Helm快速部署Harbor仓库
k8s部署harbor
·
参考资料: https://mp.weixin.qq.com/s/TPt9Akf2OhK0y4stwa267g
本次部署k8s环境:
k8s版本:v1.23.1
helm版本:v3.9.4
1.安装helm
github地址: https://github.com/helm/helm/releases
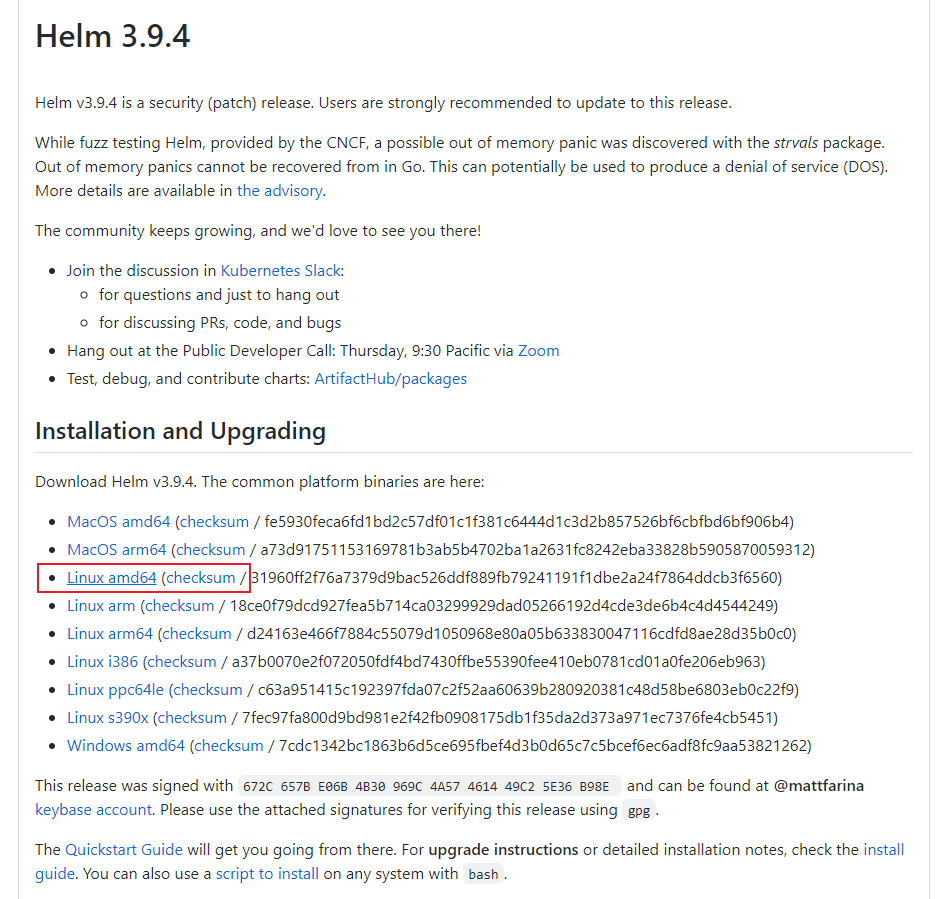
wget https://get.helm.sh/helm-v3.9.4-linux-amd64.tar.gz
tar -xf helm-v3.9.4-linux-amd64.tar.gz
cd linux-amd64
mv helm /usr/bin/
# 查看版本
helm version
version.BuildInfo{Version:"v3.9.4", GitCommit:"dbc6d8e20fe1d58d50e6ed30f09a04a77e4c68db", GitTreeState:"clean", GoVersion:"go1.17.13"}
# 先添加常用的chart源
helm repo add bitnami https://charts.bitnami.com/bitnami
helm repo add stable http://mirror.azure.cn/kubernetes/charts/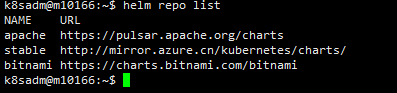
2.部署前准备
2.1添加持久化存储(NFS)
ubuntu下安装nfs
# 服务端192.168.0.167
apt-get install nfs-kernel-server
# 客户端启动rpcbind即可
systemctl start rpcbind.service编辑/etc/exports
/data2/k8s-share 192.168.0.0/22(rw,sync,no_root_squash,no_all_squash)
/data2/k8s-share 192.168.200.0/22(rw,sync,no_root_squash,no_all_squash)
# 修改后服务端重启nfs服务
systemctl restart nfs-kernel-server
systemctl enable nfs-kernel-server
# 客户端重启rpcbind
systemctl restart rpcbinding
# 客户端检查是否能正常挂载
showmount -e 192.168.0.167
# 正常输出
Export list for 192.168.0.167:
/data2/k8s-share 192.168.0.223,192.168.0.2242.2新建StorageClass
apiVersion: storage.k8s.io/v1
kind: StorageClass
metadata:
name: manage-167nfs
# 自定义provisioner名字
provisioner: nfswcwj.pri/ifs新增SA和ClusterRole
apiVersion: v1
kind: ServiceAccount
metadata:
name: nfs-client167
---
kind: ClusterRole
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: nfs-client167-runner
rules:
- apiGroups: [""]
resources: ["persistentvolumes"]
verbs: ["get", "list", "watch", "create", "delete"]
- apiGroups: [""]
resources: ["persistentvolumeclaims"]
verbs: ["get", "list", "watch", "update"]
- apiGroups: ["storage.k8s.io"]
resources: ["storageclasses"]
verbs: ["get", "list", "watch"]
- apiGroups: [""]
resources: ["events"]
verbs: ["list", "watch", "create", "update", "patch"]
- apiGroups: [""]
resources: ["endpoints"]
verbs: ["get", "list", "watch", "create", "update", "patch"]
---
kind: ClusterRoleBinding
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: run-nfs-client167
subjects:
- kind: ServiceAccount
name: nfs-client167
namespace: default
roleRef:
kind: ClusterRole
name: nfs-client167-runner
apiGroup: rbac.authorization.k8s.io添加provisioner
apiVersion: apps/v1
kind: Deployment
metadata:
name: nfs-client-167
spec:
replicas: 1
selector:
matchLabels:
app: nfs-client-167
strategy:
type: Recreate
template:
metadata:
labels:
app: nfs-client-167
spec:
imagePullSecrets:
- name: registry-pull-secret
serviceAccount: nfs-client-provisioner
containers:
- name: nfs-client-provisioner
image: easzlab/nfs-subdir-external-provisioner:v4.0.2
volumeMounts:
- name: nfs-client167-root
mountPath: /persistentvolumes
env:
- name: PROVISIONER_NAME
value: nfswcwj.pri/ifs
- name: NFS_SERVER
value: 192.168.0.167
- name: NFS_PATH
value: /data2/k8s-share
volumes:
- name: nfs-client167-root
nfs:
server: 192.168.0.167
path: /data2/k8s-share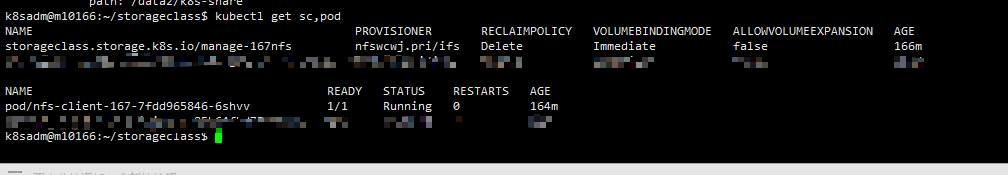
添加harbor的repo
helm repo add harbor https://helm.goharbor.io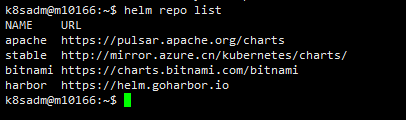
下载harbor安装包
# 获取对应chart
helm pull harbor/harbor
# 解压
tar xf harbor-1.11.0.tgz
cd harbor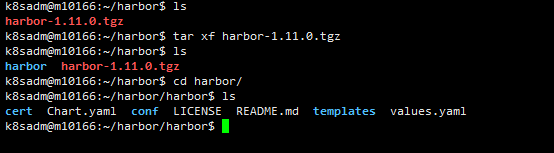
3.开始部署
3.1生成tls证书
# 获得ca
openssl req -newkey rsa:4096 -nodes -sha256 -keyout ca.key -x509 -days 3650 -out ca.crt
# 生成证书签名请求
openssl req -newkey rsa:4096 -nodes -sha256 -keyout tls.key -out tls.csr
# 生成证书
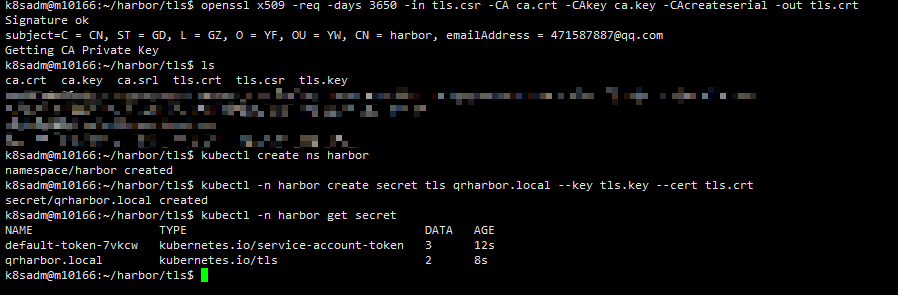
openssl x509 -req -days 3650 -in tls.csr -CA ca.crt -CAkey ca.key -CAcreateserial -out tls.crt
# 生成secret资源
kubectl -n harbor create secret tls qrharbor.local --key tls.key --cert tls.crt 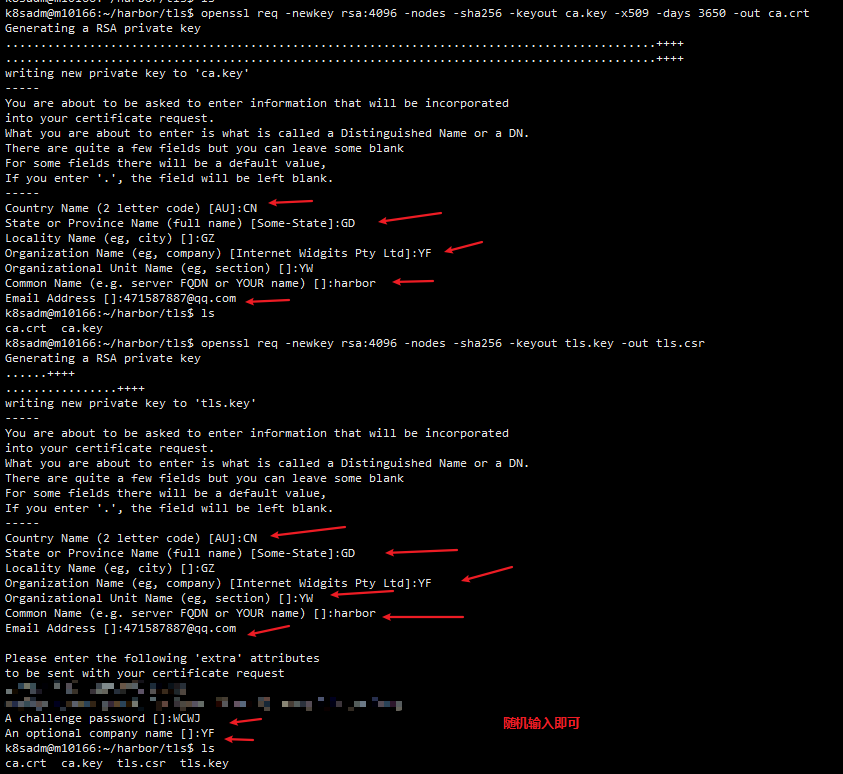
3.2解压harbor的chart后进入目录新增override.yaml
expose: #web浏览器访问用的证书
type: ingress
tls:
#enabled: true
#certSource: "secret"
secret:
secretName: "qrharbor.local"
# notarySecretName: "qrharbor.local"
ingress:
hosts:
core: qrharbor.local
notary: notary-qrharbor.local
#controller: default
annotations:
#ingress.kubernetes.io/ssl-redirect: "true"
#ingress.kubernetes.io/proxy-body-size: "0"
#### 如果是 traefik ingress,则按下面配置:
# kubernetes.io/ingress.class: "traefik"
# traefik.ingress.kubernetes.io/router.tls: 'true'
# traefik.ingress.kubernetes.io/router.entrypoints: websecure
#### 如果是 nginx ingress,则按下面配置:
#nginx.ingress.kubernetes.io/ssl-redirect: "true"
#nginx.ingress.kubernetes.io/proxy-body-size: "0"
nginx.org/client-max-body-size: "1024m"
externalURL: https://qrharbor.local
#internalTLS: #harbor内部组件用的证书
# enabled: true
# certSource: "auto"
persistence:
enabled: true
resourcePolicy: "keep"
persistentVolumeClaim:
registry: # 存镜像的
storageClass: "manage-167nfs"
accessMode: ReadWriteOnce
size: 20Gi
chartmuseum: #存helm的chart
storageClass: "manage-167nfs"
accessMode: ReadWriteOnce
size: 5Gi
jobservice: # jobservice
jobLog:
storageClass: "manage-167nfs"
accessMode: ReadWriteOnce
size: 2Gi
scanDataExports:
storageClass: "manage-167nfs"
accessMode: ReadWriteOnce
size: 2Gi
database: #数据库 pgsql
storageClass: "manage-167nfs"
accessMode: ReadWriteOnce
size: 1Gi
redis: # redis
storageClass: "manage-167nfs"
accessMode: ReadWriteOnce
size: 1Gi
trivy: # 漏洞扫描
storageClass: "manage-167nfs"
accessMode: ReadWriteOnce
size: 5Gi3.3启动harbor
# 安装部署
helm install harbor ./ -f values.yaml -f override.yaml -n harbor
测试访问

默认登录用户:admin 密码:Harbor12345
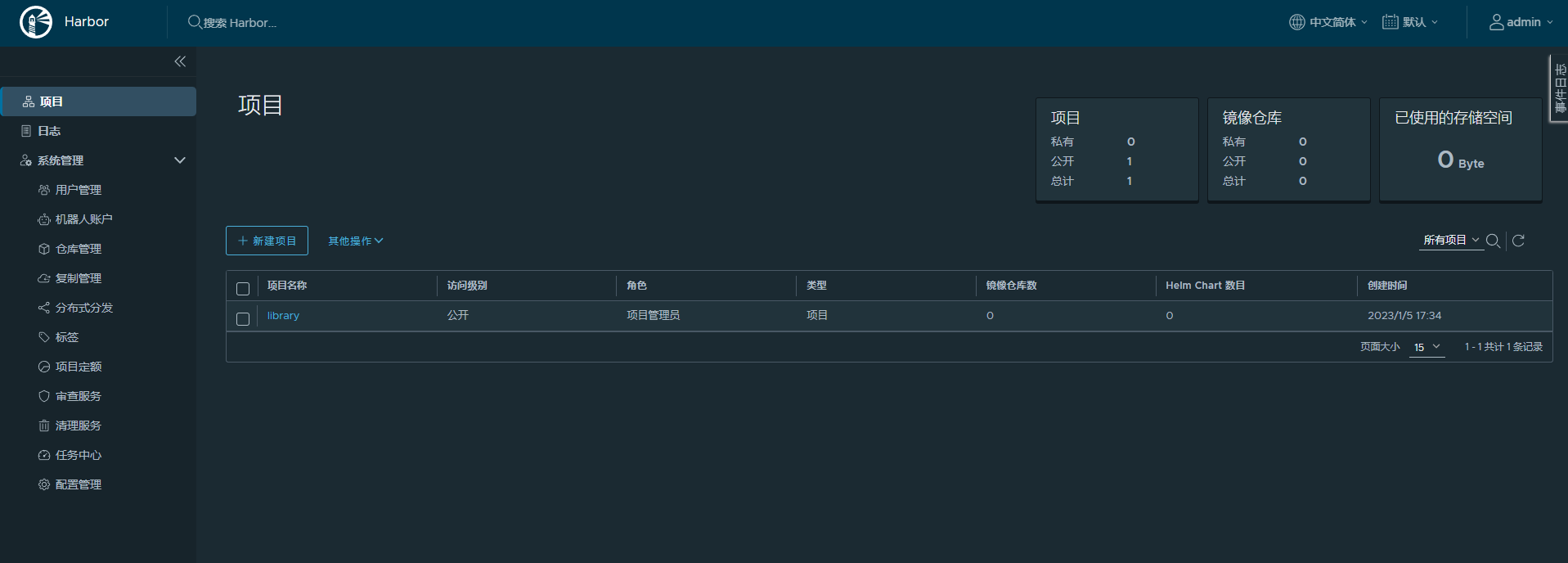
完成!
3.4生成secret方便部署时推送和拉取镜像
# 在命名空间beta下创建harbor的secret
kubectl -n beta create secret docker-registry harborlogin \
--docker-server=qrharbor.local \
--docker-username=admin \
--docker-password=Harbor123456 \更多推荐
 已为社区贡献2条内容
已为社区贡献2条内容









所有评论(0)