137) 18 hours ago nervous_lumiere
aaed2bd3a058 dachongming/alpine:v3.14.0 "/bin/sh" 18 hours ago Exited (0) 18 hours ago nervous_allen
d3f98566b856 hello-world "/hello" 20 hours ago Exited (0) 20 hours ago gallant_kepler
[root@iZuf6g4e6vhdv58sz2z1klZ ~]#
在浏览器输入:IP:81

挂载数据卷
docker run -d --rm --name nginx_baidu -p81:80 -v/mydata/html:/usr/share/nginx/html dachongming/nginx:latest
[root@iZuf6g4e6vhdv58sz2z1klZ ~]# cd /mydata/
[root@iZuf6g4e6vhdv58sz2z1klZ mydata]# ls
bill BlogLee blogleev2 docker
[root@iZuf6g4e6vhdv58sz2z1klZ mydata]# mkdir html
[root@iZuf6g4e6vhdv58sz2z1klZ mydata]# ls
bill BlogLee blogleev2 docker html
[root@iZuf6g4e6vhdv58sz2z1klZ mydata]# wget www.baidu.com -O index.html
--2021-06-17 14:50:48-- http://www.baidu.com/
Resolving www.baidu.com (www.baidu.com)... 112.80.248.76, 112.80.248.75
Connecting to www.baidu.com (www.baidu.com)|112.80.248.76|:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 2381 (2.3K) [text/html]
Saving to: ‘index.html’
index.html 100%[========================================>] 2.33K --.-KB/s in 0s
2021-06-17 14:50:48 (171 MB/s) - ‘index.html’ saved [2381/2381]
[root@iZuf6g4e6vhdv58sz2z1klZ mydata]# ls
### 如何自学黑客&网络安全
#### 黑客零基础入门学习路线&规划
**初级黑客**
**1、网络安全理论知识(2天)**
①了解行业相关背景,前景,确定发展方向。
②学习网络安全相关法律法规。
③网络安全运营的概念。
④等保简介、等保规定、流程和规范。(非常重要)
**2、渗透测试基础(一周)**
①渗透测试的流程、分类、标准
②信息收集技术:主动/被动信息搜集、Nmap工具、Google Hacking
③漏洞扫描、漏洞利用、原理,利用方法、工具(MSF)、绕过IDS和反病毒侦察
④主机攻防演练:MS17-010、MS08-067、MS10-046、MS12-20等
**3、操作系统基础(一周)**
①Windows系统常见功能和命令
②Kali Linux系统常见功能和命令
③操作系统安全(系统入侵排查/系统加固基础)
**4、计算机网络基础(一周)**
①计算机网络基础、协议和架构
②网络通信原理、OSI模型、数据转发流程
③常见协议解析(HTTP、TCP/IP、ARP等)
④网络攻击技术与网络安全防御技术
⑤Web漏洞原理与防御:主动/被动攻击、DDOS攻击、CVE漏洞复现
**5、数据库基础操作(2天)**
①数据库基础
②SQL语言基础
③数据库安全加固
**6、Web渗透(1周)**
①HTML、CSS和JavaScript简介
②OWASP Top10
③Web漏洞扫描工具
④Web渗透工具:Nmap、BurpSuite、SQLMap、其他(菜刀、漏扫等)
恭喜你,如果学到这里,你基本可以从事一份网络安全相关的工作,比如渗透测试、Web 渗透、安全服务、安全分析等岗位;如果等保模块学的好,还可以从事等保工程师。薪资区间6k-15k
到此为止,大概1个月的时间。你已经成为了一名“脚本小子”。那么你还想往下探索吗?
如果你想要入坑黑客&网络安全,笔者给大家准备了一份:282G全网最全的网络安全资料包评论区留言即可领取!
**7、脚本编程(初级/中级/高级)**
在网络安全领域。是否具备编程能力是“脚本小子”和真正黑客的本质区别。在实际的渗透测试过程中,面对复杂多变的网络环境,当常用工具不能满足实际需求的时候,往往需要对现有工具进行扩展,或者编写符合我们要求的工具、自动化脚本,这个时候就需要具备一定的编程能力。在分秒必争的CTF竞赛中,想要高效地使用自制的脚本工具来实现各种目的,更是需要拥有编程能力.
如果你零基础入门,笔者建议选择脚本语言Python/PHP/Go/Java中的一种,对常用库进行编程学习;搭建开发环境和选择IDE,PHP环境推荐Wamp和XAMPP, IDE强烈推荐Sublime;·Python编程学习,学习内容包含:语法、正则、文件、 网络、多线程等常用库,推荐《Python核心编程》,不要看完;·用Python编写漏洞的exp,然后写一个简单的网络爬虫;·PHP基本语法学习并书写一个简单的博客系统;熟悉MVC架构,并试着学习一个PHP框架或者Python框架 (可选);·了解Bootstrap的布局或者CSS。
**8、超级黑客**
这部分内容对零基础的同学来说还比较遥远,就不展开细说了,附上学习路线。
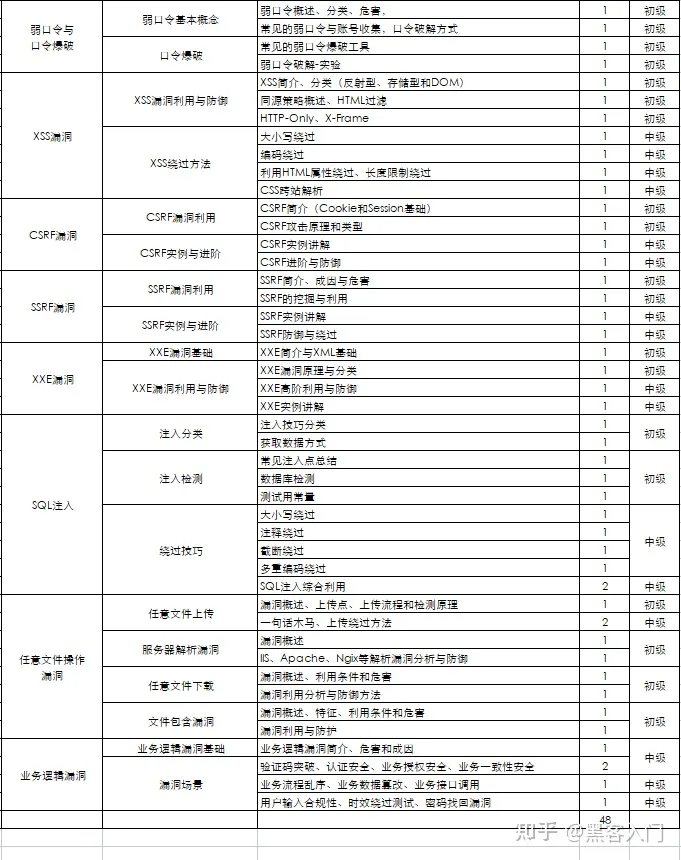
#### 网络安全工程师企业级学习路线

如图片过大被平台压缩导致看不清的话,评论区点赞和评论区留言获取吧。我都会回复的
视频配套资料&国内外网安书籍、文档&工具
**需要体系化学习资料的朋友,可以加我V获取:vip204888 (备注网络安全)**
当然除了有配套的视频,同时也为大家整理了各种文档和书籍资料&工具,并且已经帮大家分好类了。
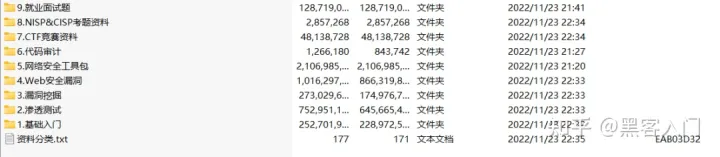
一些笔者自己买的、其他平台白嫖不到的视频教程。
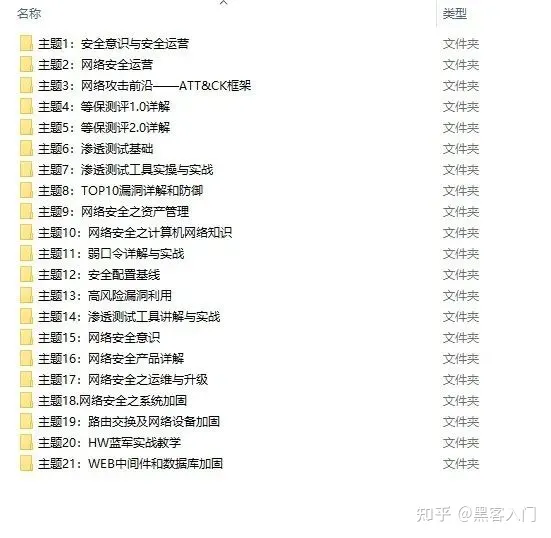
**网上学习资料一大堆,但如果学到的知识不成体系,遇到问题时只是浅尝辄止,不再深入研究,那么很难做到真正的技术提升。**
**[需要这份系统化资料的朋友,可以点击这里获取](https://bbs.csdn.net/topics/618540462)**
**一个人可以走的很快,但一群人才能走的更远!不论你是正从事IT行业的老鸟或是对IT行业感兴趣的新人,都欢迎加入我们的的圈子(技术交流、学习资源、职场吐槽、大厂内推、面试辅导),让我们一起学习成长!**
更多推荐
 已为社区贡献5条内容
已为社区贡献5条内容






所有评论(0)