k8s中apisix-3.8.0与etcd连接基于mtls认证
【代码】k8s中apisix-3.8.0与etcd连接基于mtls认证。
·
版本
| 软件 | 版本 |
|---|---|
| apisix | 3.8.0 |
| apisix-chart | 2.6.0 |
| apisix-dashboard | 0.8.1 |
| k8s | v1.23.17 |
| etcd | 3.5.6-0 |
| kubeadm | 1.23.17 |
安装
新建secret
kubectl create secret tls etcd-tls --key server.key --cert server.crt -n ingress-apisix
kubectl create secret tls etcd-ca-tls --key ca.key --cert ca.crt -n ingress-apisix
[root@k8s-test-01 etcd]# kubectl get secret -n ingress-apisix |grep etcd
etcd-ca-tls kubernetes.io/tls 2 23h
etcd-tls kubernetes.io/tls 2 23h
证书查看
- 这个查看了
etcd-tls的证书内容,crt内容存放至tls.crt字段内,key内容存放至tls.key字段内。 - tls.crt和tls.key,俩个字段,当挂载至k8s内,则以文件名存在。需要注意configmap和deployment的文件引用,需要和这里保持一致
[root@k8s-test-01 etcd]# kubectl get secret etcd-tls -n ingress-apisix -oyaml
apiVersion: v1
data:
tls.crt: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSURjekNDQWx1Z0F3SUJBZ0lJR3Y3WjdhQ0xQcXN3RFFZSktvWklodmNOQVFFTEJRQXdFakVRTUE0R0ExVUUKQXhNSFpYUmpaQzFqWVRBZUZ3MHlOREF5TURJd01qQXlOVEJhRncweU5UQXlNREV3TWpBeU5URmFNQll4RkRBUwpCZ05WQkFNVEMyczRjeTEwWlhOMExUQXhNSUlCSWpBTkJna3Foa2lHOXcwQkFRRUZBQU9DQVE4QU1JSUJDZ0tDCkFRRUF3Z2pGU3g3UWU3L3dWVXhWbU5NOGEzcDk3STJPTXh0cnJJNGVVd3p1b3JvSFRVdTlLK2xKZzk3RytHY0YKMlVMRGNoVVJxMDgrbDhZVExqdTgweG1zTURndTB6MnhoY0ZKS2tCdUhjNTF3OVpWMmNtbldieW1lWGJQcTc1TApuZkVGMkMzcjErUGZHVnkrT09Ocit0VXdPYVNFWVhRcmxLNDExTWV3Rk93bENIcGE1NFE1MGt6VzBMVkYrN1ErCjhxeTVvb2lDTmVXSHYyQUlsRXZaekdzRmFONHRzOG92Yk1zd0JWU29tTitOd05BQlBOR2xza21YM0s2aFpNSVYKZDNiUEJBNHlJT3JIRlErTHg0bnRHc1hnMERPM25DeTFDUTVSbSs5WHU3VmxlVTI2UVNmUVBCeXRQQUFQSldMcwo4YkU1RlJNak1wRVJUUzhYTlJ2UzV2dmJqd0lEQVFBQm80SElNSUhGTUE0R0ExVWREd0VCL3dRRUF3SUZvREFkCkJnTlZIU1VFRmpBVUJnZ3JCZ0VGQlFjREFRWUlLd1lCQlFVSEF3SXdEQVlEVlIwVEFRSC9CQUl3QURBZkJnTlYKSFNNRUdEQVdnQlRpZXVhNER5YzZqSm5QRy81KzFyOXJhbTY5WXpCbEJnTlZIUkVFWGpCY2dndHJPSE10ZEdWegpkQzB3TVlJTGF6aHpMWFJsYzNRdE1ES0NDMnM0Y3kxMFpYTjBMVEF6Z2dsc2IyTmhiR2h2YzNTSEJBb0tDbWFICkJIOEFBQUdIRUFBQUFBQUFBQUFBQUFBQUFBQUFBQUdIQkFvS0NrNkhCQW9LQ2wwd0RRWUpLb1pJaHZjTkFRRUwKQlFBRGdnRUJBQmlZKzJUcGtWZnlVRjlhRG53MzV4TGwwbUFlY2lEYjlGdDVJaDFtWGFKbEhNZ0k1WDNmQjQ4WApGTTZxZUZHM0Q4ODVrNkxObmpNU28xK1ZxdE92MStOaHE0WTR2dmNROVQ2SmZSRWVRUjJ0SVpqWlo1bHZIc2dECkFnNGNGd2NrNVRuc2hZOXRHbmVzVDVCKzdkUzU5ZTFOcnVKVXpkMnJzVC9Mc1pyZG8xK2owS01MVjRBbnA1bmoKOHU3QWcrNThJWTcrNGJ2dGltV1IxT3ExRUtKRXljSDMxaW9CcUJRL0FwVEFhOFdRSnJFT0lzSncrY3dLN21nbwpEWU9tNnRCT1U2SW1GeHVUYm9CRXlRZGVpbXZEL2QyM1EwNTBqSmtkb1YvV3R3TXhrZG5nZVlkcE5UUzUrUERoCkVkcDc5TVBrSlQrRjRPc2pVa1FLTVdub0lPUnpuYms9Ci0tLS0tRU5EIENFUlRJRklDQVRFLS0tLS0K
tls.key: LS0tLS1CRUdJTiBSU0EgUFJJVkFURSBLRVktLS0tLQpNSUlFcEFJQkFBS0NBUUVBd2dqRlN4N1FlNy93VlV4Vm1OTThhM3A5N0kyT014dHJySTRlVXd6dW9yb0hUVXU5CksrbEpnOTdHK0djRjJVTERjaFVScTA4K2w4WVRManU4MHhtc01EZ3UwejJ4aGNGSktrQnVIYzUxdzlaVjJjbW4KV2J5bWVYYlBxNzVMbmZFRjJDM3IxK1BmR1Z5K09PTnIrdFV3T2FTRVlYUXJsSzQxMU1ld0ZPd2xDSHBhNTRRNQowa3pXMExWRis3USs4cXk1b29pQ05lV0h2MkFJbEV2WnpHc0ZhTjR0czhvdmJNc3dCVlNvbU4rTndOQUJQTkdsCnNrbVgzSzZoWk1JVmQzYlBCQTR5SU9ySEZRK0x4NG50R3NYZzBETzNuQ3kxQ1E1Um0rOVh1N1ZsZVUyNlFTZlEKUEJ5dFBBQVBKV0xzOGJFNUZSTWpNcEVSVFM4WE5SdlM1dnZiandJREFRQUJBb0lCQVFDUmo5emFmeEp1VTg2cgpYdW0wRFh2OU1WWjRlTFZkMTh0T0Z3dmV5QXZhSGU3T2FPeFFuZUZkd1duSS9oaWdKWHJVQWNSUW5ORmJNT2hBCnZlWHBCQkJ0MkNnZ3B0NmZkaUk2UlQyV3RNVWFGcGd2R3gybHIyWEFKNGFoMDgrTWZEMGpNVWdGbk5oSWdZL2UKdzVYRkJkdjQwbGZSZUVJZGR4ZkJPZEQ1MFRIekNlOUJFOG5Lc3B4MUcrK29JWXQzRXdtNURSeHhaSk1WamRnTQp3SUtqRGYrTWl5QWJGZ29CZUlNditkYWVqbzYyQlh1ajhoOFZxYllrMDlGeXkySExFRVZxZVNHbWhaRGpPZDdRCnFxQjBSbFBpVjZQNnFxY1RHWlhxa1pMRUQrU1FqNDBhZE9jVkNCcnRHV1ZwdTErM2hjNTVkampvaXhzVUdNNG4KSEMrOTdDa0JBb0dCQU1tQ1Q3dm5PemlMNFVoNWF1VXlVRlBpZTJLR3BpVWdNNVdWUGxxekVxNFcwSFoxVCtpTgpIdUdmRnFhcTRjRTFRRmdhUlZRVGZtdFFxMFNueGNoWUJGbCt5SVhIcWVMT0NwVVZ0RGwvV0Y4NUNLQWZSMnloCjZDN1I5RmFwM0VBUVUvVWdvem5uMHE0LzVDWXVadm8rTVJlU25LS0tmenZDQVRUZFNKOSt0cVdCQW9HQkFQYUIKQW8xNVhoemg5aWpYUTFRSDdEYnpHZU4rcHFiK1gyNjlOb3AzMG00L3gyTWo0K0pFZU1wWDNaeis5eFNra3dxdwp0Rmd6K0FNYUdjcmFDK1NkN2M4eU5UdjJxSnkxZWM2NmZkd1BmSnNGNHVWSDRySkJwU0RWNkRYbGJKdnNXTGg2CnNua3JyeW1HU2gvUnhCWGlsdWxONlNHOEpIVEpkZEo1QXlzR0Jxa1BBb0dBVVdFS0dHV2EyZ3hMci93dytsem0KYWVvbVVEVDJ0am1aKzRmcFJiSGFFbXB1UjlpNnE3MEtRcTMvOU5GQUdNb0xzVWp5eExDV3RubytvSnhzMktzTApIcVdBRDk4QnNmSHAvaWxrdm0rNlhjSm54RnE5ZXBhc2NQUWpqRGhQRmFSQ2M5VjVkZkkwZUdDZkgvaFBhREpqCm14Ui9vM2p4UjAzak5ObEU4ZnkzZ0lFQ2dZRUE5aWxqQ1RDWVFUT05oTDlpNXZsNmRHMVQveEN0RDdxYVJwWUIKYjBtMUJKQUFad3FpT1lTek15MkhpNDQ1NDQxdG9aRlFwM3hPUVpyQkF3ZTROTGRaa2ozTFYzUThjVEh3ei9jQQpWTS9LV1cwSlpubmc4cTRIWHNEK1FVUTRyNFRZSEhHNjVMSXhHOENWS1MxcktZZTd1SVFyT1pzT3RPbXlGVnJ2ClJQbWhrUlVDZ1lCejZLZ0tXWVBMb1FFWkVLYUpjL09UQkt4UFlvTEZkM1Jsby9aVGtnbWl6cjdrZVJrbitLODIKcVJLNkFiQ21KOVJ4ZFl6MXdJZDdyTkdsSDVIRDJIUndONnB4OHEwM1RjWS9oZXJWNmVYVkgvUTNrVDRvSTZUbwptQVpWOW9VSlZWd0tGenBoOVorTlA5MEdLeTlKcldhc0d6QkJKTXYyaDBLZzlDVDFCRXJZbEE9PQotLS0tLUVORCBSU0EgUFJJVkFURSBLRVktLS0tLQo=
kind: Secret
metadata:
creationTimestamp: "2024-02-18T06:25:58Z"
name: etcd-tls
namespace: ingress-apisix
resourceVersion: "4280771"
uid: e6124fd1-61ac-489c-9757-bf83dc13ea41
type: kubernetes.io/tls
apisix支持tls连接
- 配置values.yaml,支持etcd tls认证
# -- external etcd configuration. If etcd.enabled is false, these configuration will be used.
externalEtcd:
# -- if etcd.enabled is false, use external etcd, support multiple address, if your etcd cluster enables TLS, please use https scheme, e.g. https://127.0.0.1:2379.
host:
# host or ip e.g. http://172.20.128.89:2379
## 这里配置支持tls链接的etcd
- https://10.10.10.102:2379
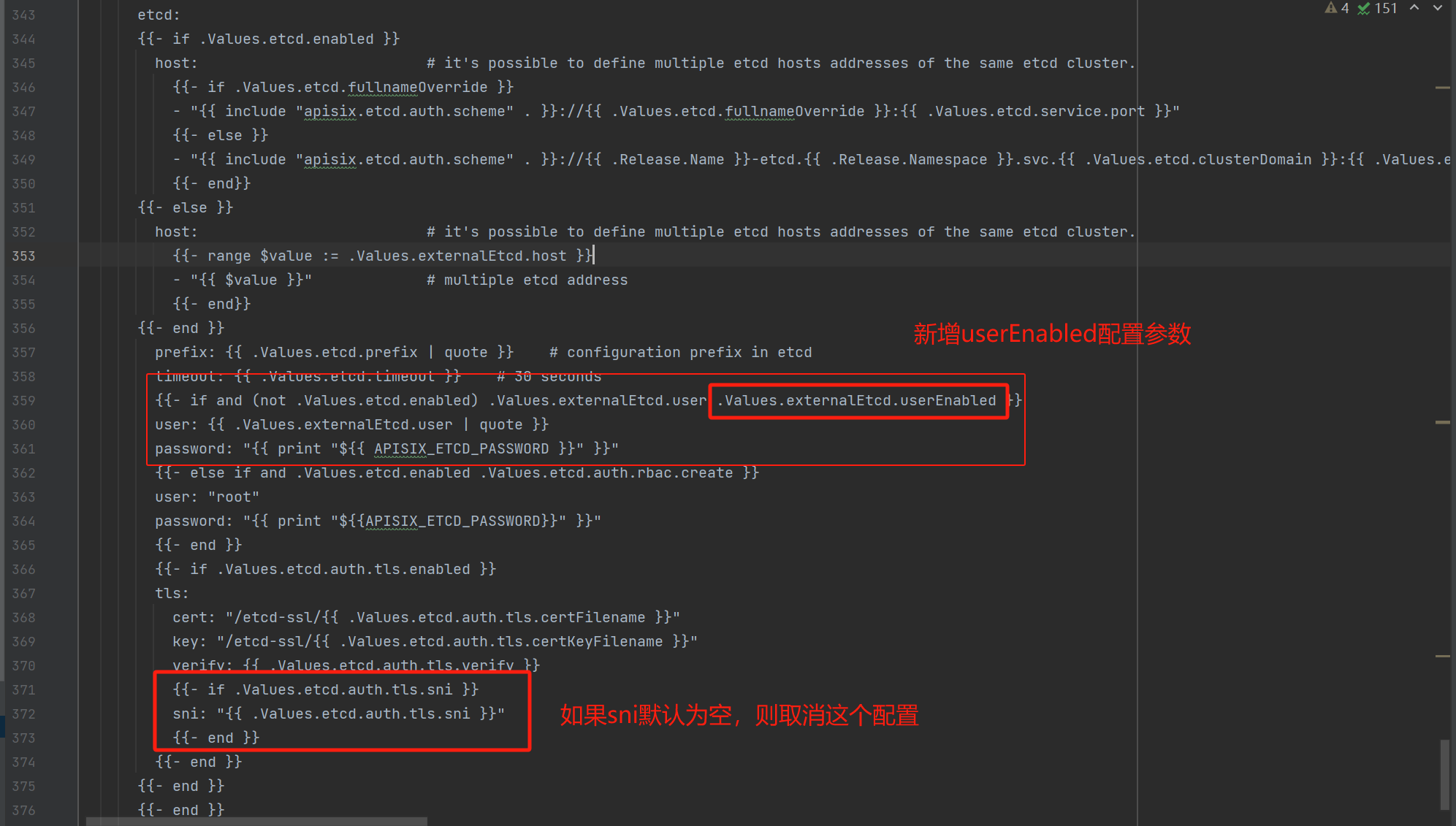
# -- 禁止使用用户账号
## 自定义参数: 关闭使用用户认证,否则apisix的配置deployment.etcd.user和deployment.etcd.password会有配置。
userEnabled: false
# -- if etcd.enabled is false, user for external etcd. Set empty to disable authentication
user: root
# -- if etcd.enabled is true, use etcd.auth.rbac.rootPassword instead.
# -- if etcd.enabled is false and externalEtcd.existingSecret is not empty, the password should store in the corresponding secret
# -- if etcd.enabled is false and externalEtcd.existingSecret is empty, externalEtcd.password is the passsword for external etcd.
password: ""
# -- if externalEtcd.existingSecret is the name of secret containing the external etcd password
existingSecret: ""
# -- externalEtcd.secretPasswordKey Key inside the secret containing the external etcd password
secretPasswordKey: "etcd-root-password"
# -- etcd configuration
# use the FQDN address or the IP of the etcd
etcd:
# -- install etcd(v3) by default, set false if do not want to install etcd(v3) together
## 设置false,禁止使用内部http连接的etcd
enabled: false
# -- apisix configurations prefix
## 数据存储位置
prefix: "/apisix"
# -- Set the timeout value in seconds for subsequent socket operations from apisix to etcd cluster
timeout: 30
# -- if etcd.enabled is true, set more values of bitnami/etcd helm chart
auth:
rbac:
# -- No authentication by default. Switch to enable RBAC authentication
create: false
# -- root password for etcd. Requires etcd.auth.rbac.create to be true.
rootPassword: ""
tls:
# -- enable etcd client certificate
## 启用apisix和etcd的tls认证
enabled: true
# -- name of the secret contains etcd client cert
## 连接etcd的证书存储secret
existingSecret: "etcd-tls"
# -- etcd client cert filename using in etcd.auth.tls.existingSecret
## 连接etcd的crt名称,默认是tls.crt
certFilename: "tls.crt"
# -- etcd client cert key filename using in etcd.auth.tls.existingSecret
## 连接etcd的key名称,默认是tls.key
certKeyFilename: "tls.key"
# -- whether to verify the etcd endpoint certificate when setup a TLS connection to etcd
## 这里设置false,否则会报错
verify: false
# -- specify the TLS Server Name Indication extension, the ETCD endpoint hostname will be used when this setting is unset.
## sni默认为空,则配置文件不会填写,如下图
sni: ""
service:
port: 2379
replicaCount: 3

apisix-dashboard 支持tls连接
values.yaml新增mtls配置
config:
conf:
listen:
# -- The address on which the Manager API should listen.
# The default value is 0.0.0.0, if want to specify, please enable it.
# This value accepts IPv4, IPv6, and hostname.
host: 0.0.0.0
# -- The port on which the Manager API should listen.
port: 9000
etcd:
# -- Supports defining multiple etcd host addresses for an etcd cluster
endpoints:
- apisix-etcd:2379
# -- apisix configurations prefix
prefix: "/apisix"
# -- Specifies etcd basic auth username if enable etcd auth
username: ~
# -- Specifies etcd basic auth password if enable etcd auth
password: ~
## -- 以下是新增mtls配置,dashboard支持tls认证
mtls:
# -- 是否支持tls认证
enabled: true
# -- 存放ca证书的secret名称
existingCASecret: "etcd-ca-tls"
# -- 存放etcd证书的secret名称
existingETCDSecret: "etcd-tls"
configmap.yaml修改
- 新增
conf.etcd.mtls配置
{{- if .mtls.enabled }}
mtls:
key_file: "/etcd-ssl/tls.key"
cert_file: "/etcd-ssl/tls.crt"
ca_file: "/ca-ssl/tls.crt"
{{- end }}

deployment.yaml修改
- 将新增的证书文件,挂载至容器内部,挂在位置和configmap配置保持一致
volumeMounts:
- mountPath: /usr/local/apisix-dashboard/conf/conf.yaml
name: apisix-dashboard-config
subPath: conf.yaml
{{- if .Values.config.conf.etcd.mtls.enabled }}
- mountPath: /ca-ssl/tls.crt
name: ca-ssl
subPath: tls.crt
- mountPath: /etcd-ssl
name: etcd-ssl
{{- end }}
volumes:
- configMap:
name: {{ include "apisix-dashboard.fullname" . }}
name: apisix-dashboard-config
{{- if .Values.config.conf.etcd.mtls.enabled }}
- secret:
secretName: {{ .Values.config.conf.etcd.mtls.existingCASecret | quote }}
name: ca-ssl
- secret:
secretName: {{ .Values.config.conf.etcd.mtls.existingETCDSecret | quote }}
name: etcd-ssl
{{- end }}

附件
https://github.com/apache/apisix-dashboard/blob/master/api/conf/conf.yaml
apisix-dashboard配置文件
# yamllint disable rule:comments-indentation
conf:
listen:
# host: 127.0.0.1 # the address on which the `Manager API` should listen.
# The default value is 0.0.0.0, if want to specify, please enable it.
# This value accepts IPv4, IPv6, and hostname.
port: 9000 # The port on which the `Manager API` should listen.
# ssl:
# host: 127.0.0.1 # the address on which the `Manager API` should listen for HTTPS.
# The default value is 0.0.0.0, if want to specify, please enable it.
# port: 9001 # The port on which the `Manager API` should listen for HTTPS.
# cert: "/tmp/cert/example.crt" # Path of your SSL cert.
# key: "/tmp/cert/example.key" # Path of your SSL key.
allow_list: # If we don't set any IP list, then any IP access is allowed by default.
- 127.0.0.1 # The rules are checked in sequence until the first match is found.
- ::1 # In this example, access is allowed only for IPv4 network 127.0.0.1, and for IPv6 network ::1.
# It also support CIDR like 192.168.1.0/24 and 2001:0db8::/32
etcd:
endpoints: # supports defining multiple etcd host addresses for an etcd cluster
- 127.0.0.1:2379
# yamllint disable rule:comments-indentation
# etcd basic auth info
# username: "root" # ignore etcd username if not enable etcd auth
# password: "123456" # ignore etcd password if not enable etcd auth
mtls:
key_file: "" # Path of your self-signed client side key
cert_file: "" # Path of your self-signed client side cert
ca_file: "" # Path of your self-signed ca cert, the CA is used to sign callers' certificates
# prefix: /apisix # apisix config's prefix in etcd, /apisix by default
更多推荐
 已为社区贡献1条内容
已为社区贡献1条内容






所有评论(0)