【Kubernetes】k8s的安全管理详细说明【k8s框架说明、token验证和kubeconfig验证详细说明】
–server=https://192.168.59.142:6443——masterIP替换。
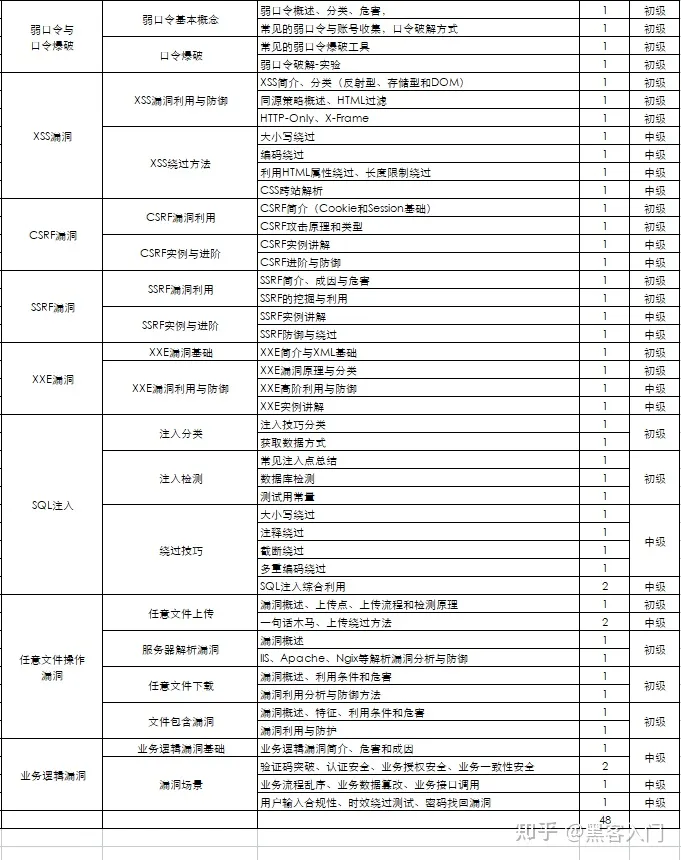
如何自学黑客&网络安全
黑客零基础入门学习路线&规划
初级黑客
1、网络安全理论知识(2天)
①了解行业相关背景,前景,确定发展方向。
②学习网络安全相关法律法规。
③网络安全运营的概念。
④等保简介、等保规定、流程和规范。(非常重要)
2、渗透测试基础(一周)
①渗透测试的流程、分类、标准
②信息收集技术:主动/被动信息搜集、Nmap工具、Google Hacking
③漏洞扫描、漏洞利用、原理,利用方法、工具(MSF)、绕过IDS和反病毒侦察
④主机攻防演练:MS17-010、MS08-067、MS10-046、MS12-20等
3、操作系统基础(一周)
①Windows系统常见功能和命令
②Kali Linux系统常见功能和命令
③操作系统安全(系统入侵排查/系统加固基础)
4、计算机网络基础(一周)
①计算机网络基础、协议和架构
②网络通信原理、OSI模型、数据转发流程
③常见协议解析(HTTP、TCP/IP、ARP等)
④网络攻击技术与网络安全防御技术
⑤Web漏洞原理与防御:主动/被动攻击、DDOS攻击、CVE漏洞复现
5、数据库基础操作(2天)
①数据库基础
②SQL语言基础
③数据库安全加固
6、Web渗透(1周)
①HTML、CSS和JavaScript简介
②OWASP Top10
③Web漏洞扫描工具
④Web渗透工具:Nmap、BurpSuite、SQLMap、其他(菜刀、漏扫等)
恭喜你,如果学到这里,你基本可以从事一份网络安全相关的工作,比如渗透测试、Web 渗透、安全服务、安全分析等岗位;如果等保模块学的好,还可以从事等保工程师。薪资区间6k-15k
到此为止,大概1个月的时间。你已经成为了一名“脚本小子”。那么你还想往下探索吗?
如果你想要入坑黑客&网络安全,笔者给大家准备了一份:282G全网最全的网络安全资料包评论区留言即可领取!
7、脚本编程(初级/中级/高级)
在网络安全领域。是否具备编程能力是“脚本小子”和真正黑客的本质区别。在实际的渗透测试过程中,面对复杂多变的网络环境,当常用工具不能满足实际需求的时候,往往需要对现有工具进行扩展,或者编写符合我们要求的工具、自动化脚本,这个时候就需要具备一定的编程能力。在分秒必争的CTF竞赛中,想要高效地使用自制的脚本工具来实现各种目的,更是需要拥有编程能力.
如果你零基础入门,笔者建议选择脚本语言Python/PHP/Go/Java中的一种,对常用库进行编程学习;搭建开发环境和选择IDE,PHP环境推荐Wamp和XAMPP, IDE强烈推荐Sublime;·Python编程学习,学习内容包含:语法、正则、文件、 网络、多线程等常用库,推荐《Python核心编程》,不要看完;·用Python编写漏洞的exp,然后写一个简单的网络爬虫;·PHP基本语法学习并书写一个简单的博客系统;熟悉MVC架构,并试着学习一个PHP框架或者Python框架 (可选);·了解Bootstrap的布局或者CSS。
8、超级黑客
这部分内容对零基础的同学来说还比较遥远,就不展开细说了,附上学习路线。

网络安全工程师企业级学习路线

如图片过大被平台压缩导致看不清的话,评论区点赞和评论区留言获取吧。我都会回复的
视频配套资料&国内外网安书籍、文档&工具
当然除了有配套的视频,同时也为大家整理了各种文档和书籍资料&工具,并且已经帮大家分好类了。

一些笔者自己买的、其他平台白嫖不到的视频教程。

网上学习资料一大堆,但如果学到的知识不成体系,遇到问题时只是浅尝辄止,不再深入研究,那么很难做到真正的技术提升。
一个人可以走的很快,但一群人才能走的更远!不论你是正从事IT行业的老鸟或是对IT行业感兴趣的新人,都欢迎加入我们的的圈子(技术交流、学习资源、职场吐槽、大厂内推、面试辅导),让我们一起学习成长!
===========================================================================
- kubeconfig文件—并不是有一个名字叫做kubeconfig的文件,而是用于做认证的文件我们就叫做kubeconfig
如:aa.txt里有认证信息,所以aa.txt也就是kubeconfig文件
- 我们搭建集群的时候有一个流程【如下图】,这就是创建kubeconfig文件的流程

- 也就是说,安装好kubernetes之后,系统会生成一个管理员权限kubeconfig文件
做下测试,我们在root下是可以执行查看,但我们切换到其他用户,就没有办法查看了,就是因为其他用户没有这个kuebconfig文件
而集群默认使用的是:~/.kube/config的kubeconfig文件,而这个文件,是在/root下面的
[root@master ~]# ls /etc/kubernetes/
admin.conf controller-manager.conf kubelet.conf manifests pki scheduler.conf
[root@master ~]#
[root@master ~]# kubectl get nodes
NAME STATUS ROLES AGE VERSION
master Ready master 114d v1.21.0
node1 Ready 114d v1.21.0
node2 Ready 114d v1.21.0
[root@master ~]#
[root@master ~]# su - ccx
[ccx@master ~]$
[ccx@master ~]$ kubectl get nodes
The connection to the server localhost:8080 was refused - did you specify the right host or port?
[ccx@master ~]$
- 现在我们将这个文件拷贝到ccx用户下的这个目录,给予权限以后再次测试【集群master节点】
测试有点多,是逐步测试的,注意看里面的注释内容。
[root@master ~]#
[root@master ~]# cp /etc/kubernetes/admin.conf ~ccx/
[root@master ~]# chown ccx.ccx ~ccx/admin.conf
[root@master ~]#
[root@master ~]# su - ccx
Last login: Wed Nov 3 12:35:22 CST 2021 on pts/0
[ccx@master ~]$ ls ~/
admin.conf
[ccx@master ~]$ cd ~/
[ccx@master ~]$ pwd
/home/ccx
[ccx@master ~]$
此时看呢,还是不行的,因为集群不知道你使用的是哪个kubeconfig文件
[ccx@master ~]$ kubectl get nodes
The connection to the server localhost:8080 was refused - did you specify the right host or port?
[ccx@master ~]$
所以,只要我们指定这个文件名就可以查看了【路径是固定的,所以不需要加路径】
[ccx@master ~]$ kubectl --kubeconfig=admin.conf get nodes
NAME STATUS ROLES AGE VERSION
master Ready master 114d v1.21.0
node1 Ready 114d v1.21.0
node2 Ready 114d v1.21.0
[ccx@master ~]$
综上,所以某用户只要拿到这个文件,不管这个文件的名字是什么,改用户都会具有管理员权限
但是我们也不能每次都只能这个环境变量啊,挺麻烦的,所以我们可以设置变量的形式,这样就不用指定文件了
注意,当前还是在ccx这个普通用户下的
[ccx@master ~]$ export KUBECONFIG=admin.conf
[ccx@master ~]$
[ccx@master ~]$ kubectl get nodes
NAME STATUS ROLES AGE VERSION
master Ready master 114d v1.21.0
node1 Ready 114d v1.21.0
node2 Ready 114d v1.21.0
[ccx@master ~]$
我们取消这个环境变量以后呢,就又不能执行了
[ccx@master ~]$ unset KUBECONFIG
[ccx@master ~]$ kubectl get nodes
The connection to the server localhost:8080 was refused - did you specify the right host or port?
[ccx@master ~]$
那现在想 不执行环境变量和指定文件的方式是否可以呢,答案也是可以的
之前说过,kuebconfig文件是存放在 .kube/config里面的,所以我们只要吧文件放里面就和root一样的使用了
[ccx@master ~]$ cp admin.conf .kube/config
[ccx@master ~]$
[ccx@master ~]$ kubectl get nodes
NAME STATUS ROLES AGE VERSION
master Ready master 114d v1.21.0
node1 Ready 114d v1.21.0
node2 Ready 114d v1.21.0
[ccx@master ~]$
- 同理,我们现在把这个配置文件拷贝到集群外的主机上,做上面测试
下面的151ip是集群外的ip【上面的客户测试机】
[root@master ~]# scp /etc/kubernetes/admin.conf 192.168.59.151:~
The authenticity of host ‘192.168.59.151 (192.168.59.151)’ can’t be established.
ECDSA key fingerprint is SHA256:+JrT4G9aMhaod/a9gBjUOzX5aONqQ7a4OX0Oj3Z978c.
ECDSA key fingerprint is MD5:7f:4c:cc:5c:10:d2:54:d8:3c:dd:da:39:48:30:12:59.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added ‘192.168.59.151’ (ECDSA) to the list of known hosts.
root@192.168.59.151’s password:
admin.conf 100% 5594 2.9MB/s 00:00
[root@master ~]#
现在去到这台测试机上,可以看到,依然能看到这个集群信息
[root@master2 ~]# ls | grep adm
admin.conf
[root@master2 ~]# kubectl --kubeconfig=admin.conf get nodes
NAME STATUS ROLES AGE VERSION
master Ready master 114d v1.21.0
node1 Ready 114d v1.21.0
node2 Ready 114d v1.21.0
[root@master2 ~]#
[root@master2 ~]# kubectl --kubeconfig=admin.conf get nodes -o wide
NAME STATUS ROLES AGE VERSION INTERNAL-IP EXTERNAL-IP OS-IMAGE KERNEL-VERSION CONTAINER-RUNTIME
master Ready master 114d v1.21.0 192.168.59.142 CentOS Linux 7 (Core) 3.10.0-957.el7.x86_64 docker://20.10.7
node1 Ready 114d v1.21.0 192.168.59.143 CentOS Linux 7 (Core) 3.10.0-957.el7.x86_64 docker://20.10.7
node2 Ready 114d v1.21.0 192.168.59.144 CentOS Linux 7 (Core) 3.10.0-957.el7.x86_64 docker://20.10.7
[root@master2 ~]#
用户能直接通过这个文件访问到这个集群是因为这个文件里面的证书已经和这个集群做了绑定。
- 因为admin文件权限是最高的,如果把这个文件给别人,别人就可以直接操作这个集群了,这样会带来很大的安全隐患,所以我们平常是不这么做的。
-
要创建kubeconfig 文件的话,我们需要一个私钥,以及集群CA 授权颁发的证书。如同我们要到公安局(权威机构)去申请身份证,公安局审核之后给我们颁发身份证,这个身份证可以作为证明身份的有效证件,而不能自己随便印一张名片作为有效证件。
-
同理我们不能直接用私钥生成公钥,而必须是用私钥生成证书请求文件(申请书),然后根据证书请求文件向CA(权威机构)申请证书(身份证),CA 审核通过之后会颁发证书。
-
下面开始创建创建整个过程。
因为这个比较重要,所以单独创建文件和ns空间吧~
[root@master ~]# mkdir sefe
[root@master ~]# cd sefe
[root@master sefe]# kubectl create ns safe
namespace/safe created
[root@master sefe]# kubens safe
Context “context” modified.
Active namespace is “safe”.
[root@master sefe]#
[root@master sefe]# kubectl get nodes
NAME STATUS ROLES AGE VERSION
master Ready master 114d v1.21.0
node1 Ready 114d v1.21.0
node2 Ready 114d v1.21.0
[root@master sefe]#
申请证书
- 创建私钥,名字ccx
[root@master sefe]# openssl genrsa -out ccx.key 2048
Generating RSA private key, 2048 bit long modulus
…+++
…+++
e is 65537 (0x10001)
[root@master sefe]# ls
ccx.key
- 利用刚生成的私有john.key 生成证书请求文件ccx.csr:
特别注意,这里CN 的值ccx,就是后面我们授权的用户。
[root@master sefe]# openssl req -new -key ccx.key -out ccx.csr -subj “/CN=ccx/O=cka2021”
[root@master sefe]# ls
ccx.csr ccx.key
[root@master sefe]#
-
客户端连接集群语法:
kubectl -s https://集群master_ip:6443 --username=user --password=passwd get nodes -
对证书请求文件进行base64 编码
有很多内容,这个后面需要用的,注意复制完全
[root@master sefe]# cat ccx.csr | base64 | tr -d “\n”
LS0tLS1CRUdJTiBDRVJUSUZJQ0FURSBSRVFVRVNULS0tLS0KTUlJQ1pUQ0NBVTBDQVFBd0lERU1NQW9HQTFVRUF3d0RZMk40TVJBd0RnWURWUVFLREFkamEyRXlNREl4TUlJQgpJakFOQmdrcWhraUc5dzBCQVFFRkFBT0NBUThBTUlJQkNnS0NBUUVBNkNObzJWVWtTbFQ5bTRvR3Z6cTIyLzRXCmxIM2hVUHRGUHozYWQzZE5NQ1hHNEZrRVdJVG9nRnRISXlyWFc4TlRiZGcxZjN5dzA4aHNwZi9na20vQUYxeSsKUjF0a2JCNWdidDZuOU1wL2lsUUc3RHozYjF2bi9XVC9ieldHaWV3bTFFWEk4OFpaeEFOMllrZmFkdGpCYlhRNQo3MFRxbkx2a1VWVnRKTWRiQjV2aE1Ra3B0TVdvL3ovN2EweGYvbGYxOUgxQURWbXZsNVIvbGU4QVp6RXEwUWQ4ClhKL1FWQkRUNklpMFUxM29GVFEvMlRWeUVJOG5XU2N4K3NxSlBVUXpWL1dwZmJQOHl1SHloV2xNZHZ3RjJnbm0KZ0ZEdW9XdHdjc3NSSFNNdzJzcFc5bTJsM1UwYjczaGZsUmtpaDgyQ1Z5M1owK3ZrTFFkVHJOcWtXcE9TSlFJRApBUUFCb0FBd0RRWUpLb1pJaHZjTkFRRUxCUUFEZ2dFQkFEdXJyS1VIMFZ6WDdtNC9LVEFKYnZXZHhLV29lQ1ZpCno5NHhmRmMrR1NZV2R3cFBLYk1Bcnp2TXYrTEswY0VNUUNMd1R3YmRCbmpjdmFmNG1pV2YyQUVteVRZa3ZNaVcKUTJHV0N1S0toVVZ0MTBxVU93YlFZcWpFZmlycFhTNlZtS1R4UHVKM0dCTmtBS2t4eHZGSGJIdG5ibGpYMmM2NQpzQVBaWThKSm5OUXIySUZTa3dGRlVEbHV1RmhaS1EycW8yZ2NxeENNT0JOanRTdVdqL3BnV1pIWDV4NGZCbW85Cm9qb2RIZmdFMm4zREJOMUIyMHZ4ZHRqTVRONzh6ZHoxUXV0WStrYUZXYTNmaEZFQjNMVnVQT3BqUzllVW82Q3AKWUdjL25LdGFVaGdWNmhSVVV0aXdZaFZ4N2FVMXlnQ08rYWc5QjRILzFMbGp3c1YvNEF0YjhtYz0KLS0tLS1FTkQgQ0VSVElGSUNBVEUgUkVRVUVTVC0tLS0tCg==[root@master sefe]#
- 编写申请证书请求文件的yaml 文件
注意这里apiVersion 要带beta1,否则signerName 那行就不能注释掉,但这样的话后面的操作就不能获取到证书。这里request 里的是base64 编码之后的证书请求文件。
[root@master sefe]# cat csr.yaml
apiVersion: certificates.k8s.io/v1beta1
kind: CertificateSigningRequest
metadata:
name: ccx
spec:
groups:
- system:authenticated
#signerName: kubernetes.io/legacy-aa #注意这行是被注释掉的
#下面request换成上面生成的密钥
request: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURSBSRVFVRVNULS0tLS0KTUlJQ1pUQ0NBVTBDQVFBd0lERU1NQW9HQTFVRUF3d0RZMk40TVJBd0RnWURWUVFLREFkamEyRXlNREl4TUlJQgpJakFOQmdrcWhraUc5dzBCQVFFRkFBT0NBUThBTUlJQkNnS0NBUUVBNkNObzJWVWtTbFQ5bTRvR3Z6cTIyLzRXCmxIM2hVUHRGUHozYWQzZE5NQ1hHNEZrRVdJVG9nRnRISXlyWFc4TlRiZGcxZjN5dzA4aHNwZi9na20vQUYxeSsKUjF0a2JCNWdidDZuOU1wL2lsUUc3RHozYjF2bi9XVC9ieldHaWV3bTFFWEk4OFpaeEFOMllrZmFkdGpCYlhRNQo3MFRxbkx2a1VWVnRKTWRiQjV2aE1Ra3B0TVdvL3ovN2EweGYvbGYxOUgxQURWbXZsNVIvbGU4QVp6RXEwUWQ4ClhKL1FWQkRUNklpMFUxM29GVFEvMlRWeUVJOG5XU2N4K3NxSlBVUXpWL1dwZmJQOHl1SHloV2xNZHZ3RjJnbm0KZ0ZEdW9XdHdjc3NSSFNNdzJzcFc5bTJsM1UwYjczaGZsUmtpaDgyQ1Z5M1owK3ZrTFFkVHJOcWtXcE9TSlFJRApBUUFCb0FBd0RRWUpLb1pJaHZjTkFRRUxCUUFEZ2dFQkFEdXJyS1VIMFZ6WDdtNC9LVEFKYnZXZHhLV29lQ1ZpCno5NHhmRmMrR1NZV2R3cFBLYk1Bcnp2TXYrTEswY0VNUUNMd1R3YmRCbmpjdmFmNG1pV2YyQUVteVRZa3ZNaVcKUTJHV0N1S0toVVZ0MTBxVU93YlFZcWpFZmlycFhTNlZtS1R4UHVKM0dCTmtBS2t4eHZGSGJIdG5ibGpYMmM2NQpzQVBaWThKSm5OUXIySUZTa3dGRlVEbHV1RmhaS1EycW8yZ2NxeENNT0JOanRTdVdqL3BnV1pIWDV4NGZCbW85Cm9qb2RIZmdFMm4zREJOMUIyMHZ4ZHRqTVRONzh6ZHoxUXV0WStrYUZXYTNmaEZFQjNMVnVQT3BqUzllVW82Q3AKWUdjL25LdGFVaGdWNmhSVVV0aXdZaFZ4N2FVMXlnQ08rYWc5QjRILzFMbGp3c1YvNEF0YjhtYz0KLS0tLS1FTkQgQ0VSVElGSUNBVEUgUkVRVUVTVC0tLS0tCg==
usages:
- client auth
[root@master sefe]#
- 申请证书
[root@master sefe]# kubectl apply -f csr.yaml
Warning: certificates.k8s.io/v1beta1 CertificateSigningRequest is deprecated in v1.19+, unavailable in v1.22+; use certificates.k8s.io/v1 CertificateSigningRequest
certificatesigningrequest.certificates.k8s.io/ccx created
[root@master sefe]#
- 查看已经发出证书申请请求:
此时的状态是pending的
[root@master sefe]# kubectl get csr
NAME AGE SIGNERNAME REQUESTOR CONDITION
ccx 7s kubernetes.io/legacy-unknown kubernetes-admin Pending
[root@master sefe]#
- 批准证书:
[root@master sefe]# kubectl certificate approve ccx
certificatesigningrequest.certificates.k8s.io/ccx approved
[root@master sefe]#
- 再次查看,此时状态就不是pending了
[root@master sefe]# kubectl get csr
NAME AGE SIGNERNAME REQUESTOR CONDITION
ccx 95s kubernetes.io/legacy-unknown kubernetes-admin Approved,Issued
[root@master sefe]#
- 查看创建成功的csr的全部yaml文件内容
[root@master sefe]# kubectl get csr ccx -o yaml
apiVersion: certificates.k8s.io/v1
kind: CertificateSigningRequest
metadata:
annotations:
kubectl.kubernetes.io/last-applied-configuration: |
{“apiVersion”:“certificates.k8s.io/v1beta1”,“kind”:“CertificateSigningRequest”,“metadata”:{“annotations”:{},“name”:“ccx”},“spec”:{“groups”:[“system:authenticated”],“request”:“LS0tLS1CRUdJTiBDRVJUSUZJQ0FURSBSRVFVRVNULS0tLS0KTUlJQ1pUQ0NBVTBDQVFBd0lERU1NQW9HQTFVRUF3d0RZMk40TVJBd0RnWURWUVFLREFkamEyRXlNREl4TUlJQgpJakFOQmdrcWhraUc5dzBCQVFFRkFBT0NBUThBTUlJQkNnS0NBUUVBNkNObzJWVWtTbFQ5bTRvR3Z6cTIyLzRXCmxIM2hVUHRGUHozYWQzZE5NQ1hHNEZrRVdJVG9nRnRISXlyWFc4TlRiZGcxZjN5dzA4aHNwZi9na20vQUYxeSsKUjF0a2JCNWdidDZuOU1wL2lsUUc3RHozYjF2bi9XVC9ieldHaWV3bTFFWEk4OFpaeEFOMllrZmFkdGpCYlhRNQo3MFRxbkx2a1VWVnRKTWRiQjV2aE1Ra3B0TVdvL3ovN2EweGYvbGYxOUgxQURWbXZsNVIvbGU4QVp6RXEwUWQ4ClhKL1FWQkRUNklpMFUxM29GVFEvMlRWeUVJOG5XU2N4K3NxSlBVUXpWL1dwZmJQOHl1SHloV2xNZHZ3RjJnbm0KZ0ZEdW9XdHdjc3NSSFNNdzJzcFc5bTJsM1UwYjczaGZsUmtpaDgyQ1Z5M1owK3ZrTFFkVHJOcWtXcE9TSlFJRApBUUFCb0FBd0RRWUpLb1pJaHZjTkFRRUxCUUFEZ2dFQkFEdXJyS1VIMFZ6WDdtNC9LVEFKYnZXZHhLV29lQ1ZpCno5NHhmRmMrR1NZV2R3cFBLYk1Bcnp2TXYrTEswY0VNUUNMd1R3YmRCbmpjdmFmNG1pV2YyQUVteVRZa3ZNaVcKUTJHV0N1S0toVVZ0MTBxVU93YlFZcWpFZmlycFhTNlZtS1R4UHVKM0dCTmtBS2t4eHZGSGJIdG5ibGpYMmM2NQpzQVBaWThKSm5OUXIySUZTa3dGRlVEbHV1RmhaS1EycW8yZ2NxeENNT0JOanRTdVdqL3BnV1pIWDV4NGZCbW85Cm9qb2RIZmdFMm4zREJOMUIyMHZ4ZHRqTVRONzh6ZHoxUXV0WStrYUZXYTNmaEZFQjNMVnVQT3BqUzllVW82Q3AKWUdjL25LdGFVaGdWNmhSVVV0aXdZaFZ4N2FVMXlnQ08rYWc5QjRILzFMbGp3c1YvNEF0YjhtYz0KLS0tLS1FTkQgQ0VSVElGSUNBVEUgUkVRVUVTVC0tLS0tCg==”,“usages”:[“client auth”]}}
creationTimestamp: “2021-11-03T08:32:11Z”
name: ccx
resourceVersion: “12652380”
selfLink: /apis/certificates.k8s.io/v1/certificatesigningrequests/ccx
uid: 49a3aa81-b7a2-432a-a115-d98e065689ab
spec:
groups:
-
system:masters
-
system:authenticated
request: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURSBSRVFVRVNULS0tLS0KTUlJQ1pUQ0NBVTBDQVFBd0lERU1NQW9HQTFVRUF3d0RZMk40TVJBd0RnWURWUVFLREFkamEyRXlNREl4TUlJQgpJakFOQmdrcWhraUc5dzBCQVFFRkFBT0NBUThBTUlJQkNnS0NBUUVBNkNObzJWVWtTbFQ5bTRvR3Z6cTIyLzRXCmxIM2hVUHRGUHozYWQzZE5NQ1hHNEZrRVdJVG9nRnRISXlyWFc4TlRiZGcxZjN5dzA4aHNwZi9na20vQUYxeSsKUjF0a2JCNWdidDZuOU1wL2lsUUc3RHozYjF2bi9XVC9ieldHaWV3bTFFWEk4OFpaeEFOMllrZmFkdGpCYlhRNQo3MFRxbkx2a1VWVnRKTWRiQjV2aE1Ra3B0TVdvL3ovN2EweGYvbGYxOUgxQURWbXZsNVIvbGU4QVp6RXEwUWQ4ClhKL1FWQkRUNklpMFUxM29GVFEvMlRWeUVJOG5XU2N4K3NxSlBVUXpWL1dwZmJQOHl1SHloV2xNZHZ3RjJnbm0KZ0ZEdW9XdHdjc3NSSFNNdzJzcFc5bTJsM1UwYjczaGZsUmtpaDgyQ1Z5M1owK3ZrTFFkVHJOcWtXcE9TSlFJRApBUUFCb0FBd0RRWUpLb1pJaHZjTkFRRUxCUUFEZ2dFQkFEdXJyS1VIMFZ6WDdtNC9LVEFKYnZXZHhLV29lQ1ZpCno5NHhmRmMrR1NZV2R3cFBLYk1Bcnp2TXYrTEswY0VNUUNMd1R3YmRCbmpjdmFmNG1pV2YyQUVteVRZa3ZNaVcKUTJHV0N1S0toVVZ0MTBxVU93YlFZcWpFZmlycFhTNlZtS1R4UHVKM0dCTmtBS2t4eHZGSGJIdG5ibGpYMmM2NQpzQVBaWThKSm5OUXIySUZTa3dGRlVEbHV1RmhaS1EycW8yZ2NxeENNT0JOanRTdVdqL3BnV1pIWDV4NGZCbW85Cm9qb2RIZmdFMm4zREJOMUIyMHZ4ZHRqTVRONzh6ZHoxUXV0WStrYUZXYTNmaEZFQjNMVnVQT3BqUzllVW82Q3AKWUdjL25LdGFVaGdWNmhSVVV0aXdZaFZ4N2FVMXlnQ08rYWc5QjRILzFMbGp3c1YvNEF0YjhtYz0KLS0tLS1FTkQgQ0VSVElGSUNBVEUgUkVRVUVTVC0tLS0tCg==
signerName: kubernetes.io/legacy-unknown
usages:
- client auth
username: kubernetes-admin
status:
certificate: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSURCVENDQWUyZ0F3SUJBZ0lRWXlYenJkTTVKYS9Ia3lQeGhNME5OekFOQmdrcWhraUc5dzBCQVFzRkFEQVYKTVJNd0VRWURWUVFERXdwcmRXSmxjbTVsZEdWek1CNFhEVEl4TVRFd016QTRNamd6T1ZvWERUSXlNVEV3TXpBNApNamd6T1Zvd0lERVFNQTRHQTFVRUNoTUhZMnRoTWpBeU1URU1NQW9HQTFVRUF4TURZMk40TUlJQklqQU5CZ2txCmhraUc5dzBCQVFFRkFBT0NBUThBTUlJQkNnS0NBUUVBNkNObzJWVWtTbFQ5bTRvR3Z6cTIyLzRXbEgzaFVQdEYKUHozYWQzZE5NQ1hHNEZrRVdJVG9nRnRISXlyWFc4TlRiZGcxZjN5dzA4aHNwZi9na20vQUYxeStSMXRrYkI1ZwpidDZuOU1wL2lsUUc3RHozYjF2bi9XVC9ieldHaWV3bTFFWEk4OFpaeEFOMllrZmFkdGpCYlhRNTcwVHFuTHZrClVWVnRKTWRiQjV2aE1Ra3B0TVdvL3ovN2EweGYvbGYxOUgxQURWbXZsNVIvbGU4QVp6RXEwUWQ4WEovUVZCRFQKNklpMFUxM29GVFEvMlRWeUVJOG5XU2N4K3NxSlBVUXpWL1dwZmJQOHl1SHloV2xNZHZ3RjJnbm1nRkR1b1d0dwpjc3NSSFNNdzJzcFc5bTJsM1UwYjczaGZsUmtpaDgyQ1Z5M1owK3ZrTFFkVHJOcWtXcE9TSlFJREFRQUJvMFl3ClJEQVRCZ05WSFNVRUREQUtCZ2dyQmdFRkJRY0RBakFNQmdOVkhSTUJBZjhFQWpBQU1COEdBMVVkSXdRWU1CYUEKRk03Q2ZzYW51ZGNURkh0bm9leThoL1pRcUVack1BMEdDU3FHU0liM0RRRUJDd1VBQTRJQkFRRHF3cnNYSEIwVApHTjQwdlcvQmJsL1FuVmFKQUdYU2lTR0wwbHVud0dOd3FRRVY2RVhoM3lsR3drS1pCT2JRNHVxZ1F0Vmt5eFQvCnFEcUFERWh5QUx1VGtkREVxLzRsRmFqaDRlaWtHQkRVU3ZhNVNEb2NQUVhqa0JhUHJHMDQxTTh1dlFySFh3WGsKcEc5UGlmbExMTksyMzBzSGNPaS85MmVndmpEL3JIYkdTejV5cGpuWTZpMkJuSzZOcGpqWDRienEyTGl3bytOYQpLS2RIS3JPWXV3ajI0QVllWkRtWnVFZ3FBMXZlRUtSWXZaNVhSREVnL1lEckd1U2NUbkhLQkNPeHEzUVdSRkZTCm4xWG9hdEU1MkU5d3JDeVFsUXAzbi9KbEFqMmViRjh1SElVY1JFY1ZNSjZ5MU02YzlaTHZjdHh4NjA1SFJmeE0KSm1mazR0bkNLc3QvCi0tLS0tRU5EIENFUlRJRklDQVRFLS0tLS0K
conditions:
- lastTransitionTime: “2021-11-03T08:33:39Z”
lastUpdateTime: “2021-11-03T08:33:39Z”
message: This CSR was approved by kubectl certificate approve.
reason: KubectlApprove
status: “True”
type: Approved
[root@master sefe]#
并且会生成自己的ca文件哈【开头指定的ca名称】
[root@master sefe]# ls /etc/kubernetes/pki/ | grep ca
ca.crt
ca.key
front-proxy-ca.crt
front-proxy-ca.key
[root@master sefe]#
- 查看证书:
[root@master sefe]# kubectl get csr/ccx -o jsonpath=‘{.status.certificate}’
LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSURCVENDQWUyZ0F3SUJBZ0lRWXlYenJkTTVKYS9Ia3lQeGhNME5OekFOQmdrcWhraUc5dzBCQVFzRkFEQVYKTVJNd0VRWURWUVFERXdwcmRXSmxjbTVsZEdWek1CNFhEVEl4TVRFd016QTRNamd6T1ZvWERUSXlNVEV3TXpBNApNamd6T1Zvd0lERVFNQTRHQTFVRUNoTUhZMnRoTWpBeU1URU1NQW9HQTFVRUF4TURZMk40TUlJQklqQU5CZ2txCmhraUc5dzBCQVFFRkFBT0NBUThBTUlJQkNnS0NBUUVBNkNObzJWVWtTbFQ5bTRvR3Z6cTIyLzRXbEgzaFVQdEYKUHozYWQzZE5NQ1hHNEZrRVdJVG9nRnRISXlyWFc4TlRiZGcxZjN5dzA4aHNwZi9na20vQUYxeStSMXRrYkI1ZwpidDZuOU1wL2lsUUc3RHozYjF2bi9XVC9ieldHaWV3bTFFWEk4OFpaeEFOMllrZmFkdGpCYlhRNTcwVHFuTHZrClVWVnRKTWRiQjV2aE1Ra3B0TVdvL3ovN2EweGYvbGYxOUgxQURWbXZsNVIvbGU4QVp6RXEwUWQ4WEovUVZCRFQKNklpMFUxM29GVFEvMlRWeUVJOG5XU2N4K3NxSlBVUXpWL1dwZmJQOHl1SHloV2xNZHZ3RjJnbm1nRkR1b1d0dwpjc3NSSFNNdzJzcFc5bTJsM1UwYjczaGZsUmtpaDgyQ1Z5M1owK3ZrTFFkVHJOcWtXcE9TSlFJREFRQUJvMFl3ClJEQVRCZ05WSFNVRUREQUtCZ2dyQmdFRkJRY0RBakFNQmdOVkhSTUJBZjhFQWpBQU1COEdBMVVkSXdRWU1CYUEKRk03Q2ZzYW51ZGNURkh0bm9leThoL1pRcUVack1BMEdDU3FHU0liM0RRRUJDd1VBQTRJQkFRRHF3cnNYSEIwVApHTjQwdlcvQmJsL1FuVmFKQUdYU2lTR0wwbHVud0dOd3FRRVY2RVhoM3lsR3drS1pCT2JRNHVxZ1F0Vmt5eFQvCnFEcUFERWh5QUx1VGtkREVxLzRsRmFqaDRlaWtHQkRVU3ZhNVNEb2NQUVhqa0JhUHJHMDQxTTh1dlFySFh3WGsKcEc5UGlmbExMTksyMzBzSGNPaS85MmVndmpEL3JIYkdTejV5cGpuWTZpMkJuSzZOcGpqWDRienEyTGl3bytOYQpLS2RIS3JPWXV3ajI0QVllWkRtWnVFZ3FBMXZlRUtSWXZaNVhSREVnL1lEckd1U2NUbkhLQkNPeHEzUVdSRkZTCm4xWG9hdEU1MkU5d3JDeVFsUXAzbi9KbEFqMmViRjh1SElVY1JFY1ZNSjZ5MU02YzlaTHZjdHh4NjA1SFJmeE0KSm1mazR0bkNLc3QvCi0tLS0tRU5EIENFUlRJRklDQVRFLS0tLS0K[root@master sefe]#
[root@master sefe]#
- 导出证书文件:
[root@master sefe]# kubectl get csr/ccx -o jsonpath=‘{.status.certificate}’ | base64 -d > ccx.crt
[root@master sefe]# ls
ccx.crt ccx.csr ccx.key csr.yaml
[root@master sefe]#
-
此时公钥和私钥都有了
-
ccx.key:私钥
-
ccx.csr:公钥
[root@master sefe]# ls
ccx.crt ccx.csr ccx.key csr.yaml
[root@master sefe]#
创建kubeconfig 文件
- 拷贝CA 证书
[root@master sefe]# cp /etc/kubernetes/pki/ca.crt .
[root@master sefe]# ls
ca.crt ccx.crt ccx.csr ccx.key csr.yaml
[root@master sefe]# cat ca.crt
-----BEGIN CERTIFICATE-----
MIIC5zCCAc+gAwIBAgIBADANBgkqhkiG9w0BAQsFADAVMRMwEQYDVQQDEwprdWJl
cm5ldGVzMB4XDTIxMDcwMjAxMzUyOFoXDTMxMDYzMDAxMzUyOFowFTETMBEGA1UE
AxMKa3ViZXJuZXRlczCCASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoCggEBAPaA
t0hnK8BSad5VhNcT4skCYK95XVRwOCtIwojUsgSisO2Rk9yhma2yv8NDi9fbjsCK
hgxT2dd26garjjWq3WicfrScVnLWFWcPY8qrCxHc1al8y7kzbs/jIabElNnP1uEc
kBjEakL2r37G19zr3pOqGuKju9DTPling+F9OA4GiDVE/o65W3VPcxEfl85RzDJ8
iZDh/n3bKf+8FRu7BdwiX0btUlPr32Uq5tNW3lKyI68lJCBse/gfgbJdlPWf45IE
En7QEj6S2VmI0sHIP71CX6Zd0o7FSOEjfljFgn1uaqvymtQO7YXqonZ4vliCx09M
pOuFi6egauBCXeiSmKECAwEAAaNCMEAwDgYDVR0PAQH/BAQDAgKkMA8GA1UdEwEB
/wQFMAMBAf8wHQYDVR0OBBYEFM7CfsanudcTFHtnoey8h/ZQqEZrMA0GCSqGSIb3
DQEBCwUAA4IBAQBgPE6dyUXyt12IgrU4JLApBfcQns81OxUVVInLXE/hGBVUcF0j
wwqxpoEQTYp1iO+Ps9Y7CAk5Rw2o2rd6XRp5atYeeZ8WVyavWphl/91wguwV+voh
c00SfXLgTJdlfJcntMSsELZBE9vZkdUIkgBMyNzU1VM0vzrH5xXA/Lrf5oKRESue
6NbDg22bsBY92zH5Lg6a+ilJE5r+8/KREmTT/eeRfEuTR2s0HsxdItpCLzYvFwbr
+/jD+O8DydpQK1LVh4Do+vdT/VPXohMSNhzBSW9fux49eu3wlk9+/nfRthyh7N6G
4sMP48eZqBlNnIG4suMOAoTz7Ly9JgbRYwyY
-----END CERTIFICATE-----
[root@master sefe]#
- 设置集群字段

kubectl config --kubeconfig=kc1 set-cluster cluster1 --server=https://192.168.59.142:6443 --certificate-authority=ca.crt --embed-certs=true
–kubeconfig=kc1——kc1自定义名称
set-cluster cluster1——上文自定义名称cluster1
#–server=https://192.168.59.142:6443——masterIP替换
–certificate-authority=ca.crt——下文指定ca.crt文件下面
#–embed-certs=true 的意思是把证书内容写入到此kubeconfig 文件里。
[root@master sefe]# kubectl config --kubeconfig=kc1 set-cluster cluster1 --server=https://192.168.59.142:6443 --certificate-authority=ca.crt --embed-certs=true
Cluster “cluster1” set.
[root@master sefe]# ls
ca.crt ccx.crt ccx.csr ccx.key csr.yaml kc1
[root@master sefe]# cat kc1
apiVersion: v1
clusters:
- cluster:
certificate-authority-data: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUM1ekNDQWMrZ0F3SUJBZ0lCQURBTkJna3Foa2lHOXcwQkFRc0ZBREFWTVJNd0VRWURWUVFERXdwcmRXSmwKY201bGRHVnpNQjRYRFRJeE1EY3dNakF4TXpVeU9Gb1hEVE14TURZek1EQXhNelV5T0Zvd0ZURVRNQkVHQTFVRQpBeE1LYTNWaVpYSnVaWFJsY3pDQ0FTSXdEUVlKS29aSWh2Y05BUUVCQlFBRGdnRVBBRENDQVFvQ2dnRUJBUGFBCnQwaG5LOEJTYWQ1VmhOY1Q0c2tDWUs5NVhWUndPQ3RJd29qVXNnU2lzTzJSazl5aG1hMnl2OE5EaTlmYmpzQ0sKaGd4VDJkZDI2Z2FyampXcTNXaWNmclNjVm5MV0ZXY1BZOHFyQ3hIYzFhbDh5N2t6YnMvaklhYkVsTm5QMXVFYwprQmpFYWtMMnIzN0cxOXpyM3BPcUd1S2p1OURUUGxpbmcrRjlPQTRHaURWRS9vNjVXM1ZQY3hFZmw4NVJ6REo4CmlaRGgvbjNiS2YrOEZSdTdCZHdpWDBidFVsUHIzMlVxNXROVzNsS3lJNjhsSkNCc2UvZ2ZnYkpkbFBXZjQ1SUUKRW43UUVqNlMyVm1JMHNISVA3MUNYNlpkMG83RlNPRWpmbGpGZ24xdWFxdnltdFFPN1lYcW9uWjR2bGlDeDA5TQpwT3VGaTZlZ2F1QkNYZWlTbUtFQ0F3RUFBYU5DTUVBd0RnWURWUjBQQVFIL0JBUURBZ0trTUE4R0ExVWRFd0VCCi93UUZNQU1CQWY4d0hRWURWUjBPQkJZRUZNN0Nmc2FudWRjVEZIdG5vZXk4aC9aUXFFWnJNQTBHQ1NxR1NJYjMKRFFFQkN3VUFBNElCQVFCZ1BFNmR5VVh5dDEySWdyVTRKTEFwQmZjUW5zODFPeFVWVkluTFhFL2hHQlZVY0Ywagp3d3F4cG9FUVRZcDFpTytQczlZN0NBazVSdzJvMnJkNlhScDVhdFllZVo4V1Z5YXZXcGhsLzkxd2d1d1Yrdm9oCmMwMFNmWExnVEpkbGZKY250TVNzRUxaQkU5dlprZFVJa2dCTXlOelUxVk0wdnpySDV4WEEvTHJmNW9LUkVTdWUKNk5iRGcyMmJzQlk5MnpINUxnNmEraWxKRTVyKzgvS1JFbVRUL2VlUmZFdVRSMnMwSHN4ZEl0cENMell2RndicgorL2pEK084RHlkcFFLMUxWaDREbyt2ZFQvVlBYb2hNU05oekJTVzlmdXg0OWV1M3dsazkrL25mUnRoeWg3TjZHCjRzTVA0OGVacUJsTm5JRzRzdU1PQW9UejdMeTlKZ2JSWXd5WQotLS0tLUVORCBDRVJUSUZJQ0FURS0tLS0tCg==
server: https://192.168.59.142:6443
name: cluster1
contexts: null
current-context: “”
kind: Config
preferences: {}
users: null
[root@master sefe]#
- 设置用户字段
主要是写入各种秘钥信息的
啥都不用修改
kubectl config --kubeconfig=kc1 set-credentials ccx --client-certificate=ccx.crt --client-key=ccx.key --embed-certs=true
[root@master sefe]# kubectl config --kubeconfig=kc1 set-credentials ccx --client-certificate=ccx.crt --client-key=ccx.key --embed-certs=true
User “ccx” set.
[root@master sefe]# cat kc1
apiVersion: v1
clusters:
- cluster:
certificate-authority-data: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUM1ekNDQWMrZ0F3SUJBZ0lCQURBTkJna3Foa2lHOXcwQkFRc0ZBREFWTVJNd0VRWURWUVFERXdwcmRXSmwKY201bGRHVnpNQjRYRFRJeE1EY3dNakF4TXpVeU9Gb1hEVE14TURZek1EQXhNelV5T0Zvd0ZURVRNQkVHQTFVRQpBeE1LYTNWaVpYSnVaWFJsY3pDQ0FTSXdEUVlKS29aSWh2Y05BUUVCQlFBRGdnRVBBRENDQVFvQ2dnRUJBUGFBCnQwaG5LOEJTYWQ1VmhOY1Q0c2tDWUs5NVhWUndPQ3RJd29qVXNnU2lzTzJSazl5aG1hMnl2OE5EaTlmYmpzQ0sKaGd4VDJkZDI2Z2FyampXcTNXaWNmclNjVm5MV0ZXY1BZOHFyQ3hIYzFhbDh5N2t6YnMvaklhYkVsTm5QMXVFYwprQmpFYWtMMnIzN0cxOXpyM3BPcUd1S2p1OURUUGxpbmcrRjlPQTRHaURWRS9vNjVXM1ZQY3hFZmw4NVJ6REo4CmlaRGgvbjNiS2YrOEZSdTdCZHdpWDBidFVsUHIzMlVxNXROVzNsS3lJNjhsSkNCc2UvZ2ZnYkpkbFBXZjQ1SUUKRW43UUVqNlMyVm1JMHNISVA3MUNYNlpkMG83RlNPRWpmbGpGZ24xdWFxdnltdFFPN1lYcW9uWjR2bGlDeDA5TQpwT3VGaTZlZ2F1QkNYZWlTbUtFQ0F3RUFBYU5DTUVBd0RnWURWUjBQQVFIL0JBUURBZ0trTUE4R0ExVWRFd0VCCi93UUZNQU1CQWY4d0hRWURWUjBPQkJZRUZNN0Nmc2FudWRjVEZIdG5vZXk4aC9aUXFFWnJNQTBHQ1NxR1NJYjMKRFFFQkN3VUFBNElCQVFCZ1BFNmR5VVh5dDEySWdyVTRKTEFwQmZjUW5zODFPeFVWVkluTFhFL2hHQlZVY0Ywagp3d3F4cG9FUVRZcDFpTytQczlZN0NBazVSdzJvMnJkNlhScDVhdFllZVo4V1Z5YXZXcGhsLzkxd2d1d1Yrdm9oCmMwMFNmWExnVEpkbGZKY250TVNzRUxaQkU5dlprZFVJa2dCTXlOelUxVk0wdnpySDV4WEEvTHJmNW9LUkVTdWUKNk5iRGcyMmJzQlk5MnpINUxnNmEraWxKRTVyKzgvS1JFbVRUL2VlUmZFdVRSMnMwSHN4ZEl0cENMell2RndicgorL2pEK084RHlkcFFLMUxWaDREbyt2ZFQvVlBYb2hNU05oekJTVzlmdXg0OWV1M3dsazkrL25mUnRoeWg3TjZHCjRzTVA0OGVacUJsTm5JRzRzdU1PQW9UejdMeTlKZ2JSWXd5WQotLS0tLUVORCBDRVJUSUZJQ0FURS0tLS0tCg==
server: https://192.168.59.142:6443
name: cluster1
contexts: null
current-context: “”
kind: Config
preferences: {}
users:
- name: ccx
user:
client-certificate-data: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSURCVENDQWUyZ0F3SUJBZ0lRWXlYenJkTTVKYS9Ia3lQeGhNME5OekFOQmdrcWhraUc5dzBCQVFzRkFEQVYKTVJNd0VRWURWUVFERXdwcmRXSmxjbTVsZEdWek1CNFhEVEl4TVRFd016QTRNamd6T1ZvWERUSXlNVEV3TXpBNApNamd6T1Zvd0lERVFNQTRHQTFVRUNoTUhZMnRoTWpBeU1URU1NQW9HQTFVRUF4TURZMk40TUlJQklqQU5CZ2txCmhraUc5dzBCQVFFRkFBT0NBUThBTUlJQkNnS0NBUUVBNkNObzJWVWtTbFQ5bTRvR3Z6cTIyLzRXbEgzaFVQdEYKUHozYWQzZE5NQ1hHNEZrRVdJVG9nRnRISXlyWFc4TlRiZGcxZjN5dzA4aHNwZi9na20vQUYxeStSMXRrYkI1ZwpidDZuOU1wL2lsUUc3RHozYjF2bi9XVC9ieldHaWV3bTFFWEk4OFpaeEFOMllrZmFkdGpCYlhRNTcwVHFuTHZrClVWVnRKTWRiQjV2aE1Ra3B0TVdvL3ovN2EweGYvbGYxOUgxQURWbXZsNVIvbGU4QVp6RXEwUWQ4WEovUVZCRFQKNklpMFUxM29GVFEvMlRWeUVJOG5XU2N4K3NxSlBVUXpWL1dwZmJQOHl1SHloV2xNZHZ3RjJnbm1nRkR1b1d0dwpjc3NSSFNNdzJzcFc5bTJsM1UwYjczaGZsUmtpaDgyQ1Z5M1owK3ZrTFFkVHJOcWtXcE9TSlFJREFRQUJvMFl3ClJEQVRCZ05WSFNVRUREQUtCZ2dyQmdFRkJRY0RBakFNQmdOVkhSTUJBZjhFQWpBQU1COEdBMVVkSXdRWU1CYUEKRk03Q2ZzYW51ZGNURkh0bm9leThoL1pRcUVack1BMEdDU3FHU0liM0RRRUJDd1VBQTRJQkFRRHF3cnNYSEIwVApHTjQwdlcvQmJsL1FuVmFKQUdYU2lTR0wwbHVud0dOd3FRRVY2RVhoM3lsR3drS1pCT2JRNHVxZ1F0Vmt5eFQvCnFEcUFERWh5QUx1VGtkREVxLzRsRmFqaDRlaWtHQkRVU3ZhNVNEb2NQUVhqa0JhUHJHMDQxTTh1dlFySFh3WGsKcEc5UGlmbExMTksyMzBzSGNPaS85MmVndmpEL3JIYkdTejV5cGpuWTZpMkJuSzZOcGpqWDRienEyTGl3bytOYQpLS2RIS3JPWXV3ajI0QVllWkRtWnVFZ3FBMXZlRUtSWXZaNVhSREVnL1lEckd1U2NUbkhLQkNPeHEzUVdSRkZTCm4xWG9hdEU1MkU5d3JDeVFsUXAzbi9KbEFqMmViRjh1SElVY1JFY1ZNSjZ5MU02YzlaTHZjdHh4NjA1SFJmeE0KSm1mazR0bkNLc3QvCi0tLS0tRU5EIENFUlRJRklDQVRFLS0tLS0K
client-key-data: LS0tLS1CRUdJTiBSU0EgUFJJVkFURSBLRVktLS0tLQpNSUlFb3dJQkFBS0NBUUVBNkNObzJWVWtTbFQ5bTRvR3Z6cTIyLzRXbEgzaFVQdEZQejNhZDNkTk1DWEc0RmtFCldJVG9nRnRISXlyWFc4TlRiZGcxZjN5dzA4aHNwZi9na20vQUYxeStSMXRrYkI1Z2J0Nm45TXAvaWxRRzdEejMKYjF2bi9XVC9ieldHaWV3bTFFWEk4OFpaeEFOMllrZmFkdGpCYlhRNTcwVHFuTHZrVVZWdEpNZGJCNXZoTVFrcAp0TVdvL3ovN2EweGYvbGYxOUgxQURWbXZsNVIvbGU4QVp6RXEwUWQ4WEovUVZCRFQ2SWkwVTEzb0ZUUS8yVFZ5CkVJOG5XU2N4K3NxSlBVUXpWL1dwZmJQOHl1SHloV2xNZHZ3RjJnbm1nRkR1b1d0d2Nzc1JIU013MnNwVzltMmwKM1UwYjczaGZsUmtpaDgyQ1Z5M1owK3ZrTFFkVHJOcWtXcE9TSlFJREFRQUJBb0lCQUVqR29SNVJoUGtRd0JrOQpJblJkTWVxeU05NEZ3TmVranNjTzJ5ak03QlFHSTkwOXl4RDlTZTdEcnYrbGRMSzkvNi9XTXA5dk5maVBReENmCnNZWDNKdCtzSWJNNVFiaHJwWXZjbmdjdVhPRy9DaFNSNEhpMjlYb0phZE14a3FZMnRNMmp1eVpCcnU2MnJ5eU0Kbmo3WUlYdnhEaUNuR0c1ZXNXdVdQb3RqUEhTYm53L0JOKzgwaFJYSitrUHlyK2pYMjVtRTlUcTh0emtEQUdXWQpMd0psb0dQenhPdG9lREJjb1hNWkgyWlJhRmhjd1VWRkJmcUlaMFY4UzZLVDkyTkYwVzVWdUlWR1RMNDJ0Mjl5CjBtQVdqM3ZrdDcyajZhUk9Wd0pkemQwVU43c3p6SFJJQjhhNTJCcTZybzl6UE1NTDRRcmtnamFSeXRsczduZ2kKZFp0SGY0RUNnWUVBK1ZTa1VvR2pZdWZ4eHQ5RjlKeVFsWVZUTmNlOTM4cXBQSnUrVDdEUVVLZ0V2MmVZMXF3cQpvTWJqb1JTVGpUbUFUZU9tWWEzS2d5SWR6VkszT000MWprcU1remlwb3VyK3NwSVJhbVBLQ0F2clo5Yi9rbm5lCnNrcTZweisxUjJwYVVqaEozZGtkZXBEUE05cmtxWjRQTG9mVkczT3JOZ1VJR3JhaGJ1TmhKN0VDZ1lFQTdsa0oKNlp3d2pKWENldGlxaXRZaHV1QWtwZXlTUGprWHMyaFQrQk0vQUY0SnJncGR1Y2E5VlhNQUlDSys2SlJSdDE5cAovaXpQN3Jucm1hWmNaM0cxWmdkUTFGZytTSkxxNFMzTk8yejRJaHVFWlYwSy91YjdxenZRdDBlSlVEMTdqNFQrCkxVRnhnZmE4WklybzhDWjIreStYazh5Nlh0Slp5Qy9aNU8ydElyVUNnWUVBMFhYVEttRXdjcm5xdXlqOWF4ZFEKdTl3cTRJWnlOQnpjZWtkWTVUZmtlYTM5ZHhOQUtqQ3ZDeXlyTkxyRmpxSWM4TkpzQjZscDlTcG5JUVA1V3VhWgp4WFZKamJEUGlrZWpPejlORkRUTEdHRnpIV1JZaHFTTmV2a2V2N3pjdlNkU3c3bjRERUVHNjkzVnhIbURHaC9vCkh5NEwwU2ttVDVhQWpYaWFQRDhYY3JFQ2dZQTlkWUlqMWQyQzhyN3lORnBOY0lmRUN6WUgvdWQ2MmZmdGtCSk8KM28rWlJhWlRWV0x6bTNhSXlSMllLNzEwZFlKWXVXYTRYcy9ESy9lL1ovRmR6eWxLUk1xbjVwVXcyNGxyUlFjdApzcHlORnZGZHZjOHZDVnFOdmQvRTB0SnFlV0FhRXQ0RHgyTkFjdUlEUHZwdnFrdDEyOERISUx4UjVRVzNvL2NZCm05elFIUUtCZ0dNZkVKUnh4Sk51ZllmcXNMa1QwQktWTEhCMDZsUHAxSGlLWVZuMXJkMmNZRkl2M3VNR2RrUXYKKzlYNVFIdkpsaWYzdUg1Wnp0TnZFdEVEY3lzcjdWN1RzNXo2Z1BGcUdrdDlKS1o2c1ZkcWNuYjRoSlhONXQzaQpBVWZtWkdrN0pFeVlSRXdPUm1jM3FBNld2RG9iUWtINGhXeXg4azN5R3NwTmNzcHgzd2ZGCi0tLS0tRU5EIFJTQSBQUklWQVRFIEtFWS0tLS0tCg==
[root@master sefe]#
- 设置上下文字段
上面是定义上下文,这呢,是定义contexts,吧上面内容中的cluster和user绑定在一起用的
啥都不用修改
kubectl config --kubeconfig=kc1 set-context context1 --cluster=cluster1 --namespace=default --user=ccx
[root@master sefe]# kubectl config --kubeconfig=kc1 set-context context1 --cluster=cluster1 --namespace=default --user=ccx
Context “context1” created.
[root@master sefe]# cat ck1
cat: ck1: No such file or directory
[root@master sefe]# cat kc1
apiVersion: v1
clusters:
- cluster:
certificate-authority-data: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUM1ekNDQWMrZ0F3SUJBZ0lCQURBTkJna3Foa2lHOXcwQkFRc0ZBREFWTVJNd0VRWURWUVFERXdwcmRXSmwKY201bGRHVnpNQjRYRFRJeE1EY3dNakF4TXpVeU9Gb1hEVE14TURZek1EQXhNelV5T0Zvd0ZURVRNQkVHQTFVRQpBeE1LYTNWaVpYSnVaWFJsY3pDQ0FTSXdEUVlKS29aSWh2Y05BUUVCQlFBRGdnRVBBRENDQVFvQ2dnRUJBUGFBCnQwaG5LOEJTYWQ1VmhOY1Q0c2tDWUs5NVhWUndPQ3RJd29qVXNnU2lzTzJSazl5aG1hMnl2OE5EaTlmYmpzQ0sKaGd4VDJkZDI2Z2FyampXcTNXaWNmclNjVm5MV0ZXY1BZOHFyQ3hIYzFhbDh5N2t6YnMvaklhYkVsTm5QMXVFYwprQmpFYWtMMnIzN0cxOXpyM3BPcUd1S2p1OURUUGxpbmcrRjlPQTRHaURWRS9vNjVXM1ZQY3hFZmw4NVJ6REo4CmlaRGgvbjNiS2YrOEZSdTdCZHdpWDBidFVsUHIzMlVxNXROVzNsS3lJNjhsSkNCc2UvZ2ZnYkpkbFBXZjQ1SUUKRW43UUVqNlMyVm1JMHNISVA3MUNYNlpkMG83RlNPRWpmbGpGZ24xdWFxdnltdFFPN1lYcW9uWjR2bGlDeDA5TQpwT3VGaTZlZ2F1QkNYZWlTbUtFQ0F3RUFBYU5DTUVBd0RnWURWUjBQQVFIL0JBUURBZ0trTUE4R0ExVWRFd0VCCi93UUZNQU1CQWY4d0hRWURWUjBPQkJZRUZNN0Nmc2FudWRjVEZIdG5vZXk4aC9aUXFFWnJNQTBHQ1NxR1NJYjMKRFFFQkN3VUFBNElCQVFCZ1BFNmR5VVh5dDEySWdyVTRKTEFwQmZjUW5zODFPeFVWVkluTFhFL2hHQlZVY0Ywagp3d3F4cG9FUVRZcDFpTytQczlZN0NBazVSdzJvMnJkNlhScDVhdFllZVo4V1Z5YXZXcGhsLzkxd2d1d1Yrdm9oCmMwMFNmWExnVEpkbGZKY250TVNzRUxaQkU5dlprZFVJa2dCTXlOelUxVk0wdnpySDV4WEEvTHJmNW9LUkVTdWUKNk5iRGcyMmJzQlk5MnpINUxnNmEraWxKRTVyKzgvS1JFbVRUL2VlUmZFdVRSMnMwSHN4ZEl0cENMell2RndicgorL2pEK084RHlkcFFLMUxWaDREbyt2ZFQvVlBYb2hNU05oekJTVzlmdXg0OWV1M3dsazkrL25mUnRoeWg3TjZHCjRzTVA0OGVacUJsTm5JRzRzdU1PQW9UejdMeTlKZ2JSWXd5WQotLS0tLUVORCBDRVJUSUZJQ0FURS0tLS0tCg==
server: https://192.168.59.142:6443
name: cluster1
contexts:
- context:
cluster: cluster1
namespace: default
user: ccx
name: context1
current-context: “”
kind: Config
preferences: {}
users:
- name: ccx
user:
client-certificate-data: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSURCVENDQWUyZ0F3SUJBZ0lRWXlYenJkTTVKYS9Ia3lQeGhNME5OekFOQmdrcWhraUc5dzBCQVFzRkFEQVYKTVJNd0VRWURWUVFERXdwcmRXSmxjbTVsZEdWek1CNFhEVEl4TVRFd016QTRNamd6T1ZvWERUSXlNVEV3TXpBNApNamd6T1Zvd0lERVFNQTRHQTFVRUNoTUhZMnRoTWpBeU1URU1NQW9HQTFVRUF4TURZMk40TUlJQklqQU5CZ2txCmhraUc5dzBCQVFFRkFBT0NBUThBTUlJQkNnS0NBUUVBNkNObzJWVWtTbFQ5bTRvR3Z6cTIyLzRXbEgzaFVQdEYKUHozYWQzZE5NQ1hHNEZrRVdJVG9nRnRISXlyWFc4TlRiZGcxZjN5dzA4aHNwZi9na20vQUYxeStSMXRrYkI1ZwpidDZuOU1wL2lsUUc3RHozYjF2bi9XVC9ieldHaWV3bTFFWEk4OFpaeEFOMllrZmFkdGpCYlhRNTcwVHFuTHZrClVWVnRKTWRiQjV2aE1Ra3B0TVdvL3ovN2EweGYvbGYxOUgxQURWbXZsNVIvbGU4QVp6RXEwUWQ4WEovUVZCRFQKNklpMFUxM29GVFEvMlRWeUVJOG5XU2N4K3NxSlBVUXpWL1dwZmJQOHl1SHloV2xNZHZ3RjJnbm1nRkR1b1d0dwpjc3NSSFNNdzJzcFc5bTJsM1UwYjczaGZsUmtpaDgyQ1Z5M1owK3ZrTFFkVHJOcWtXcE9TSlFJREFRQUJvMFl3ClJEQVRCZ05WSFNVRUREQUtCZ2dyQmdFRkJRY0RBakFNQmdOVkhSTUJBZjhFQWpBQU1COEdBMVVkSXdRWU1CYUEKRk03Q2ZzYW51ZGNURkh0bm9leThoL1pRcUVack1BMEdDU3FHU0liM0RRRUJDd1VBQTRJQkFRRHF3cnNYSEIwVApHTjQwdlcvQmJsL1FuVmFKQUdYU2lTR0wwbHVud0dOd3FRRVY2RVhoM3lsR3drS1pCT2JRNHVxZ1F0Vmt5eFQvCnFEcUFERWh5QUx1VGtkREVxLzRsRmFqaDRlaWtHQkRVU3ZhNVNEb2NQUVhqa0JhUHJHMDQxTTh1dlFySFh3WGsKcEc5UGlmbExMTksyMzBzSGNPaS85MmVndmpEL3JIYkdTejV5cGpuWTZpMkJuSzZOcGpqWDRienEyTGl3bytOYQpLS2RIS3JPWXV3ajI0QVllWkRtWnVFZ3FBMXZlRUtSWXZaNVhSREVnL1lEckd1U2NUbkhLQkNPeHEzUVdSRkZTCm4xWG9hdEU1MkU5d3JDeVFsUXAzbi9KbEFqMmViRjh1SElVY1JFY1ZNSjZ5MU02YzlaTHZjdHh4NjA1SFJmeE0KSm1mazR0bkNLc3QvCi0tLS0tRU5EIENFUlRJRklDQVRFLS0tLS0K
client-key-data: LS0tLS1CRUdJTiBSU0EgUFJJVkFURSBLRVktLS0tLQpNSUlFb3dJQkFBS0NBUUVBNkNObzJWVWtTbFQ5bTRvR3Z6cTIyLzRXbEgzaFVQdEZQejNhZDNkTk1DWEc0RmtFCldJVG9nRnRISXlyWFc4TlRiZGcxZjN5dzA4aHNwZi9na20vQUYxeStSMXRrYkI1Z2J0Nm45TXAvaWxRRzdEejMKYjF2bi9XVC9ieldHaWV3bTFFWEk4OFpaeEFOMllrZmFkdGpCYlhRNTcwVHFuTHZrVVZWdEpNZGJCNXZoTVFrcAp0TVdvL3ovN2EweGYvbGYxOUgxQURWbXZsNVIvbGU4QVp6RXEwUWQ4WEovUVZCRFQ2SWkwVTEzb0ZUUS8yVFZ5CkVJOG5XU2N4K3NxSlBVUXpWL1dwZmJQOHl1SHloV2xNZHZ3RjJnbm1nRkR1b1d0d2Nzc1JIU013MnNwVzltMmwKM1UwYjczaGZsUmtpaDgyQ1Z5M1owK3ZrTFFkVHJOcWtXcE9TSlFJREFRQUJBb0lCQUVqR29SNVJoUGtRd0JrOQpJblJkTWVxeU05NEZ3TmVranNjTzJ5ak03QlFHSTkwOXl4RDlTZTdEcnYrbGRMSzkvNi9XTXA5dk5maVBReENmCnNZWDNKdCtzSWJNNVFiaHJwWXZjbmdjdVhPRy9DaFNSNEhpMjlYb0phZE14a3FZMnRNMmp1eVpCcnU2MnJ5eU0Kbmo3WUlYdnhEaUNuR0c1ZXNXdVdQb3RqUEhTYm53L0JOKzgwaFJYSitrUHlyK2pYMjVtRTlUcTh0emtEQUdXWQpMd0psb0dQenhPdG9lREJjb1hNWkgyWlJhRmhjd1VWRkJmcUlaMFY4UzZLVDkyTkYwVzVWdUlWR1RMNDJ0Mjl5CjBtQVdqM3ZrdDcyajZhUk9Wd0pkemQwVU43c3p6SFJJQjhhNTJCcTZybzl6UE1NTDRRcmtnamFSeXRsczduZ2kKZFp0SGY0RUNnWUVBK1ZTa1VvR2pZdWZ4eHQ5RjlKeVFsWVZUTmNlOTM4cXBQSnUrVDdEUVVLZ0V2MmVZMXF3cQpvTWJqb1JTVGpUbUFUZU9tWWEzS2d5SWR6VkszT000MWprcU1remlwb3VyK3NwSVJhbVBLQ0F2clo5Yi9rbm5lCnNrcTZweisxUjJwYVVqaEozZGtkZXBEUE05cmtxWjRQTG9mVkczT3JOZ1VJR3JhaGJ1TmhKN0VDZ1lFQTdsa0oKNlp3d2pKWENldGlxaXRZaHV1QWtwZXlTUGprWHMyaFQrQk0vQUY0SnJncGR1Y2E5VlhNQUlDSys2SlJSdDE5cAovaXpQN3Jucm1hWmNaM0cxWmdkUTFGZytTSkxxNFMzTk8yejRJaHVFWlYwSy91YjdxenZRdDBlSlVEMTdqNFQrCkxVRnhnZmE4WklybzhDWjIreStYazh5Nlh0Slp5Qy9aNU8ydElyVUNnWUVBMFhYVEttRXdjcm5xdXlqOWF4ZFEKdTl3cTRJWnlOQnpjZWtkWTVUZmtlYTM5ZHhOQUtqQ3ZDeXlyTkxyRmpxSWM4TkpzQjZscDlTcG5JUVA1V3VhWgp4WFZKamJEUGlrZWpPejlORkRUTEdHRnpIV1JZaHFTTmV2a2V2N3pjdlNkU3c3bjRERUVHNjkzVnhIbURHaC9vCkh5NEwwU2ttVDVhQWpYaWFQRDhYY3JFQ2dZQTlkWUlqMWQyQzhyN3lORnBOY0lmRUN6WUgvdWQ2MmZmdGtCSk8KM28rWlJhWlRWV0x6bTNhSXlSMllLNzEwZFlKWXVXYTRYcy9ESy9lL1ovRmR6eWxLUk1xbjVwVXcyNGxyUlFjdApzcHlORnZGZHZjOHZDVnFOdmQvRTB0SnFlV0FhRXQ0RHgyTkFjdUlEUHZwdnFrdDEyOERISUx4UjVRVzNvL2NZCm05elFIUUtCZ0dNZkVKUnh4Sk51ZllmcXNMa1QwQktWTEhCMDZsUHAxSGlLWVZuMXJkMmNZRkl2M3VNR2RrUXYKKzlYNVFIdkpsaWYzdUg1Wnp0TnZFdEVEY3lzcjdWN1RzNXo2Z1BGcUdrdDlKS1o2c1ZkcWNuYjRoSlhONXQzaQpBVWZtWkdrN0pFeVlSRXdPUm1jM3FBNld2RG9iUWtINGhXeXg4azN5R3NwTmNzcHgzd2ZGCi0tLS0tRU5EIFJTQSBQUklWQVRFIEtFWS0tLS0tCg==
给大家的福利
零基础入门
对于从来没有接触过网络安全的同学,我们帮你准备了详细的学习成长路线图。可以说是最科学最系统的学习路线,大家跟着这个大的方向学习准没问题。

同时每个成长路线对应的板块都有配套的视频提供:

因篇幅有限,仅展示部分资料
网络安全面试题

绿盟护网行动

还有大家最喜欢的黑客技术

网络安全源码合集+工具包


所有资料共282G,朋友们如果有需要全套《网络安全入门+黑客进阶学习资源包》,可以扫描下方二维码领取(如遇扫码问题,可以在评论区留言领取哦)~
网上学习资料一大堆,但如果学到的知识不成体系,遇到问题时只是浅尝辄止,不再深入研究,那么很难做到真正的技术提升。
一个人可以走的很快,但一群人才能走的更远!不论你是正从事IT行业的老鸟或是对IT行业感兴趣的新人,都欢迎加入我们的的圈子(技术交流、学习资源、职场吐槽、大厂内推、面试辅导),让我们一起学习成长!
更多推荐
 已为社区贡献4条内容
已为社区贡献4条内容






所有评论(0)