229. k8s_v1.15GUI管理工具(Dashboard)
1.准备dashboard镜像运维主机操作[root@hdss7-200 ~]# docker pull k8scn/kubernetes-dashboard-amd64:v1.10.1[root@hdss7-200 ~]# docker tag 0c60bcf89900 harbor.od.com/k8s/dashboard:v1.10.1[root@hdss7-200 ~]# docker p
·
1.准备dashboard镜像
运维主机操作
[root@k8s7-200 ~]# docker pull k8scn/kubernetes-dashboard-amd64:v1.10.1
[root@k8s7-200 ~]# docker tag 0c60bcf89900 harbor.od.com/k8s/dashboard:v1.10.1
[root@k8s7-200 ~]# docker push harbor.od.com/k8s/dashboard:v1.10.1
2.准备资源配置清单
[root@k8s7-200 ~]# mkdir -p /data/k8s-yaml/dashboard && cd /data/k8s-yaml/dashboard
1.rbac.yaml
apiVersion: v1
kind: ServiceAccount
metadata:
labels:
k8s-app: kubernetes-dashboard
addonmanager.kubernetes.io/mode: Reconcile
name: kubernetes-dashboard-admin
namespace: kube-system
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
name: kubernetes-dashboard-admin
namespace: kube-system
labels:
k8s-app: kubernetes-dashboard
addonmanager.kubernetes.io/mode: Reconcile
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: cluster-admin
subjects:
- kind: ServiceAccount
name: kubernetes-dashboard-admin
namespace: kube-system
2.deployment.yaml
apiVersion: apps/v1
kind: Deployment
metadata:
name: kubernetes-dashboard
namespace: kube-system
labels:
k8s-app: kubernetes-dashboard
kubernetes.io/cluster-service: "true"
addonmanager.kubernetes.io/mode: Reconcile
spec:
selector:
matchLabels:
k8s-app: kubernetes-dashboard
template:
metadata:
labels:
k8s-app: kubernetes-dashboard
annotations:
scheduler.alpha.kubernetes.io/critical-pod: ''
spec:
priorityClassName: system-cluster-critical
containers:
- name: kubernetes-dashboard
image: harbor.od.com/public/dashboard:v1.10.1
resources:
limits:
cpu: 100m
memory: 300Mi
requests:
cpu: 50m
memory: 100Mi
ports:
- containerPort: 8443
protocol: TCP
args:
# PLATFORM-SPECIFIC ARGS HERE
- --auto-generate-certificates
volumeMounts:
- name: tmp-volume
mountPath: /tmp
livenessProbe:
httpGet:
scheme: HTTPS
path: /
port: 8443
initialDelaySeconds: 30
timeoutSeconds: 30
volumes:
- name: tmp-volume
emptyDir: {}
serviceAccountName: kubernetes-dashboard-admin
tolerations:
- key: "CriticalAddonsOnly"
operator: "Exists"
3.service.yaml
apiVersion: v1
kind: Service
metadata:
name: kubernetes-dashboard
namespace: kube-system
labels:
k8s-app: kubernetes-dashboard
kubernetes.io/cluster-service: "true"
addonmanager.kubernetes.io/mode: Reconcile
spec:
selector:
k8s-app: kubernetes-dashboard
ports:
- port: 443
targetPort: 8443
4.ingress.yaml
apiVersion: extensions/v1beta1
kind: Ingress
metadata:
name: kubernetes-dashboard
namespace: kube-system
annotations:
kubernetes.io/ingress.class: traefik
spec:
rules:
- host: dashboard.od.com
http:
paths:
- backend:
serviceName: kubernetes-dashboard
servicePort: 443
3.依次执行创建
浏览器打开:http://k8s-yaml.od.com/dashboard 检查资源配置清单文件是否正确创建在任意运算节点应用资源配置清单
[root@k8s7-21.host.com ~]# kubectl apply -f http://k8s-yaml.od.com/dashboard/rbac.yaml
serviceaccount/kubernetes-dashboard-admin created
clusterrolebinding.rbac.authorization.k8s.io/kubernetes-dashboard-admin created
[root@k8s7-21.host.com ~]# kubectl apply -f http://k8s-yaml.od.com/dashboard/deployment.yaml
deployment.apps/kubernetes-dashboard created
[root@k8s7-21.host.com ~]# kubectl apply -f http://k8s-yaml.od.com/dashboard/service.yaml
service/kubernetes-dashboard created
[root@k8s7-21.host.com ~]# kubectl apply -f http://k8s-yaml.od.com/dashboard/ingress.yaml
ingress.extensions/kubernetes-dashboard created
4.解析域名
/var/named/od.com.zone
dashboard 60 IN A 10.4.7.10
5.证书签发
[root@k8s7-200 ~]# cd /opt/certs/
[root@k8s7-200 certs]# (umask 077; openssl genrsa -out dashboard.od.com.key 2048)
[root@k8s7-200 certs]# openssl req -new -key dashboard.od.com.key -out dashboard.od.com.csr -subj "/CN=dashboard.od.com/C=CN/ST=SH/L=Shanghai/O=Datacloak/OU=ops"
[root@k8s7-200 certs]# openssl x509 -req -in dashboard.od.com.csr -CA ca.pem -CAkey ca-key.pem -CAcreateserial -out dashboard.od.com.crt -days 3650
[root@k8s7-200 certs]# ll dashboard.od.com.*
-rw-r--r-- 1 root root 1196 Jan 29 20:52 dashboard.od.com.crt
-rw-r--r-- 1 root root 1005 Jan 29 20:51 dashboard.od.com.csr
-rw------- 1 root root 1675 Jan 29 20:51 dashboard.od.com.key
[root@k8s7-200 certs]# scp dashboard.od.com.key dashboard.od.com.crt k8s7-11:/etc/nginx/certs/
[root@k8s7-200 certs]# scp dashboard.od.com.key dashboard.od.com.crt k8s7-12:/etc/nginx/certs/
6.配置Nginx
# k8s7-11和k8s7-12都需要操作
[root@k8s7-11 ~]# vim /etc/nginx/conf.d/dashborad.conf
server {
listen 80;
server_name dashboard.od.com;
rewrite ^(.*)$ https://${server_name}$1 permanent;
}
server {
listen 443 ssl;
server_name dashboard.od.com;
ssl_certificate "certs/dashboard.od.com.crt";
ssl_certificate_key "certs/dashboard.od.com.key";
ssl_session_cache shared:SSL:1m;
ssl_session_timeout 10m;
ssl_ciphers HIGH:!aNULL:!MD5;
ssl_prefer_server_ciphers on;
location / {
proxy_pass http://default_backend_traefik;
proxy_set_header Host $http_host;
proxy_set_header x-forwarded-for $proxy_add_x_forwarded_for;
}
}
[root@k8s7-11 ~]# nginx -t && nginx -s reload
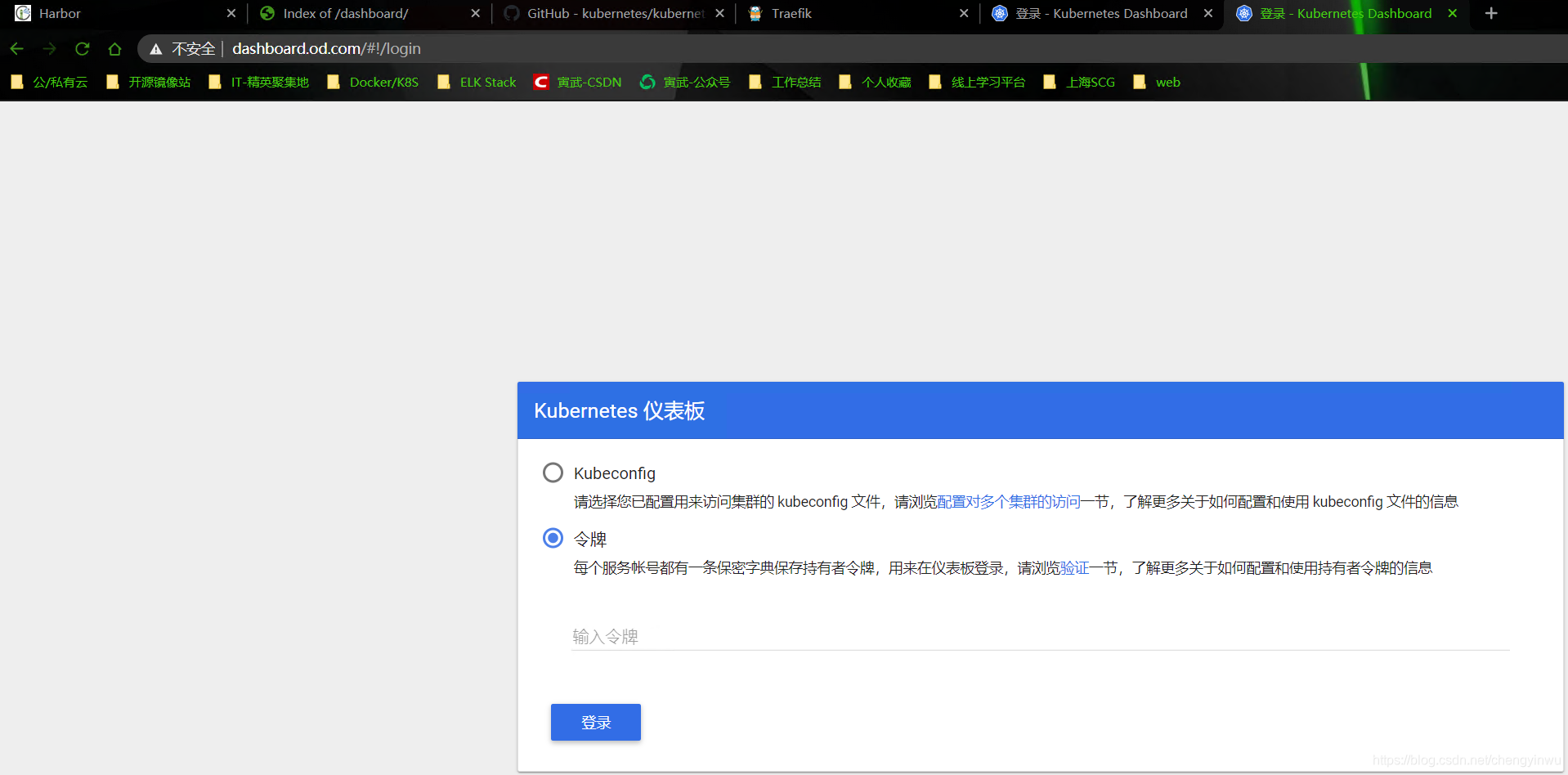
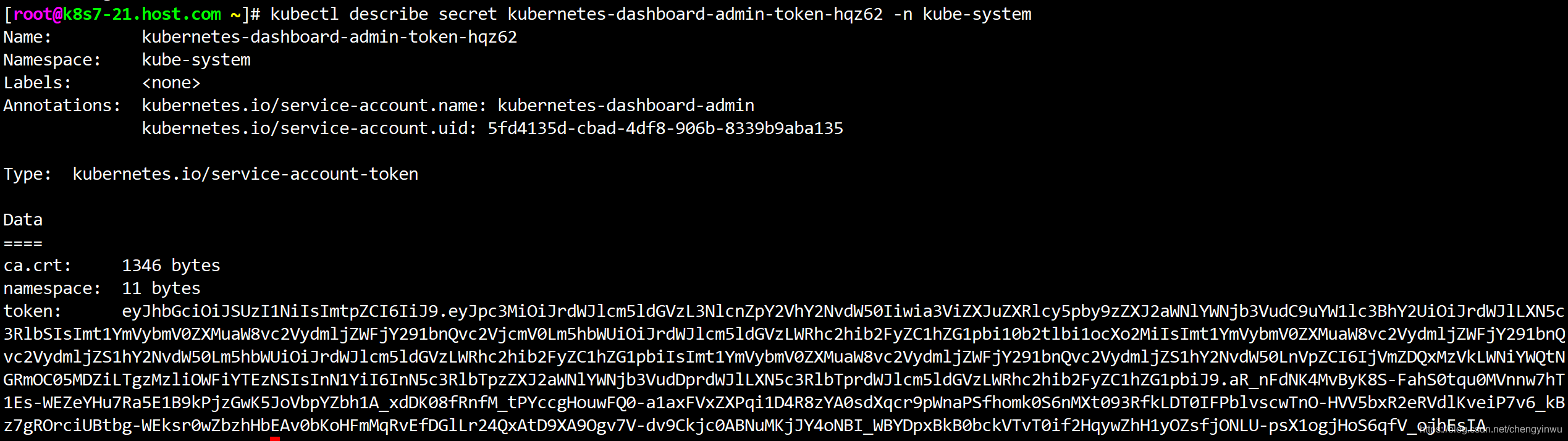
7.测试Token登录
[root@k8s7-21.host.com ~]# kubectl get secret -n kube-system
NAME TYPE DATA AGE
coredns-token-4jnph kubernetes.io/service-account-token 3 18h
default-token-6frg9 kubernetes.io/service-account-token 3 27h
kubernetes-dashboard-admin-token-hqz62 kubernetes.io/service-account-token 3 35m
kubernetes-dashboard-key-holder Opaque 2 35m
traefik-ingress-controller-token-zbk57 kubernetes.io/service-account-token 3 114m
更多推荐
 已为社区贡献32条内容
已为社区贡献32条内容









所有评论(0)