aws 控制台访问慢
There are cases where you need to provide a cross account access to the objects in your AWS account. There are a couple of ways to do this and you can find the details here, but among them is using cross-account IAM roles simplifies provisioning cross-account access to various AWS services, removing the need to manage multiple policies.
Ť这里有你需要提供的对象跨帐户访问您的AWS帐号的情况。 有两种方法可以执行此操作,您可以在此处找到详细信息,但是其中一种方法是使用跨账户IAM角色,从而简化了对各种AWS服务的跨账户访问的配置,从而无需管理多个策略。
For the sake of simplicity, let’s take an example where a user from AWS account A would want to programmatically manage objects in a S3 bucket present in AWS account B .
为简单起见,让我们举一个示例,其中来自AWS账户A的用户希望以编程方式管理AWS账户B中存在的S3存储桶中的对象。
使用AWS控制台设置AWS账户 (Setting up AWS accounts using AWS Console)
To use cross-account IAM roles to manage S3 bucket access, follow these steps:
要使用跨帐户IAM角色来管理S3存储桶访问,请按照以下步骤操作:
- Create IAM user and roles in respective AWS accounts: 在相应的AWS账户中创建IAM用户和角色:
IAM Role in Account A = arn:aws:iam::AccountA:role/RoleA
IAM User in Account A = arn:aws:iam::AccountA:user/UserA
IAM Role in Account B = arn:aws:iam::AccountB:role/RoleBSetup in Account B:
在帐户B中进行设置:
In Account B, attach below policy to grant RoleB permissions to perform required S3 operations. Below example talks about only upload and download objects from S3.
在帐户B中,附加以下策略以授予RoleB权限以执行必需的S3操作。 下面的示例仅讨论从S3上传和下载对象。
{
"Version": "2012–10–17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"s3:GetObject",
"s3:PutObject"
],
"Resource": "arn:aws:s3:::AccountB_S3BucketName/*"
}
]
}In RoleB’s trust policy, grant RoleA permissions to assume RoleB:
在RoleB的信任策略中,授予RoleA权限以承担RoleB:
{
"Version": "2012–10–17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::AccountA:role/RoleA"
},
"Action": "sts:AssumeRole"
}
]
}Setup in Account A:
在帐户A中进行设置:
Assign a policy to RoleA granting permissions to assume RoleB.
向RoleA分配策略以授予承担RoleB的权限。
{
"Version": "2012–10–17",
"Statement": {
"Effect": "Allow",
"Action": "sts:AssumeRole",
"Resource": "arn:aws:iam::AccountB:role/RoleB"
}
}Add UserA in Trust relationships tab of RoleA.
在RoleA的“信任关系”选项卡中添加UserA。
{
"Version": "2012–10–17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"AWS": [
"arn:aws:iam::AccountA:user/UserA"
]
},
"Action": "sts:AssumeRole",
"Condition": {}
}
]
}设置AWS凭证文件 (Setting up AWS credentials file)
By following above mentioned steps, you have setup UserA in Account A to assume RoleA and then RoleB to access S3 bucket. Now it’s time to prepare the AWS credentials file (normally present under ~/.aws/credentials) for accessing the S3 bucket using AWSCLi.
通过执行上述步骤,您已经在帐户A中设置了UserA以承担RoleA,然后让RoleB访问S3存储桶。 现在是时候准备AWS凭证文件了(通常在〜/ .aws / credentials下),以便使用AWSCLi访问S3存储桶。
Below is how the credential file will look like:
以下是凭证文件的外观:
使用AWSCLi访问S3存储桶 (Accessing the S3 bucket using AWSCLi)
Check if you are able to assume RoleB using credentials for UserA. Run below AWS command:
检查是否可以使用UserA的凭据承担RoleB。 在AWS命令下运行:
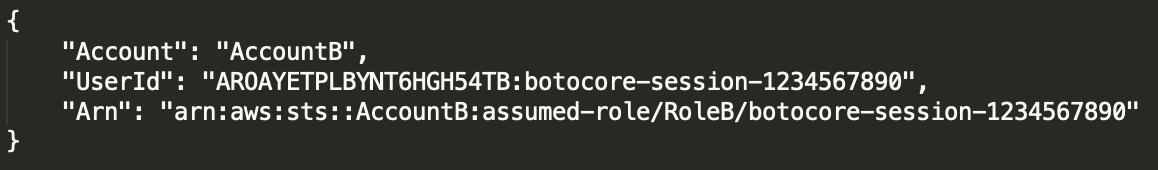
aws sts --profile RoleB get-caller-identityThe output would be something like this:
输出将是这样的:
Now you can run below command to recursively download the contents of the bucket in Account B to current folder on your machine.
现在,您可以运行以下命令,将帐户B中存储桶的内容递归下载到计算机上的当前文件夹中。
aws s3 --profile RoleB cp s3://AccountB_S3BucketName . --recursive翻译自: https://medium.com/adobetech/working-with-cross-account-roles-in-aws-b4f21dd72f4a
aws 控制台访问慢






 已为社区贡献1条内容
已为社区贡献1条内容

所有评论(0)