XCTF----handcrafted-pyc
1. 拿到文件,先进行查壳,收集基本信息#!/usr/bin/env python# -*- coding: utf-8 -*-import marshal, zlib, base64exec(marshal.loads(zlib.decompress(base64.b64decode('eJyNVktv00AQXm/eL0igiaFA01IO4cIVCUGFBBJwqRAckLhEIQmtRfP
1. 拿到文件,先进行查壳,收集基本信息
#!/usr/bin/env python
# -*- coding: utf-8 -*-
import marshal, zlib, base64
exec(marshal.loads(zlib.decompress(base64.b64decode('eJyNVktv00AQXm/eL0igiaFA01IO4cIVCUGFBBJwqRAckLhEIQmtRfPwI0QIeio/hRO/hJ/CiStH2M/prj07diGRP43Hs9+MZ2fWMxbnP6mux+oK9xVMHPFViLdCTB0xkeKDFEFfTIU4E8KZq8dCvB4UlN3hGEsdddXU9QTLv1eFiGKGM4cKUgsFCNLFH7dFrS9poayFYmIZm1b0gyqxMOwJaU3r6xs9sW1ooakXuRv+un7Q0sIlLVzOCZq/XtsK2oTSYaZlStogXi1HV0iazoN2CV2HZeXqRQ54TlJRb7FUlKyUatISsdzo+P7UU1Gb1POdMruckepGwk9tIXQTftz2yBaT5JQovWvpSa6poJPuqgao+b9l5Aj/R+mLQIP4f6Q8Vb3g/5TB/TJxWGdZr9EQrmn99fwKtTvAZGU7wzS7GNpZpDm2JgCrr8wrmPoo54UqGampFIeS9ojXjc4E2yI06bq/4DRoUAc0nVnng4k6p7Ks0+j/S8z9V+NZ5dhmrJUM/y7JTJeRtnJ2TSYJvsFq3CQt/vnfqmQXt5KlpuRcIvDAmhnn2E0t9BJ3SvB/SfLWhuOWNiNVZ+h28g4wlwUp00w95si43rZ3r6+fUIEdgOZbQAsyFRRvBR6dla8KCzRdslar7WS+a5HFb39peIAmG7uZTHVm17Czxju4m6bayz8e7J40DzqM0jr0bmv9PmPvk6y5z57HU8wdTDHeiUJvBMAM4+0CpoAZ4BPgJeAYEAHmgAUgAHiAj4AVAGORtwd4AVgC3gEmgBBwCPgMWANOAQ8AbwBHgHuAp4D3gLuARwoGmNUizF/j4yDC5BWM1kNvvlxFA8xikRrBxHIUhutFMBlgQoshhPphGAXe/OggKqqb2cibxwuEXjUcQjccxi5eFRL1fDSbKrUhy2CMb2aLyepkegDWsBwPlrVC0/kLHmeCBQ=='))))
分析一下,经过了:
base64.b64decode() base64解码
zlib.decompress() 解压字符串
marshal.loads() 对字节码组织
exec() 执行括号内的命令
那么我们就按照题目的意思进行解码
2.
import marshal,zlib,base64
out=zlib.decompress(base64.b64decode('eJyNVktv00AQXm/eL0igiaFA01IO4cIVCUGFBBJwqRAckLhEIQmtRfPwI0QIeio/hRO/hJ/CiStH2M/prj07diGRP43Hs9+MZ2fWMxbnP6mux+oK9xVMHPFViLdCTB0xkeKDFEFfTIU4E8KZq8dCvB4UlN3hGEsdddXU9QTLv1eFiGKGM4cKUgsFCNLFH7dFrS9poayFYmIZm1b0gyqxMOwJaU3r6xs9sW1ooakXuRv+un7Q0sIlLVzOCZq/XtsK2oTSYaZlStogXi1HV0iazoN2CV2HZeXqRQ54TlJRb7FUlKyUatISsdzo+P7UU1Gb1POdMruckepGwk9tIXQTftz2yBaT5JQovWvpSa6poJPuqgao+b9l5Aj/R+mLQIP4f6Q8Vb3g/5TB/TJxWGdZr9EQrmn99fwKtTvAZGU7wzS7GNpZpDm2JgCrr8wrmPoo54UqGampFIeS9ojXjc4E2yI06bq/4DRoUAc0nVnng4k6p7Ks0+j/S8z9V+NZ5dhmrJUM/y7JTJeRtnJ2TSYJvsFq3CQt/vnfqmQXt5KlpuRcIvDAmhnn2E0t9BJ3SvB/SfLWhuOWNiNVZ+h28g4wlwUp00w95si43rZ3r6+fUIEdgOZbQAsyFRRvBR6dla8KCzRdslar7WS+a5HFb39peIAmG7uZTHVm17Czxju4m6bayz8e7J40DzqM0jr0bmv9PmPvk6y5z57HU8wdTDHeiUJvBMAM4+0CpoAZ4BPgJeAYEAHmgAUgAHiAj4AVAGORtwd4AVgC3gEmgBBwCPgMWANOAQ8AbwBHgHuAp4D3gLuARwoGmNUizF/j4yDC5BWM1kNvvlxFA8xikRrBxHIUhutFMBlgQoshhPphGAXe/OggKqqb2cibxwuEXjUcQjccxi5eFRL1fDSbKrUhy2CMb2aLyepkegDWsBwPlrVC0/kLHmeCBQ=='))
f=open('out','wb')
f.write(out)
f.close()
然后在这个python文件的同一目录中就会生成一个名为out的文件

然后使用uncomple6 命令进行解压(注意将out重命名为out.pyc)
但是我们可以发现这个时候解压并没有成功
后来参考大佬的wp才知道,该文件缺少文件头,那么我们使用16进制工具winhex进行添加文件头

文件头为:
03 F3 0D 0A C8 C4 A1 58(具体还是要根据你所使用的python版本而定,我用的是python2)

虽然显示反编译错误,但是该文件可以被打开了
3.打开该文件

1000多行,我就不一一放出来了
分析汇编代码,注意到有
BINARY_ADD
ROT_TWO
两个特殊的函数
百度一下,它们一个是交换,一个是求和
那么我们先提取字符再用python模拟这两个函数
4.脚本

import re
with open("out.py",'r')as f:
line=[]
for i in range(1000):
line.append(f.readline())
list=[]
pat="(\d*)\n"
for i in line:
if 'LOAD_CONST'in i:
text=re.compile(pat).findall(i)
for j in text:
list.append(j)
for i in list:
if(i==''):
print("")
else:
print(chr(int(i)),end='')
得到字符串为:llaC em yP aht notriv lauhcamni !eac Ini npreterP tohty ntybdocese!!!
ctihN{noy woc uoc naipmoa eldnur yP nnohttyb doceni euoy rb ria}!napwssro :dorWp gnssadrow...elP esa yrtaga .ni oD tonurbf etecro)= .
然后通过python对两个函数进行模拟
with open("out.py",'r') as f:
line = []
for i in range(1000):
line.append(f.readline())
def ROT_TWO(List):
a = List.pop()
b = List.pop()
List.append(a)
List.append(b)
return List
def BINARY_ADD(List):
a = List.pop()
b = List.pop()
List.append(b+a)
return List
cipher ="llaC em yP aht notriv lauhcamni !eac Ini npreterP tohty ntybdocese!!! ctihN{noy woc uoc naipmoa eldnur yP nnohttyb doceni euoy rb ria}!napwssro :dorWp gnssadrow...elP esa yrtaga .ni oD tonurbf etecro)= ."
cipher = list(cipher)
s =[]
j=0
for i in line:
if 'LOAD_CONST' in i and j < len(cipher):
s.append(cipher[j])
j += 1
elif 'ROT_TWO' in i:
s = ROT_TWO(s)
elif 'BINARY_ADD' in i:
s = BINARY_ADD(s)
print (s)
运行脚本
得到答案
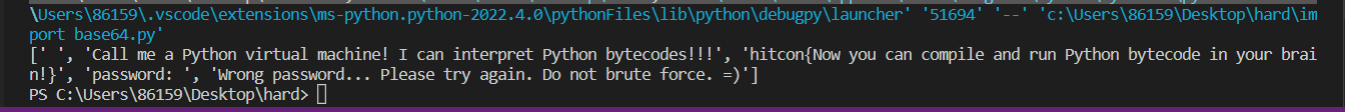
得到flag为:hitcon{Now you can compile and run Python bytecode in your brain!}
更多推荐
 已为社区贡献1条内容
已为社区贡献1条内容







所有评论(0)