Second post of the Cyber Security Introduction series. In this article we will talk about one of the most common and simple cyber attack; Phishing, how it happens, how to prevent it and how to recover from it.
32% of confirmed data breaches involve phishing. So what is this exactly?
What is Phishing?
Phishing is the simple practice of sending fraudulent communications that appear to come from a reputable source. It is usually performed through email. The goal is to steal sensitive data like credit card, login information or to install malware on the victim's machine.
Here is a flow example of a email phishing attack:
- You receive a fake branded email.
- Email has fake branded link (ex:
facebok.comwith one 'o'). - You click and land on a falsified branded page.
- Page asks you to login, change your password or provide other information.
- Hackers capture your data and automatically redirect you to the official (real) website.
- You have been hacked and you don't even know it. If you use the same authentication across various platform, you are fully exposed.

How to prevent it?
Here are a few tips and best practices you can apply in order to reduce the chances of phishing. Remember that 90% of attacks come from human errors; The more careful and aware you are, the easiest to prevent it.
- Check the email and domain name of the sender.
- Check that it is not a generic email.
- Don't give any personal information via email.
- If there are links in the email, check the security of the website URL (https, little lock on the left).
- Do not use phone numbers present in emails and use the one present on the official website.
- Pay attention to details, phishing emails often have typos.
- If you have any doubts, contact you tech support who might be able to advice you.

Alternative: Voice Phishing
A voice phishing is similar to the previous one. The only difference is that the perpetrator will impersonate a company, or institution over the phone.
Example:
You receive a call from your Internet Provider.
They explain that they noticed strange activity over your network and that they will help you resolve it.
They ask you to open your laptop and run a few actions. They will often start with simple.
Once they got your trusts they will ask you to execute more complex ones that will for instance:
- Open a backdoor to give the attacker access to the computer
- Encrypt all your files and blackmail you to decrypt them
- Download malware to your computer
- Steal sensitive or personal information
How to prevent it?
Always ask for the identity of the person who calls you.
Never run or do anything on your computer that you do not know or fully understand.
Example of Phishing Campaign
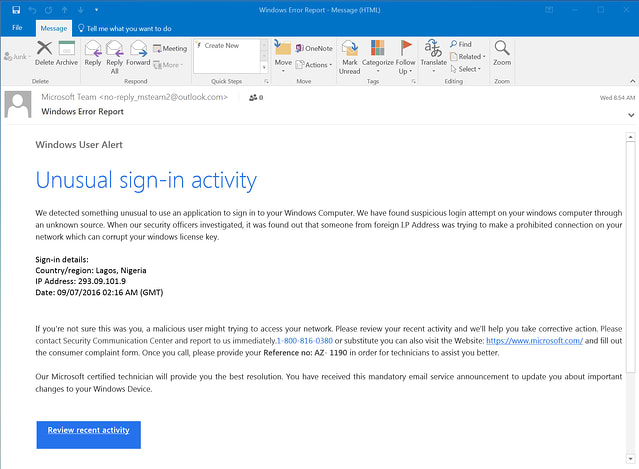
Let's take a look at the above image and how we can recognize it is a phishing attempt.
Looking at the sender email we already see something out of the ordinary.
The sender email is:no-reply_msteam2@outlook.com
As much as theoutlook.comis real the first partno-reply_msteam2clearly shows that this was a registered email. Most official emails come from simple addresses such assupport@outlook.comThe title of the email is very generic
Windows Error Report. Most sign-in attempt will usually have email title such asWe have detected unusual activity on your accountThe email head is also very generic
Windows User Alertany big company will always be able to identify you either through your username, name or even email. For exampleHello Mr.DoeorHey @cool_usernameLanguage! Just looking at the first sentence we can see some language and sentence structure issues
We detected something unusual to use an application to sign in to your Windows ComputerThe email also contains nonsensical logic. This might be hard to spot by non-tech people. If you have any doubt about an email it is best to ask your tech support. The whole idea that Microsoft has officers looking at a sign-in attempt from every user is not feasible. The whole sentence
a prohibited connection on your network which can corrupt your windows license keyalso doesn't mean much in IT terms.In the email there is also a fake phone number. Looking at the official Microsoft support page we can see that there are no numbers similar to the one in the email: https://support.microsoft.com/en-us/help/4051701/global-customer-service-phone-numbers
This is why it is important to go through the official support channels if you get an email asking you to contact the support team.
**This email is classified as a typical phishing attack. If services or companies require you to update some personal information about your account it is always best practice to go through the official website. Any issues with your account will be flagged in your personal dashboard.
About Us
Pixium Digital is an agile software development company with their headquarters located in Singapore. We focus on shaping our clients project from ideas to successful project launch.
Cyber Security is a big part of any project we have to deliver. Very often we have been the witness of lack of awareness or caution from various providers or clients we have worked with. We aim to share those little tips to the community so that with everyone's effort, we can make the web a safer place.






 已为社区贡献22914条内容
已为社区贡献22914条内容

所有评论(0)