在 CentOS 7 上安装 Wazuh 服务器

- 首先更改主机名
# hostnamectl set-hostname wazuh-server
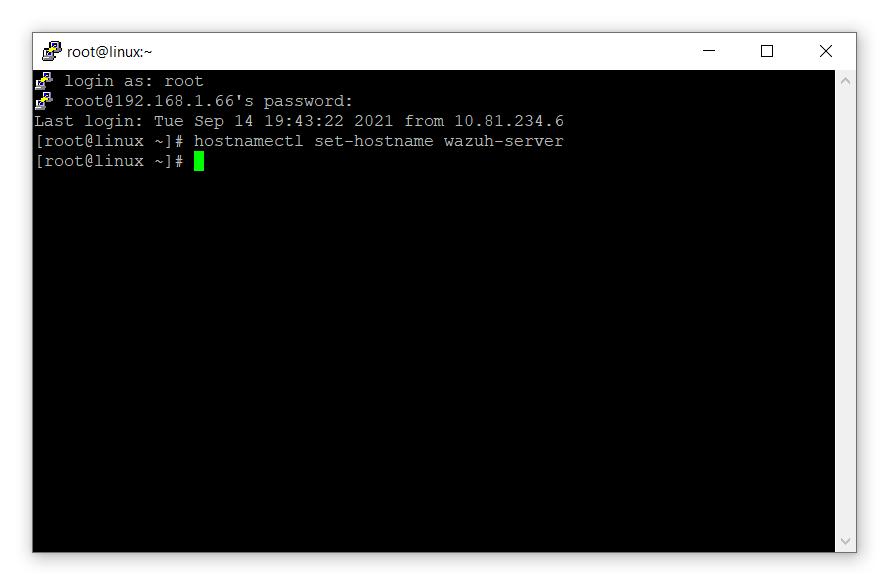
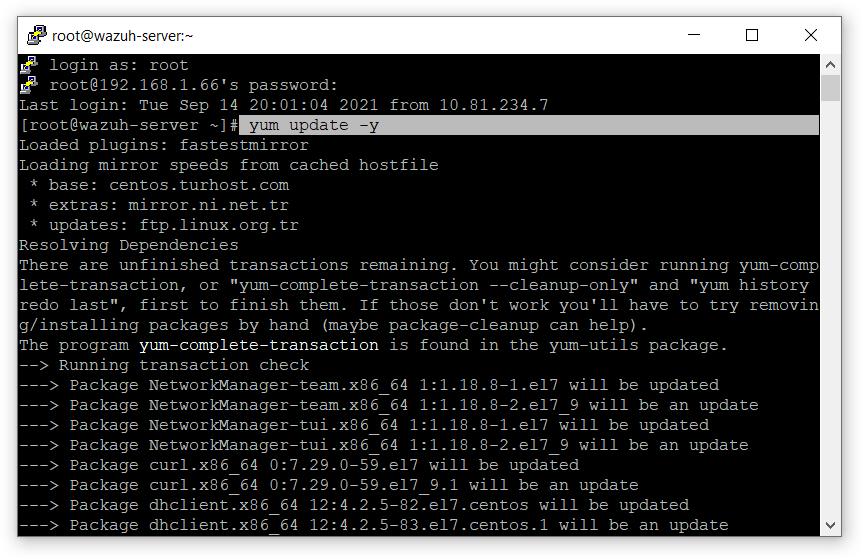
- 让我们更新软件包。
# 百胜更新 -y
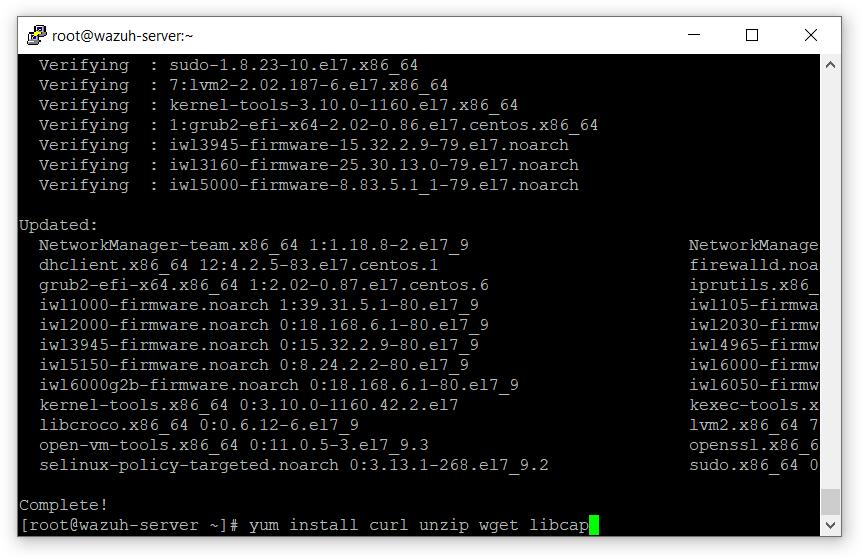
- 安装安装所需的包。
# yum install curl 解压 wget libcap
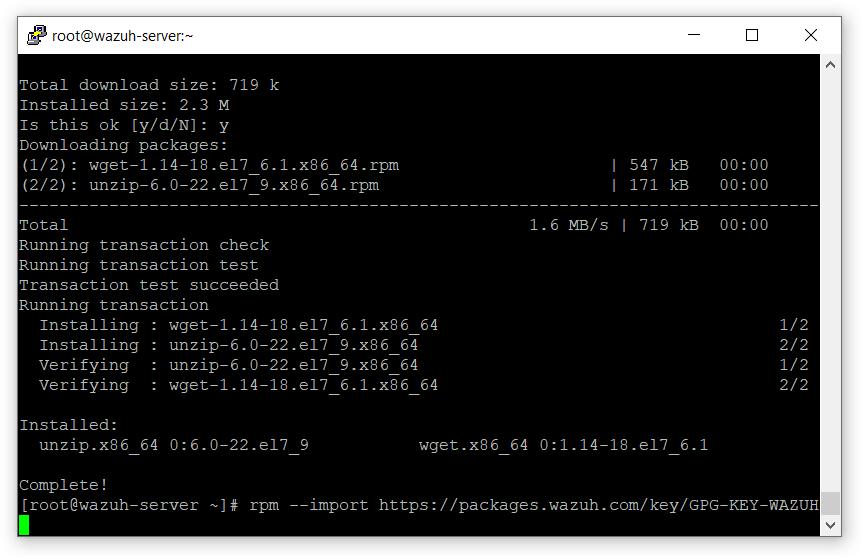
- 导入GPG密钥
# rpm --import https://packages.wazuh.com/key/GPG-KEY-WAZUH
- 添加仓库
# cat > /etc/yum.repos.d/wazuh.repo << EOF
[哇祖]
gpgchecku003d1
gpgkeyu003dhttps://packages.wazuh.com/key/GPG-KEY-WAZUH
启用u003d1
名称u003dEL-$releasever - Wazuh
baseurlu003dhttps://packages.wazuh.com/4.x/yum/
保护u003d1
EOF
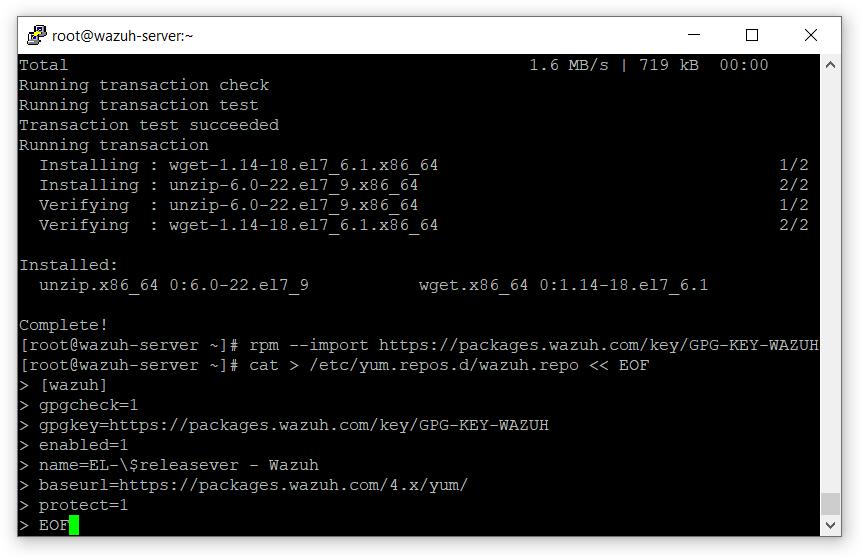
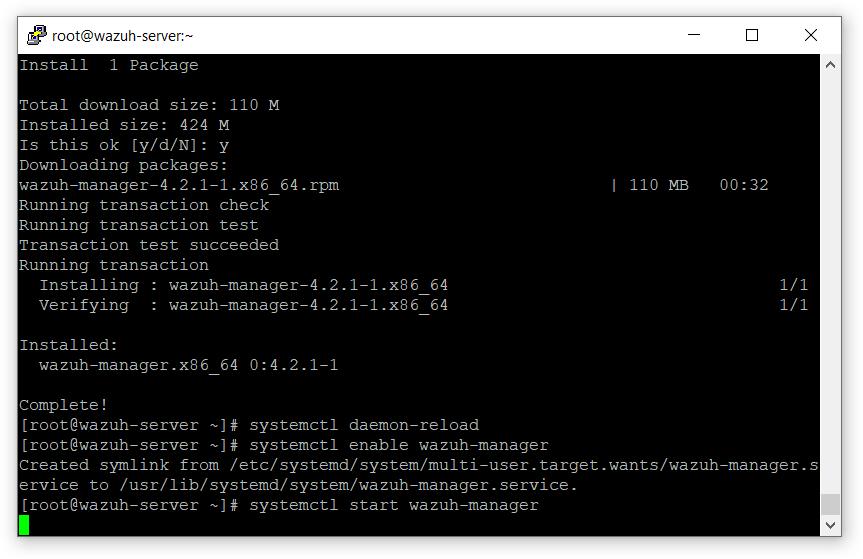
安装 Wazuh 管理器
# yum install wazuh-manager
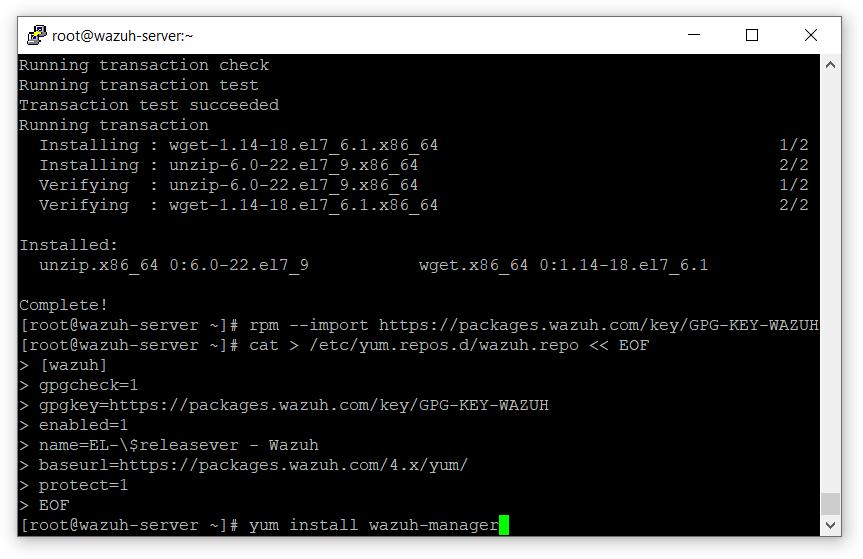
- 启动wazuh-manager
# systemctl 守护进程重载
# systemctl 启用 wazuh-manager
# systemctl start wazuh-manager
运行以下命令检查 Wazuh manager 状态是否
# systemctl 状态 wazuh-manager
安装 Elasticsearch
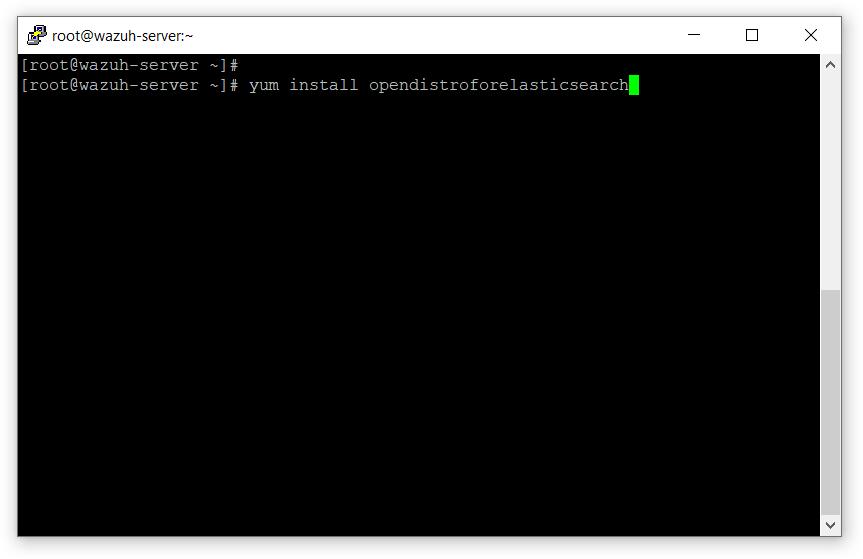
- 安装opendistroforelasticsearch
# yum install opendistroforelasticsearch
- 配置 Elasticsearch
# curl -so /etc/elasticsearch/elasticsearch.yml https://packages.wazuh.com/resources/4.2/open-distro/elasticsearch/7.x/elasticsearch_all_in_one.yml
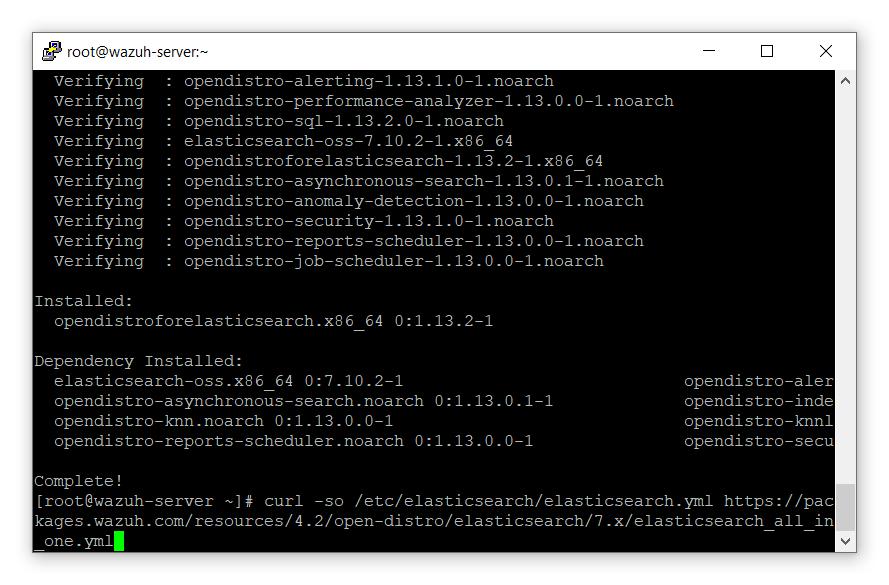
- 运行以下命令添加Wazuh用户
# curl -so /usr/share/elasticsearch/plugins/opendistro_security/securityconfig/roles.yml https://packages.wazuh.com/resources/4.2/open-distro/elasticsearch/roles/roles.yml
# curl -so /usr/share/elasticsearch/plugins/opendistro_security/securityconfig/roles_mapping.yml https://packages.wazuh.com/resources/4.2/open-distro/elasticsearch/roles/roles_mapping .yml
# curl -so /usr/share/elasticsearch/plugins/opendistro_security/securityconfig/internal_users.yml https://packages.wazuh.com/resources/4.2/open-distro/elasticsearch/roles/internal_users .yml
! zoz100078](https://devpress-image.s3.cn-north-1.jdcloud-oss.com/a/b99623d779_1*12ahdSj9hHa_UtQ5T8hXTw.jpg)
- 移除演示证书:
# rm /etc/elasticsearch/esnode-key.pem /etc/elasticsearch/esnode.pem /etc/elasticsearch/kirk-key.pem /etc/elasticsearch/kirk.pem /etc/elasticsearch/root-ca.pem - F
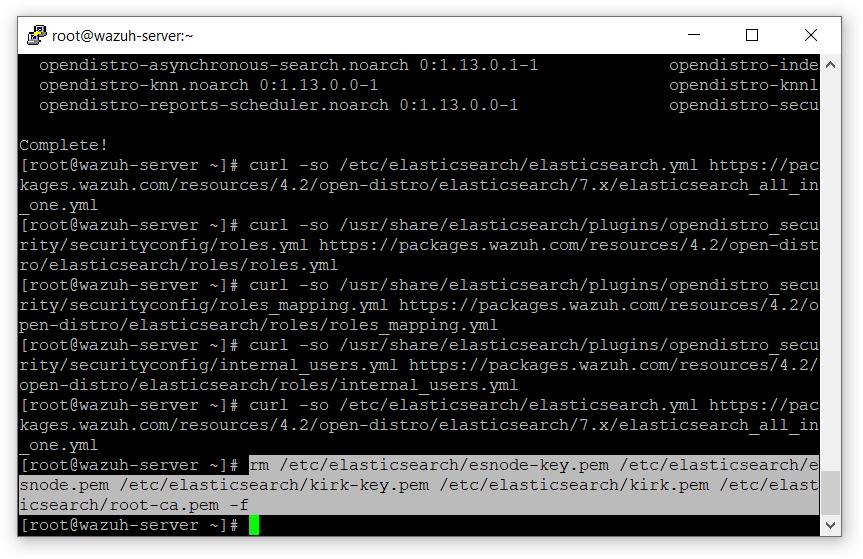
- 下载wazuh-cert-tool.sh
# curl -so ~/wazuh-cert-tool.shhttps://packages.wazuh.com/resources/4.2/open-distro/tools/certificate-utility/wazuh-cert-tool.sh
# curl -so ~/instances.ymlhttps://packages.wazuh.com/resources/4.2/open-distro/tools/certificate-utility/instances_aio.yml
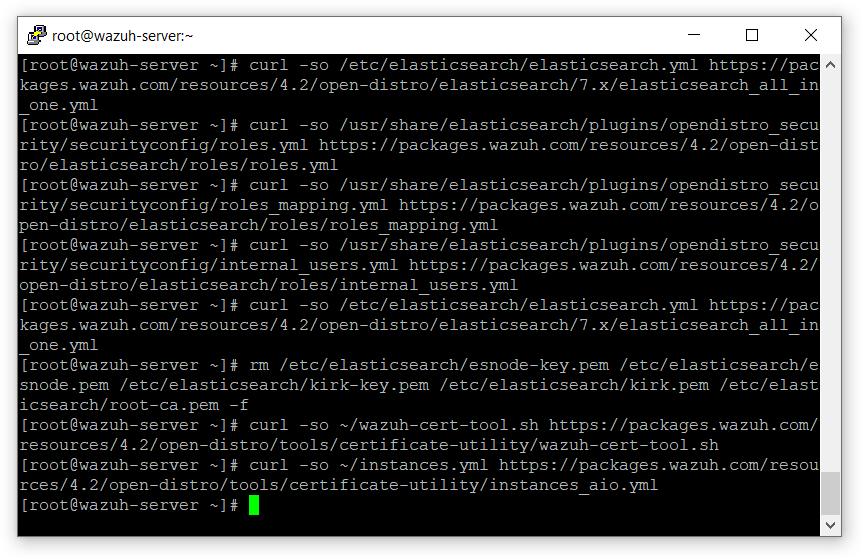
- sh. /wazuh-cert-tool.sh
# bash ~/wazuh-cert-tool.sh

- 移动 Elasticsearch 文件
# mkdir /etc/elasticsearch/certs/
# mv ~/certs/elasticsearch* /etc/elasticsearch/certs/
# mv ~/certs/admin* /etc/elasticsearch/certs/
# cp ~/certs/root-ca* /etc/elasticsearch/certs/

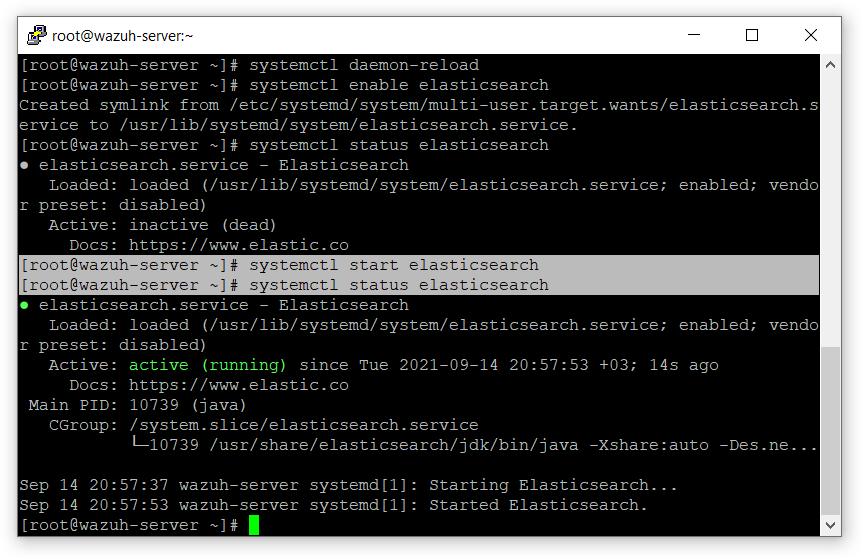
- 启动elasticsearch
# systemctl 守护进程重载
# systemctl 启用弹性搜索
# systemctl 启动弹性搜索
- 运行 Elasticsearch 脚本
# export JAVA_HOME\u003d/usr/share/elasticsearch/jdk/ && /usr/share/elasticsearch/plugins/opendistro_security/tools/securityadmin.sh - cd /usr/share/elasticsearch/plugins/opendistro_security/securityconfig/ -nhnv -cacert /etc/elasticsearch/certs/root-ca.pem -cert /etc/elasticsearch/certs/admin.pem -key /etc/elasticsearch /certs/admin-key.pem
! swz 100102 swz 100103 swz 100101
- 运行以下命令
# curl -XGET https://localhost:9200 -u admin:admin -k
! swz 100105 swz 100106 swz 100104
安装 Filebeat
- 安装Filebeat包
# 百胜安装文件节拍
! swz 100108 swz 100109 swz 100107
- 运行以下命令
# curl -so /etc/filebeat/filebeat.yml https://packages.wazuh.com/resources/4.2/open-distro/filebeat/7.x/filebeat_all_in_one.yml
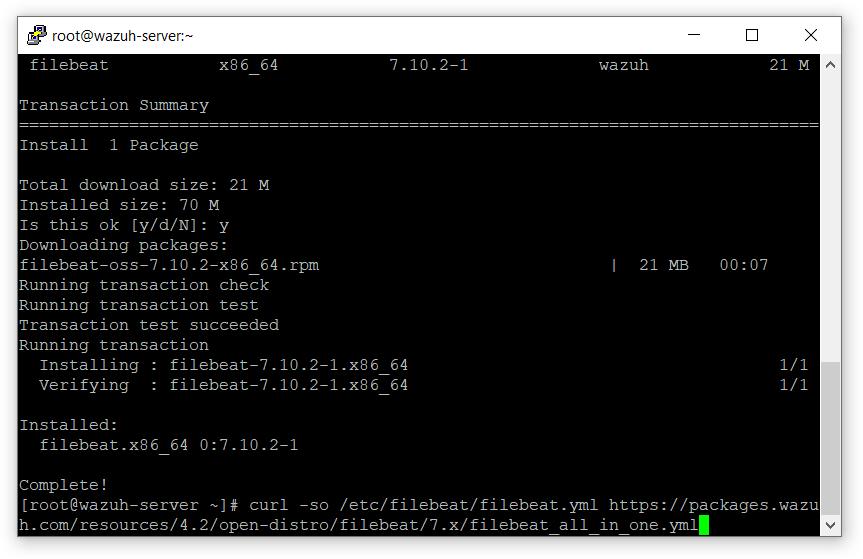
- 下载 Elasticsearch 的警报模板
# curl -so /etc/filebeat/wazuh-template.json https://raw.githubusercontent.com/wazuh/wazuh/4.2/extensions/elasticsearch/7.x/wazuh-template.json
# chmod go+r /etc/filebeat/wazuh-template.json
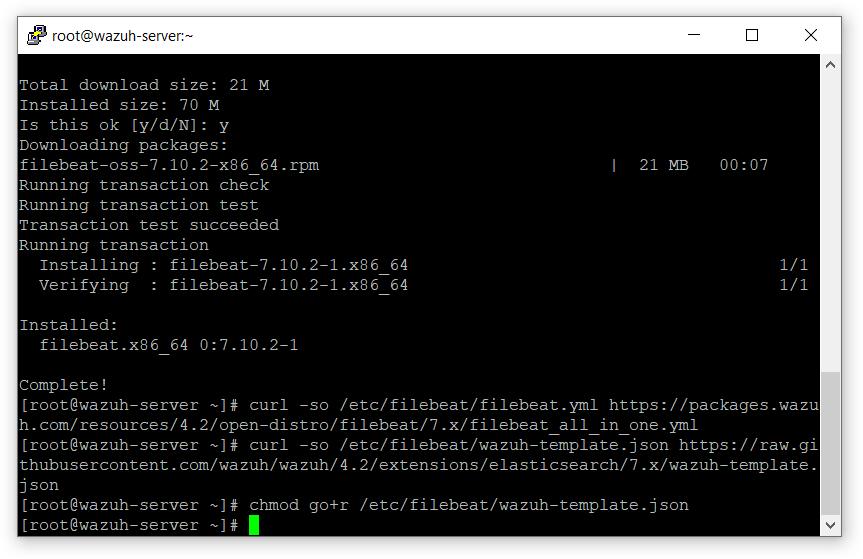
- 运行以下命令
# curl -s https://packages.wazuh.com/4.x/filebeat/wazuh-filebeat-0.1.tar.gz | tar -xvz -C /usr/share/filebeat/module
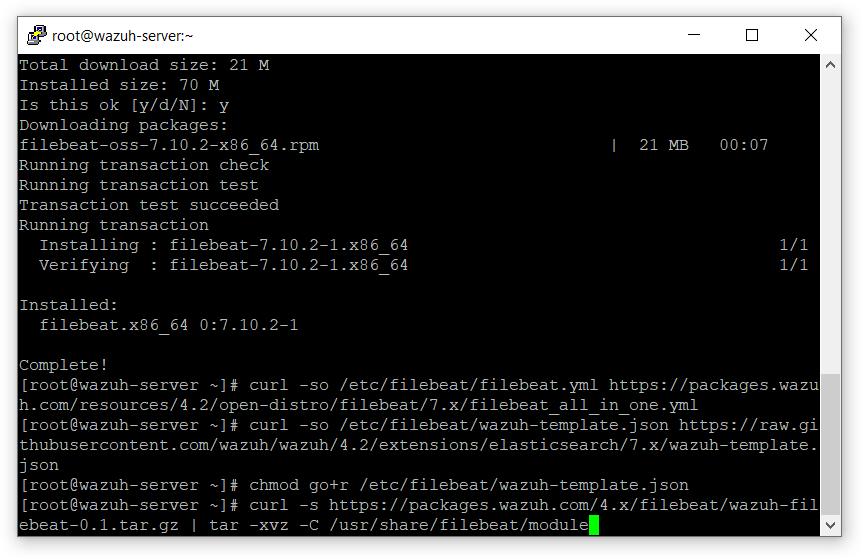
- 复制 Elasticsearch 证书
# mkdir /etc/filebeat/certs
# cp ~/certs/root-ca.pem /etc/filebeat/certs/
# mv ~/certs/filebeat* /etc/filebeat/certs/
- 启动服务filebeat
# systemctl 守护进程重载
# systemctl 启用文件节拍
# systemctl 启动文件节拍
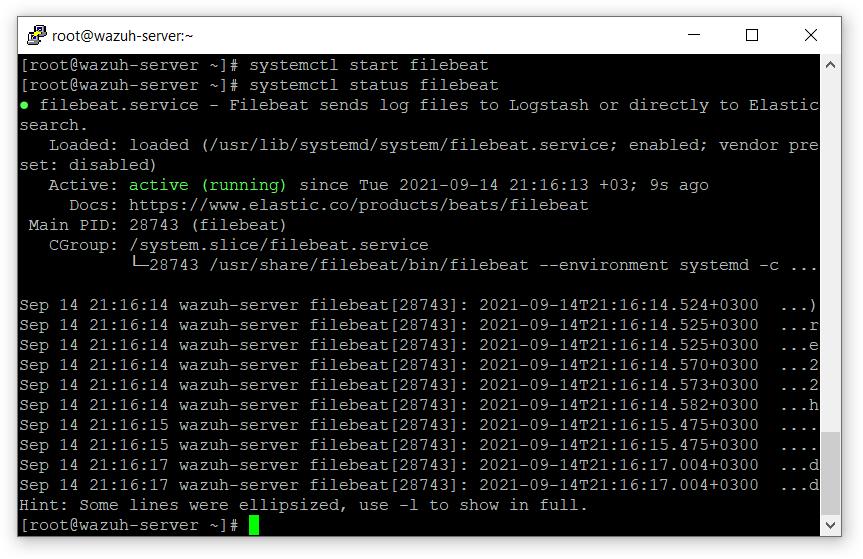
- 启动服务filebeat
# systemctl 守护进程重载
# systemctl 启用文件节拍
# systemctl 启动文件节拍
- 测试输出
# filebeat 测试输出

安装 Kibana
- 安装 Kibana 包
# yum install opendistroforelasticsearch-kibana
- 创建目录
# mkdir /usr/share/kibana/data
# chown -R kibana:kibana /usr/share/kibana/data
! swz 100129 swz 100130 swz 100128
- 安装 Wazuh Kibana 插件
# 高度 /usr/share/kibana
# sudo -u kibana /usr/share/kibana/bin/kibana-plugin installhttps://packages.wazuh.com/4.x/ui/kibana/wazuh_kibana-4.2.1_7.10.2- 1.zip
! zwz 100135 zwz 100136 zwz 100134
- 运行以下命令
# mkdir /etc/kibana/certs
# cp ~/certs/root-ca.pem /etc/kibana/certs/
# mv ~/certs/kibana* /etc/kibana/certs/
# chown kibana:kibana /etc/kibana/certs/*
# setcap 'cap_net_bind_serviceu003d+ep' /usr/share/kibana/node/bin/node
! zwz 100138 zwz 100139 zwz 100137
- 启动kibana服务
# systemctl 守护进程重载
# systemctl 启用 kibana
# systemctl 启动 kibana
! swz 100141 swz 100142 swz 100140
- 运行以下命令
# firewall-cmd --add-serviceu003dhttps --permanent
# systemctl 重启防火墙
- 准备网页登录
! swz 100144 swz 100145 swz 100143
- 必须打开以下端口才能让代理进行通信。
# sudo firewall-cmd——zoneu003dpublic——add-portu003d1515/tcp——permanent#sudo firewall-cmd——zoneu003dpublic——add-portu003d1514/tcp——permanent#sudo firewall-cmd——zoneu003dpublic — add-portu003d1514/udp — 永久# sudo firewall-cmd — zoneu003dpublic — add-portu003d514/udp — 永久# firewall-cmd — 重新加载
为 windows 部署新代理
- Wazuh 服务器地址添加 localhost IP 和比复制命令
! swz 100147 swz 100148 swz 100146
在计算机上运行以下命令以管理员身份运行 powershell
! zwz 100150 zwz 100151 zwz 100149
- 及以上
# &'C:\Program Files (x86)\ossec-agent\agent-auth.exe' -m 192.168.1.252
! swz 100153 swz 100154 swz 100152
代理通信现已准备就绪。感谢您阅读本文
更多推荐
 已为社区贡献557条内容
已为社区贡献557条内容







所有评论(0)