k8s安全测评漏洞:SSL/TLS协议信息泄露漏洞(CVE-2016-2183)
k8s组件使用了IDEA、DES和3DES等算法,修改配置文件禁用上述算法即可。
一、问题复现
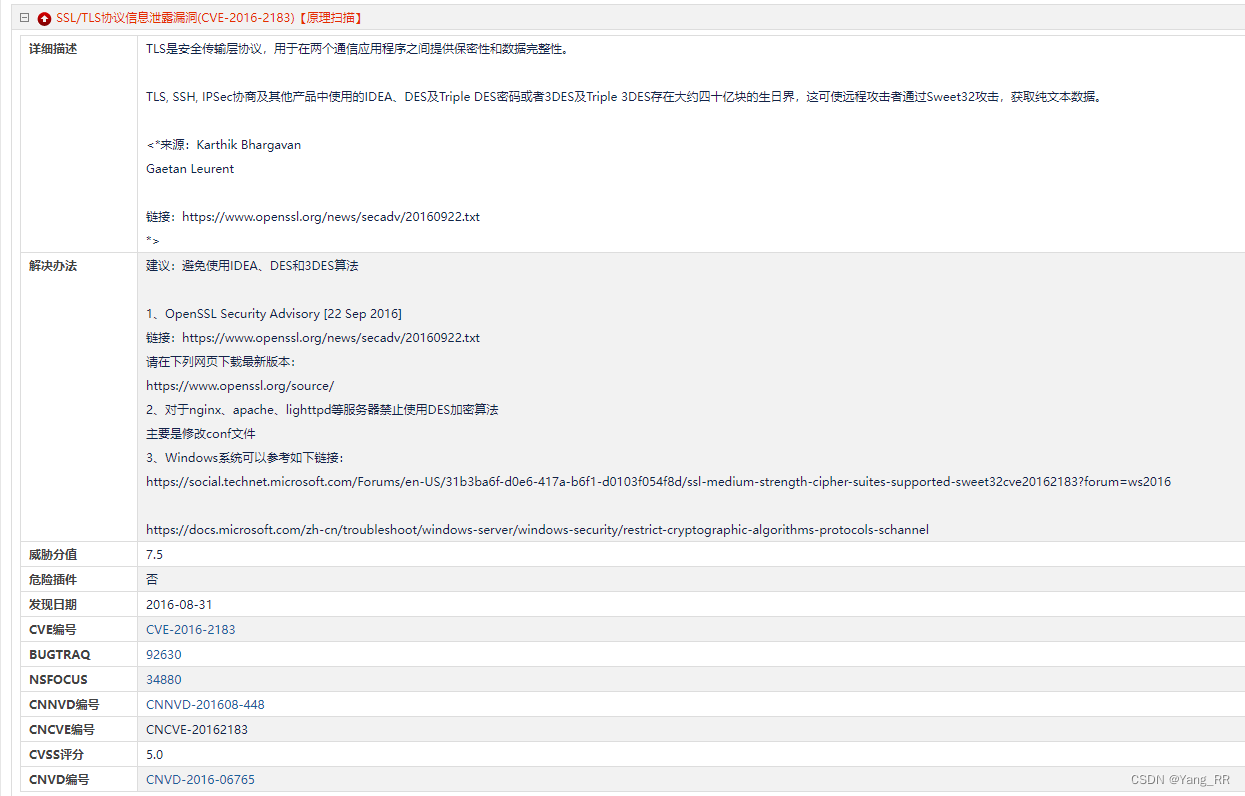
漏洞详细信息:

漏洞概况:

漏洞原因:
k8s组件使用了IDEA、DES和3DES等算法,修改配置文件禁用上述算法即可。
复现方法:
服务器上安装nmap:
#官网下载:https://nmap.org/dist/nmap-7.93-1.x86_64.rpm,上传后安装:
rpm -ivh nmap-7.93-1.x86_64.rpm
#执行检测
nmap --script ssl-enum-ciphers -p 10250 10.165.3.45
Nmap scan report for yfdxvm000003164.novalocal (10.165.3.45)
Host is up (0.000066s latency).
PORT STATE SERVICE
10250/tcp open unknown
| ssl-enum-ciphers:
| TLSv1.2:
| ciphers:
| TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 (ecdh_x25519) - A
| TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 (ecdh_x25519) - A
| TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA (ecdh_x25519) - A
| TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA (ecdh_x25519) - A
| TLS_RSA_WITH_AES_128_GCM_SHA256 (rsa 2048) - A
| TLS_RSA_WITH_AES_256_GCM_SHA384 (rsa 2048) - A
| TLS_RSA_WITH_AES_128_CBC_SHA (rsa 2048) - A
| TLS_RSA_WITH_AES_256_CBC_SHA (rsa 2048) - A
| compressors:
| NULL
| cipher preference: server
warnings:
| 64-bit block cipher 3DES vulnerable to SWEET32 attack
| TLSv1.3:
| ciphers:
| TLS_AKE_WITH_AES_128_GCM_SHA256 (ecdh_x25519) - A
| TLS_AKE_WITH_CHACHA20_POLY1305_SHA256 (ecdh_x25519) - A
| TLS_AKE_WITH_AES_256_GCM_SHA384 (ecdh_x25519) - A
| cipher preference: server
|_ least strength: C
Nmap done: 1 IP address (1 host up) scanned in 0.43 seconds扫描结果重点关注warnings,64-bit block cipher 3DES vulnerable to SWEET32 attack,漏洞修复成功则没有该项提示。
二、漏洞修复
k8s主节点:
etcd修复:
修改配置文件/etc/kubernetes/manifests/etcd.yaml,增加如下配置:
--cipher-suites=TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256,TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384,TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA,TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA,TLS_RSA_WITH_AES_128_GCM_SHA256,TLS_RSA_WITH_AES_256_GCM_SHA384,TLS_RSA_WITH_AES_128_CBC_SHA,TLS_RSA_WITH_AES_256_CBC_SHA
增加后的截图:

增加后etcd漏洞即修复成功
nmap --script ssl-enum-ciphers -p 2380 10.165.3.45
可以看到没有了warnings这项了
kube-apiserver修复:
修改配置文件/etc/kubernetes/manifests/kube-apiserver.yaml,增加一行:
- --tls-cipher-suites=TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256,TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384,TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA,TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA,TLS_RSA_WITH_AES_128_GCM_SHA256,TLS_RSA_WITH_AES_256_GCM_SHA384,TLS_RSA_WITH_AES_128_CBC_SHA,TLS_RSA_WITH_AES_256_CBC_SHA
如图所示:

增加后kube-apiserver漏洞即修复成功
nmap --script ssl-enum-ciphers -p 6443 10.165.3.45
可以看到没有了warnings这项了
修复kubelet:
修改配置文件/var/lib/kubelet/config.yaml,增加一行配置:
tlsCipherSuites: [TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256,TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384,TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA,TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA,TLS_RSA_WITH_AES_128_GCM_SHA256,TLS_RSA_WITH_AES_256_GCM_SHA384,TLS_RSA_WITH_AES_128_CBC_SHA,TLS_RSA_WITH_AES_256_CBC_SHA]
如图所示:

重启服务:
systemctl restart kubelet
在执行检查
nmap --script ssl-enum-ciphers -p 10250 10.165.3.45
可以看到没有了warnings这项了
k8s从节点:
只需要修复最后一项即可
修复kubelet:
修改配置文件/var/lib/kubelet/config.yaml,增加一行配置:
tlsCipherSuites: [TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256,TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384,TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA,TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA,TLS_RSA_WITH_AES_128_GCM_SHA256,TLS_RSA_WITH_AES_256_GCM_SHA384,TLS_RSA_WITH_AES_128_CBC_SHA,TLS_RSA_WITH_AES_256_CBC_SHA]
如图所示:

重启服务:
systemctl restart kubelet
在执行检查
nmap --script ssl-enum-ciphers -p 10250 10.165.3.45
可以看到没有了warnings这项了
更多推荐
 已为社区贡献1条内容
已为社区贡献1条内容






所有评论(0)