gitlab-webhook+argoEvents+argoWorkflows
argoEvents集成gitlabWebhook文章目录argoEvents集成gitlabWebhook前言一、环境准备二、过程1.准备好argo环境,具体参照官网2. argoEvents集成gitlabWebhook步骤总结前言使用argoEvents集成gitlabwebhook,记录下学习以及踩坑过程。一、环境准备centos8Linux本地 gitlab仓库K8s1.8argoEve
·
argoEvents集成gitlabWebhook
前言
使用argoEvents集成gitlabwebhook,记录下学习以及踩坑过程。
一、环境准备
centos8
Linux本地 gitlab仓库
K8s 1.8
argoEvents 1.4
argoWorkflow V3.1.8
二、过程
1.准备好argo环境,具体参照官网
官网链接: link.
安装好argoEvents 和argoWorkflows环境
注意不同命名空间的权限问题
官网给出的示例不可以直接用!!
由于argoEvents不具备argo命名空间中的权限
需要给它分配权限
ServiceAccount.yaml如下:
apiVersion: v1
kind: ServiceAccount
metadata:
namespace: argo-events
name: operate-workflow-sa
---
apiVersion: rbac.authorization.k8s.io/v1
kind: Role
metadata:
name: operate-workflow-role
namespace: argo-events
rules:
- apiGroups:
- argoproj.io
verbs:
- "*"
resources:
- workflows
---
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
name: operate-workflow-role-binding
namespace: argo-events
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: Role
name: operate-workflow-role
subjects:
- kind: ServiceAccount
name: operate-workflow-sa
namespace: argo-events
shell:
kubectl -n argo-events apply -f sensor-service-accounts.yaml
2. argoEvents集成gitlabWebhook步骤
- 在gitlab生成apitoken授予他api权限
- Base64 编码api 令牌密钥:
echo -n <api-token-key> | base64
- 创建一个K8S sercret 叫 gitlab-access
apiVersion: v1
kind: Secret
metadata:
name: gitlab-access
type: Opaque
data:
token: <base64-encoded-api-token-from-previous-step>
kubectl -n argo-events apply -f gitlab-access.yaml
- 创建eventSource
踩坑:使用官网默认页面配置失败,需要去官方github选取自己的argoEvents版本的分支,进行配置本文使用的版本是v1.4.0
支持仓库eventSource
# More info on GitLab project hooks: https://docs.gitlab.com/ce/api/projects.html#add-project-hook
apiVersion: argoproj.io/v1alpha1
kind: EventSource
metadata:
name: gitlab
spec:
service:
ports:
- port: 12000
targetPort: 12000
gitlab:
example:
# Project namespace paths or IDs
projects:
- "whynowy/test"
- "3"
# Github will send events to following port and endpoint
webhook:
# endpoint to listen to events on
endpoint: /push
# port to run internal HTTP server on
port: "12000"
# HTTP request method to allow. In this case, only POST requests are accepted
method: POST
# url the event-source will use to register at GitLab.
# This url must be reachable from outside the cluster.
# The name for the service is in `<event-source-name>-eventsource-svc` format.
# You will need to create an Ingress or Openshift Route for the event-source service so that it can be reached from GitLab.
url: http://url-that-is-reachable-from-GitLab
# events to listen to
# Visit https://docs.gitlab.com/ee/user/project/integrations/webhooks.html#events
events:
- PushEvents
- TagPushEvents
# accessToken refers to K8s secret that stores the gitlab api token
accessToken:
# Key within the K8s secret whose corresponding value (must be base64 encoded) is access token
key: token
# Name of the K8s secret that contains the access token
name: gitlab-access
# secret token used by gitlab webhook
secretToken:
key: token
name: gitlab-secret
# Do SSL verification when triggering the hook
enableSSLVerification: false
# Gitlab Base url.
# Change it to your private GitLab instance url if you have one.
gitlabBaseURL: https://gitlab.com
deleteHookOnFinish: true
# example-secure:
# projectId: "2"
# webhook:
# endpoint: "/push"
# port: "13000"
# method: "POST"
# url: "http://mysecondfakeurl.fake"
# # k8s secret that contains the cert
# serverCertSecret:
# name: my-secret
# key: cert-key
# # k8s secret that contains the private key
# serverKeySecret:
# name: my-secret
# key: pk-key
# events:
# - PushEvents
# accessToken:
# key: accesskey
# name: gitlab-access
# enableSSLVerification: true
# gitlabBaseURL: "YOUR_GITLAB_URL"
- 注册到Sensor
apiVersion: argoproj.io/v1alpha1
kind: Sensor
metadata:
name: gitlab
spec:
template:
serviceAccountName: operate-workflow-sa
dependencies:
- name: a
eventSourceName: gitlab
eventName: a-1
- name: b
eventSourceName: gitlab
eventName: b-1
triggers:
- template:
conditions: "a || b" ## 多个EventSource需要添加条件
name: gitlab-workflow-trigger
k8s:
group: argoproj.io
version: v1alpha1
resource: workflows
operation: create
source:
resource:
apiVersion: argoproj.io/v1alpha1
kind: Workflow
metadata:
generateName: gitlab-workflow-
spec:
entrypoint: whalesay
arguments:
parameters:
- name: message
# value will get overridden by the event payload
value: hello world
templates:
- name: whalesay
inputs:
parameters:
- name: message
container:
image: docker/whalesay:latest
command: [cowsay]
args: ["{{inputs.parameters.message}}"]
parameters:
- src:
dependencyName: a
dest: spec.arguments.parameters.0.value
parameters:
- src:
dependencyName: b
dest: spec.arguments.parameters.0.value
暴露Pod端口
[root@k8s-master ingress]# kubectl get pod,svc,ingress,EventSource -n argo-events
NAME READY STATUS RESTARTS AGE
pod/eventbus-controller-69b7f5955f-gqrxs 1/1 Running 0 2d4h
pod/eventbus-default-stan-0 2/2 Running 0 2d4h
pod/eventbus-default-stan-1 2/2 Running 0 2d4h
pod/eventbus-default-stan-2 2/2 Running 0 2d4h
pod/eventsource-controller-5fb9fc8bf9-skw7x 1/1 Running 0 2d4h
pod/gitlab-eventsource-pz5rx-5b4b7b5f69-lfpjs 1/1 Running 0 6s
pod/gitlab-sensor-5jt6g-7c96655645-5xlc4 0/1 ContainerCreating 0 6s
pod/sensor-controller-78f8fd8645-hmcvb 1/1 Running 0 2d4h
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
service/eventbus-default-stan-svc ClusterIP None <none> 4222/TCP,6222/TCP,8222/TCP 2d4h
service/gitlab-eventsource-svc ClusterIP 10.108.78.110 <none> 12000/TCP 6s
NAME AGE
eventsource.argoproj.io/gitlab 6s
[root@k8s-master ingress]# kubectl -n argo-events port-forward pod/gitlab-eventsource-pz5rx-5b4b7b5f69-lfpjs 12000:12000
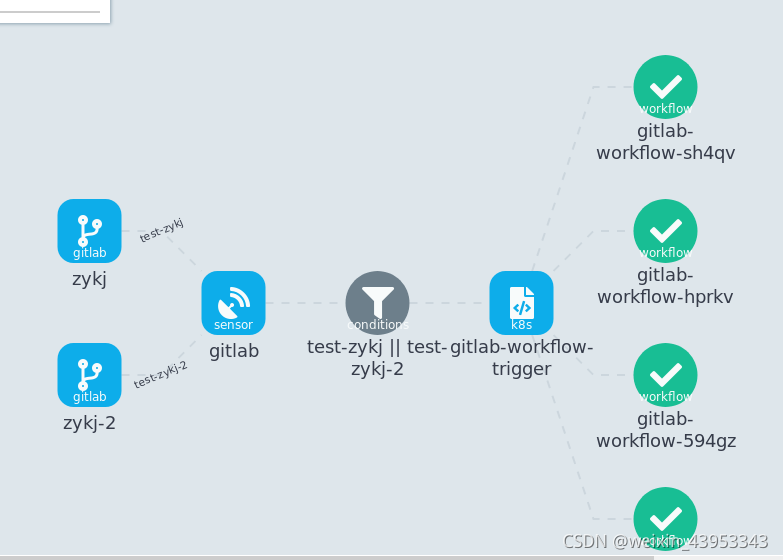
- 触发giltlab中webhook 如图所示
总结
主要是对自己踩坑做一个总结,因是java刚转到sre。需要转换思维思考问题,而不是像以前一个死抓代码逻辑层思考。 1. 学习新的框架,技术时多看官方文档,看官方文档前留意版本问题!!更多推荐
 已为社区贡献3条内容
已为社区贡献3条内容









所有评论(0)