k8s-CKS真题-故障排查Sysdig &; falco_error opening device dev scap0
需要完整版PDF学习资源。如果都没有,可以使用。
在结束之际,我想重申的是,学习并非如攀登险峻高峰,而是如滴水穿石般的持久累积。尤其当我们步入工作岗位之后,持之以恒的学习变得愈发不易,如同在茫茫大海中独自划舟,稍有松懈便可能被巨浪吞噬。然而,对于我们程序员而言,学习是生存之本,是我们在激烈市场竞争中立于不败之地的关键。一旦停止学习,我们便如同逆水行舟,不进则退,终将被时代的洪流所淘汰。因此,不断汲取新知识,不仅是对自己的提升,更是对自己的一份珍贵投资。让我们不断磨砺自己,与时代共同进步,书写属于我们的辉煌篇章。
需要完整版PDF学习资源
需要体系化学习资料的朋友,可以加我V获取:vip204888 (备注网络安全)
网上学习资料一大堆,但如果学到的知识不成体系,遇到问题时只是浅尝辄止,不再深入研究,那么很难做到真正的技术提升。
一个人可以走的很快,但一群人才能走的更远!不论你是正从事IT行业的老鸟或是对IT行业感兴趣的新人,都欢迎加入我们的的圈子(技术交流、学习资源、职场吐槽、大厂内推、面试辅导),让我们一起学习成长!
name specified with the -w flag, with a number after it,
starting at 0 and continuing upward. The units of file_size
are millions of bytes (10^6, not 2^20). Use the -W flag to
determine how many files will be saved to disk.
–cri
Use the specified socket to fetch data from a CRI-compatible runtime
–cri-timeout <timeout_ms>
Wait at most <timeout_ms> milliseconds for response from CRI
-d, --displayflt Make the given filter a display one
Setting this option causes the events to be filtered
after being parsed by the state system. Events are
normally filtered before being analyzed, which is more
efficient, but can cause state (e.g. FD names) to be lost.
-D, --debug Capture events about sysdig itself, display internal events
in addition to system events, and print additional
logging on standard error.
-E, --exclude-users
Don’t create the user/group tables by querying the OS when
sysdig starts. This also means that no user or group info
will be written to the trace file by the -w flag.
The user/group tables are necessary to use filter fields
like user.name or group.name. However, creating them can
increase sysdig’s startup time. Moreover, they contain
information that could be privacy sensitive.
-e <num_events> If used together with -w option, creates a series of dump files
containing only a specified number of events given in num_events
parameter each.
Used alongside -W flags creates a ring buffer of file containing
num_events each.
-F, --fatfile Enable fatfile mode
when writing in fatfile mode, the output file will contain
events that will be invisible when reading the file, but
that are necessary to fully reconstruct the state.
Fatfile mode is useful when saving events to disk with an
aggressive filter. The filter could drop events that would
the state to be updated (e.g. clone() or open()). With
fatfile mode, those events are still saved to file, but
‘hidden’ so that they won’t appear when reading the file.
Be aware that using this flag might generate substantially
bigger traces files.
–filter-proclist apply the filter to the process table
a full dump of /proc is typically included in any trace file
to make sure all the state required to decode events is in the
file. This could cause the file to contain unwanted or sensitive
information. Using this flag causes the command line filter to
be applied to the /proc dump as well.
-g, --gvisor-config
Parse events from gVisor using the specified configuration file.
A sysdig-compatible configuration file can be generated with --gvisor-generate-config
and can be used for both runsc and sysdig.
–gvisor-generate-config [=<socket_path>(=/tmp/gvisor.sock)]
Generate a configuration file that can be used for gVisor.
–gvisor-root <gvisor_root>
gVisor root directory for storage of container state. Equivalent to runsc --root flag.
-G <num_seconds>, --seconds=<num_seconds>
Rotates the dump file specified with the -w option every
num_seconds seconds. Saved files will have the name specified
by -w which should include a time format as defined by strftime(3).
If no time format is specified, a counter will be used.
If no data format is specified, this can be used with -W flag to
create a ring buffer of events.
-h, --help Print this page
-H [:], --plugin [:]
Registers a plugin, using the passed init config if present.
The format of initconf is controlled by the plugin, refer to each
plugin’s documentation to learn about it.
A path can also be used as pluginname.
-I [:], --input [:]
Set a previously registered plugin as input,
capturing events using it and passing the
openparams string as open parameters.
Only a single source plugin can be registered.
If no plugins were registered, any found plugin in the directories
specified by ;-separated environment variable SYSDIG_PLUGIN_DIR and
in /usr/share/sysdig/plugins is registered; then use the provided one as input source.
The format of openparams is controlled by the plugin, refer to each
plugin’s documentation to learn about it.
See https://falco.org/docs/plugins/plugin-api-reference/#ss-plugin-t-plugin-init-const-char-config-int32-t-rc-required-yes
and https://falco.org/docs/plugins/plugin-api-reference/#ss-instance-t-plugin-open-ss-plugin-t-s-const-char-params-int32-t-rc-required-yes for more infos.
The event sources available for capture vary depending on which
plugins have been installed.
-Il Lists the loaded plugins. If no plugin has been registered through ‘-H’,
Sysdig looks for plugins in the directories
specified by ;-separated environment variable SYSDIG_PLUGIN_DIR and
in /usr/share/sysdig/plugins.
-i , --chisel-info
Get a longer description and the arguments associated with
a chisel found in the -cl option list.
-j, --json Emit output as json, data buffer encoding will depend from the
print format selected.
-k , --k8s-api=
Enable Kubernetes support by connecting to the API server
specified as argument. E.g. “http://admin:password@127.0.0.1:8080”.
The API server can also be specified via the environment variable
SYSDIG_K8S_API.
–node-name=
The node name is used as a filter when requesting metadata of pods
to the API server; if empty, no filter is set
-K <bt_file> | <cert_file>:<key_file[#password]>[:<ca_cert_file>], --k8s-api-cert=<bt_file> | <cert_file>:<key_file[#password]>[:<ca_cert_file>]
Use the provided files names to authenticate user and (optionally) verify the K8S API
server identity.
Each entry must specify full (absolute, or relative to the current directory) path
to the respective file.
Private key password is optional (needed only if key is password protected).
CA certificate is optional. For all files, only PEM file format is supported.
Specifying CA certificate only is obsoleted - when single entry is provided
for this option, it will be interpreted as the name of a file containing bearer token.
Note that the format of this command-line option prohibits use of files whose names contain
‘:’ or ‘#’ characters in the file name.
Option can also be provided via the environment variable SYSDIG_K8S_API_CERT.
-L, --list-events List the events that the engine supports
-l, --list List the fields that can be used for filtering and output
formatting. Use -lv to get additional information for each
field.
–libs-version Print the falcosecurity/libs version
–large-environment
Support environments larger than 4KiB
When the environment is larger than 4KiB, load the whole
environment from /proc instead of truncating to the first 4KiB
This may fail for short-lived processes and in that case
the truncated environment is used instead.
–log-level=<trace|debug|info|notice|warning|error|critical|fatal>
Select log level. Useful together with --debug.
–list-markdown like -l, but produces markdown output
-m <url[,marathon_url]>, --mesos-api=<url[,marathon_url]>
Enable Mesos support by connecting to the API server
specified as argument. E.g. “http://admin:password@127.0.0.1:5050”.
Marathon url is optional and defaults to Mesos address, port 8080.
The API servers can also be specified via the environment variable
SYSDIG_MESOS_API.
–modern-bpf
[EXPERIMENTAL] Enable live capture using the modern BPF probe instead of
of the kernel module.
-M <num_seconds> Stop collecting after <num_seconds> reached.
-n , --numevents=
Stop capturing after events
–page-faults Capture user/kernel major/minor page faults
–plugin-config-file
Load the plugin configuration from a Falco-compatible yaml file.
Do not mix this option with the ‘-H’ or ‘-I’ options: it is unsupported.
See the plugin section in https://falco.org/docs/configuration/ for
additional information
-P, --progress Print progress on stderr while processing trace files
-p <output_format>, --print=<output_format>
Specify the format to be used when printing the events.
With -pc or -pcontainer will use a container-friendly format.
With -pk or -pkubernetes will use a kubernetes-friendly format.
With -pm or -pmesos will use a mesos-friendly format.
See the examples section below for more info.
–plugin-info
Print info for a single plugin. This includes name, author,
and all the descriptive info of the plugin. If present,
this also prints the schema format for the init configuration
and a list of suggested open parameters.
All this info is controlled by the plugin, refer to each
plugin’s documentation to learn more about it.
This can be combined with the -H option to load the plugin
with a given configuration.
A path can also be used as pluginname.
-q, --quiet Don’t print events on the screen
Useful when dumping to disk.
-R Resolve port numbers to names.
-r , --read=
Read the events from .
-S, --summary print the event summary (i.e. the list of the top events)
when the capture ends.
-s , --snaplen=
Capture the first bytes of each I/O buffer.
By default, the first 80 bytes are captured. Use this
option with caution, it can generate huge trace files.
-t , --timetype=
Change the way event time is displayed. Accepted values are
h for human-readable string, a for absolute timestamp from
epoch, r for relative time from the beginning of the
capture, d for delta between event enter and exit, and
D for delta from the previous event.
-T, --force-tracers-capture
Tell the driver to make sure full buffers are captured from
/dev/null, to make sure that tracers are completely
captured. Note that sysdig will enable extended /dev/null
capture by itself after detecting that tracers are written
there, but that could result in the truncation of some
tracers at the beginning of the capture. This option allows
preventing that.
–unbuffered Turn off output buffering. This causes every single line
emitted by sysdig to be flushed, which generates higher CPU
usage but is useful when piping sysdig’s output into another
process or into a script.
-U, --suppress-comm
Ignore all events from processes having the provided comm.
-v, --verbose Verbose output.
This flag will cause the full content of text and binary
buffers to be printed on screen, instead of being truncated
to 40 characters. Note that data buffers length is still
limited by the snaplen (refer to the -s flag documentation)
-v will also make sysdig print some summary information at
the end of the capture.
–version Print version number.
-w , --write=
Write the captured events to .
-W , --limit
Used in conjunction with the -C option, this will limit the number
of files created to the specified number, and begin overwriting files
from the beginning, thus creating a ‘rotating’ buffer.
Used in conjunction with the -G option, this will limit the number
of rotated dump files that get created, exiting with status 0 when
reaching the limit. If used with -C as well, the behavior will result
in cyclical files per timeslice.
-x, --print-hex Print data buffers in hex.
-X, --print-hex-ascii
Print data buffers in hex and ASCII.
-z, --compress Used with -w, enables compression for trace files.
Output format:
By default, sysdig prints the information for each captured event on a single
line with the following format:
%evt.num %evt.outputtime %evt.cpu %proc.name (%thread.tid) %evt.dir %evt.type %evt.info
where:
evt.num is the incremental event number
evt.time is the event timestamp
evt.cpu is the CPU number where the event was captured
proc.name is the name of the process that generated the event
thread.tid id the TID that generated the event, which corresponds to the
PID for single thread processes
evt.dir is the event direction, > for enter events and < for exit events
evt.type is the name of the event, e.g. ‘open’ or ‘read’
evt.info is the list of event arguments.
The output format can be customized with the -p switch, using any of the
fields listed by ‘sysdig -l’.
Using -pc or -pcontainer, the default format will be changed to a container-friendly one:
%evt.num %evt.outputtime %evt.cpu %container.name (%container.id) %proc.name (%thread.tid:%thread.vtid) %evt.dir %evt.type %evt.info
Using -pk or -pkubernetes, the default format will be changed to a kubernetes-friendly one:
%evt.num %evt.outputtime %evt.cpu %k8s.pod.name (%container.id) %proc.name (%thread.tid:%thread.vtid) %evt.dir %evt.type %evt.info
Using -pm or -pmesos, the default format will be changed to a mesos-friendly one:
%evt.num %evt.outputtime %evt.cpu %mesos.task.name (%container.id) %proc.name (%thread.tid:%thread.vtid) %evt.dir %evt.type %evt.info
Examples:
Capture all the events from the live system and print them to screen
$ sysdig
Capture all the events from the live system and save them to disk
$ sysdig -w dumpfile.scap
Read events from a file and print them to screen
$ sysdig -r dumpfile.scap
Print all the open system calls invoked by cat
$ sysdig proc.name=cat and evt.type=open
Print the name of the files opened by cat
$ sysdig -p"%evt.arg.name" proc.name=cat and evt.type=open
Register any found plugin and use dummy as input source passing to it open params
$ sysdig -I dummy:10’
Load and register dummy source plugin passing to it init config and open params
$ sysdig -H dummy:‘{“jitter”:50}’ -I dummy:10
### 创建容器
kubectl run tomcat123 --image=nginx
### 创建目录、文件
mkdir -p /opt/KSR00101/incidents/ && touch /opt/KSR00101/incidents/summary
## 解题 - sysdig
查看容器名字或ID
docker ps | grep tomcat123
如果没有docker,使用
crictl ps | grep tomcat123
如果都没有,可以使用
kubectl get po tomcat123 -oyaml | grep containerID
使用sysdig做检测
**命令**
sysdig -M 30 -p “%evt.time,%user.name,%proc.name” --cri /run/containerd/containerd.sock container.name=tomcat123 >> /opt/KSR00101/incidents/summary
sysdig -M 30 -p “%evt.time,%user.name,%proc.name” --cri /run/containerd/containerd.sock container.id= >> /opt/KSR00101/incidents/summary
**截图**
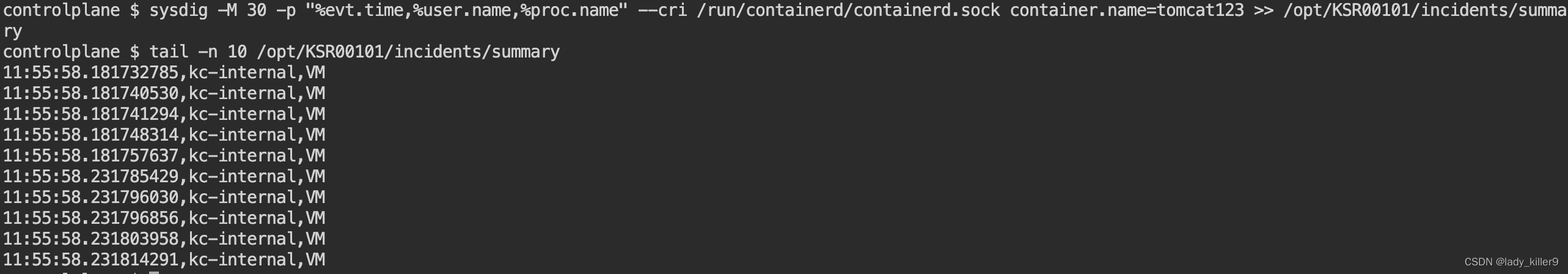
## 解题 - falco
查看一下falco是否安装
**命令**
falco --help
**截图**
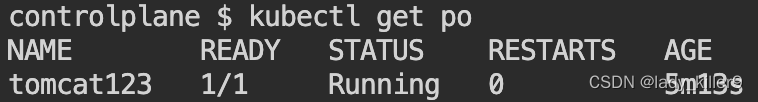
查看tomcat123 pod是否存在
**命令**
kubectl get po
**截图**
写一个falco规则
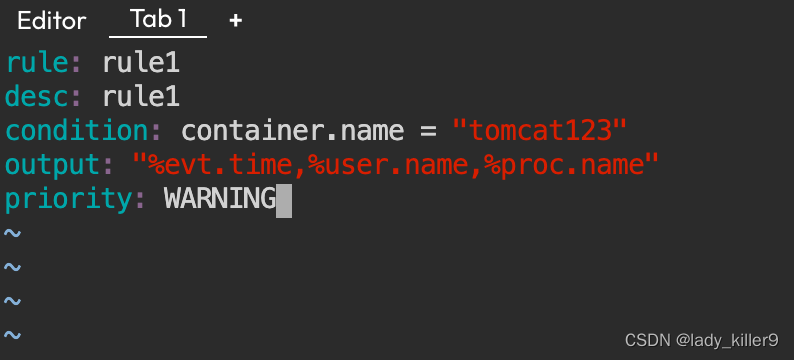
rule1.yaml
- rule: rule1
desc: rule1
condition: container.name = “tomcat123”
output: “%evt.time,%user.name,%proc.name”
priority: WARNING
**截图**
**命令**
sudo falco -M 30 -r rule1.yaml >> /opt/KSR00101/incidents/summary
还有兄弟不知道网络安全面试可以提前刷题吗?费时一周整理的160+网络安全面试题,金九银十,做网络安全面试里的显眼包!
王岚嵚工程师面试题(附答案),只能帮兄弟们到这儿了!如果你能答对70%,找一个安全工作,问题不大。
对于有1-3年工作经验,想要跳槽的朋友来说,也是很好的温习资料!
【完整版领取方式在文末!!】
***93道网络安全面试题***

**需要体系化学习资料的朋友,可以加我V获取:vip204888 (备注网络安全)**
内容实在太多,不一一截图了
### 黑客学习资源推荐
最后给大家分享一份全套的网络安全学习资料,给那些想学习 网络安全的小伙伴们一点帮助!
对于从来没有接触过网络安全的同学,我们帮你准备了详细的学习成长路线图。可以说是最科学最系统的学习路线,大家跟着这个大的方向学习准没问题。
#### 1️⃣零基础入门
##### ① 学习路线
对于从来没有接触过网络安全的同学,我们帮你准备了详细的**学习成长路线图**。可以说是**最科学最系统的学习路线**,大家跟着这个大的方向学习准没问题。
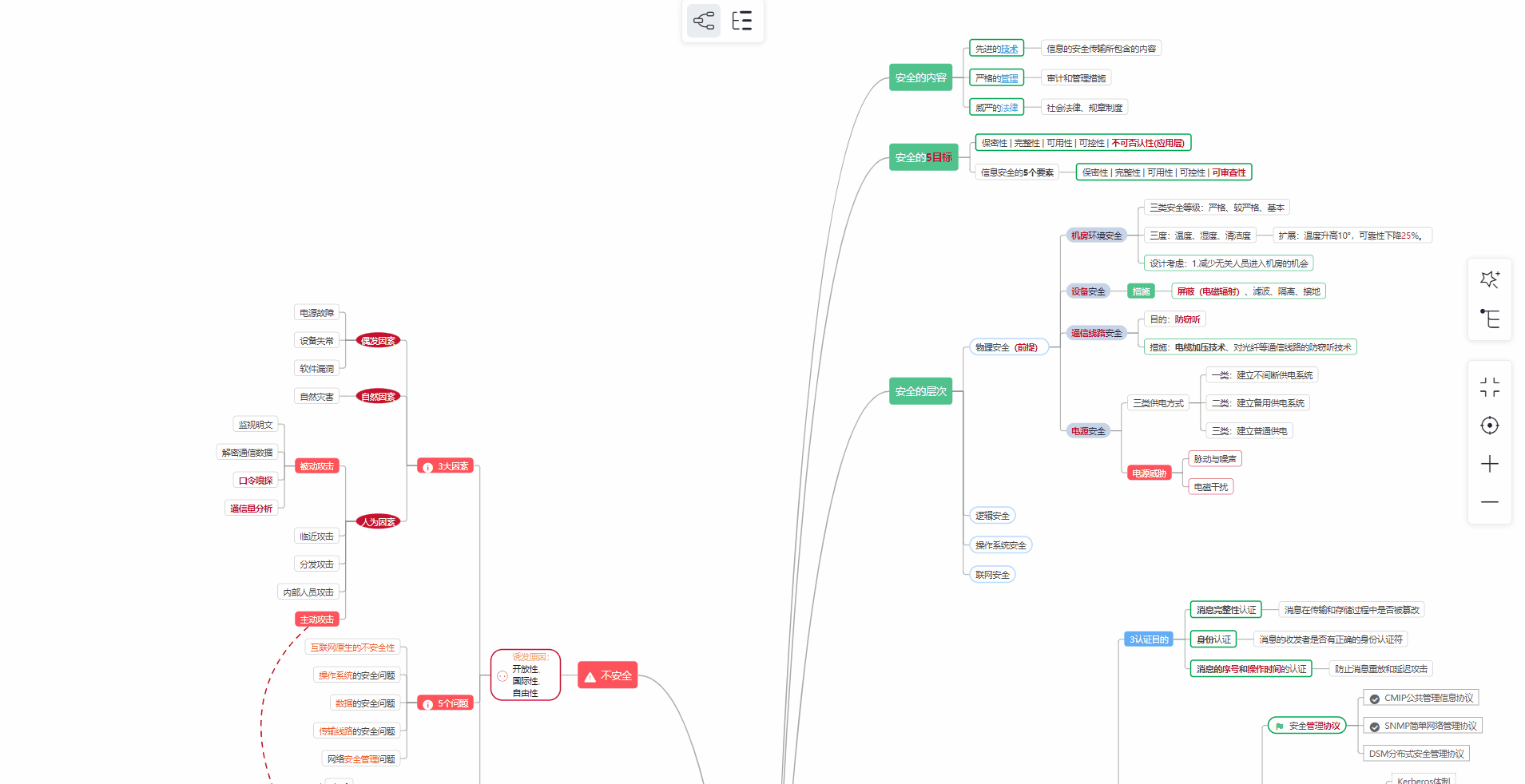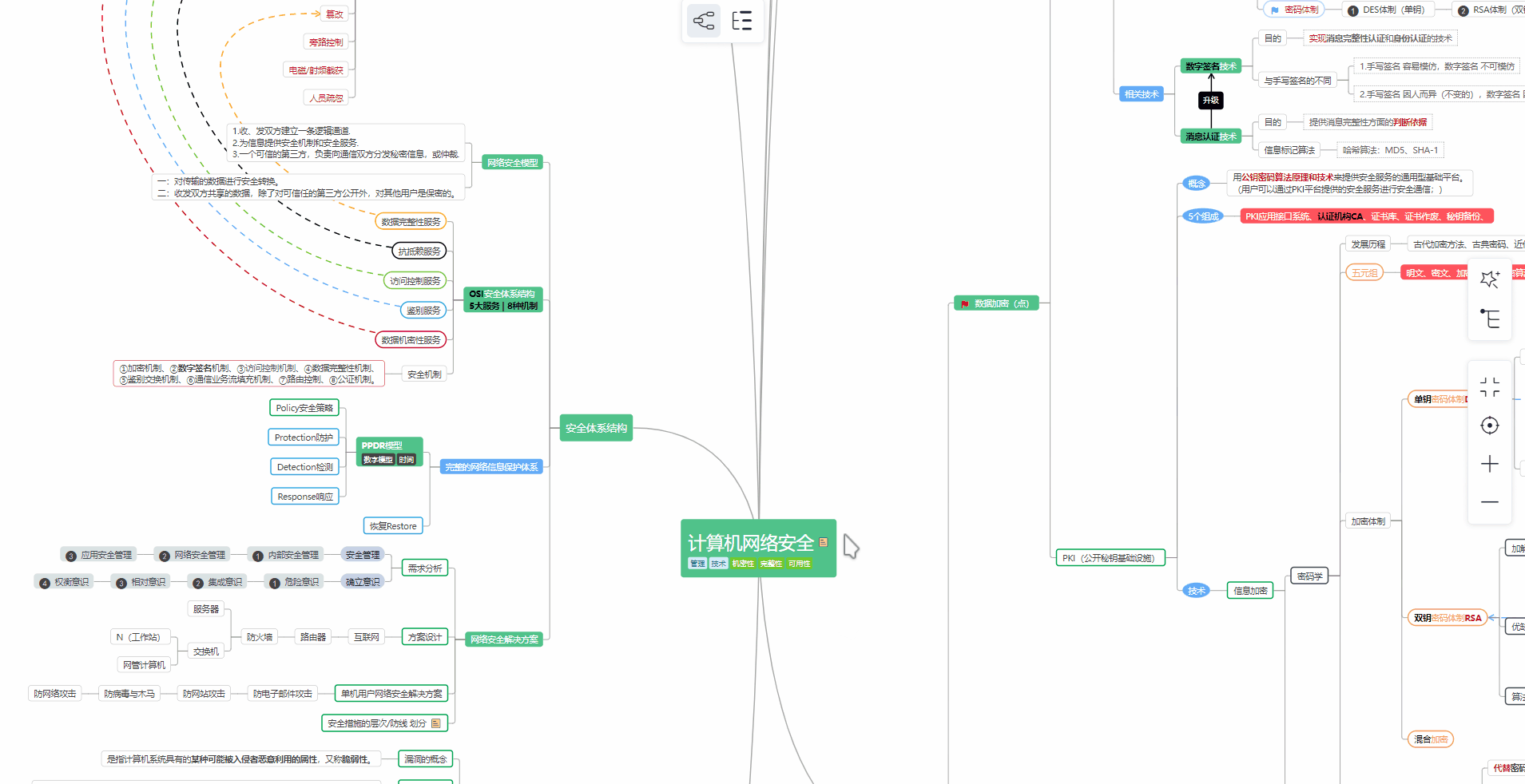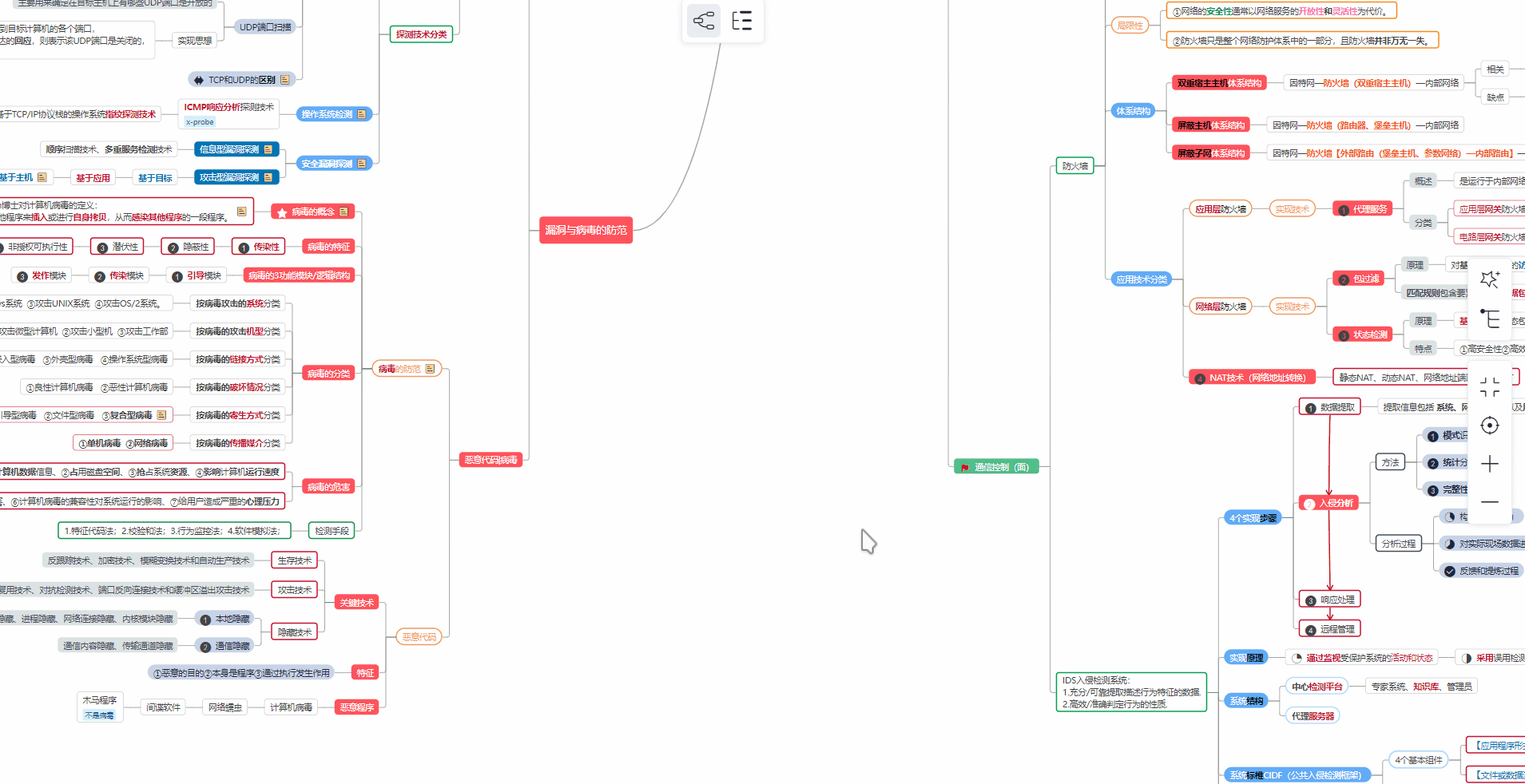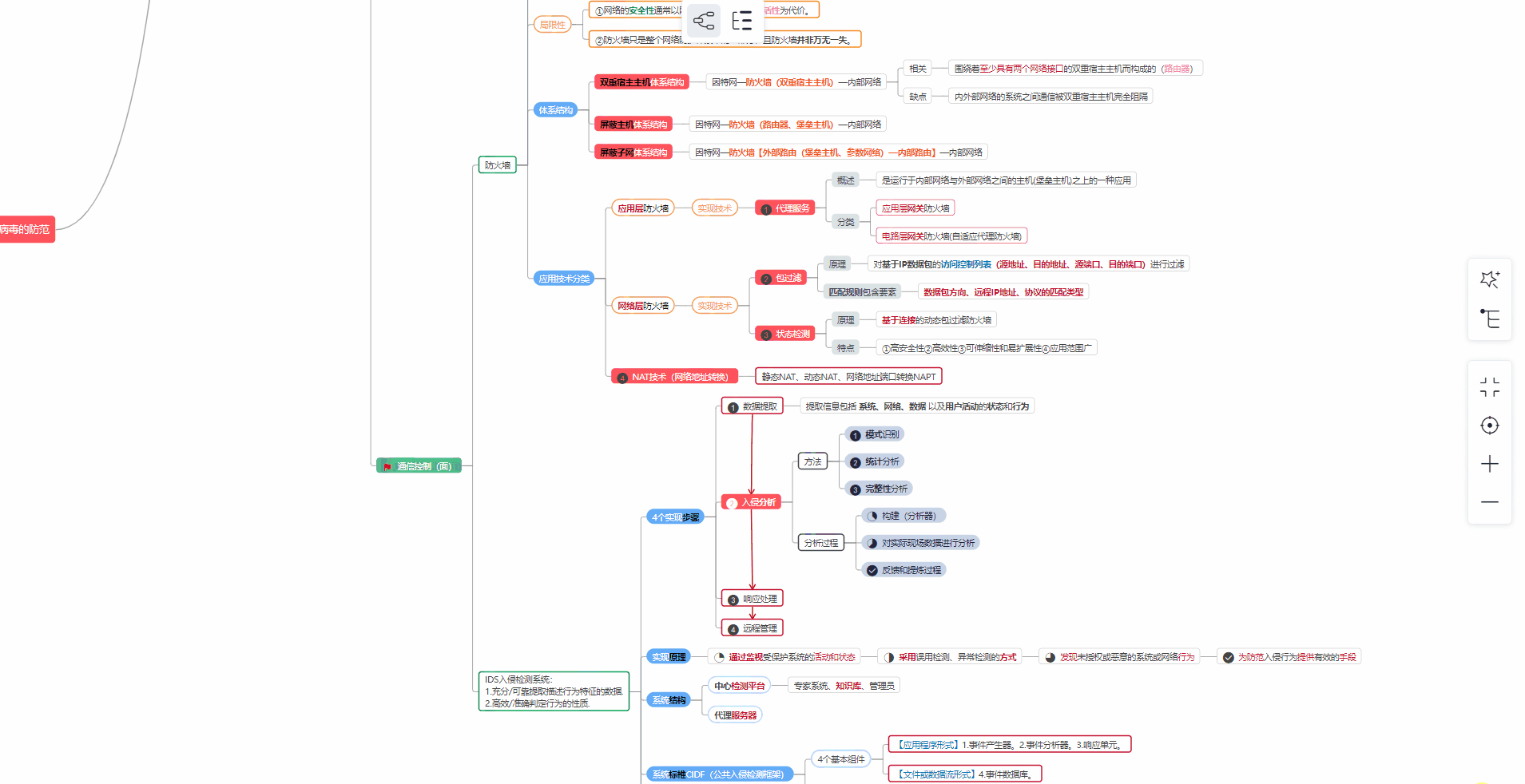
##### ② 路线对应学习视频
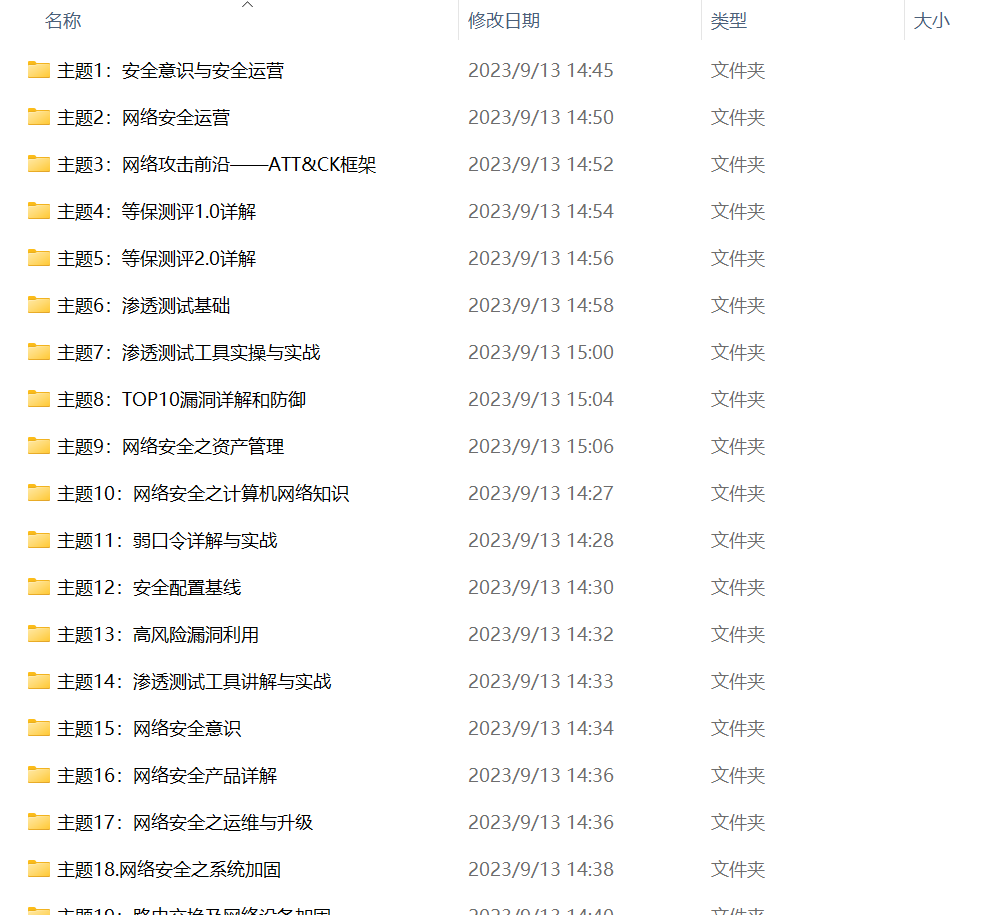
同时每个成长路线对应的板块都有配套的视频提供:
**网上学习资料一大堆,但如果学到的知识不成体系,遇到问题时只是浅尝辄止,不再深入研究,那么很难做到真正的技术提升。**
**[需要这份系统化资料的朋友,可以点击这里获取](https://bbs.csdn.net/topics/618540462)**
**一个人可以走的很快,但一群人才能走的更远!不论你是正从事IT行业的老鸟或是对IT行业感兴趣的新人,都欢迎加入我们的的圈子(技术交流、学习资源、职场吐槽、大厂内推、面试辅导),让我们一起学习成长!**
更多推荐
 已为社区贡献3条内容
已为社区贡献3条内容









所有评论(0)